Data Exfiltration Market Report
Published Date: 31 January 2026 | Report Code: data-exfiltration
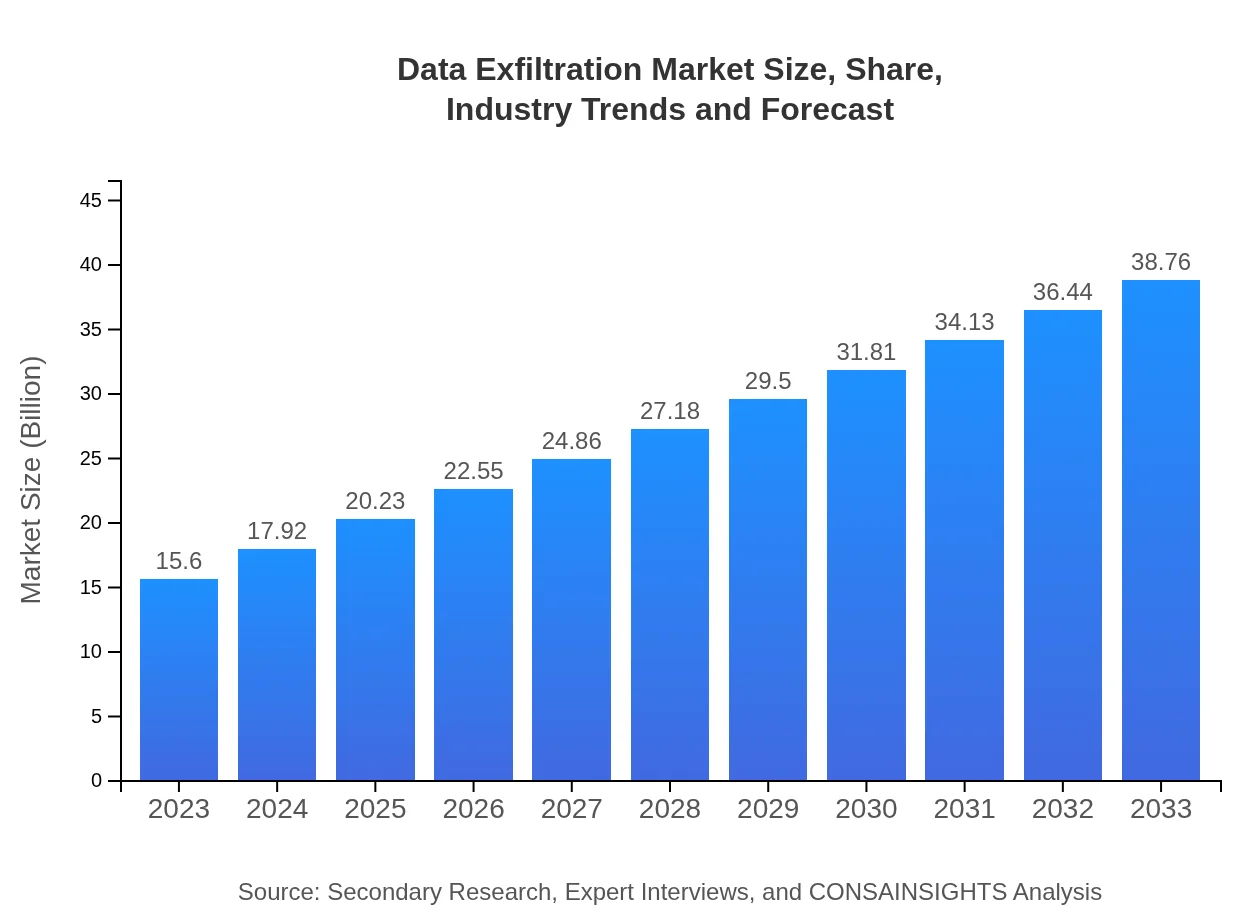
Data Exfiltration Market Size, Share, Industry Trends and Forecast to 2033
This report provides comprehensive insights into the Data Exfiltration market, covering an analysis spanning from 2023 to 2033, including market size, trends, and forecasts, alongside key industry players and technological advancements.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
| 2023 Market Size | $15.60 Billion |
| CAGR (2023-2033) | 9.2% |
| 2033 Market Size | $38.76 Billion |
| Top Companies | Symantec, Cisco, McAfee, Trend Micro |
| Last Modified Date | 31 January 2026 |
Data Exfiltration Market Overview
Customize Data Exfiltration Market Report market research report
- ✔ Get in-depth analysis of Data Exfiltration market size, growth, and forecasts.
- ✔ Understand Data Exfiltration's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Data Exfiltration
What is the Market Size & CAGR of Data Exfiltration market in 2023?
Data Exfiltration Industry Analysis
Data Exfiltration Market Segmentation and Scope
Tell us your focus area and get a customized research report.
