Cloud Intrusion Protection Software Market Report
Published Date: 31 January 2026 | Report Code: cloud-intrusion-protection-software
Cloud Intrusion Protection Software Market Size, Share, Industry Trends and Forecast to 2033
This report provides an in-depth analysis of the Cloud Intrusion Protection Software market, highlighting key trends, market size, and forecasts from 2023 to 2033. It includes insights into market segmentation, regional analysis, and leading market players.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
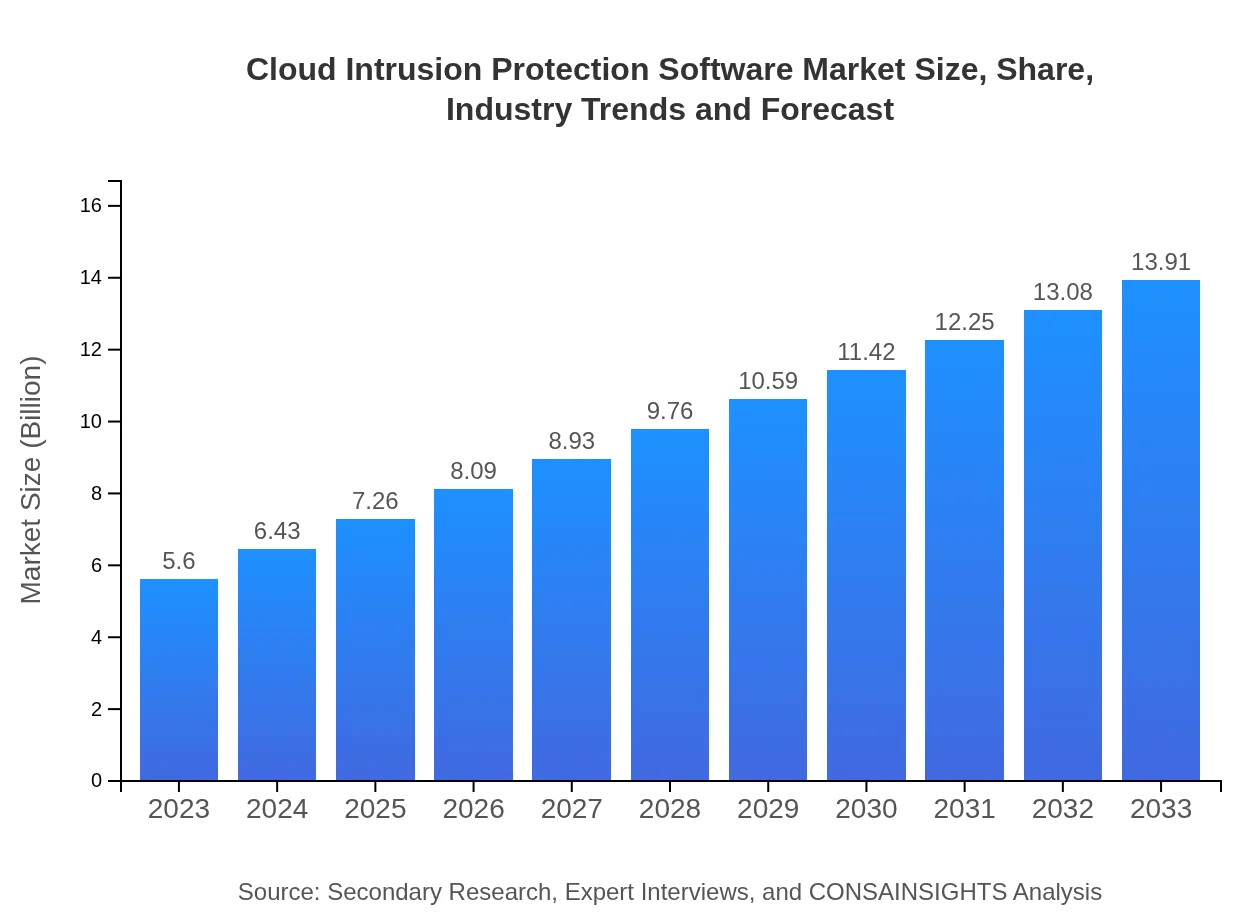
| 2023 Market Size | $5.60 Billion |
| CAGR (2023-2033) | 9.2% |
| 2033 Market Size | $13.91 Billion |
| Top Companies | Cisco Systems, Inc., Palo Alto Networks, Inc., Check Point Software Technologies Ltd., CrowdStrike Holdings, Inc. |
| Last Modified Date | 31 January 2026 |
Cloud Intrusion Protection Software Market Overview
Customize Cloud Intrusion Protection Software Market Report market research report
- ✔ Get in-depth analysis of Cloud Intrusion Protection Software market size, growth, and forecasts.
