Byod Security Market Report
Published Date: 31 January 2026 | Report Code: byod-security
Byod Security Market Size, Share, Industry Trends and Forecast to 2033
This report provides a comprehensive analysis of the BYOD Security market, including market size, segmentation, regional insights, and trends from 2023 to 2033. The insights aim to guide stakeholders in understanding the evolving landscape of BYOD security solutions.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
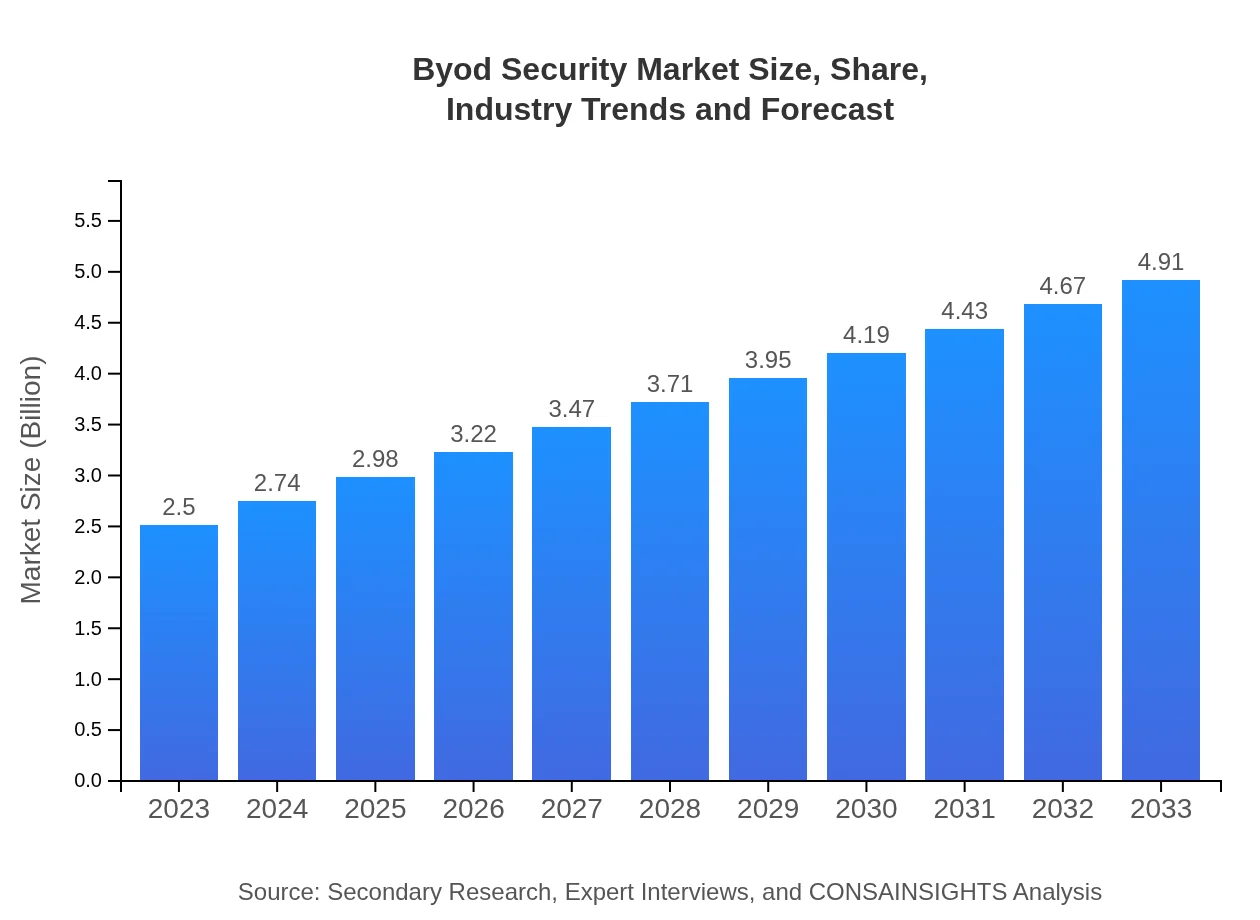
| 2023 Market Size | $2.50 Billion |
| CAGR (2023-2033) | 6.8% |
| 2033 Market Size | $4.91 Billion |
| Top Companies | Cisco Systems, Inc., Palo Alto Networks, Inc., VMware, Inc., IBM Security |
| Last Modified Date | 31 January 2026 |
BYOD Security Market Overview
Customize Byod Security Market Report market research report
- ✔ Get in-depth analysis of Byod Security market size, growth, and forecasts.
