Critical National Infrastructure Cyber Security Market Report
Published Date: 31 January 2026 | Report Code: critical-national-infrastructure-cyber-security
Critical National Infrastructure Cyber Security Market Size, Share, Industry Trends and Forecast to 2033
This report provides a comprehensive analysis of the Critical National Infrastructure Cyber Security market, encompassing market trends, segments, regional insights, industry analysis, and forecasts for the period 2023 to 2033.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
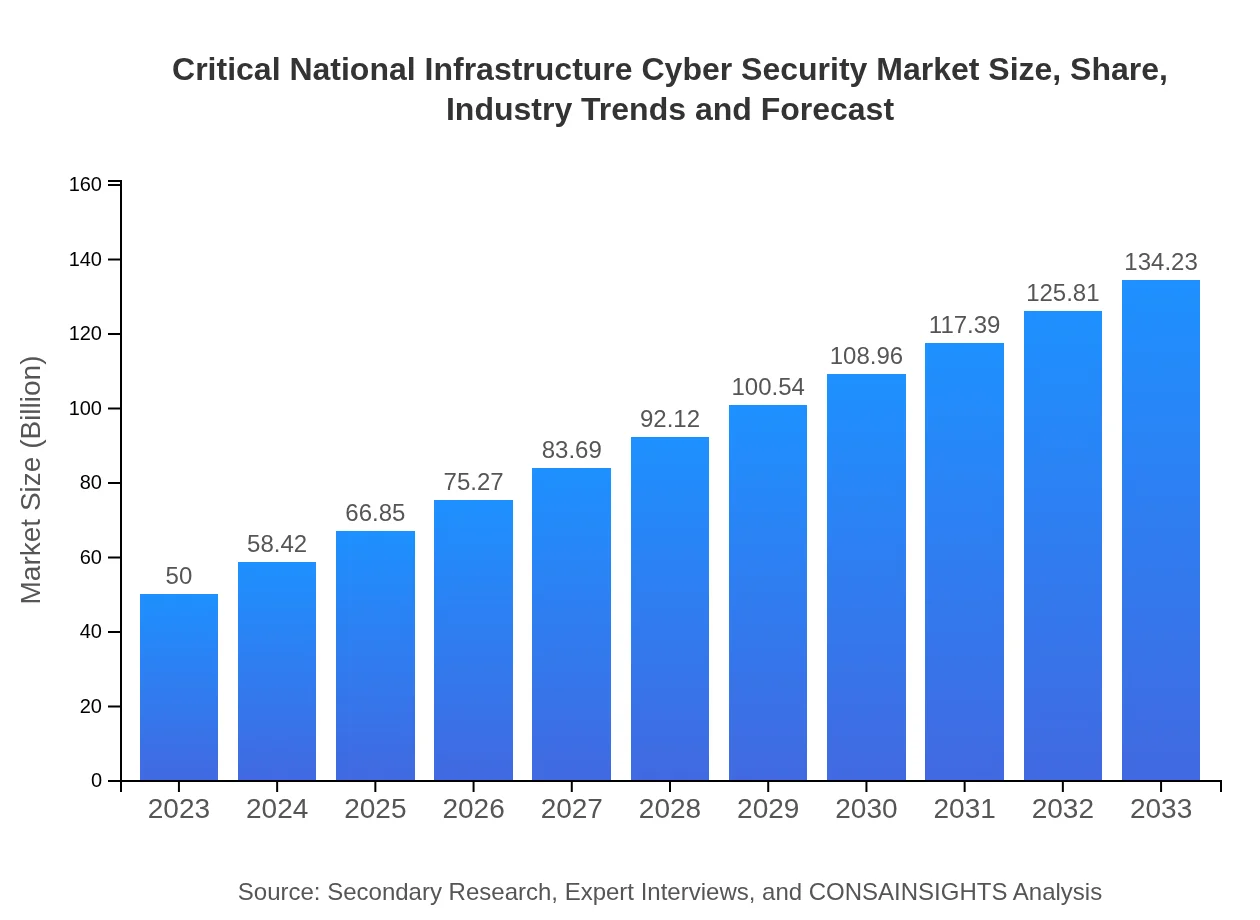
| 2023 Market Size | $50.00 Billion |
| CAGR (2023-2033) | 10% |
| 2033 Market Size | $134.23 Billion |
| Top Companies | Cisco Systems, Inc., McAfee Corp., Palo Alto Networks, Inc., Siemens AG, Fortinet, Inc. |
| Last Modified Date | 31 January 2026 |
Critical National Infrastructure Cyber Security Market Overview
Customize Critical National Infrastructure Cyber Security Market Report market research report
- ✔ Get in-depth analysis of Critical National Infrastructure Cyber Security market size, growth, and forecasts.