- ✔ Understand Cloud Intrusion Protection Software's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Cloud Intrusion Protection Software
What is the Market Size & CAGR of Cloud Intrusion Protection Software market in 2023?
Cloud Intrusion Protection Software Industry Analysis
Cloud Intrusion Protection Software Market Segmentation and Scope
Tell us your focus area and get a customized research report.
Cloud Intrusion Protection Software Market Analysis Report by Region
Europe Cloud Intrusion Protection Software Market Report:
The European market size is estimated at $1.62 billion in 2023 and is set to surge to $4.02 billion by 2033. Regulatory frameworks and increased focus on data protection standards are key drivers for market growth.Asia Pacific Cloud Intrusion Protection Software Market Report:
In the Asia Pacific region, the market size stood at $1.15 billion in 2023, projected to reach $2.87 billion by 2033. This growth is driven by the rapid digitization initiatives and increasing investments in cloud infrastructure, particularly in countries like India and China.North America Cloud Intrusion Protection Software Market Report:
North America leads the market with a valuation of $1.99 billion in 2023, projected to reach $4.94 billion by 2033. The presence of major technology firms and high cybersecurity spending make this region a critical area for market developments.South America Cloud Intrusion Protection Software Market Report:
South America currently has a market value of $0.41 billion in 2023, expected to grow to $1.01 billion by 2033. The rise in cloud adoption across various sectors, coupled with the growing awareness of cybersecurity, is contributing to this expansion.Middle East & Africa Cloud Intrusion Protection Software Market Report:
In the Middle East and Africa, the market is valued at $0.43 billion in 2023, with forecasts indicating a rise to $1.07 billion by 2033. The region's growing digital transformation efforts are prompting more investments in cloud security solutions.Tell us your focus area and get a customized research report.
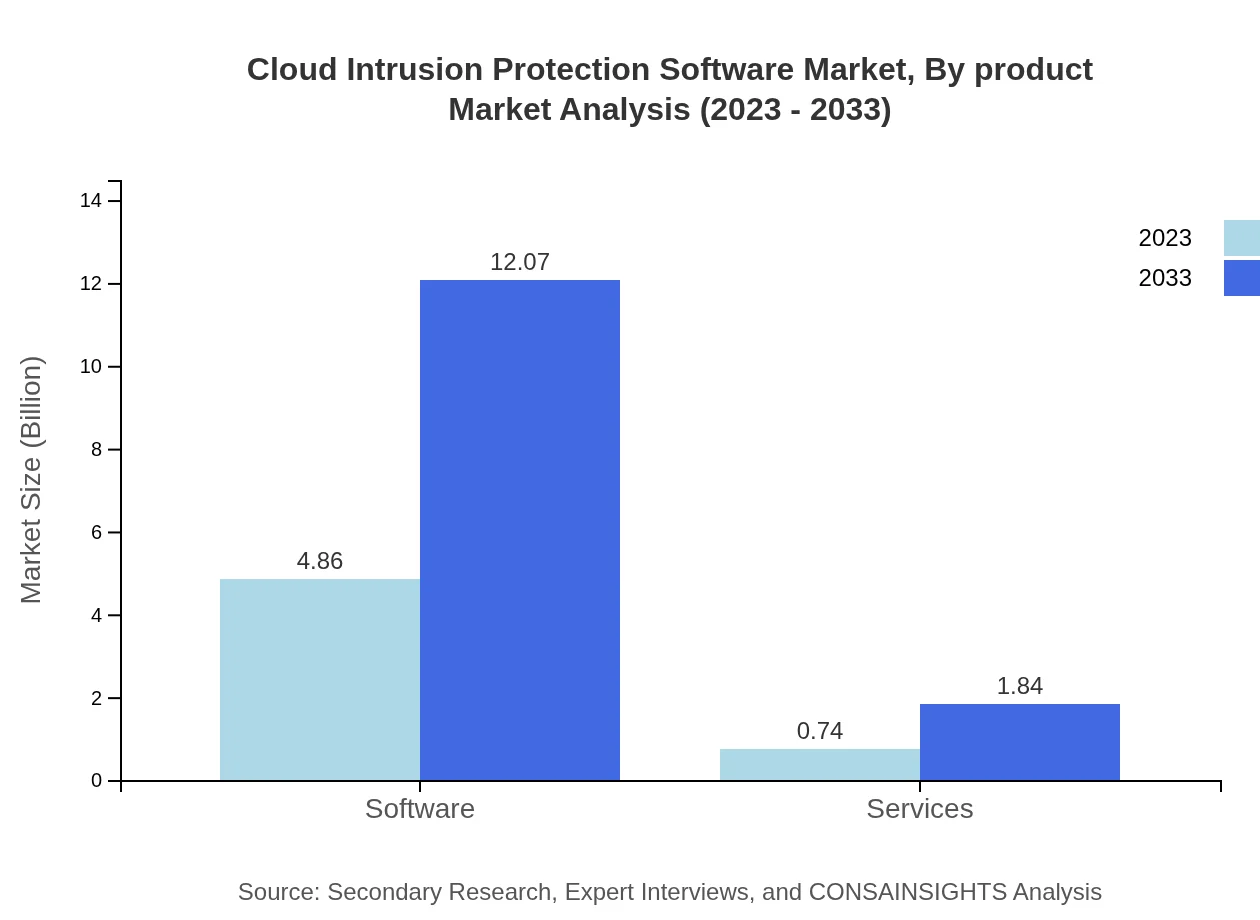
Cloud Intrusion Protection Software Market Analysis By Product
The product segment analysis indicates that Software dominates the market with a projected size growing from $4.86 billion in 2023 to $12.07 billion by 2033, claiming 86.77% market share. Services, while smaller at $0.74 billion in 2023, are expected to reach $1.84 billion, covering 13.23% of the market.