- ✔ Understand Byod Security's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Byod Security
What is the Market Size & CAGR of BYOD Security market in 2023?
BYOD Security Industry Analysis
BYOD Security Market Segmentation and Scope
Tell us your focus area and get a customized research report.
BYOD Security Market Analysis Report by Region
Europe Byod Security Market Report:
Europe's market for BYOD Security is projected to grow from $0.77 billion in 2023 to $1.51 billion by 2033. The region demonstrates a strong focus on data protection and compliance with regulations like the GDPR. Companies in Europe are increasingly investing in BYOD security solutions to mitigate risks associated with shared devices and remote working.Asia Pacific Byod Security Market Report:
In the Asia Pacific region, the BYOD Security market was valued at approximately $0.47 billion in 2023 and is projected to grow to $0.92 billion by 2033. The market's growth can be attributed to increasing adoption of mobile technologies and rising awareness regarding cybersecurity threats across various industries. However, the challenge of varying regulations across countries presents a hurdle for uniform policy implementations.North America Byod Security Market Report:
The North American BYOD Security market dominated the global landscape, valued at approximately $0.89 billion in 2023 with projections to reach $1.74 billion by 2033. The region's advanced technological infrastructure, high mobile device usage, and stringent regulatory frameworks significantly contribute to this growth. Organizations are investing heavily in cybersecurity measures to fortify their security postures amidst increasing cyber threats.South America Byod Security Market Report:
South America exhibits a developing BYOD Security market, with a valuation of $0.02 billion in 2023, expected to reach $0.05 billion by 2033. The slow growth can be linked to limited investments in advanced security technologies and comparatively lower mobile device penetration. Nevertheless, a rising number of startups and SME adoption of BYOD can fuel market growth.Middle East & Africa Byod Security Market Report:
The BYOD Security market in the Middle East and Africa is expected to grow from $0.35 billion in 2023 to $0.69 billion by 2033. The expansion of digital transformation initiatives and increasing smartphone penetration are key factors driving demand for security solutions. However, regions with varying cybersecurity maturity levels may impact overall market growth.Tell us your focus area and get a customized research report.
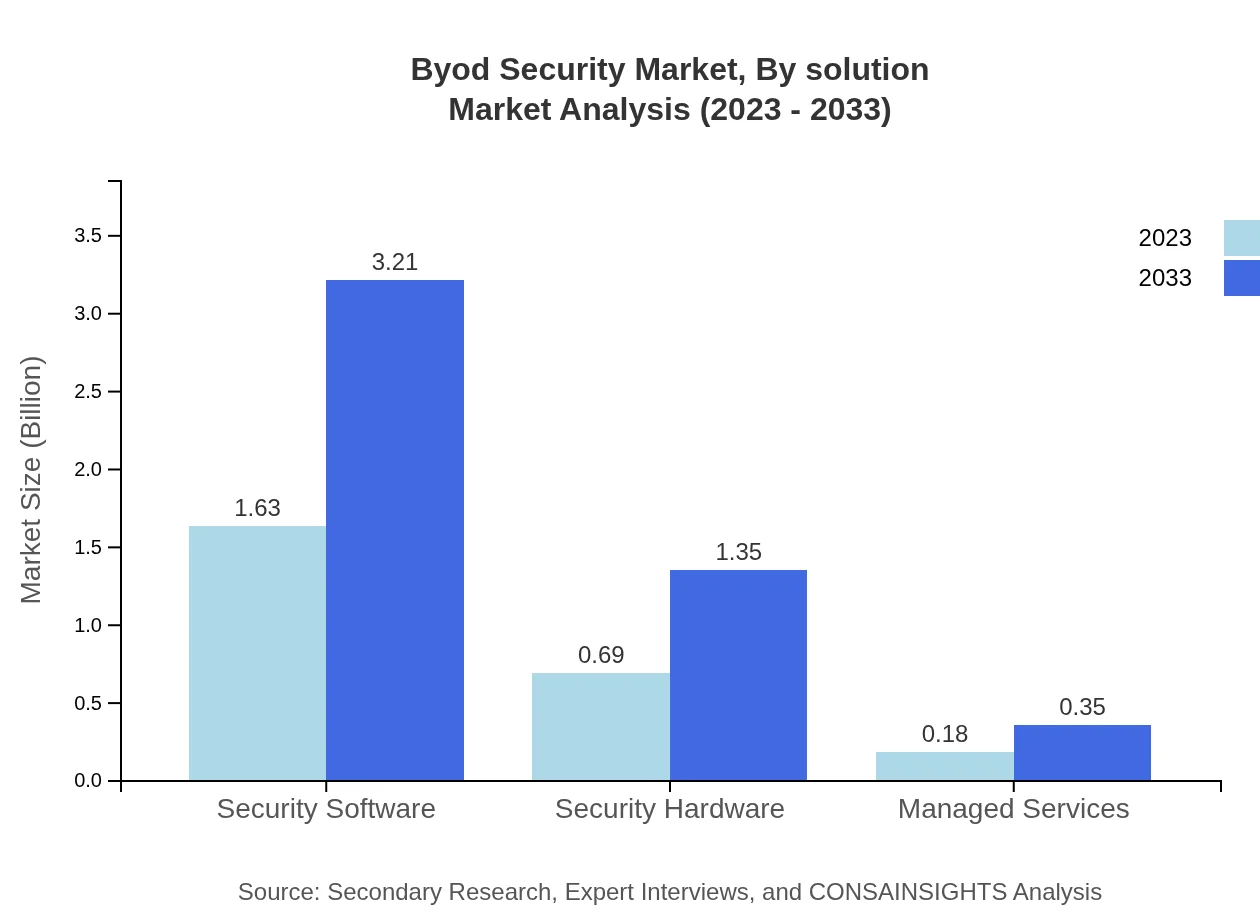
Byod Security Market Analysis By Solution
In the BYOD Security market by solution, Security Software is expected to dominate with a market size of $1.63 billion in 2023, growing to $3.21 billion by 2033, accounting for around 65.29% market share. Security Hardware, although trailing behind, is projected to grow from $0.69 billion to $1.35 billion. Managed Services also hold potential, growing from $0.18 billion to $0.35 billion.