- ✔ Understand Critical National Infrastructure Cyber Security's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Critical National Infrastructure Cyber Security
What is the Market Size & CAGR of Critical National Infrastructure Cyber Security market in 2033?
Critical National Infrastructure Cyber Security Industry Analysis
Critical National Infrastructure Cyber Security Market Segmentation and Scope
Tell us your focus area and get a customized research report.
Critical National Infrastructure Cyber Security Market Analysis Report by Region
Europe Critical National Infrastructure Cyber Security Market Report:
Europe is experiencing significant advancements in cybersecurity measures for critical infrastructure, with market growth expected from USD 14.46 billion in 2023 to USD 38.81 billion by 2033. The implementation of regulations such as GDPR emphasizes the urgency of securing critical infrastructures.Asia Pacific Critical National Infrastructure Cyber Security Market Report:
The Asia Pacific region is witnessing strong growth, driven by increased internet penetration and rising cyber threats. The market size is expected to grow from USD 8.74 billion in 2023 to USD 23.48 billion by 2033. Countries like China and India are investing heavily in technology to secure critical infrastructure, propelled by government initiatives and regulations.North America Critical National Infrastructure Cyber Security Market Report:
North America holds the largest share of the CNI Cyber Security market, projected to rise from USD 19.41 billion in 2023 to USD 52.10 billion by 2033. The market is bolstered by robust technological advancements and extensive investments from private and public sectors, particularly in the U.S. where government agencies implement comprehensive cybersecurity policies.South America Critical National Infrastructure Cyber Security Market Report:
In South America, the market for CNI Cyber Security is emerging, with an expected growth from USD 0.91 billion in 2023 to USD 2.44 billion by 2033. Countries are beginning to acknowledge the importance of cybersecurity, prompted by a rise in cyber incidents and the need to protect essential services.Middle East & Africa Critical National Infrastructure Cyber Security Market Report:
The Middle East and Africa are rapidly developing their cybersecurity strategies, with an anticipated growth from USD 6.49 billion in 2023 to USD 17.41 billion by 2033. Initiatives to modernize infrastructures and combat rising cyber risks drive the demand for cybersecurity solutions in these regions.Tell us your focus area and get a customized research report.
Critical National Infrastructure Cyber Security Market Analysis By Security Type
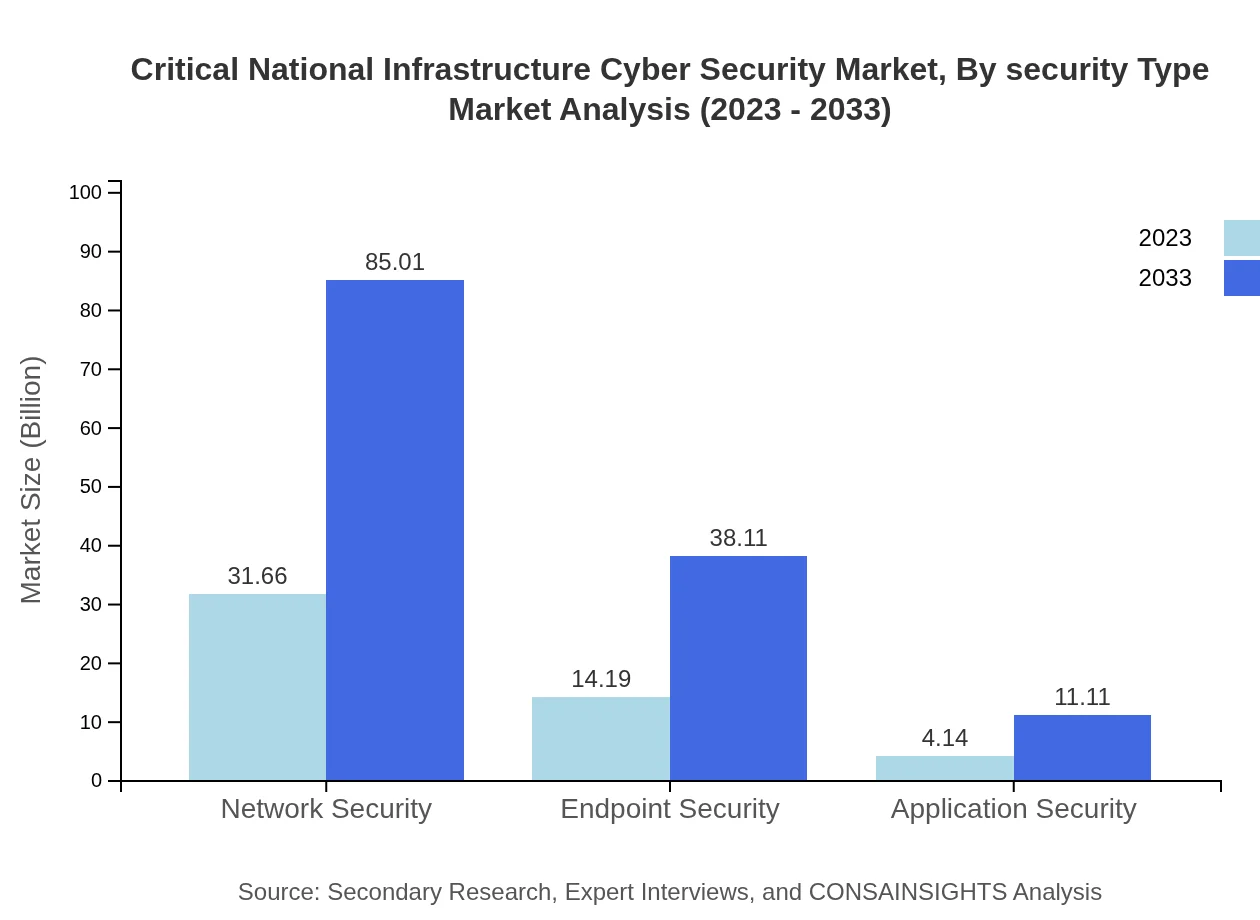
The market for CNI Cyber Security by Security Type is robust, with Network Security leading the way. In 2023, Network Security is expected to be valued at USD 31.66 billion and projected to grow to USD 85.01 billion by 2033, comprising a 63.33% share in 2023. Endpoint and Application Security are also significant, with forecasts showing respective growths to USD 38.11 billion and USD 11.11 billion by 2033.
