Cloud Workload Protection Market Report
Published Date: 31 January 2026 | Report Code: cloud-workload-protection
Cloud Workload Protection Market Size, Share, Industry Trends and Forecast to 2033
This report provides an extensive analysis of the Cloud Workload Protection market, detailing its size, growth potential, and the impact of various segments from 2023 to 2033. Insights into regional dynamics, market leaders, and future trends are also included.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
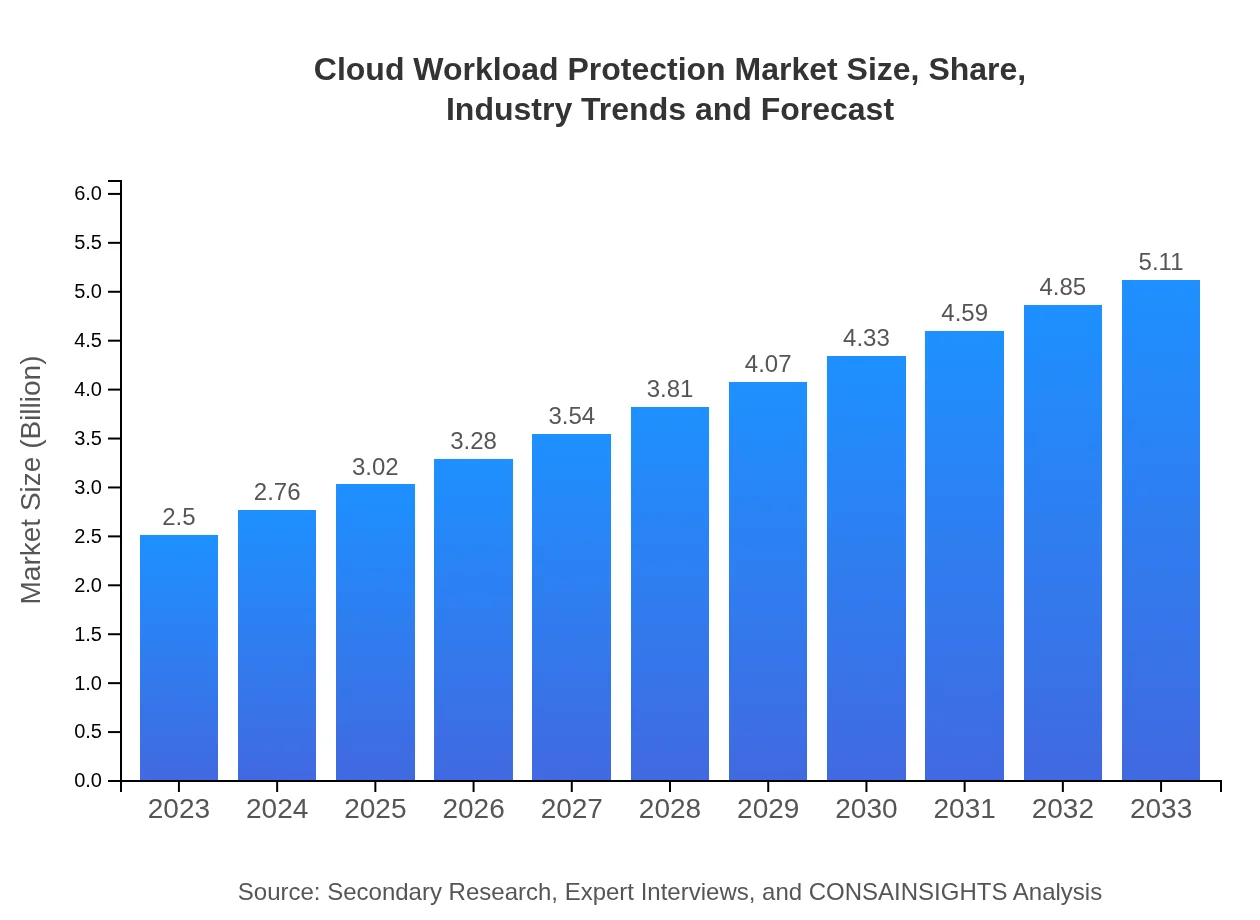
| 2023 Market Size | $2.50 Billion |
| CAGR (2023-2033) | 7.2% |
| 2033 Market Size | $5.11 Billion |
| Top Companies | Palo Alto Networks, McAfee, Symantec, Trend Micro, Zscaler |
| Last Modified Date | 31 January 2026 |
Cloud Workload Protection Market Overview
Customize Cloud Workload Protection Market Report market research report
- ✔ Get in-depth analysis of Cloud Workload Protection market size, growth, and forecasts.