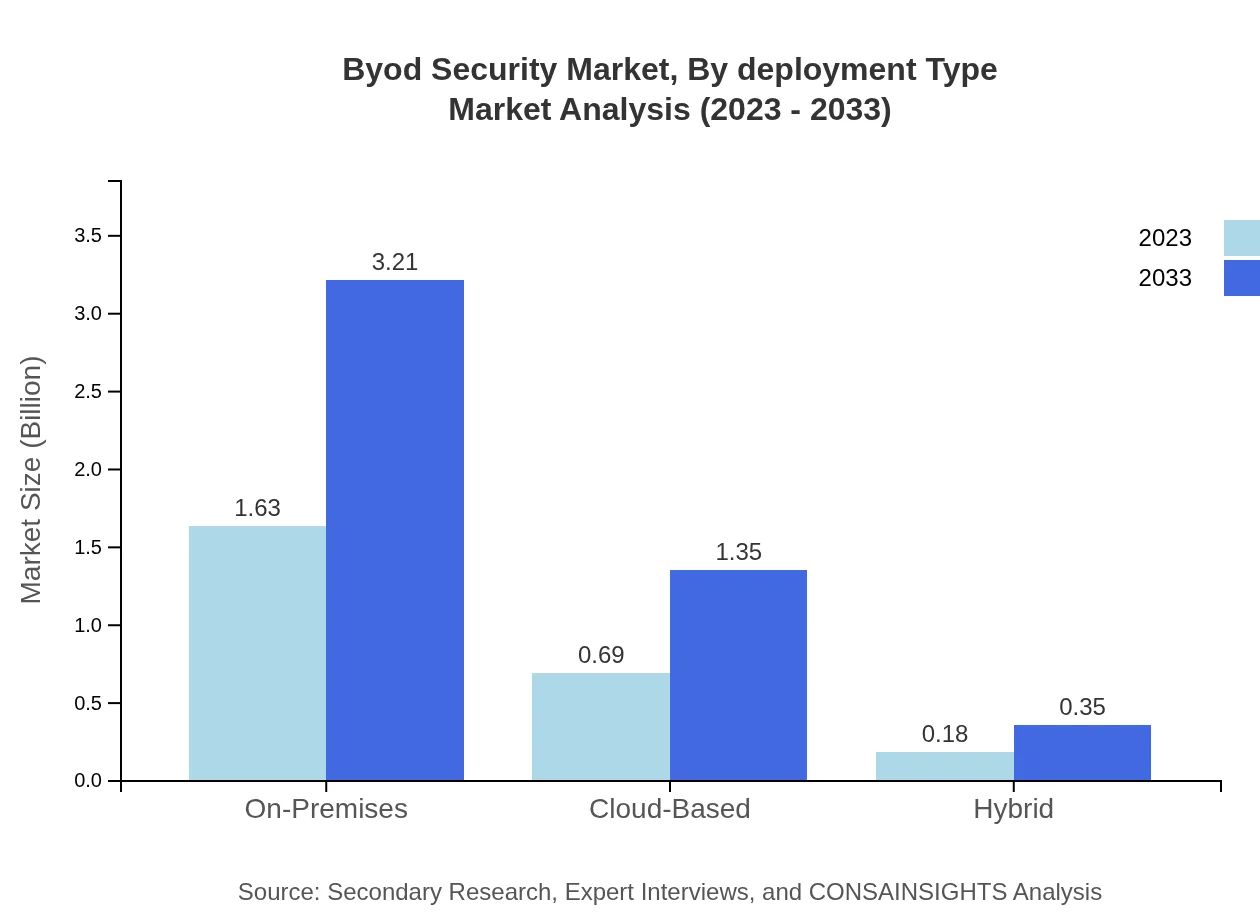
Byod Security Market Analysis By Deployment Type
By deployment type, the On-Premises segment leads the BYOD Security market, expected to grow from $1.63 billion in 2023 to $3.21 billion by 2033, maintaining a steady 65.29% share. Cloud-Based solutions follow, anticipated to rise from $0.69 billion to $1.35 billion. Hybrid models are also on the rise, likely reaching $0.35 billion, indicating a trend toward flexible deployment strategies.
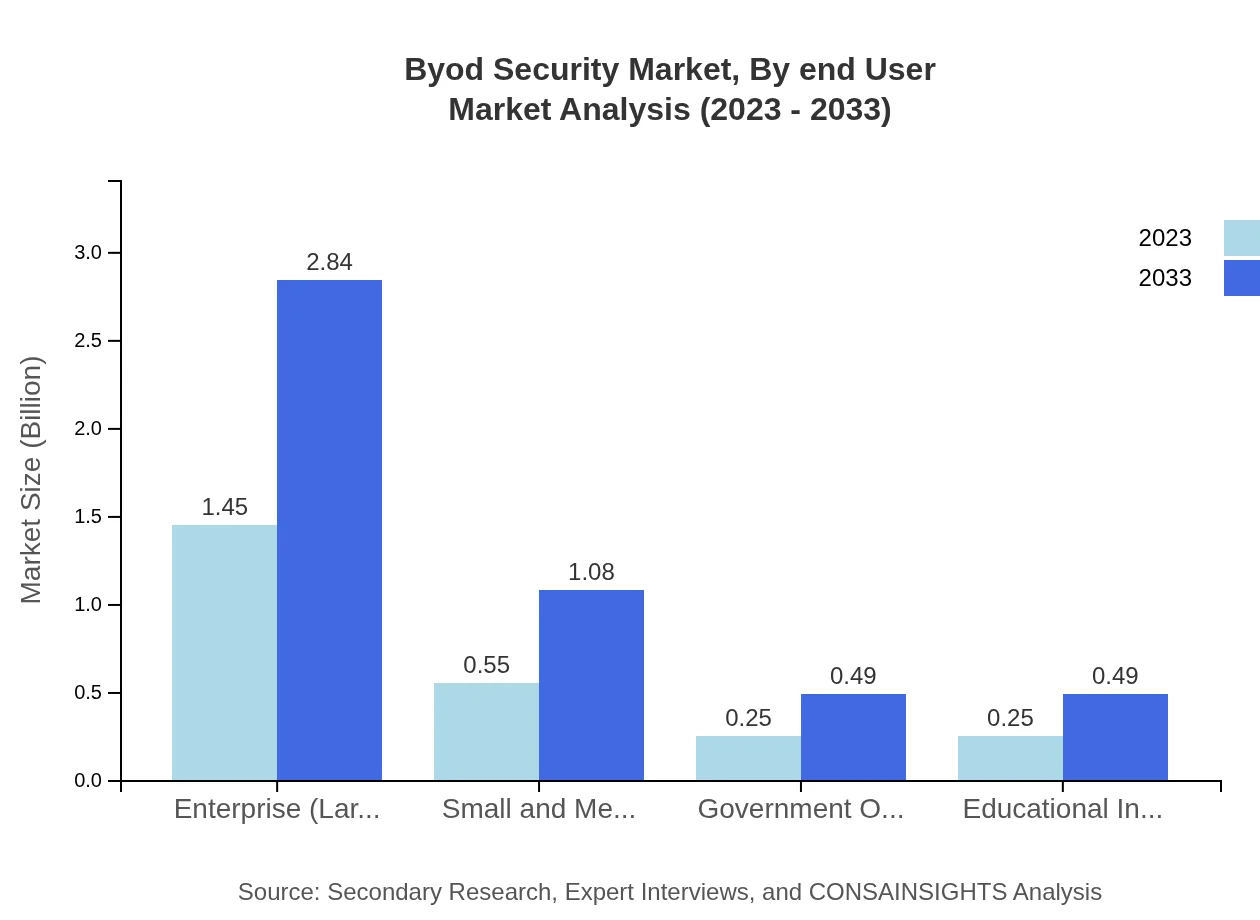
Byod Security Market Analysis By End User
The end-user segment is dominated by Large Enterprises, projected to expand from $1.45 billion in 2023 to $2.84 billion by 2033 while maintaining a share of 57.84%. Small and Medium Businesses are gaining traction, anticipated to grow from $0.55 billion to $1.08 billion, while Government Organizations and Educational Institutions will also increase to $0.49 billion. The Healthcare sector is critical, expected to grow from $1.09 billion to $2.14 billion, illustrating the sector's emphasis on patient data protection.
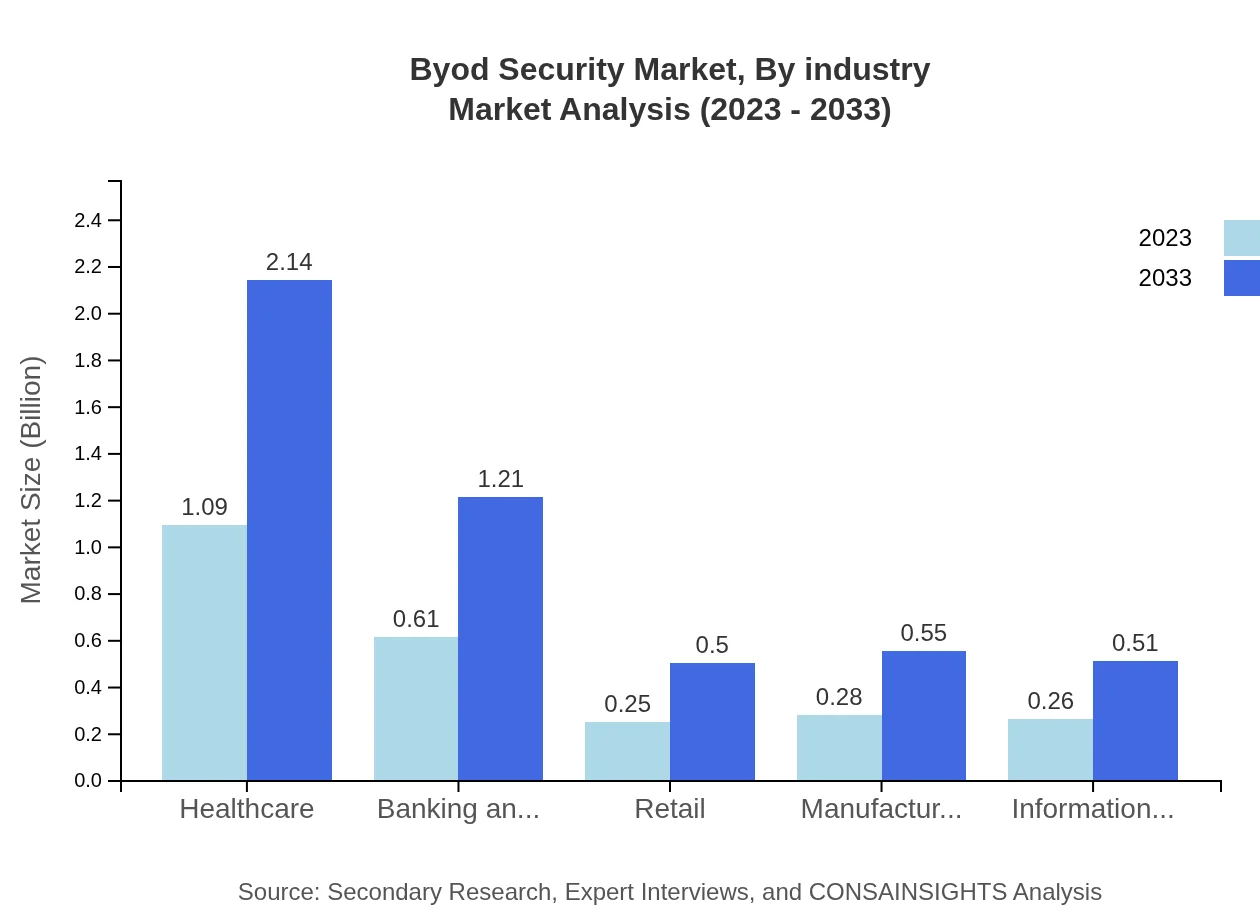
Byod Security Market Analysis By Industry
BYOD Security solutions are crucial across various industries. The Healthcare segment leads with a market share of 43.65%, expected to grow from $1.09 billion in 2023 to $2.14 billion by 2033, driven by stringent compliance requirements. The Banking and Financial Services sector follows, projected to expand from $0.61 billion to $1.21 billion. Retail, Manufacturing, and IT sectors show promising growth trends as organizations aim to secure customer and corporate data.
