Cloud Endpoint Protection Market Report
Published Date: 31 January 2026 | Report Code: cloud-endpoint-protection
Cloud Endpoint Protection Market Size, Share, Industry Trends and Forecast to 2033
This report provides an in-depth analysis of the Cloud Endpoint Protection market, including trends, forecasts, and insights from 2023 to 2033. It covers market size, segments, region-specific data, and key players driving the industry's growth.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
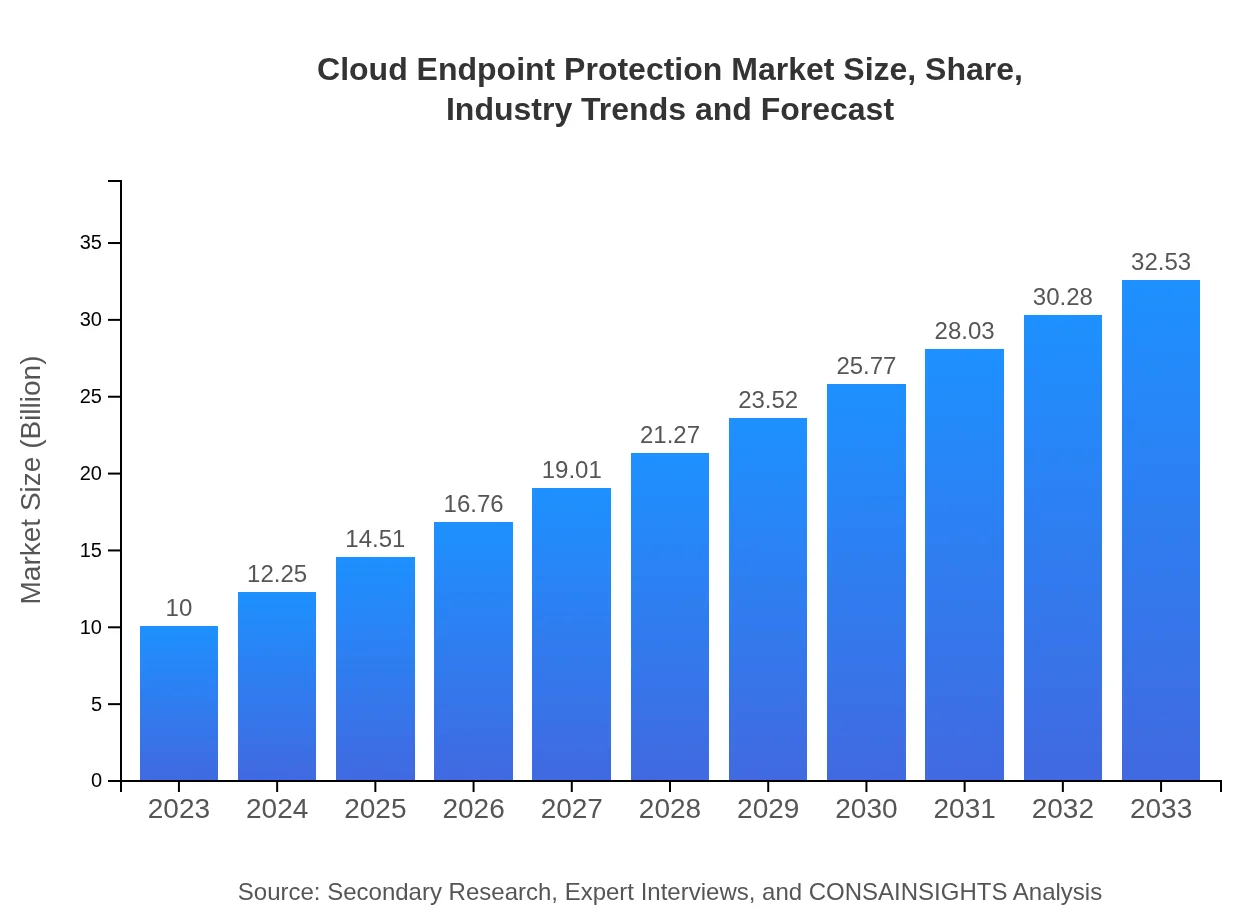
| 2023 Market Size | $10.00 Billion |
| CAGR (2023-2033) | 12% |
| 2033 Market Size | $32.53 Billion |
| Top Companies | Symantec Corporation, McAfee LLC, Trend Micro Incorporated, CrowdStrike, Palo Alto Networks |
| Last Modified Date | 31 January 2026 |
Cloud Endpoint Protection Market Overview
Customize Cloud Endpoint Protection Market Report market research report
- ✔ Get in-depth analysis of Cloud Endpoint Protection market size, growth, and forecasts.