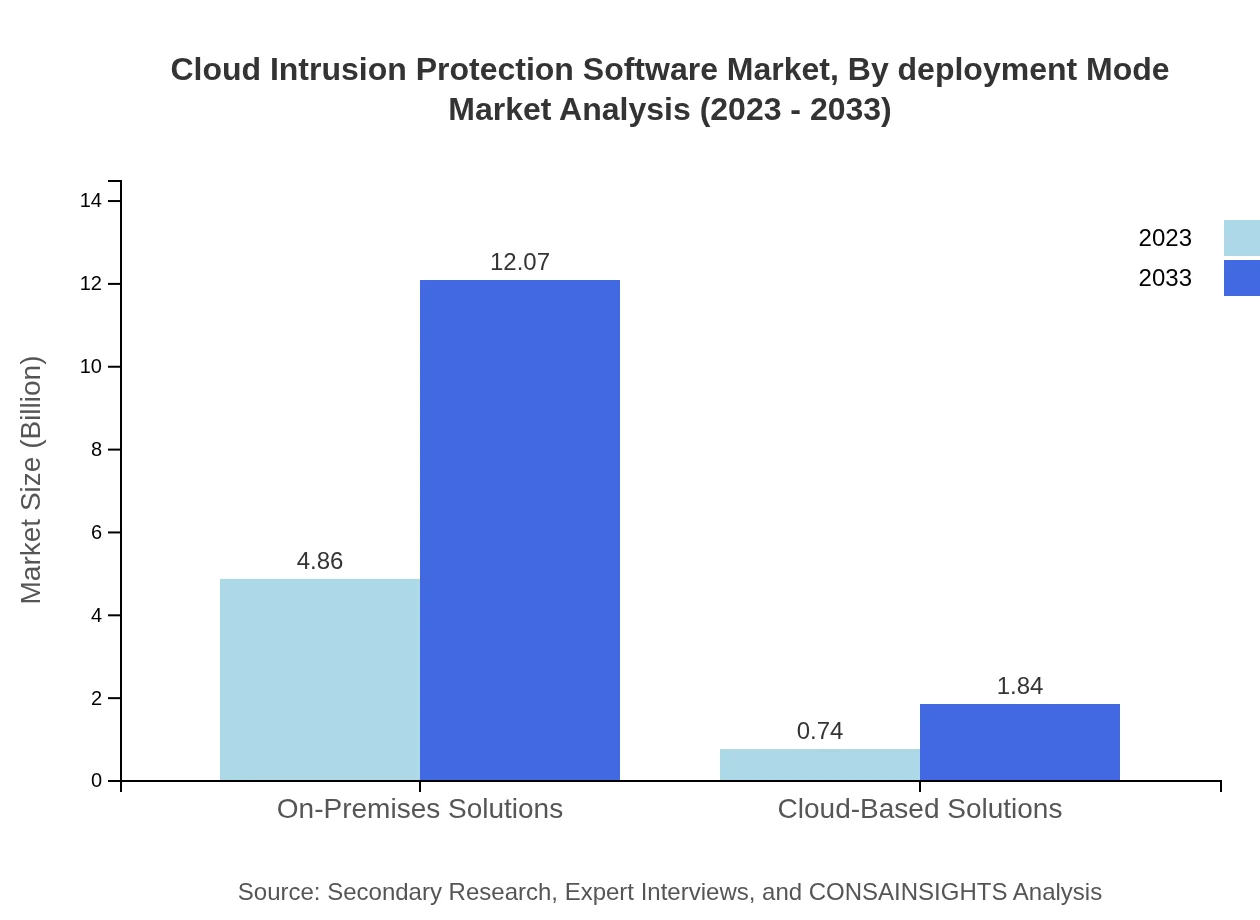
Cloud Intrusion Protection Software Market Analysis By Deployment Mode
The On-Premises Solutions segment showcases a strong performance, valued at $4.86 billion in 2023, with a likely climb to $12.07 billion by 2033, securing a robust market share. In contrast, Cloud-Based Solutions are significantly lower at $0.74 billion, reaching $1.84 billion over the same period.
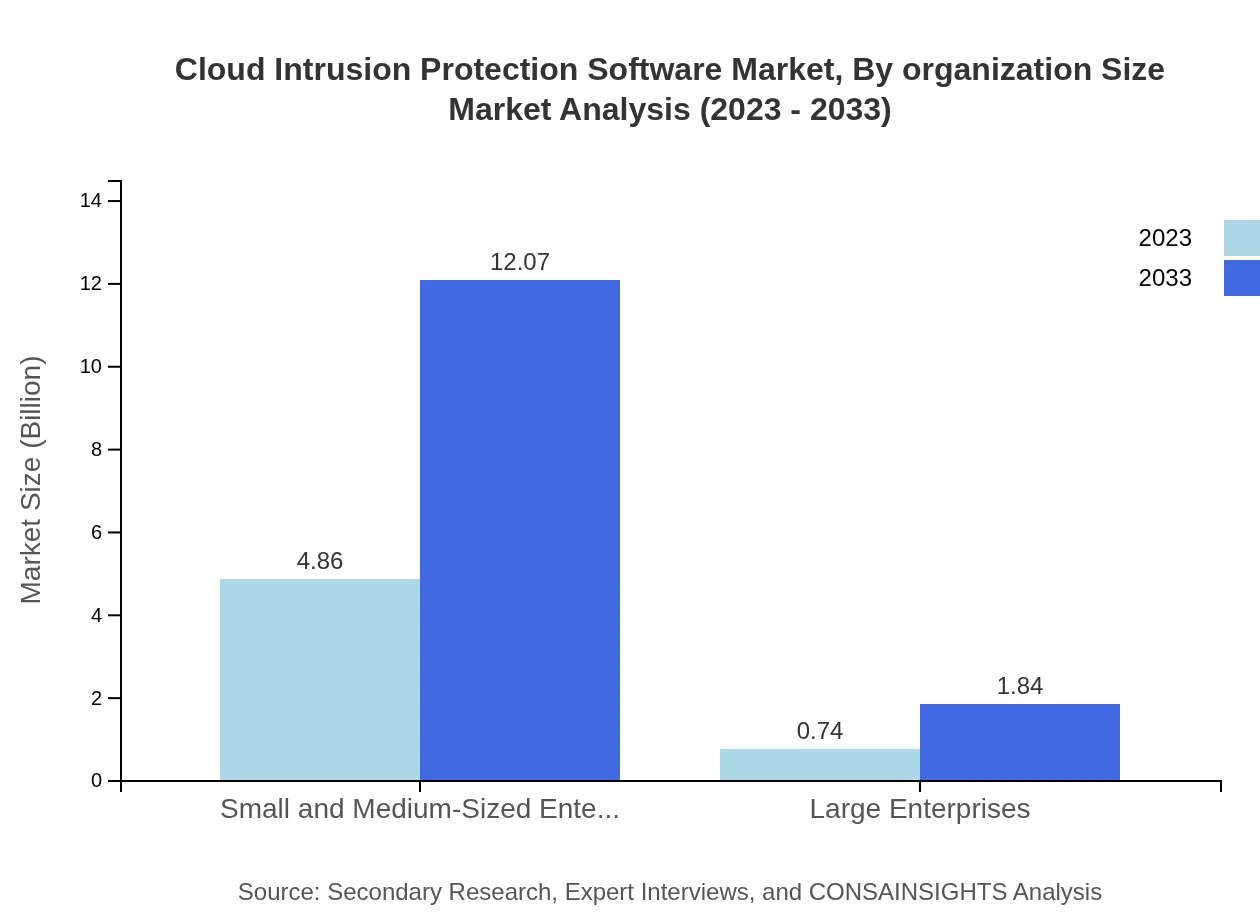
Cloud Intrusion Protection Software Market Analysis By Organization Size
Small and Medium-Sized Enterprises (SMEs) are predominantly using Cloud Intrusion Protection Software, with market size poised to increase from $4.86 billion in 2023 to $12.07 billion by 2033. Large Enterprises show a smaller growth potential from $0.74 billion to $1.84 billion.
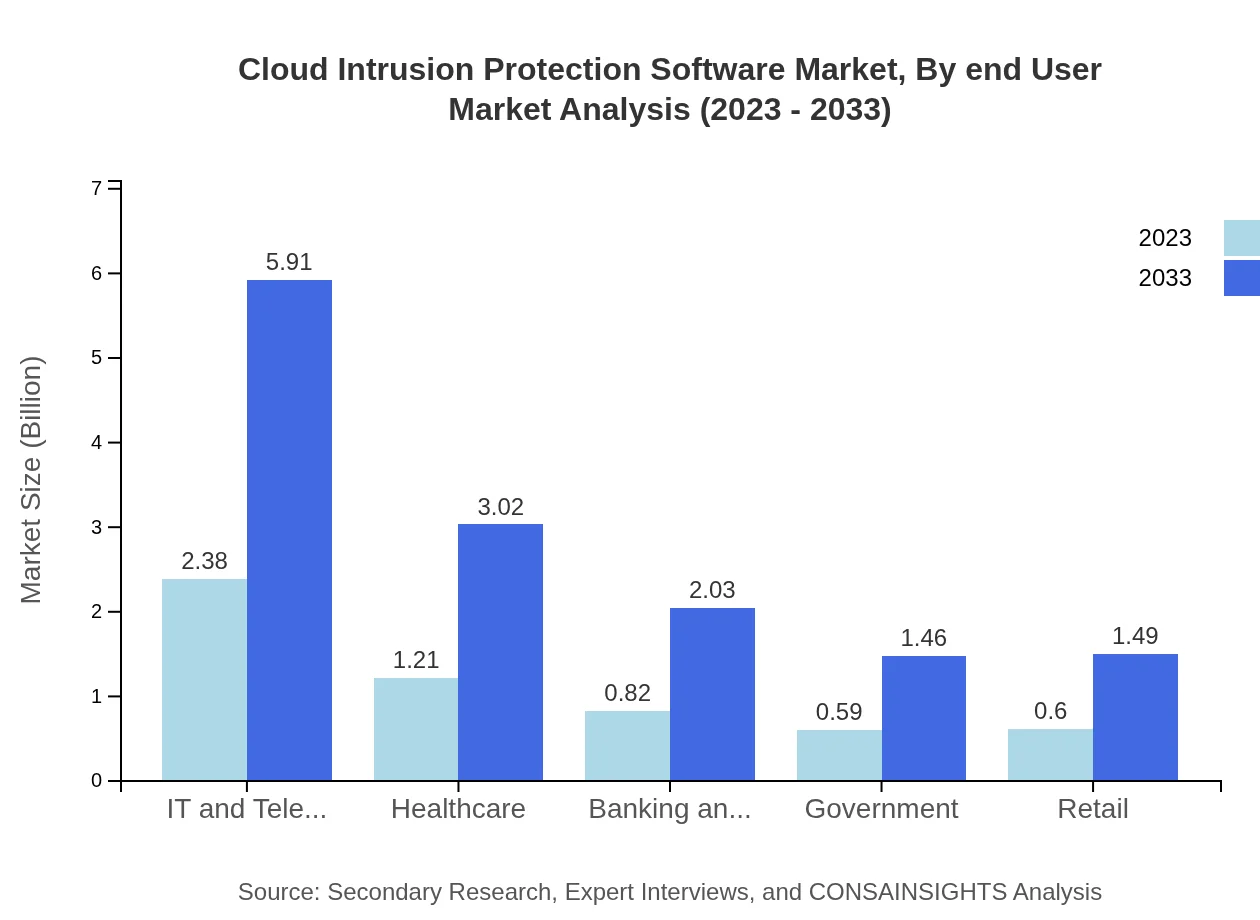
Cloud Intrusion Protection Software Market Analysis By End User