- ✔ Understand Cloud Workload Protection's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Cloud Workload Protection
What is the Market Size & CAGR of Cloud Workload Protection market in 2023?
Cloud Workload Protection Industry Analysis
Cloud Workload Protection Market Segmentation and Scope
Tell us your focus area and get a customized research report.
Cloud Workload Protection Market Analysis Report by Region
Europe Cloud Workload Protection Market Report:
The European market is expected to grow from $0.76 billion in 2023 to $1.56 billion by 2033, supported by stringent data protection regulations like GDPR and a heightened focus on cloud security practices.Asia Pacific Cloud Workload Protection Market Report:
In 2023, the Cloud Workload Protection market in Asia Pacific is estimated to be valued at $0.46 billion, with expectations to reach $0.93 billion by 2033. The region shows strong growth potential attributed to rapid digital transformation, increasing IT security awareness, and government initiatives to promote cloud adoption.North America Cloud Workload Protection Market Report:
North America leads the Cloud Workload Protection market with a value of $0.94 billion in 2023, anticipated to grow significantly to $1.92 billion by 2033. The region's mature cloud service sector and high cybersecurity spending are key drivers.South America Cloud Workload Protection Market Report:
South America is projected to grow from $0.22 billion in 2023 to $0.45 billion by 2033. Although still in the early stages of cloud migration, burgeoning demand for cloud services will drive advancements in workload protection solutions.Middle East & Africa Cloud Workload Protection Market Report:
In the Middle East and Africa, the market is projected to grow from $0.12 billion in 2023 to $0.24 billion by 2033. The region is witnessing increased cloud adoption as organizations aim to modernize their operations.Tell us your focus area and get a customized research report.
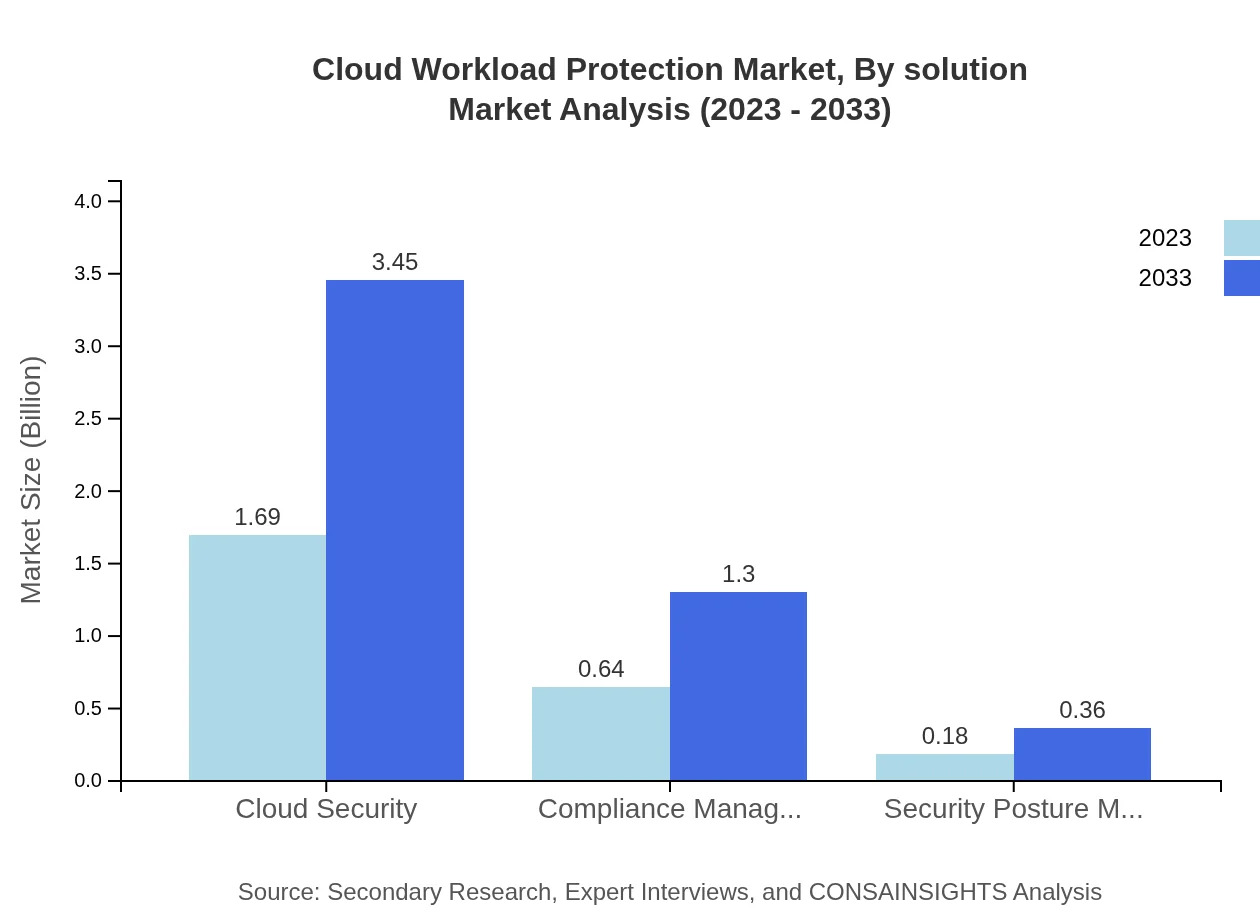
Cloud Workload Protection Market Analysis By Solution
The Cloud Workload Protection market, segmented by solution, indicates that Cloud Security maintains dominance with a market size of $1.69 billion in 2023, increasing to $3.45 billion by 2033. Compliance Management follows with a rise from $0.64 billion to $1.30 billion in the same period.
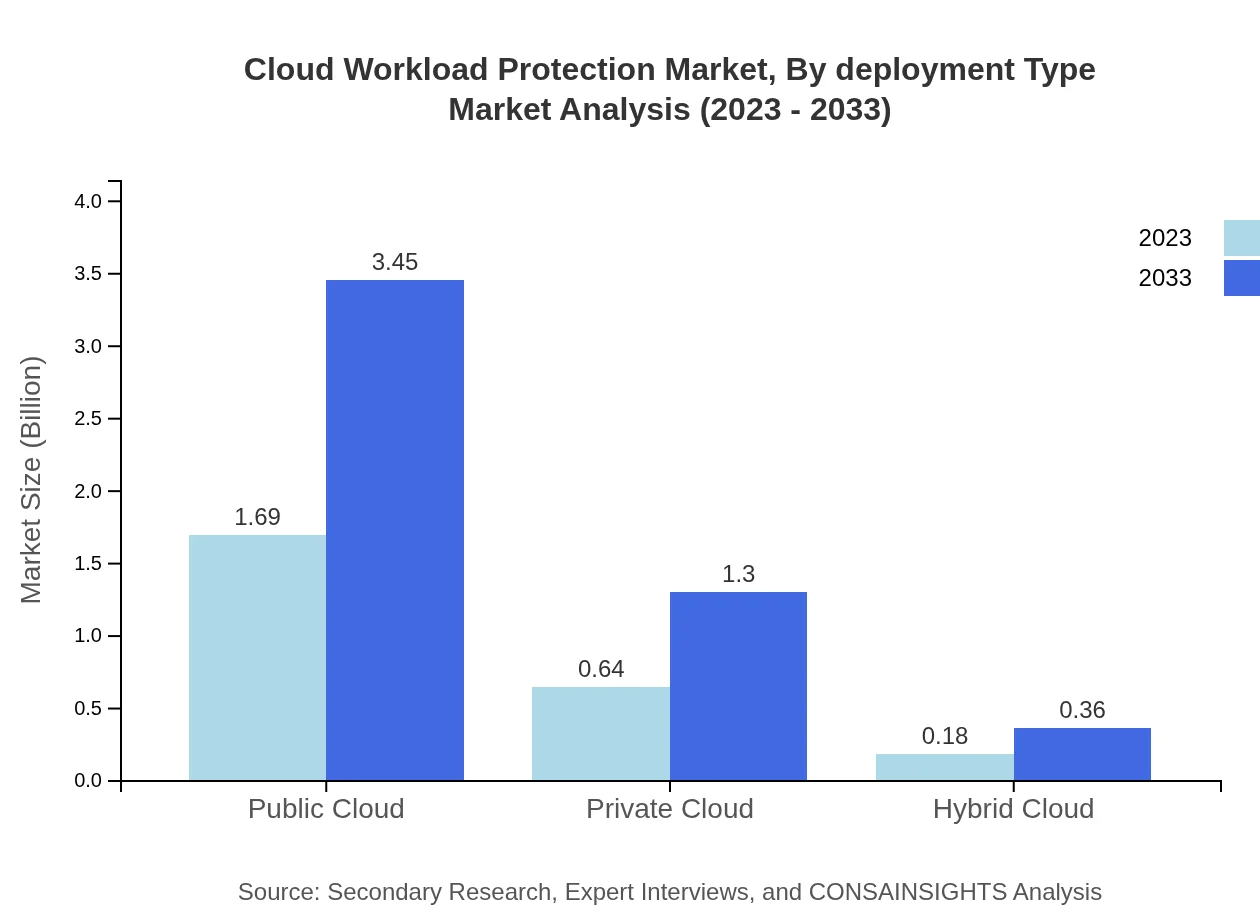
Cloud Workload Protection Market Analysis By Deployment Type
In terms of deployment, Public Cloud holds the largest share, increasing from $1.69 billion in 2023 to $3.45 billion by 2033. Hybrid Cloud and Private Cloud also show expected growth, illustrating the diversification in cloud strategies among organizations.
