Data Centric Security Market Report
Published Date: 31 January 2026 | Report Code: data-centric-security
Data Centric Security Market Size, Share, Industry Trends and Forecast to 2033
This report provides a comprehensive analysis of the Data Centric Security market, focusing on current trends, market size, and future forecasts from 2023 to 2033, highlighting key segments and competitive dynamics in the industry.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
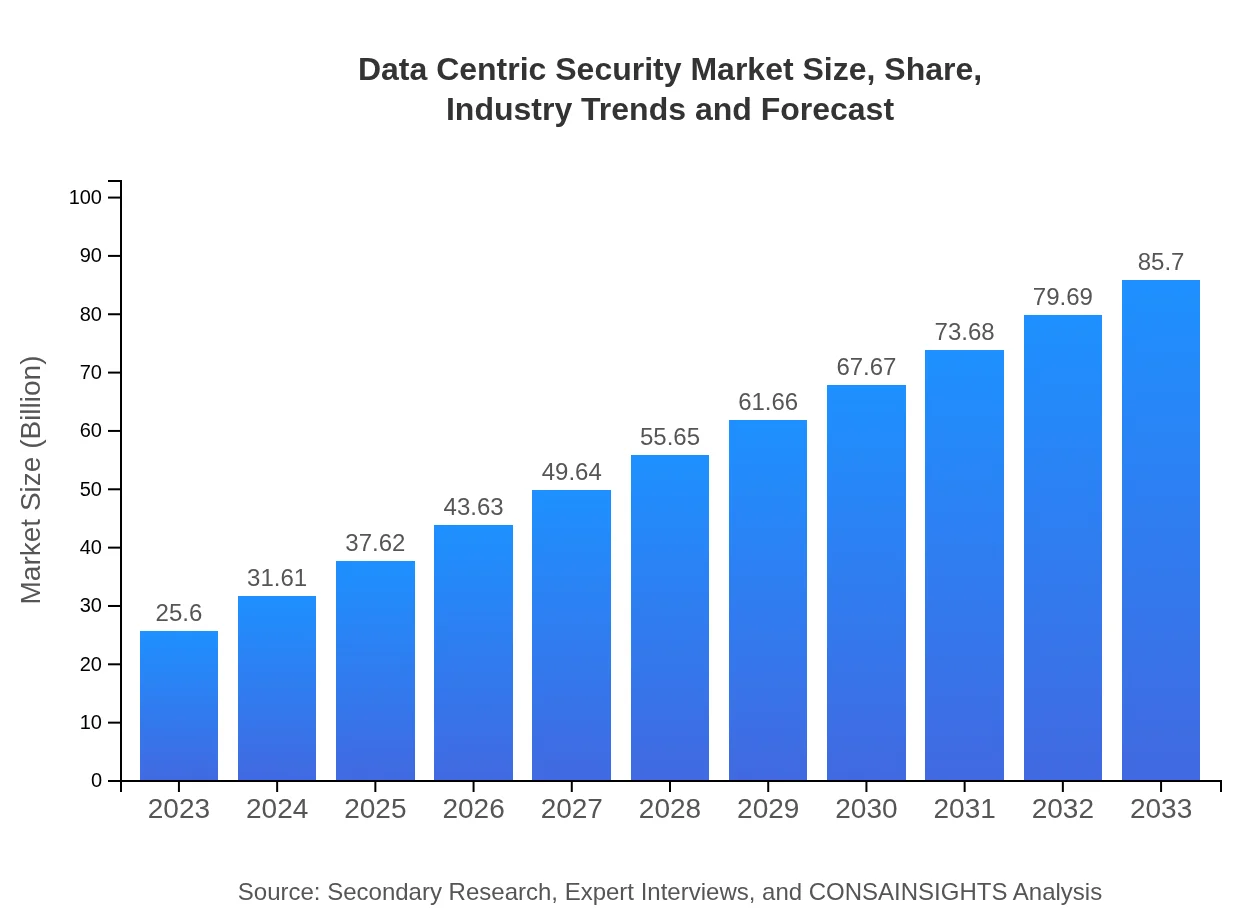
| 2023 Market Size | $25.60 Billion |
| CAGR (2023-2033) | 12.3% |
| 2033 Market Size | $85.70 Billion |
| Top Companies | IBM Corporation, Symantec Corporation, RSA Security LLC, McAfee Corp. |
| Last Modified Date | 31 January 2026 |
Data Centric Security Market Overview
Customize Data Centric Security Market Report market research report
- ✔ Get in-depth analysis of Data Centric Security market size, growth, and forecasts.