End-user analysis reveals significant adoption in IT and Telecom ($2.38 billion current size growing to $5.91 billion), followed by Healthcare and Banking sectors showing increases in demand, with Healthcare growing from $1.21 billion to $3.02 billion and Banking from $0.82 billion to $2.03 billion by 2033.
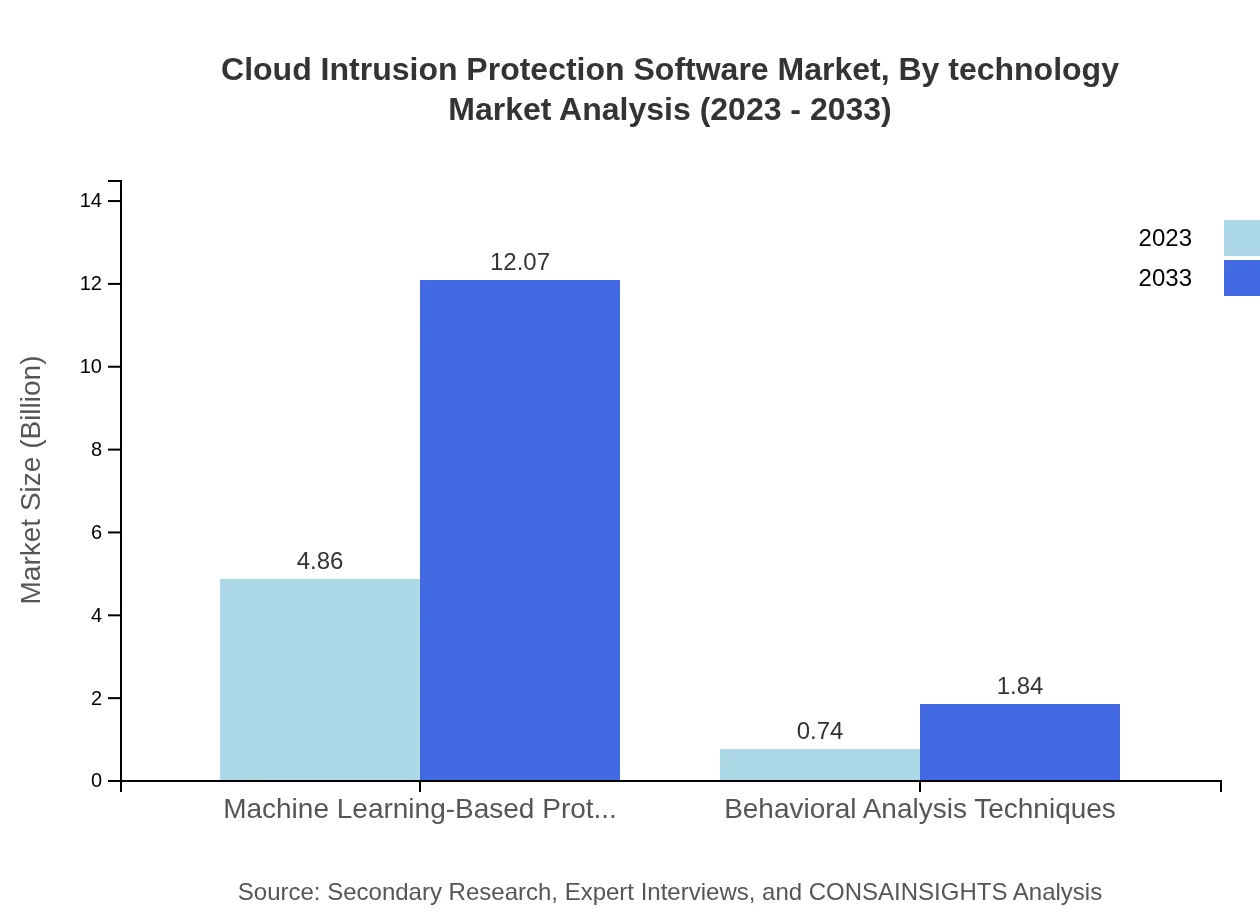
Cloud Intrusion Protection Software Market Analysis By Technology
Machine Learning-Based Protection shows a dominant market presence of $4.86 billion in 2023 rising to $12.07 billion by 2033, while Behavioral Analysis Techniques grow from $0.74 billion to $1.84 billion over the same period.
Cloud Intrusion Protection Software Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Cloud Intrusion Protection Software Industry
Cisco Systems, Inc.:
Cisco offers a wide range of cloud security solutions that protect against intrusions and data breaches, leveraging advanced threat intelligence.Palo Alto Networks, Inc.:
Palo Alto specializes in next-gen firewall technologies with integrated intrusion detection systems that are highly effective in cloud environments.Check Point Software Technologies Ltd.:
Check Point provides comprehensive cybersecurity solutions that offer advanced intrusion prevention capabilities tailored for cloud infrastructures.CrowdStrike Holdings, Inc.:
CrowdStrike leads the market with its proactive approach to cloud security, utilizing AI-driven mechanisms to thwart potential intrusions.We're grateful to work with incredible clients.









FAQs
What is the market size of cloud Intrusion Protection Software?
The global market size for cloud intrusion protection software is expected to reach approximately $5.6 billion in 2023, with a projected CAGR of 9.2% moving forward to 2033.
What are the key market players or companies in this cloud Intrusion Protection Software industry?
Key players in the cloud intrusion protection software market include companies such as Symantec, McAfee, and Palo Alto Networks, which dominate through innovative products addressing security challenges in cloud environments.
What are the primary factors driving the growth in the cloud intrusion protection software industry?
The growth of the cloud intrusion protection software market is driven by increasing cyber threats, the rapid digitization of businesses, and a heightened focus on regulatory compliance and data privacy across various sectors.
Which region is the fastest Growing in the cloud intrusion protection software market?
Asia Pacific is the fastest-growing region in the cloud intrusion protection software market, projected to grow from $1.15 billion in 2023 to $2.87 billion by 2033, highlighting the region's expanding digital economy.
Does ConsaInsights provide customized market report data for the cloud intrusion protection software industry?
Yes, ConsaInsights offers customized market report data tailored to specific needs within the cloud intrusion protection software industry, addressing unique business requirements and strategic goals.
What deliverables can I expect from this cloud intrusion protection software market research project?
Deliverables from the cloud intrusion protection software market research project will include detailed reports on market size, growth projections, competitive analysis, and trends impacting the industry.
What are the market trends of cloud intrusion protection software?
Current trends in the cloud intrusion protection software market include a shift towards machine learning-based security solutions, increased adoption by SMEs, and a growing emphasis on behavioral analysis techniques to prevent breaches.