Cyber Security As A Service Market Report
Published Date: 31 January 2026 | Report Code: cyber-security-as-a-service
Cyber Security As A Service Market Size, Share, Industry Trends and Forecast to 2033
This report analyzes the Cyber Security as a Service market, providing insights into market size, growth rates, and trends from 2023 to 2033. It covers market segments, regional insights, technology advancements, product performance, leading companies, and forecasts for future developments.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
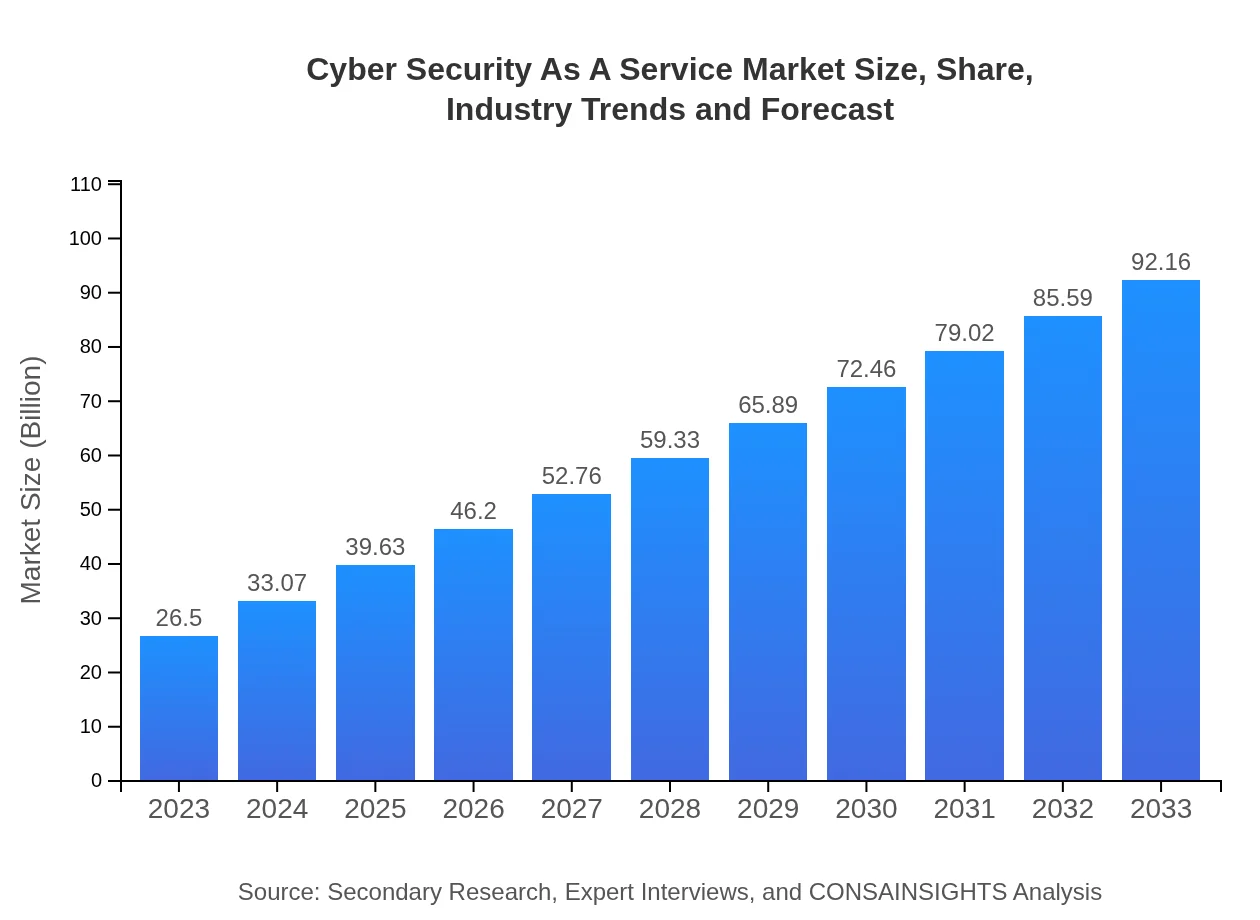
| 2023 Market Size | $26.50 Billion |
| CAGR (2023-2033) | 12.7% |
| 2033 Market Size | $92.16 Billion |
| Top Companies | Cisco Systems, Inc., Palo Alto Networks, Inc., Fortinet, Inc., Check Point Software Technologies Ltd. |
| Last Modified Date | 31 January 2026 |
Cyber Security As A Service Market Overview
Customize Cyber Security As A Service Market Report market research report
- ✔ Get in-depth analysis of Cyber Security As A Service market size, growth, and forecasts.