- ✔ Understand Cloud Endpoint Protection's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Cloud Endpoint Protection
What is the Market Size & CAGR of Cloud Endpoint Protection market in 2023?
Cloud Endpoint Protection Industry Analysis
Cloud Endpoint Protection Market Segmentation and Scope
Tell us your focus area and get a customized research report.
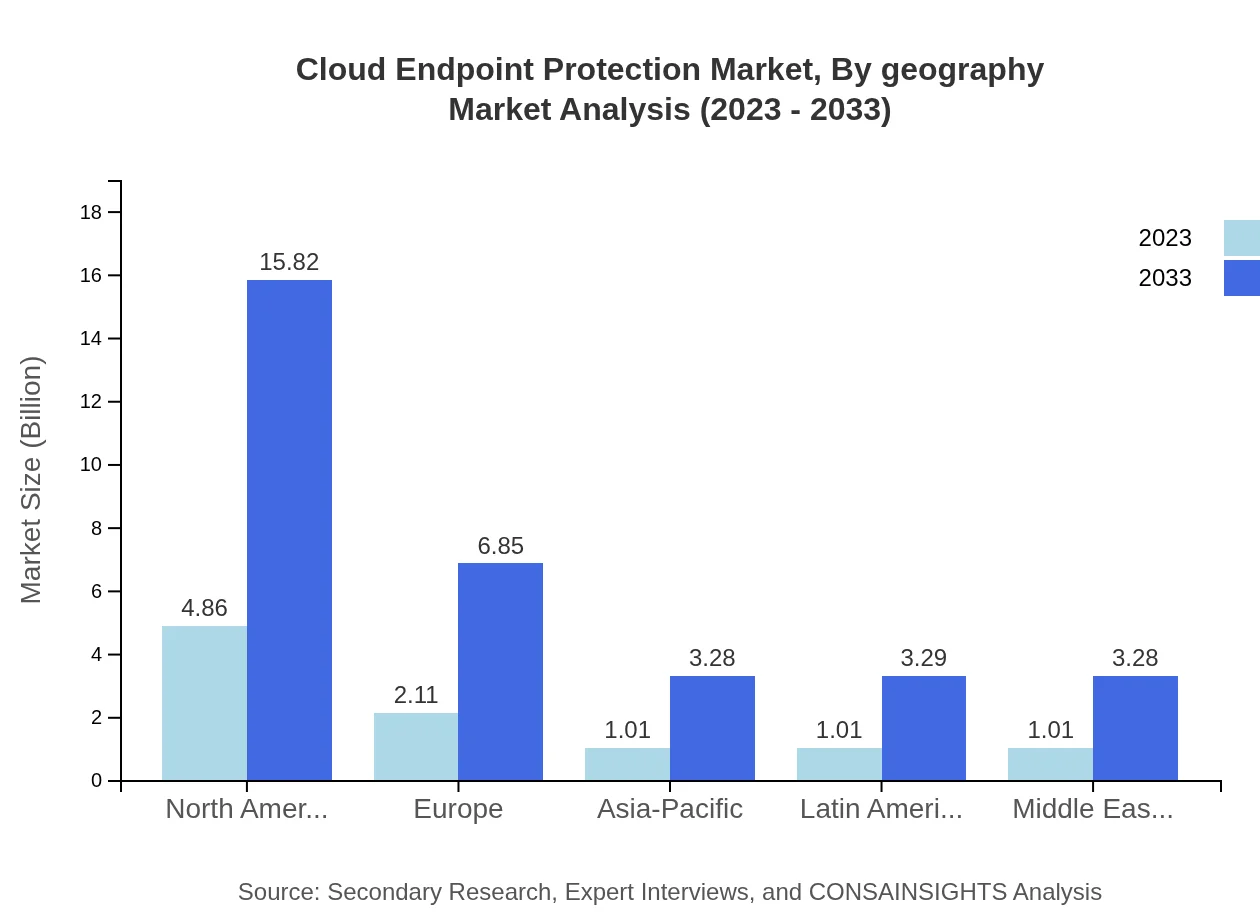
Cloud Endpoint Protection Market Analysis Report by Region
Europe Cloud Endpoint Protection Market Report:
Europe demonstrates significant growth potential, with the market projected to increase from $2.51 billion in 2023 to $8.17 billion by 2033. The European Union's GDPR and other regulations enhance the necessity for endpoint protection, encouraging enterprises to invest in comprehensive security frameworks.Asia Pacific Cloud Endpoint Protection Market Report:
In the Asia-Pacific region, the Cloud Endpoint Protection market is projected to grow from $2.17 billion in 2023 to $7.06 billion by 2033. Countries such as Japan, China, and India are witnessing increased investments in cybersecurity owing to rising incidences of cybercrime and proactive government regulations promoting digital security.North America Cloud Endpoint Protection Market Report:
North America leads the global market, with a substantial market size expected to expand from $3.80 billion in 2023 to $12.37 billion by 2033. The U.S. continues to be the primary driver, supported by advanced technological infrastructure and a focus on stringent cybersecurity measures across various sectors.South America Cloud Endpoint Protection Market Report:
South America is also experiencing growth, with the market estimated at $0.69 billion in 2023 and expected to reach $2.24 billion by 2033. As businesses increasingly digitize operations, the demand for robust endpoint security measures is rising significantly in this region.Middle East & Africa Cloud Endpoint Protection Market Report:
The Middle East and Africa market is expected to grow from $0.83 billion in 2023 to $2.69 billion by 2033. The increasing mobile workforce and rising incidents of cyber threats are creating a heightened demand for effective endpoint protection solutions in both private and public sectors.Tell us your focus area and get a customized research report.
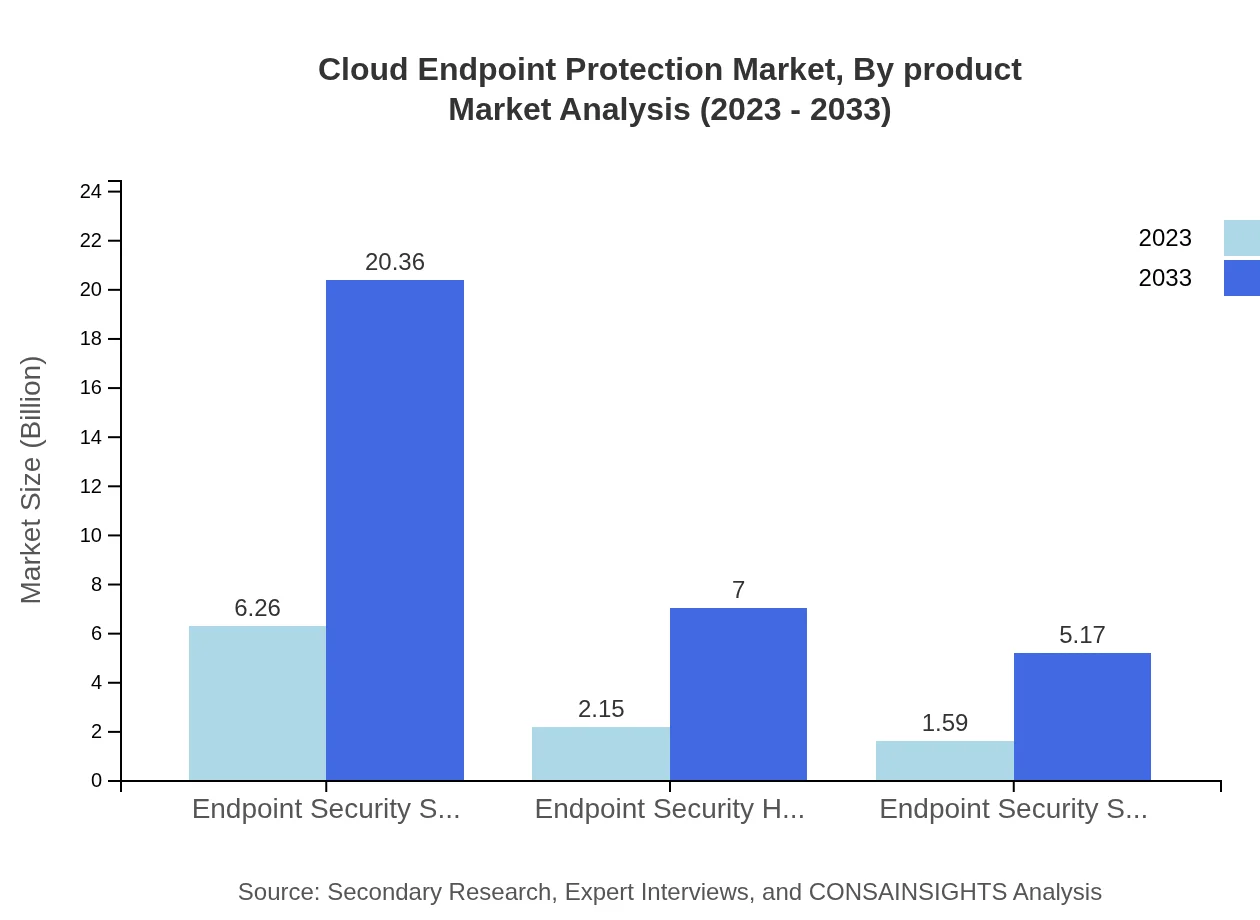
Cloud Endpoint Protection Market Analysis By Product
The Cloud Endpoint Protection market is primarily segmented into three product types: endpoint security software, endpoint security hardware, and endpoint security services. In 2023, the software segment captures the largest