- ✔ Understand Data Centric Security's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Data Centric Security
What is the Market Size & CAGR of Data Centric Security market in 2023?
Data Centric Security Industry Analysis
Data Centric Security Market Segmentation and Scope
Tell us your focus area and get a customized research report.
Data Centric Security Market Analysis Report by Region
Europe Data Centric Security Market Report:
Europe's Data Centric Security market, valued at $7.57 billion in 2023, is projected to reach $25.35 billion by 2033. Enhanced regulatory frameworks like GDPR drive organizations to enforce comprehensive data protection strategies, significantly contributing to market expansion.Asia Pacific Data Centric Security Market Report:
In 2023, the Asia Pacific region boasts a market size of $4.85 billion and is expected to grow to $16.22 billion by 2033. Rapid digital transformation and increasing data breaches compel organizations to invest heavily in security solutions. Countries like India and China lead with significant investments in data protection technologies amid stringent regulations.North America Data Centric Security Market Report:
North America, leading the Data Centric Security market with $9.36 billion in 2023, is expected to grow to $31.32 billion by 2033. The region benefits from a sophisticated technological landscape and an influx of regulatory mandates such as HIPAA and CCPA, supporting robust demand for data-centric approaches.South America Data Centric Security Market Report:
The South American Data Centric Security market is valued at $0.93 billion in 2023 and predicted to reach $3.10 billion by 2033. The gradual adoption of digital services, combined with a rise in cyber risks and growing concerns over data privacy, is driving demand for advanced security measures.Middle East & Africa Data Centric Security Market Report:
The Middle East and Africa market stands at $2.90 billion in 2023, with expectations to grow to $9.70 billion by 2033. As these regions embrace digitalization, concerns over data privacy and security are escalating, catalyzing higher investments in Data Centric Security solutions.Tell us your focus area and get a customized research report.
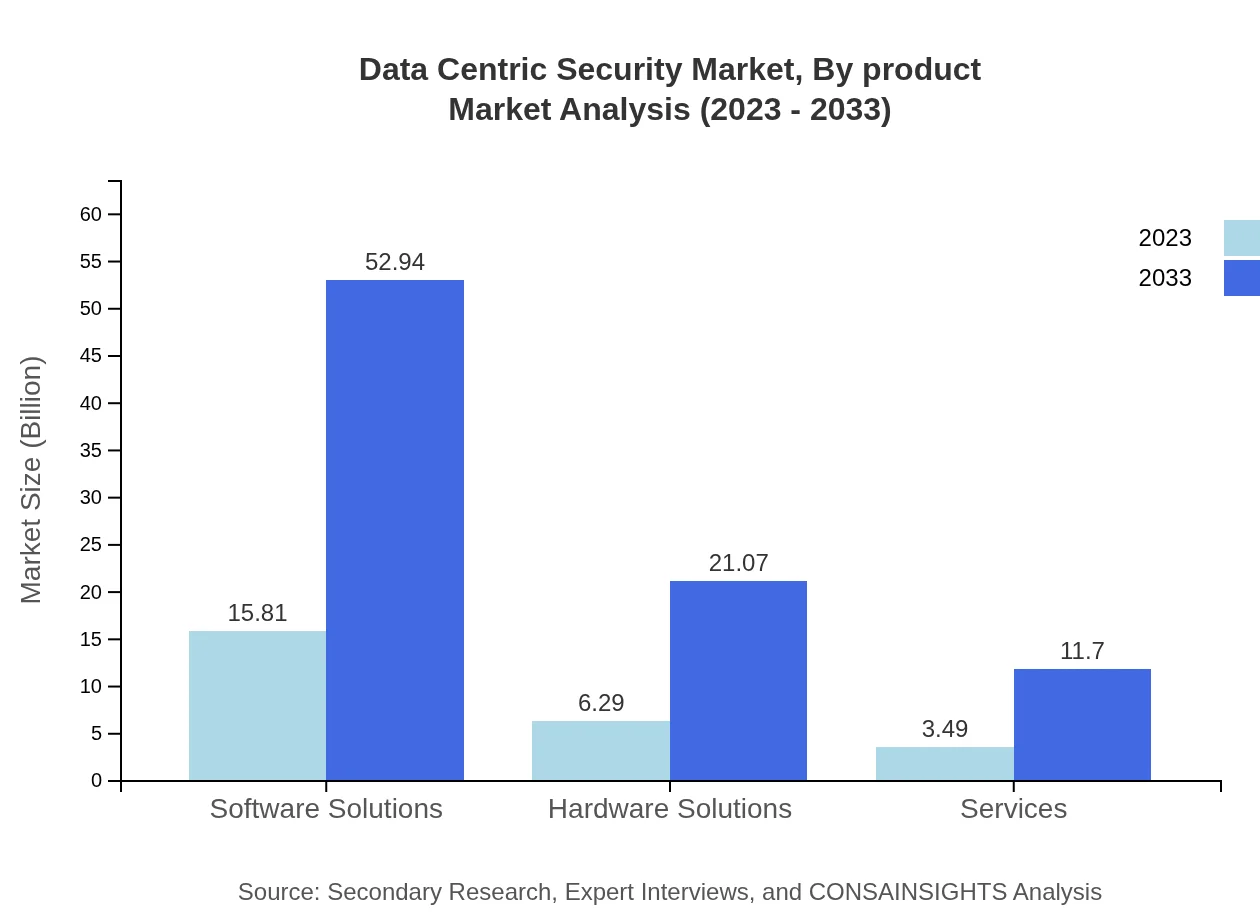
Data Centric Security Market Analysis By Product
The Data Centric Security market can be categorized into Software Solutions, Hardware Solutions, and Services. In 2023, Software Solutions dominate the market with a size of $15.81 billion, projected to grow to $52.94 billion by 2033, while Hardware Solutions are currently valued at $6.29 billion and expected to reach $21.07 billion by 2033. Services are forecasted to grow from $3.49 billion in 2023 to $11.70 billion in 2033.