- ✔ Understand Cyber Security As A Service's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Cyber Security As A Service
What is the Market Size & CAGR of Cyber Security As A Service market in 2023 and 2033?
Cyber Security As A Service Industry Analysis
Cyber Security As A Service Market Segmentation and Scope
Tell us your focus area and get a customized research report.
Cyber Security As A Service Market Analysis Report by Region
Europe Cyber Security As A Service Market Report:
In Europe, the market size for Cyber Security as a Service is expected to grow from $8.37 billion in 2023 to $29.12 billion by 2033. Rapid digital adoption and a strong regulatory environment, including GDPR, significantly influence the demand for robust cybersecurity solutions within the European landscape.Asia Pacific Cyber Security As A Service Market Report:
In 2023, the Cyber Security as a Service market in the Asia Pacific is valued at approximately $5.05 billion, with expectations to grow to around $17.56 billion by 2033. The region is increasingly adopting cloud solutions driven by rapid digital transformation, with significant investments in cybersecurity aimed at protecting sensitive data and critical infrastructure from imminent threats.North America Cyber Security As A Service Market Report:
North America leads the market, with the Cyber Security as a Service sector valued at $8.87 billion in 2023 and forecasted to reach $30.85 billion by 2033. This region's growth is primarily driven by a high concentration of cyber threats, stringent regulatory policies, and substantial investments in security technologies by businesses seeking to protect their operations.South America Cyber Security As A Service Market Report:
The South American market for Cyber Security as a Service is projected to grow from $0.57 billion in 2023 to $1.97 billion by 2033. The region is witnessing a rise in cyber incidents, prompting organizations to adopt integrated security solutions and address vulnerabilities, reflective of a growing digital economy.Middle East & Africa Cyber Security As A Service Market Report:
The Middle East and Africa market is projected to increase from $3.64 billion in 2023 to $12.64 billion by 2033. Growing digitalization, coupled with rising cyber threats in the region, drives an urgent need for cybersecurity services to safeguard regional businesses and personal data.Tell us your focus area and get a customized research report.
Cyber Security As A Service Market Analysis By Industry
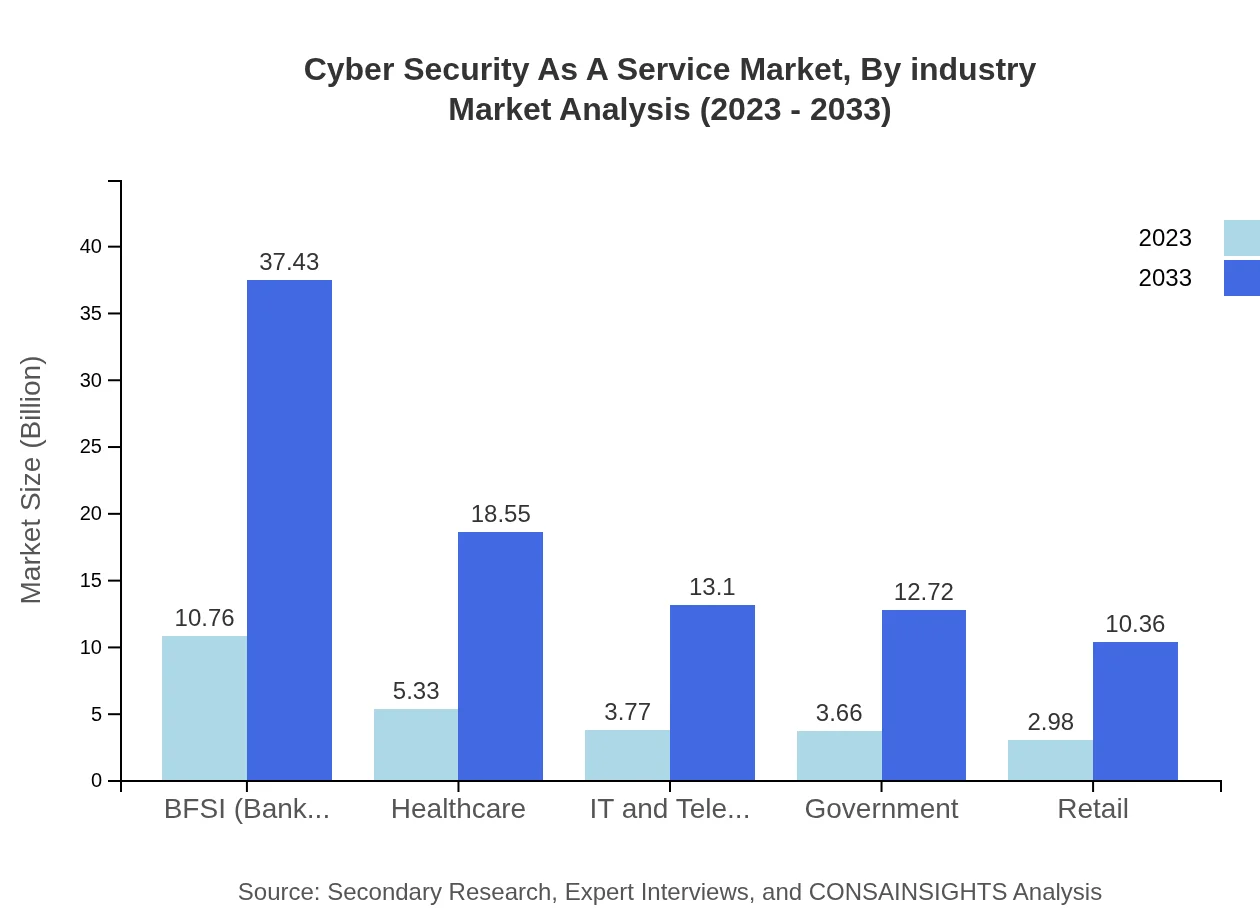
The BFSI sector commands a significant portion of the market, with its size projected to grow from $10.76 billion in 2023 to approximately $37.43 billion by 2033. In addition, the healthcare sector is set to expand from $5.33 billion to $18.55 billion, driven by increasing regulatory pressures and the need to protect patient data. The IT and telecom segment is anticipated to grow from $3.77 billion to $13.10 billion, emphasizing cybersecurity's importance in ensuring service reliability amid growing digital threats.
Cyber Security As A Service Market Analysis By Service Type
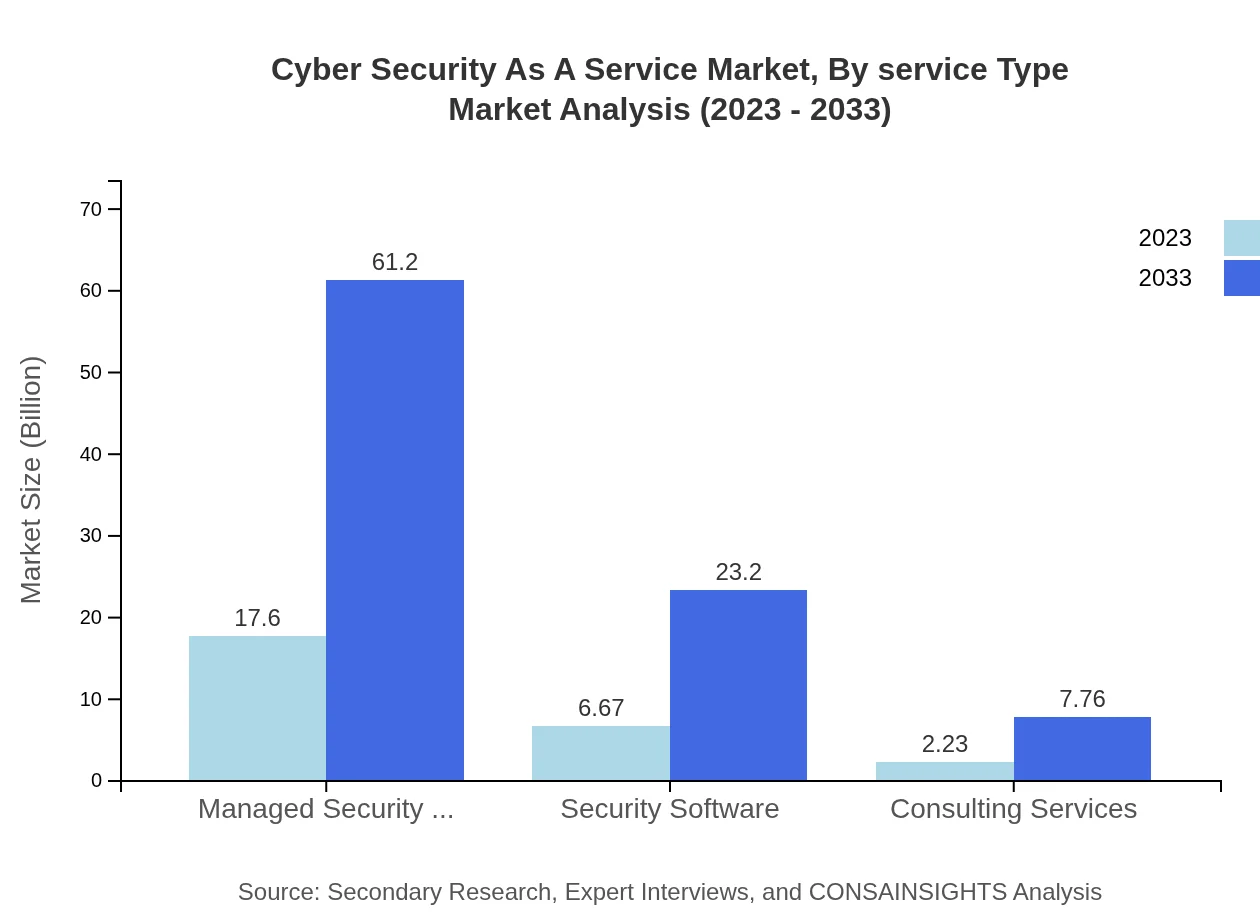