share, valued at $6.26 billion, and is expected to grow at a substantial CAGR. Hardware solutions are also gaining traction, while managed services are being increasingly outsourced by companies seeking robust security solutions without dedicating significant in-house resources.
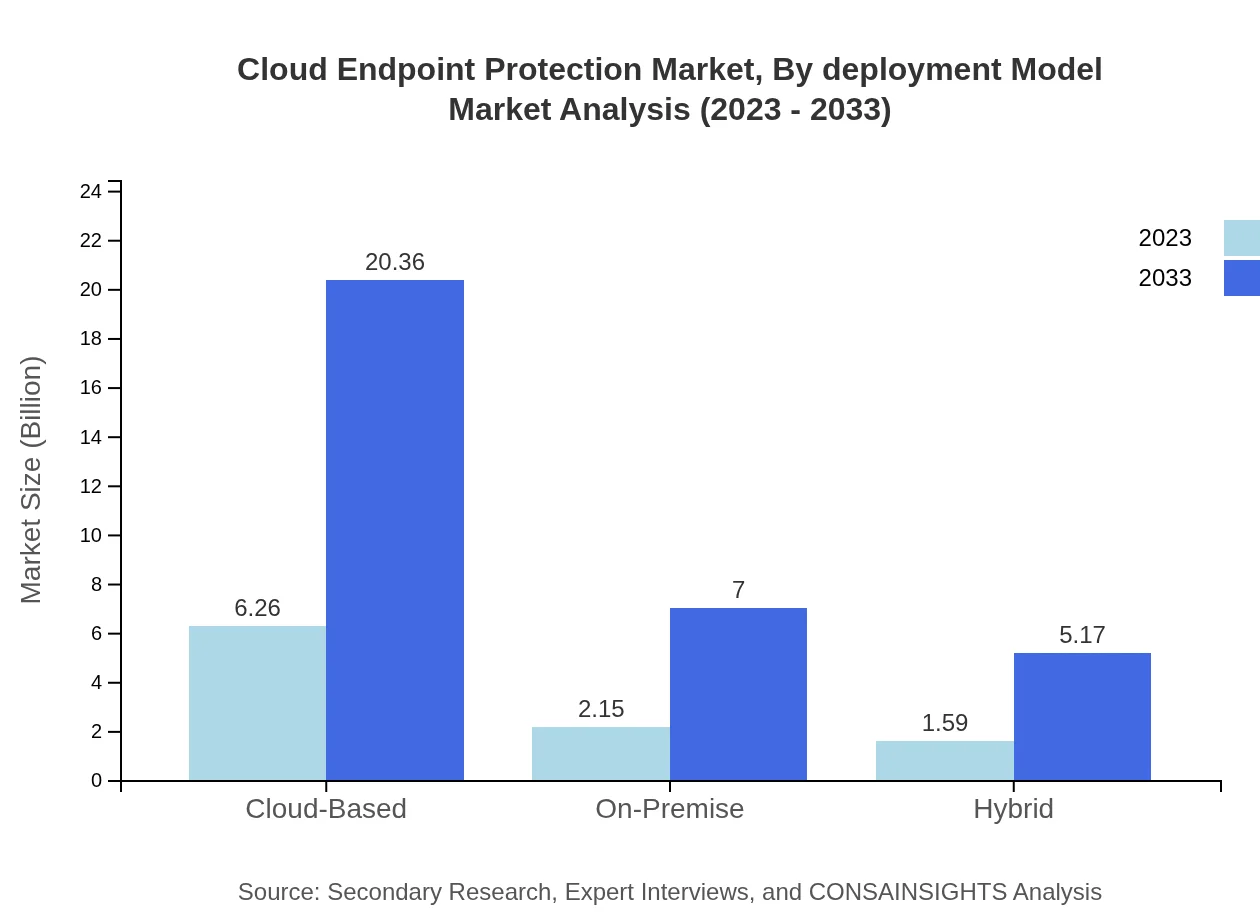
Cloud Endpoint Protection Market Analysis By Deployment Model
Deployment models for Cloud Endpoint Protection include cloud-based, on-premise, and hybrid solutions. The cloud-based model dominates the market, anticipated to grow from $6.26 billion in 2023 to $20.36 billion by 2033. Organizations favor cloud solutions due to their scalability, ease of management, and accessibility.
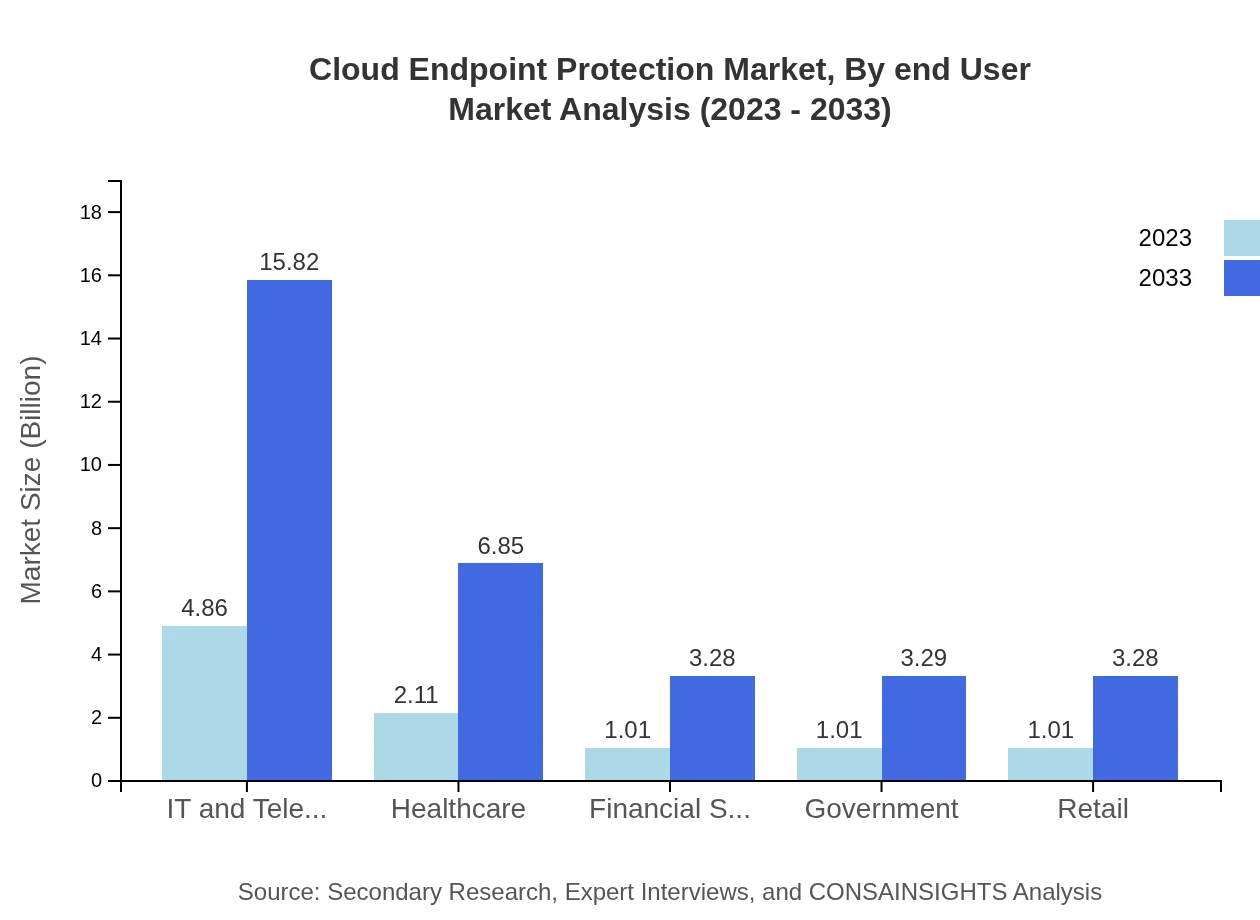
Cloud Endpoint Protection Market Analysis By End User
End-user segmentation includes IT and telecommunications, healthcare, financial services, government, and retail sectors. IT and telecommunications generate the largest revenue, followed by healthcare and financial services. Growing awareness of data breaches across these industries is spurring investment in endpoint protection solutions to safeguard sensitive data.
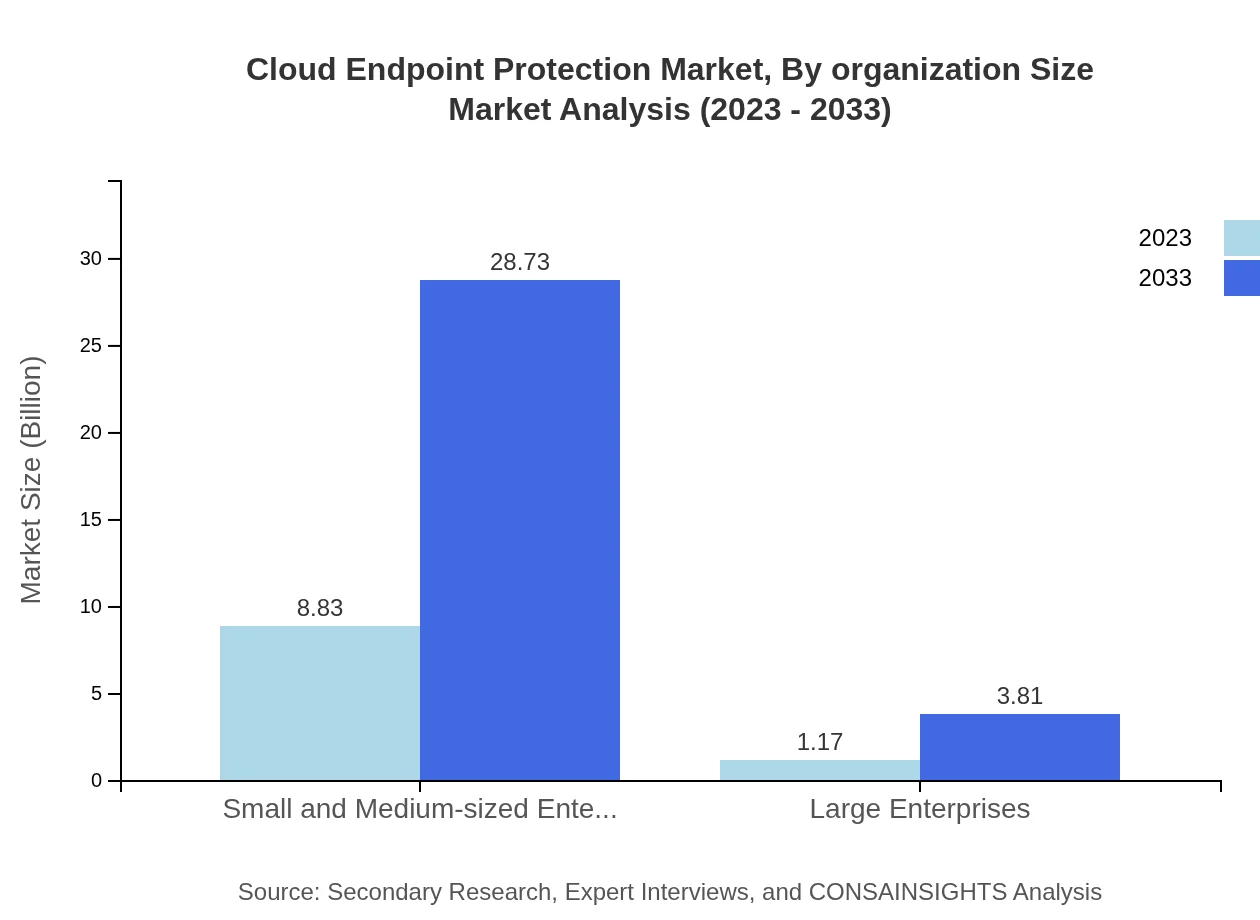
Cloud Endpoint Protection Market Analysis By Organization Size