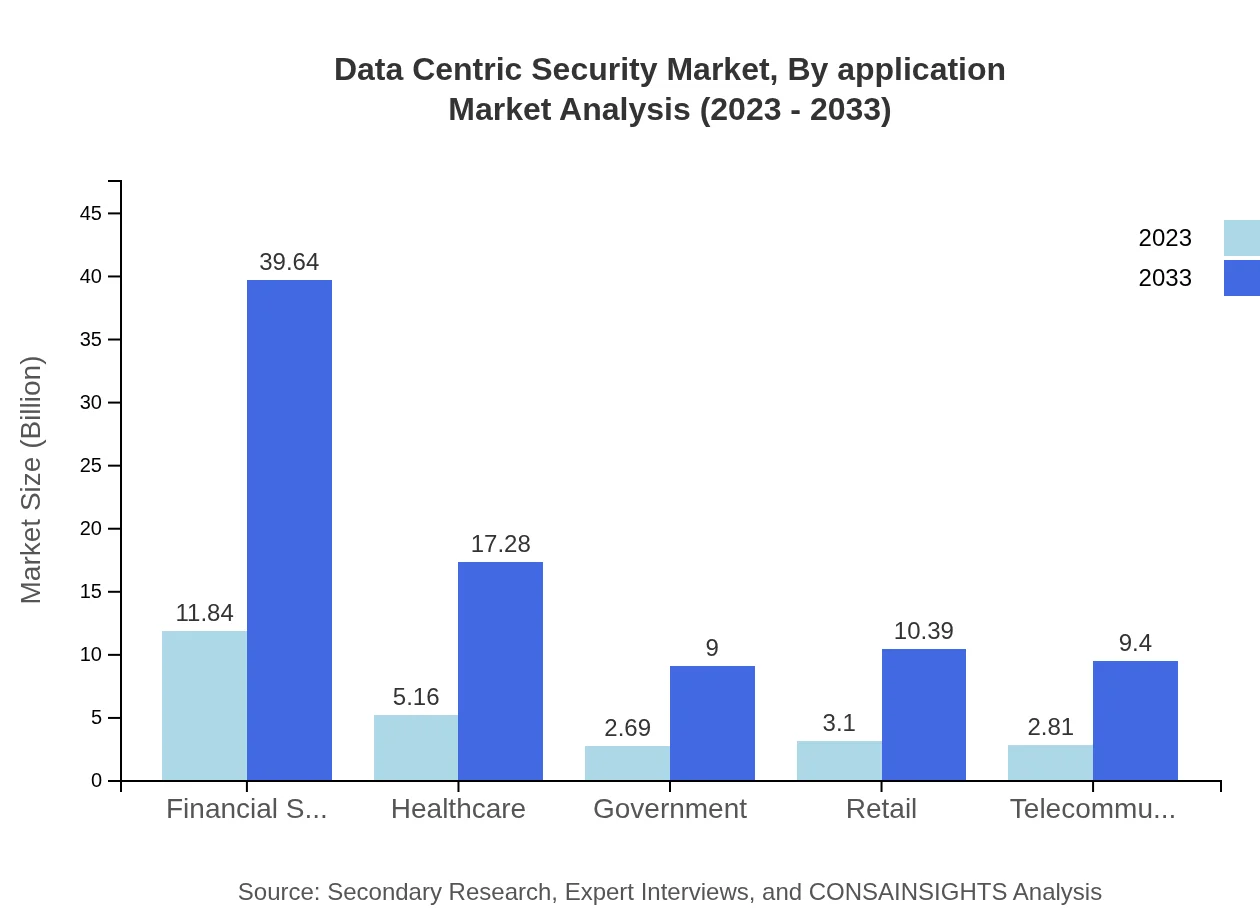
Data Centric Security Market Analysis By Application
Applications across various sectors such as Financial Services ($11.84 billion to $39.64 billion), Healthcare ($5.16 billion to $17.28 billion), Government ($2.69 billion to $9.00 billion), and Retail ($3.10 billion to $10.39 billion) are crucial drivers of Data Centric Security investments, reflecting the industry's widespread relevance in securing sensitive data.
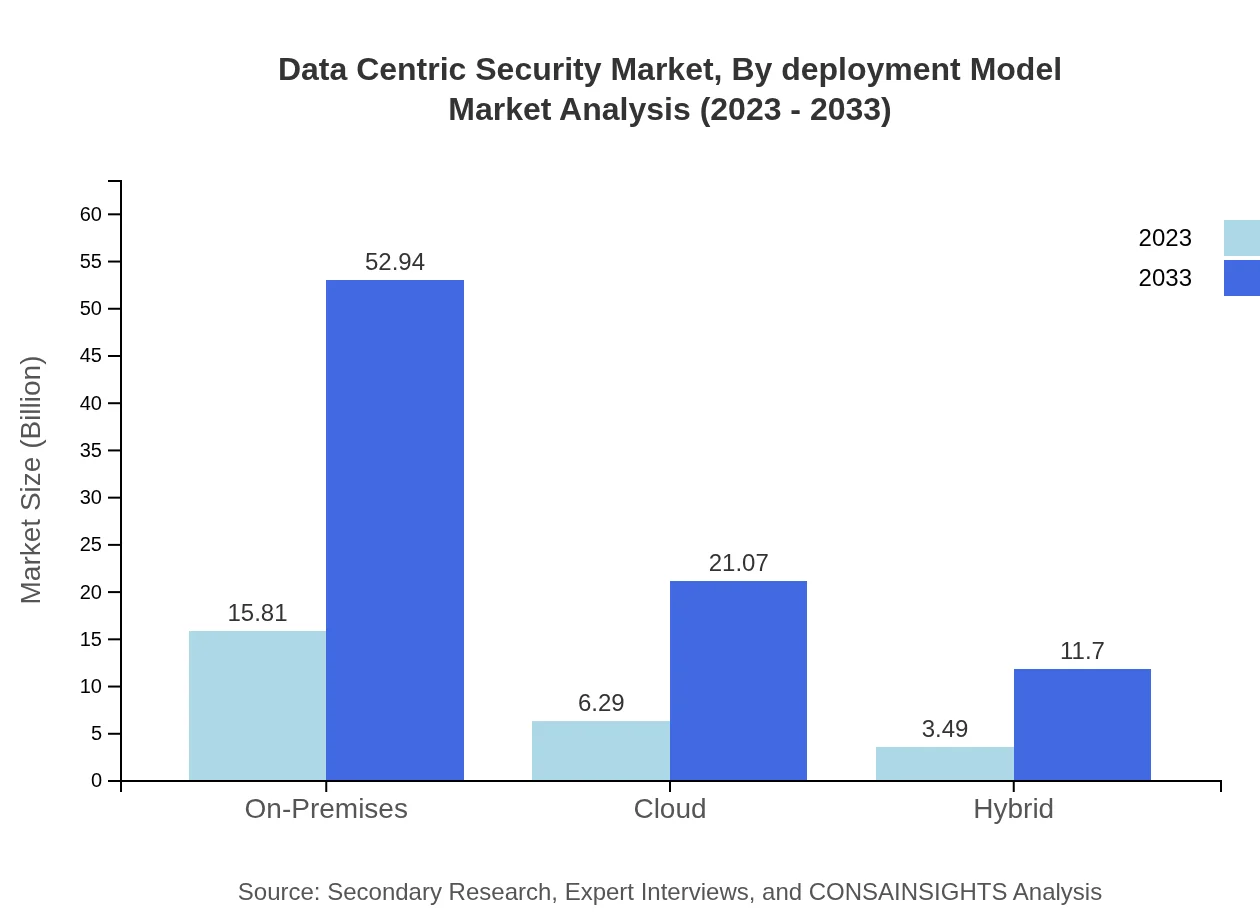
Data Centric Security Market Analysis By Deployment Model
The Data Centric Security market also breaks down into On-Premises, Cloud, and Hybrid deployment models. On-Premises solutions hold a significant share with a market size of $15.81 billion in 2023, expected to escalate to $52.94 billion by 2033. Cloud-based solutions are predicted to grow from $6.29 billion to $21.07 billion, while Hybrid models are set to rise from $3.49 billion to $11.70 billion.
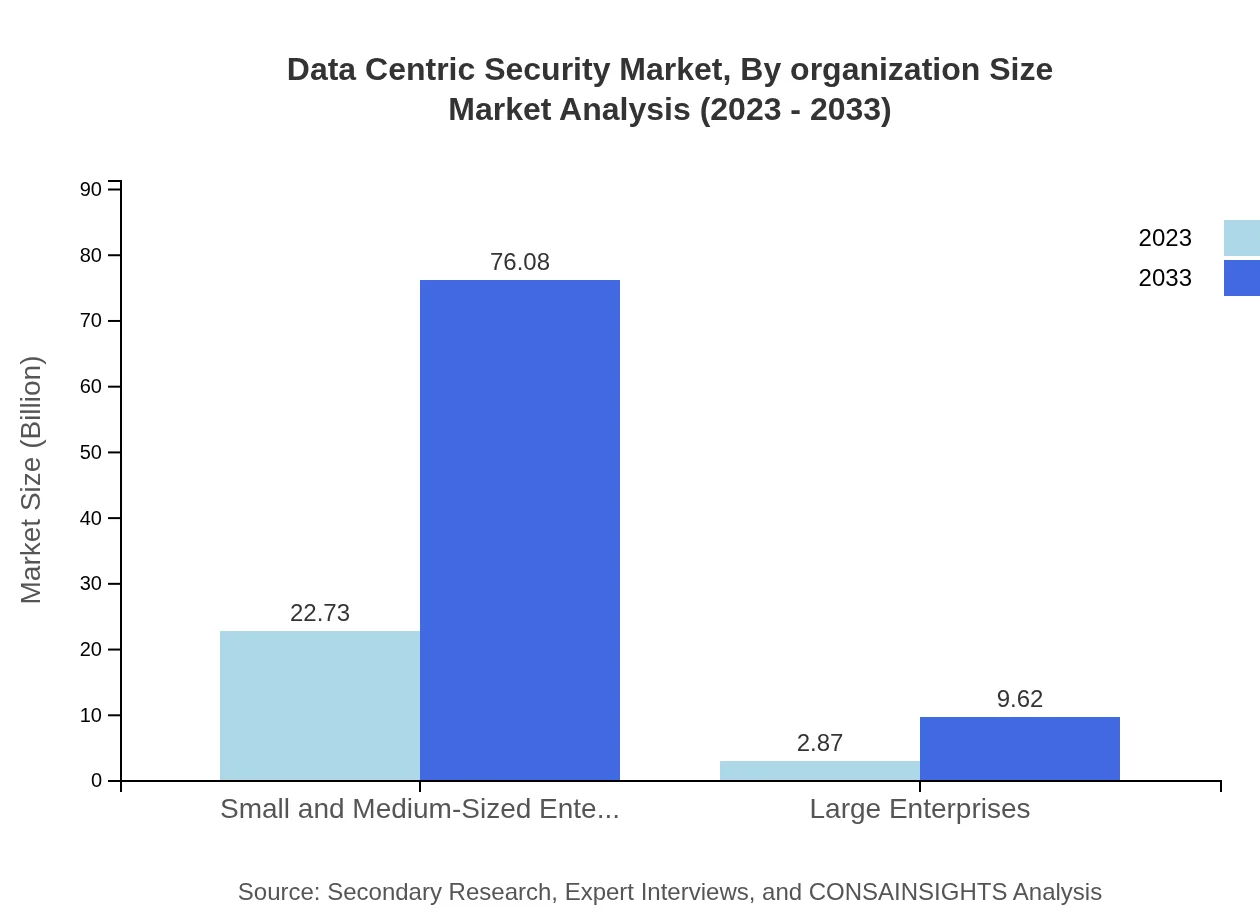
Data Centric Security Market Analysis By Organization Size