Managed Security Services hold the largest share, with market values estimated at $17.60 billion in 2023 and projected to reach $61.20 billion by 2033, demonstrating strong demand for outsourced security operations. Security Software is expected to grow from $6.67 billion to $23.20 billion, reflecting user preferences for cloud-native security solutions that integrate seamlessly with business operations.
Cyber Security As A Service Market Analysis By Deployment Model
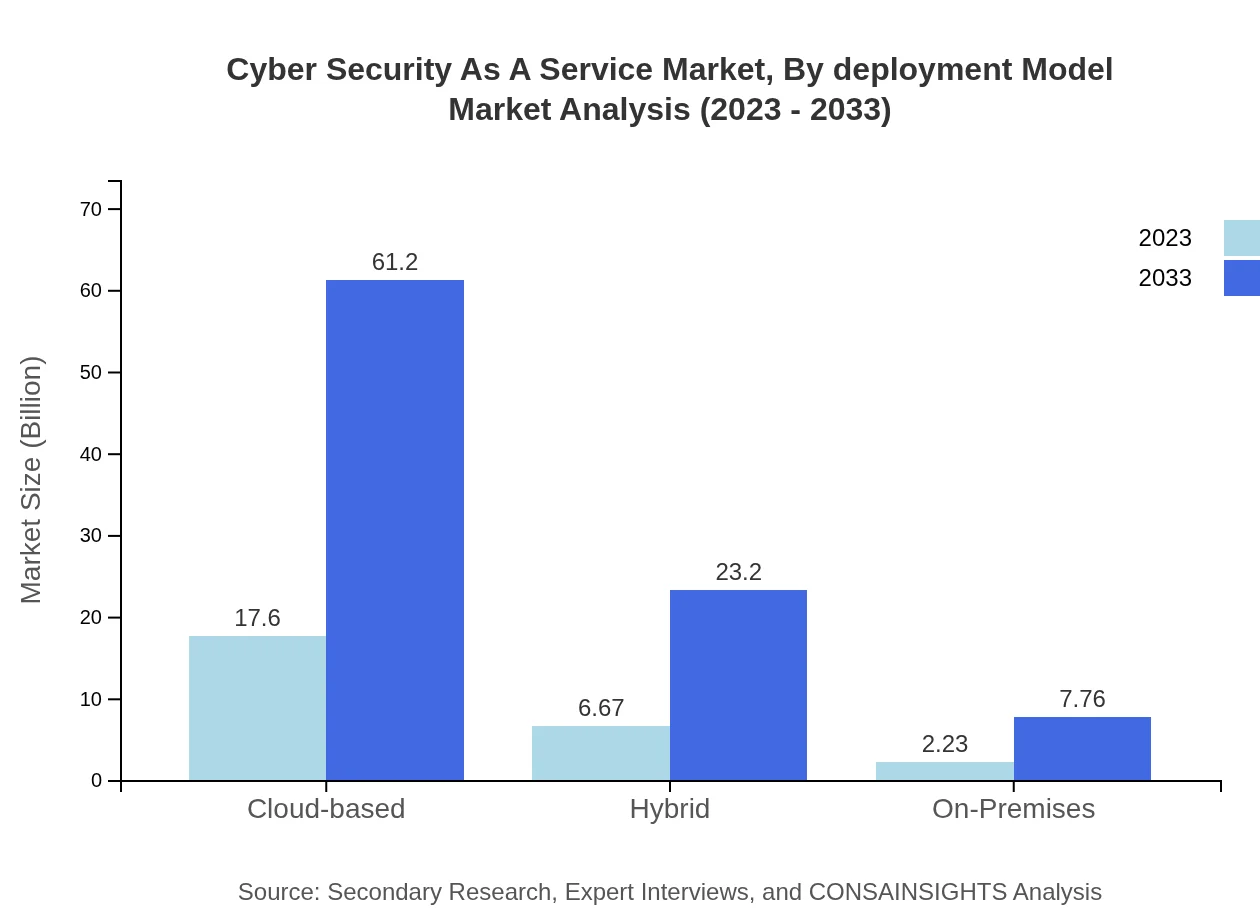
The cloud-based deployment model leads the market with anticipated growth from $17.60 billion to $61.20 billion, showcasing a shift toward flexible, scalable security solutions. Hybrid models are also gaining traction, projected to grow from $6.67 billion to $23.20 billion as businesses seek a blend of cloud benefits with on-premises security. On-Premises solutions remain relevant though less favored compared to cloud options.
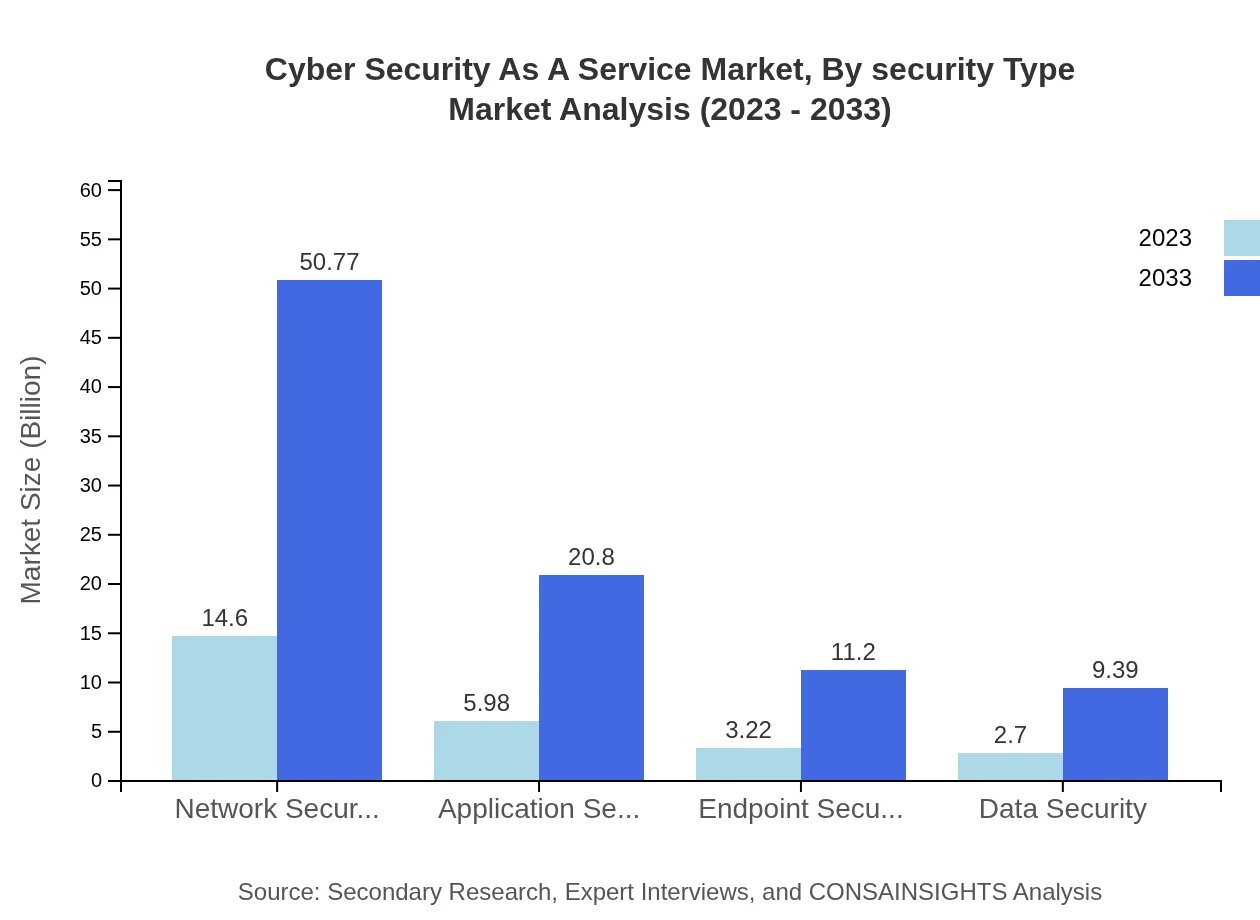
Cyber Security As A Service Market Analysis By Security Type
Network Security continues to dominate, with projections of growing from $14.60 billion in 2023 to $50.77 billion by 2033. Application Security and Endpoint Security are also critical sectors, set to grow significantly, illustrating the need for comprehensive cyber protection across business operations.
Cyber Security As A Service Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Cyber Security As A Service Industry
Cisco Systems, Inc.:
Cisco provides a suite of cybersecurity solutions tailored for various markets, emphasizing network security and threat intelligence, thereby enhancing organizational defenses against cyber threats.Palo Alto Networks, Inc.:
A leader in cybersecurity solutions, Palo Alto Networks focuses on cloud security, endpoint protection, and sophisticated threat prevention systems to help businesses secure their data environments.Fortinet, Inc.:
Fortinet delivers high-performance cybersecurity solutions through its integrated security fabric, addressing diverse sectors' challenges globally with effective threat management services.Check Point Software Technologies Ltd.:
Specializing in multi-layered cybersecurity architecture, Check Point offers cloud security services, endpoint protection, and advanced threat prevention capabilities to safeguard enterprise environments.We're grateful to work with incredible clients.









FAQs
What is the market size of Cyber Security as a Service?
The Cyber Security as a Service market is valued at approximately $26.5 billion in 2023, and is expected to grow at a CAGR of 12.7%, reaching significant growth by 2033. This market growth reflects increasing demand for outsourced security solutions.
What are the key market players or companies in the Cyber Security as a Service industry?
Key players in the Cyber Security as a Service industry include Cisco Systems, IBM Corporation, Palo Alto Networks, and Fortinet. These companies lead through innovative security technologies and extensive service offerings that cater to various industries, enhancing overall cybersecurity.
What are the primary factors driving the growth in the Cyber Security as a Service industry?
The growth in the Cyber Security as a Service industry is driven by increasing cyber threats, demand for compliance with regulations, evolving digital infrastructure, and the need for cost-effective security solutions. These factors collectively push organizations to seek comprehensive but flexible security services.
Which region is the fastest Growing in the Cyber Security as a Service?
North America is the fastest-growing region in the Cyber Security as a Service market, with a projected market size increase from $8.87 billion in 2023 to $30.85 billion by 2033. Other emerging regions like Asia Pacific are also poised for growth.
Does ConsaInsights provide customized market report data for the Cyber Security as a Service industry?
Yes, ConsaInsights offers customized market report data tailored to specific needs in the Cyber Security as a Service industry. Clients can receive insights that address particular market segments, regional trends, or competitive analysis relevant to their business.
What deliverables can I expect from this Cyber Security as a Service market research project?
Deliverables from the Cyber Security as a Service market research project include comprehensive market analysis reports, regional trend insights, competitive landscape data, growth forecasts, and market segmentation details, all tailored to inform strategic business decisions.
What are the market trends of Cyber Security as a Service?
Current market trends in Cyber Security as a Service include a shift toward managed services, increasing adoption of cloud-based security solutions, a focus on endpoint security, and a growing demand for tailored security consulting services, reflecting the need for proactive defense mechanisms.