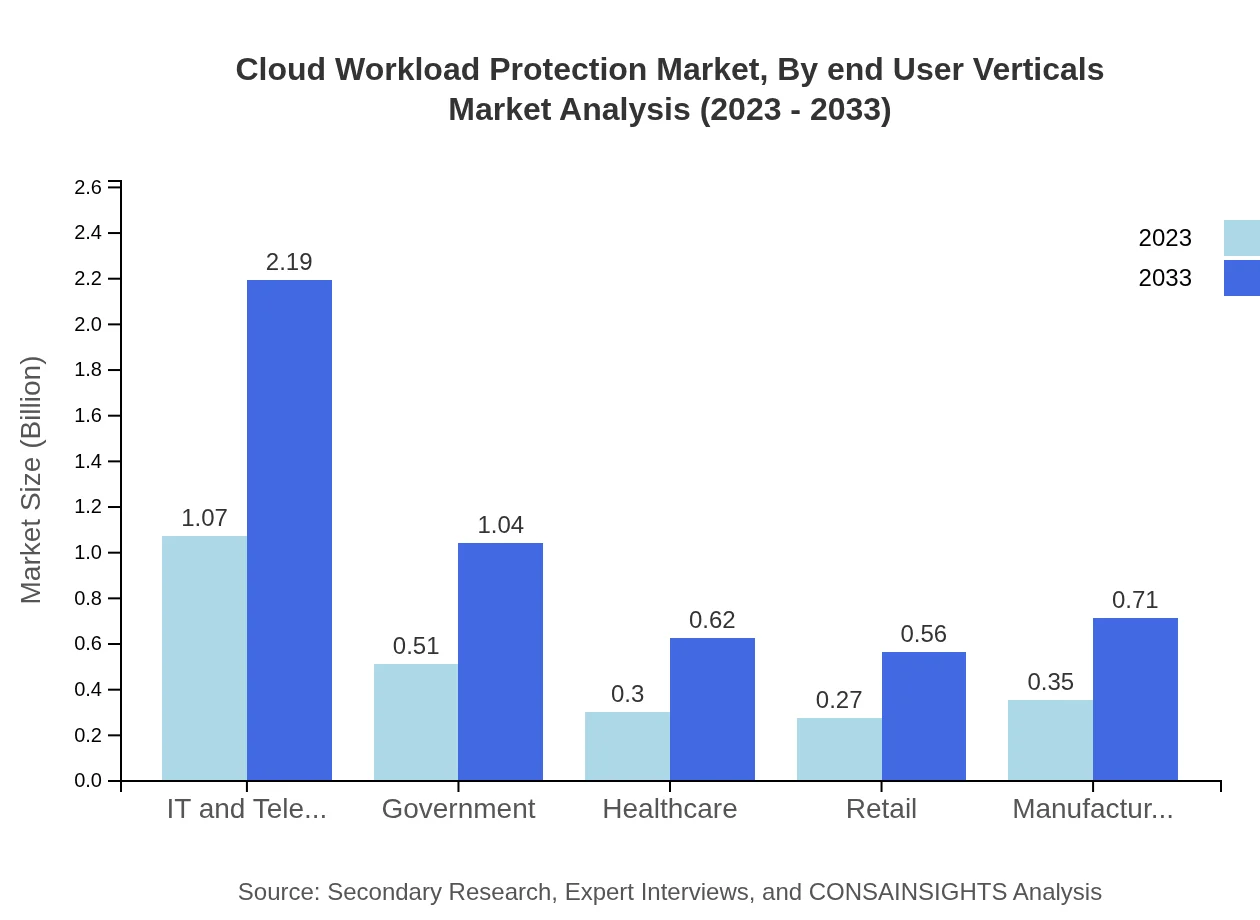
Cloud Workload Protection Market Analysis By End User Verticals
The IT and Telecommunications sector accounts for a significant share of the market, growing from $1.07 billion in 2023 to $2.19 billion by 2033. Other sectors such as Government and Healthcare also display promising expansion.
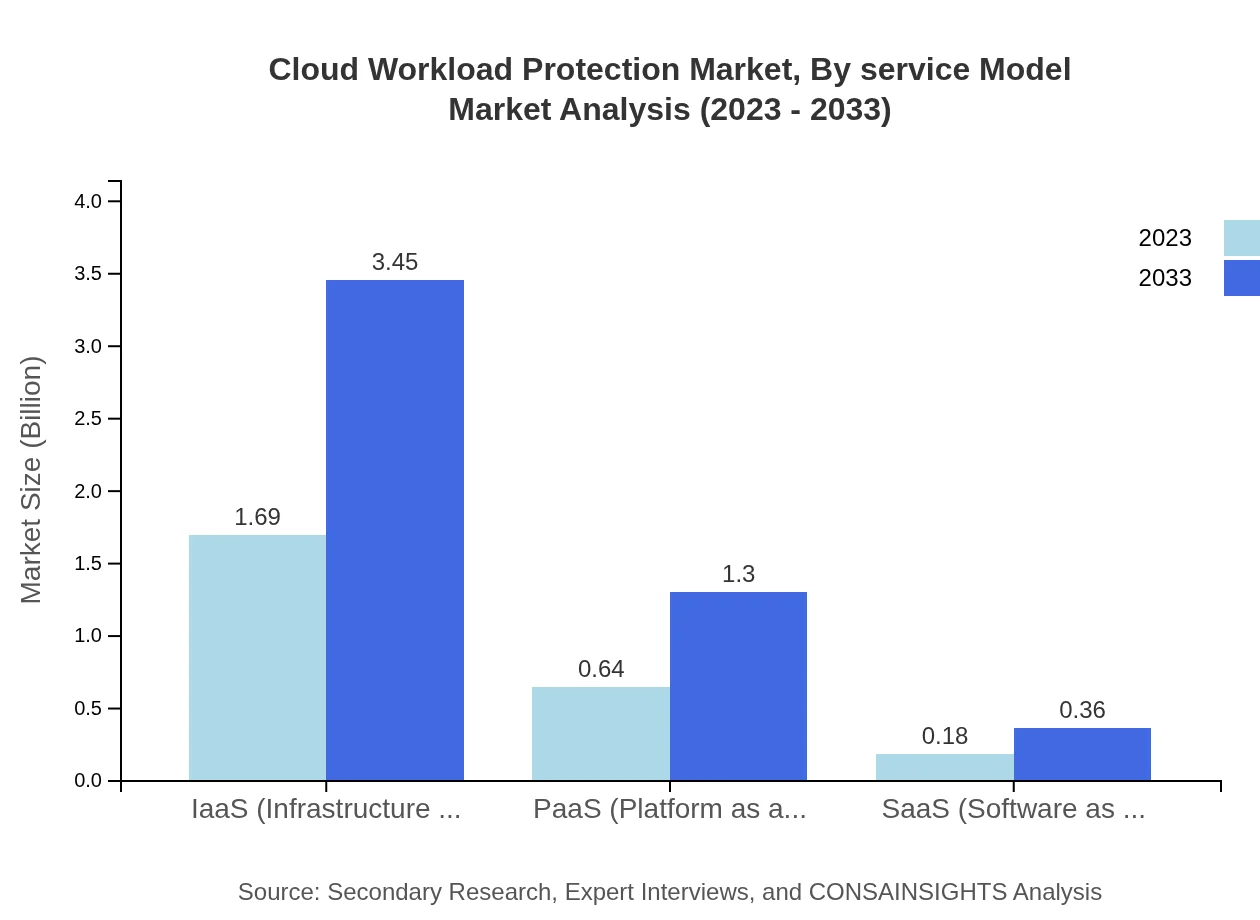
Cloud Workload Protection Market Analysis By Service Model
The SaaS model is anticipated to constitute a substantial market share, reflecting the growing preference for subscription-based software services. The IaaS segment also underscores the importance of providing secure infrastructures to support varied workloads.
Cloud Workload Protection Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Cloud Workload Protection Industry
Palo Alto Networks:
Palo Alto Networks offers a robust suite of cloud security solutions that help organizations secure their cloud workloads against cyber threats.McAfee:
McAfee is known for its comprehensive security solutions, including those specifically designed for cloud environments.Symantec:
Symantec has a long-standing reputation in cybersecurity and offers advanced cloud workload protection solutions.Trend Micro:
Trend Micro provides innovative solutions to secure cloud workloads while addressing the needs of digital transformation.Zscaler :
Zscaler is dedicated to providing cloud-native security solutions, enhancing workload protection in highly dynamic environments.We're grateful to work with incredible clients.









FAQs
What is the market size of Cloud Workload Protection?
The Cloud Workload Protection market currently stands at approximately $2.5 billion, with an anticipated compound annual growth rate (CAGR) of 7.2% from 2023 to 2033, indicating strong growth potential as organizations increasingly prioritize cloud security.
What are the key market players or companies in this Cloud Workload Protection industry?
Key players in the Cloud Workload Protection industry include leading cybersecurity firms such as Palo Alto Networks, McAfee, Trend Micro, and Check Point Software Technologies, each offering advanced solutions to address diverse cloud security needs.
What are the primary factors driving the growth in the Cloud Workload Protection industry?
The growth of the Cloud Workload Protection market is primarily driven by increasing cloud adoption, rising cyber threats, regulatory compliance requirements, and the need for advanced security measures to protect sensitive data in cloud environments.
Which region is the fastest Growing in the Cloud Workload Protection market?
North America is currently the fastest-growing region in the Cloud Workload Protection market, projected to grow from $0.94 billion in 2023 to $1.92 billion by 2033, driven by a high concentration of tech companies and regulatory pressures.
Does ConsaInsights provide customized market report data for the Cloud Workload Protection industry?
Yes, ConsaInsights offers customized market report data for the Cloud Workload Protection industry, ensuring that stakeholders receive tailored analysis that meets their specific needs and business objectives.
What deliverables can I expect from this Cloud Workload Protection market research project?
From this research project, you can expect detailed reports containing market size, growth forecasts, competitive analysis, regional breakdowns, and insights into market trends and emerging technologies within the Cloud Workload Protection space.
What are the market trends of Cloud Workload Protection?
Current market trends in Cloud Workload Protection include an increasing focus on automation, the integration of AI for threat detection, growing demand for compliance management, and the rise of multi-cloud environments, emphasizing the need for holistic security approaches.