The segmentation by organization size reveals that Small and Medium-Sized Enterprises (SMEs) hold a substantial market share, with sizes projected to jump from $22.73 billion in 2023 to $76.08 billion by 2033. Large Enterprises, while smaller in proportion with $2.87 billion in 2023, are expected to grow to $9.62 billion by 2033.
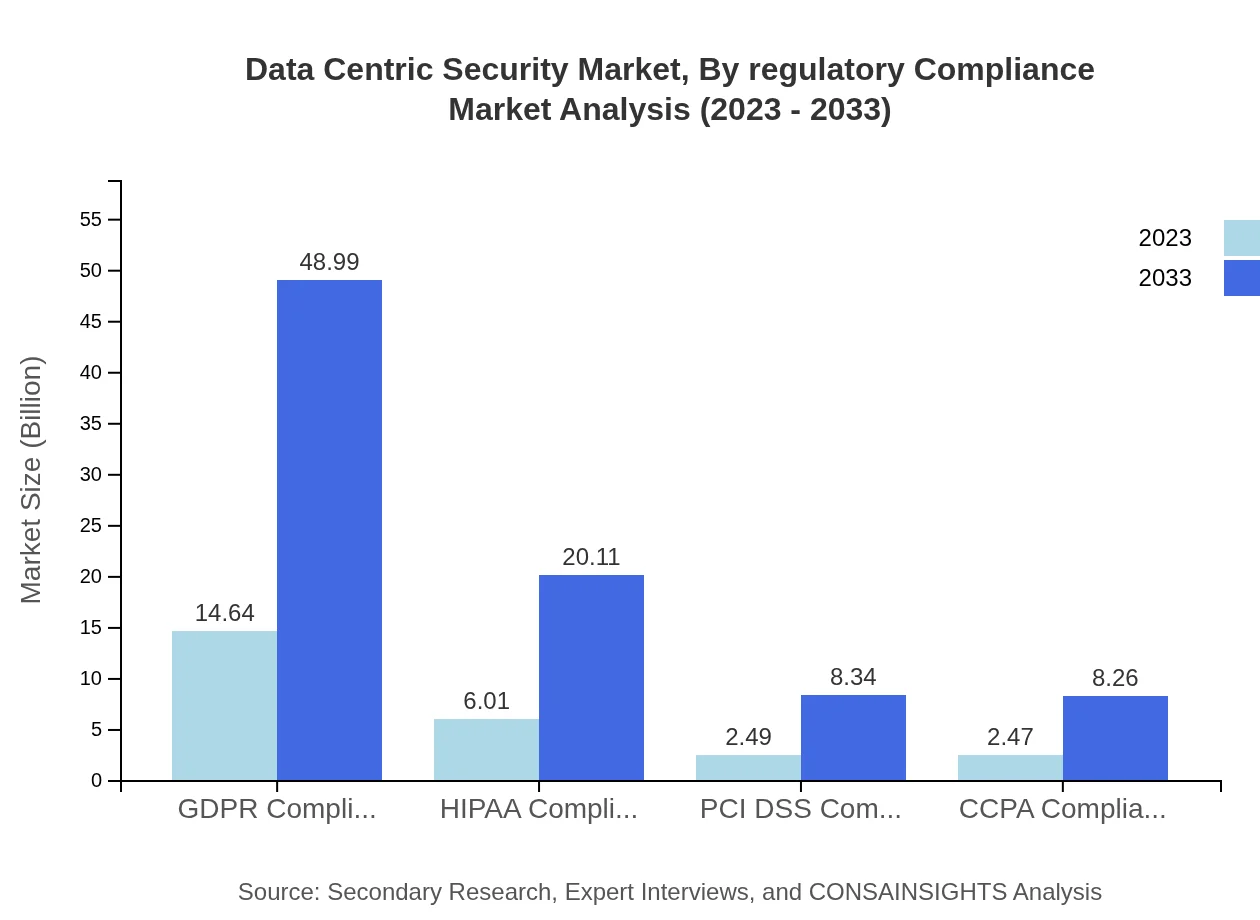
Data Centric Security Market Analysis By Regulatory Compliance
Among the various regulatory compliance standards, GDPR leads in size, expanding from $14.64 billion to $48.99 billion by 2033. Other standards like HIPAA, PCI DSS, and CCPA are essential as organizations strive to meet compliance while securing their sensitive data.
Data Centric Security Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Data Centric Security Industry
IBM Corporation:
A leading player in the Data Centric Security market, IBM offers a comprehensive portfolio of security solutions designed to protect sensitive data, with a strong focus on analytics and AI-driven security technologies.Symantec Corporation:
Symantec is known for its data protection and cybersecurity solutions. It focuses on advanced encryption, data loss prevention, and secured access mechanisms in various sectors.RSA Security LLC:
RSA specializes in cyber and data-centric security solutions, providing comprehensive identity and access management, fraud prevention, and encryption technologies.McAfee Corp.:
With a focus on endpoint protection and security management, McAfee enhances data-centric security through advanced threat intelligence and compliance solutions.We're grateful to work with incredible clients.









FAQs
What is the market size of data Centric Security?
The data-centric security market is valued at approximately $25.6 billion in 2023, with a projected CAGR of 12.3%. By 2033, the market is expected to expand significantly, illustrating robust growth opportunities within the sector.
What are the key market players or companies in this data Centric Security industry?
Key players in the data-centric security industry include leading technology firms, software providers, and security solution companies. These include large corporations and startups focusing on innovative security solutions tailored to data protection and compliance.
What are the primary factors driving the growth in the data Centric security industry?
The growth in the data-centric security market is driven by increasing data breaches, regulatory compliance requirements, digital transformation initiatives, and the need for enhanced data protection across various industries, resulting in a robust demand for security solutions.
Which region is the fastest Growing in the data Centric security market?
The fastest-growing region in the data-centric security market is North America, with a market size of $9.36 billion in 2023 projected to reach $31.32 billion by 2033. This growth is fueled by advanced technology adoption and heightened security demands.
Does ConsaInsights provide customized market report data for the data Centric Security industry?
Yes, ConsaInsights offers customized market report data tailored to specific needs within the data-centric security industry. Clients can request tailored insights and analysis to support their strategic decision-making processes.
What deliverables can I expect from this data Centric Security market research project?
Deliverables from the data-centric security market research project include detailed market analysis, key player profiles, regional and segment insights, trend forecasts, and actionable recommendations to aid strategic business goals.
What are the market trends of data Centric security?
Current trends in the data-centric security market include a shift towards cloud solutions, increased focus on GDPR and compliance regulations, the rise of AI-driven security tools, and a surge in demand for integrated security solutions across sectors.