Critical National Infrastructure Cyber Security Market Analysis By Industry
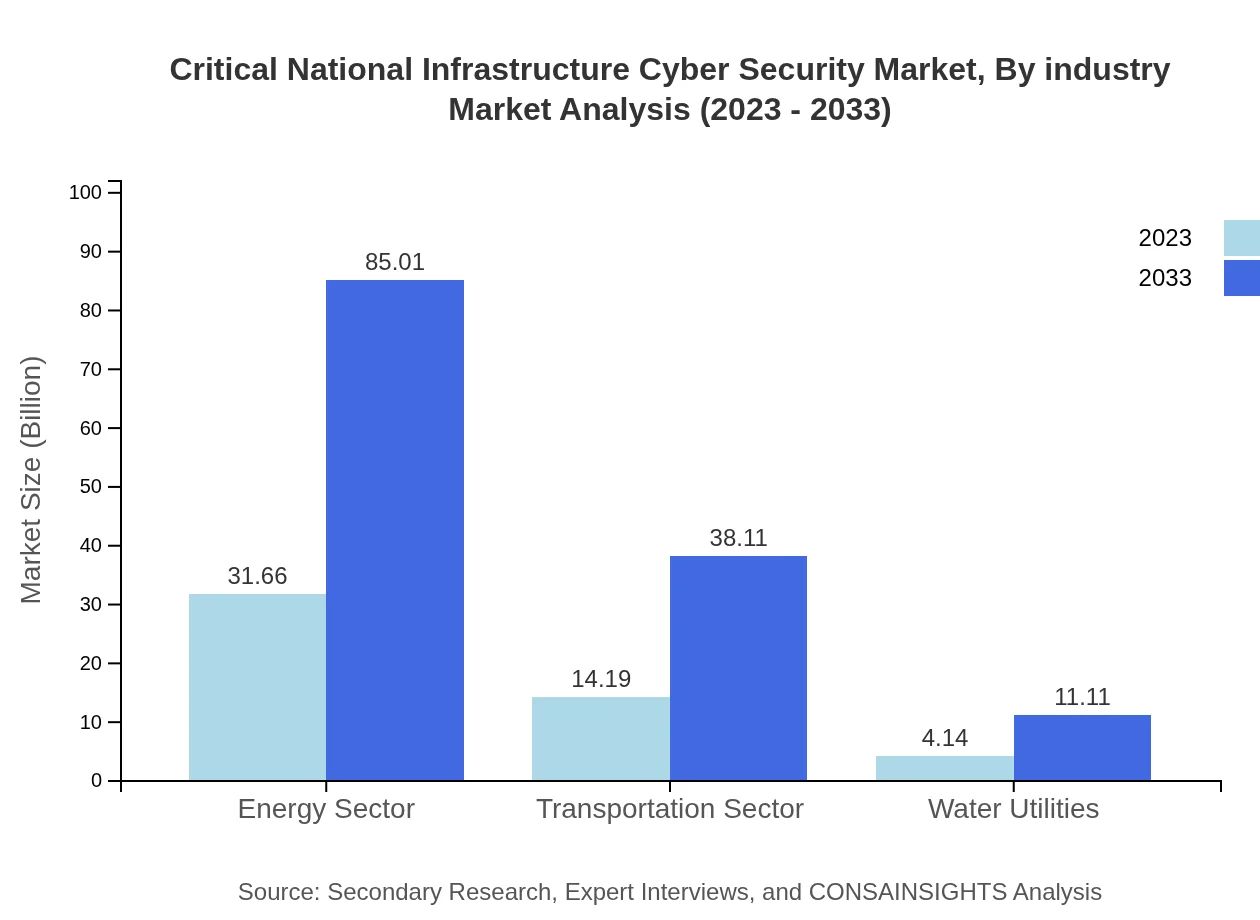
In the industry segment, the Energy sector commands the largest market share, projected to grow from USD 31.66 billion in 2023 to USD 85.01 billion by 2033, representing a 63.33% market share. Other sectors such as Transportation and Water Utilities follow, with market sizes expected to reach USD 38.11 billion and USD 11.11 billion, respectively, by 2033.
Critical National Infrastructure Cyber Security Market Analysis By Deployment Model
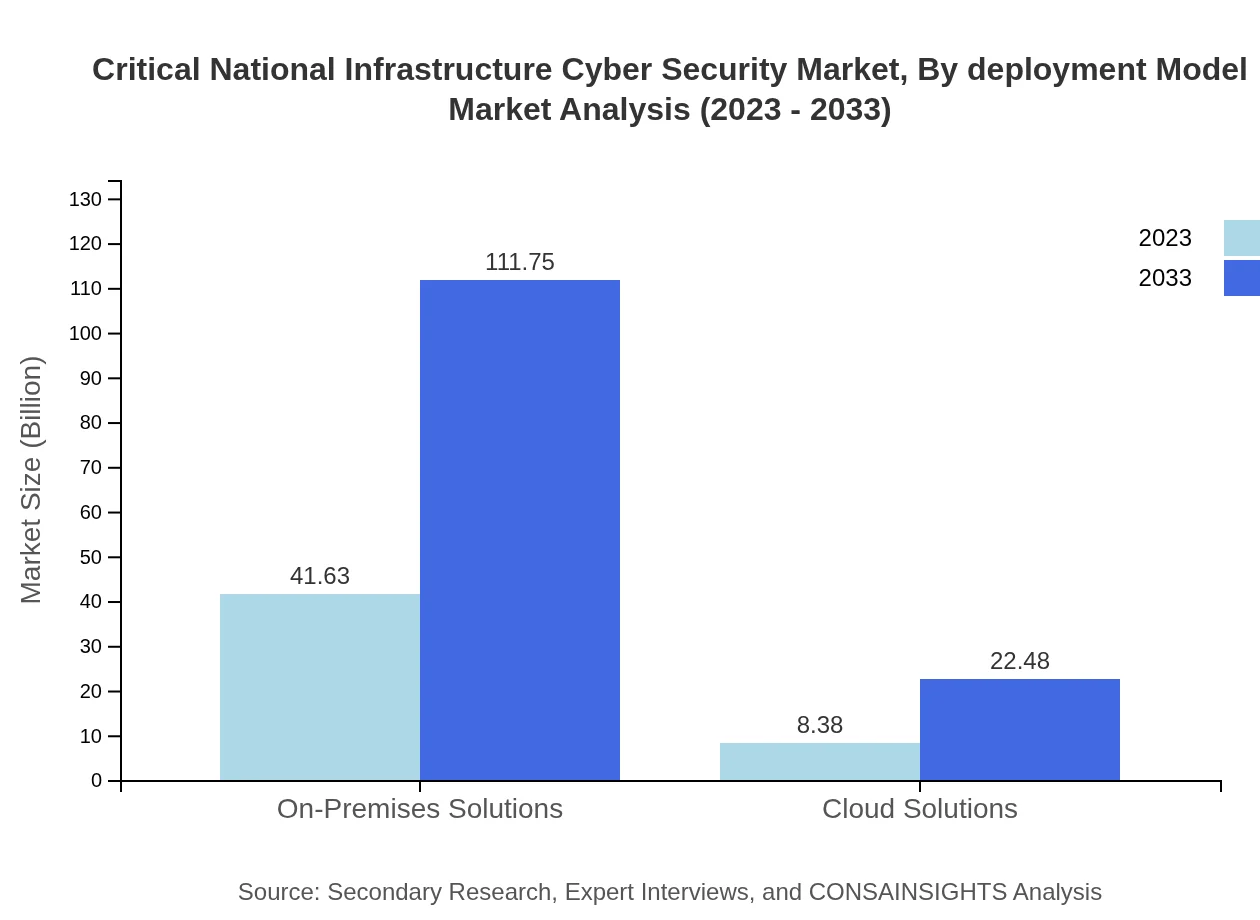
The deployment of cybersecurity solutions is analyzed via On-Premises and Cloud Solutions. On-Premises Solutions dominate the market with a size expected at USD 41.63 billion in 2023, rising to USD 111.75 billion by 2033, taking an 83.25% market share. Cloud solutions, while smaller at USD 8.38 billion in 2023, are expected to grow to USD 22.48 billion by 2033.
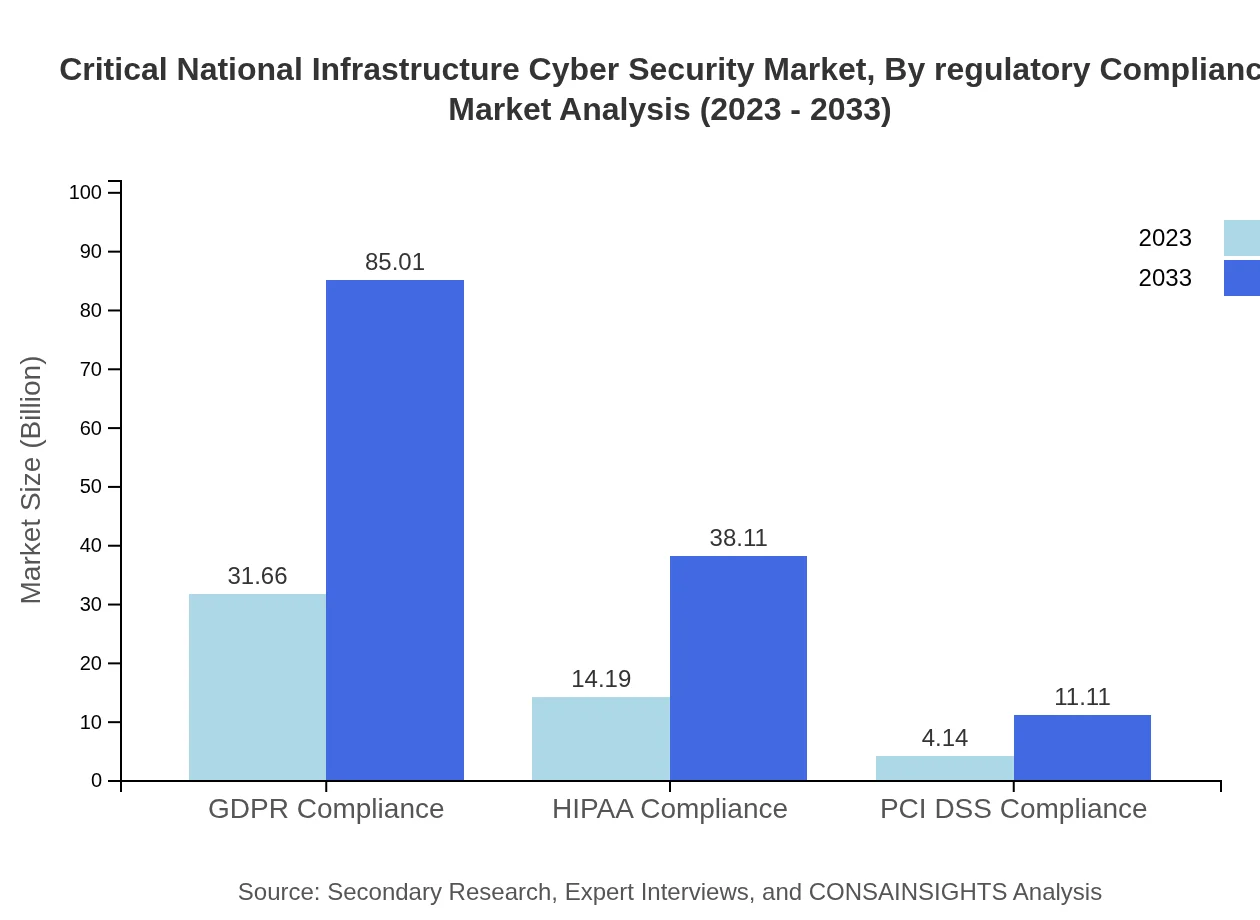
Critical National Infrastructure Cyber Security Market Analysis By Regulatory Compliance
Regulatory Compliance requirements, like GDPR, HIPAA, and PCI DSS, significantly shape the CNI Cyber Security market. GDPR Compliance is estimated to hold a share of 63.33%, growing from USD 31.66 billion in 2023 to USD 85.01 billion by 2033. HIPAA and PCI DSS Compliance segments also see considerable contributions to market growth.