BYOD Security Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in BYOD Security Industry
Cisco Systems, Inc.:
Cisco provides comprehensive security solutions tailored for BYOD environments, leveraging its advanced network technology to enhance mobile security across enterprises.Palo Alto Networks, Inc.:
Palo Alto Networks specializes in multi-cloud security, offering next-generation firewall solutions and AI-driven security tools to ensure robust protection of BYOD applications.VMware, Inc.:
VMware offers a range of security solutions focusing on endpoint protection and management, pivotal for secure BYOD implementation within organizations.IBM Security:
IBM Security provides analytics-driven security solutions designed to mitigate risks associated with BYOD policies, promoting a secure digital workspace.We're grateful to work with incredible clients.









FAQs
What is the market size of BYOD Security?
The global BYOD Security market is valued at $2.5 billion in 2023, with a projected Compound Annual Growth Rate (CAGR) of 6.8% over the next decade, indicating significant growth potential.
What are the key market players or companies in the BYOD Security industry?
Major players in the BYOD Security industry include companies like IBM, MobileIron, VMware, Citrix, and Cisco. These firms are pivotal in developing robust solutions that address the security challenges associated with BYOD policies.
What are the primary factors driving the growth in the BYOD Security industry?
The BYOD Security market is driven by increasing mobile device usage, higher flexible working arrangements, rising security breaches, and the growing need for data protection in enterprises, prompting investments in comprehensive security solutions.
Which region is the fastest Growing in the BYOD Security?
North America is the fastest-growing region in the BYOD Security market, with a market size of $0.89 billion in 2023, expected to reach $1.74 billion by 2033, showcasing robust adoption of BYOD policies and security measures.
Does ConsaInsights provide customized market report data for the BYOD Security industry?
Yes, ConsaInsights offers customized market report data tailored to specific needs in the BYOD Security industry, ensuring organizations have access to relevant, actionable insights for decision-making.
What deliverables can I expect from this BYOD Security market research project?
Deliverables include a comprehensive report outlining market trends, player analysis, regional data, growth forecasts, and insights into market segments, specifically tailored for stakeholders in the BYOD Security industry.
What are the market trends of BYOD Security?
Current trends in the BYOD Security market include increased adoption of cloud-based solutions, integration of AI for threat detection, and a shift towards zero-trust security frameworks among enterprises, reflecting evolving security needs.