Small and medium-sized enterprises (SMEs) account for the majority of the market, valued at $8.83 billion in 2023, and are projected to grow considerably as they increasingly prioritize cybersecurity. On the other hand, large enterprises show steady growth in their spending towards advanced endpoint protection technologies.
Cloud Endpoint Protection Market Analysis By Geography
Geographically, the North American market represents the highest revenue share, driven by extensive cybersecurity investments. Europe follows closely due to regulatory pressures, with Asia-Pacific showing rapid growth potential owing to increasing digitalization and cyber threats.
Cloud Endpoint Protection Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Cloud Endpoint Protection Industry
Symantec Corporation:
A pioneer in cybersecurity, Symantec offers comprehensive Cloud Endpoint Protection solutions powered by advanced threat intelligence and cutting-edge technology.McAfee LLC:
McAfee provides innovative cloud protection services with a focus on integrating machine learning and automation to enhance endpoint security.Trend Micro Incorporated:
Trend Micro specializes in endpoint security, delivering robust cloud protection solutions that cater to diverse industries and ensure compliance.CrowdStrike:
Known for its cloud-native approach to cybersecurity, CrowdStrike offers advanced threat detection powered by artificial intelligence for proactive endpoint protection.Palo Alto Networks:
Palo Alto Networks leads in providing cloud-based security solutions focused on endpoint protection and real-time threat prevention strategies.We're grateful to work with incredible clients.









FAQs
What is the market size of cloud endpoint protection?
The global cloud endpoint protection market is valued at around $10 billion in 2023, with a projected CAGR of 12% through 2033. This significant growth is expected to enhance security measures for endpoint devices worldwide.
What are the key market players or companies in this cloud endpoint protection industry?
Major players in the cloud endpoint protection market include industry giants like CrowdStrike, McAfee, Symantec, and Trend Micro. These companies are recognized for their innovative solutions and contributions to enhancing cybersecurity across various sectors.
What are the primary factors driving the growth in the cloud endpoint protection industry?
Key drivers of growth in the cloud endpoint protection market include increasing cyber threats, regulatory compliance requirements, and the rise in remote working environments. Organizations are investing heavily in robust security solutions to safeguard their data and infrastructure.
Which region is the fastest Growing in the cloud endpoint protection?
The North American region is projected to be the fastest-growing market for cloud endpoint protection, expanding from $3.80 billion in 2023 to $12.37 billion by 2033. Growing cybersecurity threats and technological advancements are key factors fueling this growth.
Does ConsaInsights provide customized market report data for the cloud endpoint protection industry?
Yes, ConsaInsights offers customized market reports tailored to the specific needs of clients in the cloud endpoint protection industry. This includes detailed insights into trends, market sizing, and competitive analysis.
What deliverables can I expect from this cloud endpoint protection market research project?
Clients can expect comprehensive market research deliverables such as detailed reports, data analytics, and actionable insights. This includes market sizing, growth forecasts, and competitive landscape overviews essential for strategic planning.
What are the market trends of cloud endpoint protection?
Notable trends in the cloud endpoint protection market include the shift towards cloud-based solutions, increasing adoption by small and medium-sized enterprises, and a focus on integrating artificial intelligence in cybersecurity measures.