Critical National Infrastructure Cyber Security Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Critical National Infrastructure Cyber Security Industry
Cisco Systems, Inc.:
Cisco Systems is a leading technology company specializing in cybersecurity products that enhance the protection of critical infrastructures through innovative, integrated solutions.McAfee Corp.:
McAfee provides comprehensive security solutions focused on protecting networks, data, and critical infrastructure from emerging cyber threats.Palo Alto Networks, Inc.:
Palo Alto is renowned for its advanced cybersecurity technology, providing solutions that enable organizations to secure their critical national infrastructure efficiently.Siemens AG:
Siemens contributes significantly to industrial security, offering solutions designed specifically for the protection of critical infrastructure in sectors like energy and utilities.Fortinet, Inc.:
Fortinet is recognized for its high-performance cybersecurity solutions that protect critical infrastructures across various industries with a strong focus on threat intelligence.We're grateful to work with incredible clients.









FAQs
What is the market size of critical National Infrastructure Cyber Security?
The critical national infrastructure cyber security market is valued at $50 billion in 2023, with a robust CAGR of 10%, indicating significant growth potential by 2033.
What are the key market players or companies in this critical National Infrastructure Cyber Security industry?
Key players in this market include leading cybersecurity firms, technology providers, and government agencies focused on protecting critical infrastructure from cyber threats.
What are the primary factors driving the growth in the critical National Infrastructure Cyber Security industry?
Growth is driven by increased cyber threats, regulatory compliance demands, and heightened investment in infrastructure modernization and resilience against attacks.
Which region is the fastest Growing in the critical National Infrastructure Cyber Security?
North America is the fastest-growing region, projected to expand from $19.41 billion in 2023 to $52.10 billion by 2033, driven by robust investments in cybersecurity initiatives.
Does ConsaInsights provide customized market report data for the critical National Infrastructure Cyber Security industry?
Yes, ConsaInsights offers tailored market report data to address specific needs and insights pertaining to the critical national infrastructure cyber security industry.
What deliverables can I expect from this critical National Infrastructure Cyber Security market research project?
Expect comprehensive market analysis, segmented data, regional insights, competitive landscape overviews, and actionable recommendations in the deliverables.
What are the market trends of critical National Infrastructure Cyber Security?
Market trends include increasing adoption of AI in cybersecurity, heightened focus on data privacy compliance, and the shift towards cloud solutions in infrastructure security.