Data Exfiltration Market Analysis Report by Region
Europe Data Exfiltration Market Report:
Europe's market is also significant, expected to grow from $5.32 billion in 2023 to $13.22 billion in 2033, driven largely by strict regulations surrounding data protection and privacy issues.Asia Pacific Data Exfiltration Market Report:
In the Asia Pacific region, the Data Exfiltration market is projected to grow from $2.90 billion in 2023 to $7.20 billion by 2033. The increasing digitization across various sectors and the awareness of data privacy regulations are driving this growth, promoting investment in advanced security solutions.North America Data Exfiltration Market Report:
North America leads the Data Exfiltration market, expected to grow from $5.32 billion in 2023 to $13.22 billion in 2033. The high concentration of key market players, stringent data protection regulations, and rising data breach incidents significantly fuel this market.South America Data Exfiltration Market Report:
The South American market is relatively smaller, with projections of growth from $0.02 billion in 2023 to $0.06 billion in 2033. However, increasing investments in cybersecurity initiatives indicate gradual growth alongside a growing acknowledgment of the importance of data protection.Middle East & Africa Data Exfiltration Market Report:
The Middle East and Africa market is anticipated to grow from $2.03 billion in 2023 to $5.05 billion by 2033. Increasing cyber threats and investments in digital infrastructure prompt organizations to enhance their defensive strategies, boosting the data exfiltration market.Tell us your focus area and get a customized research report.
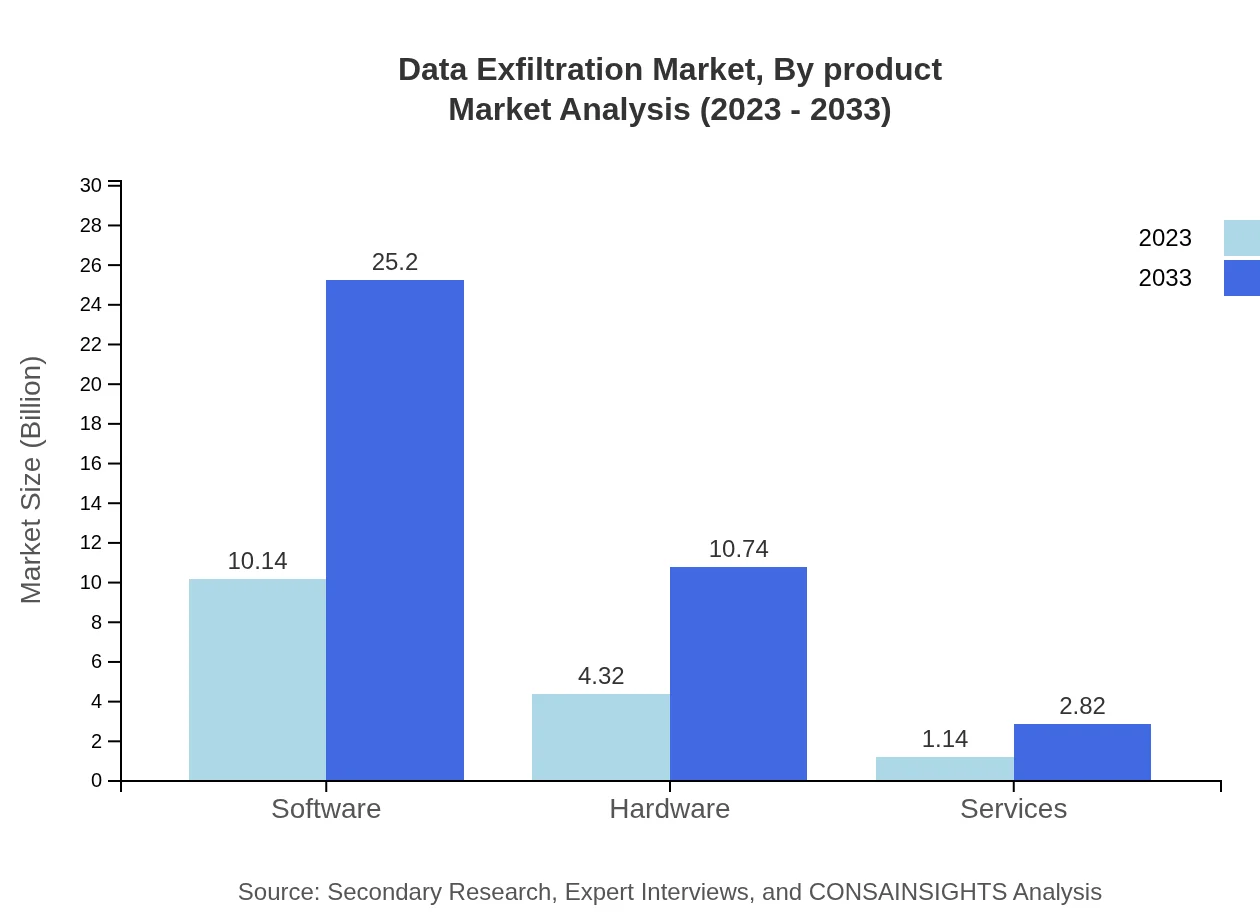
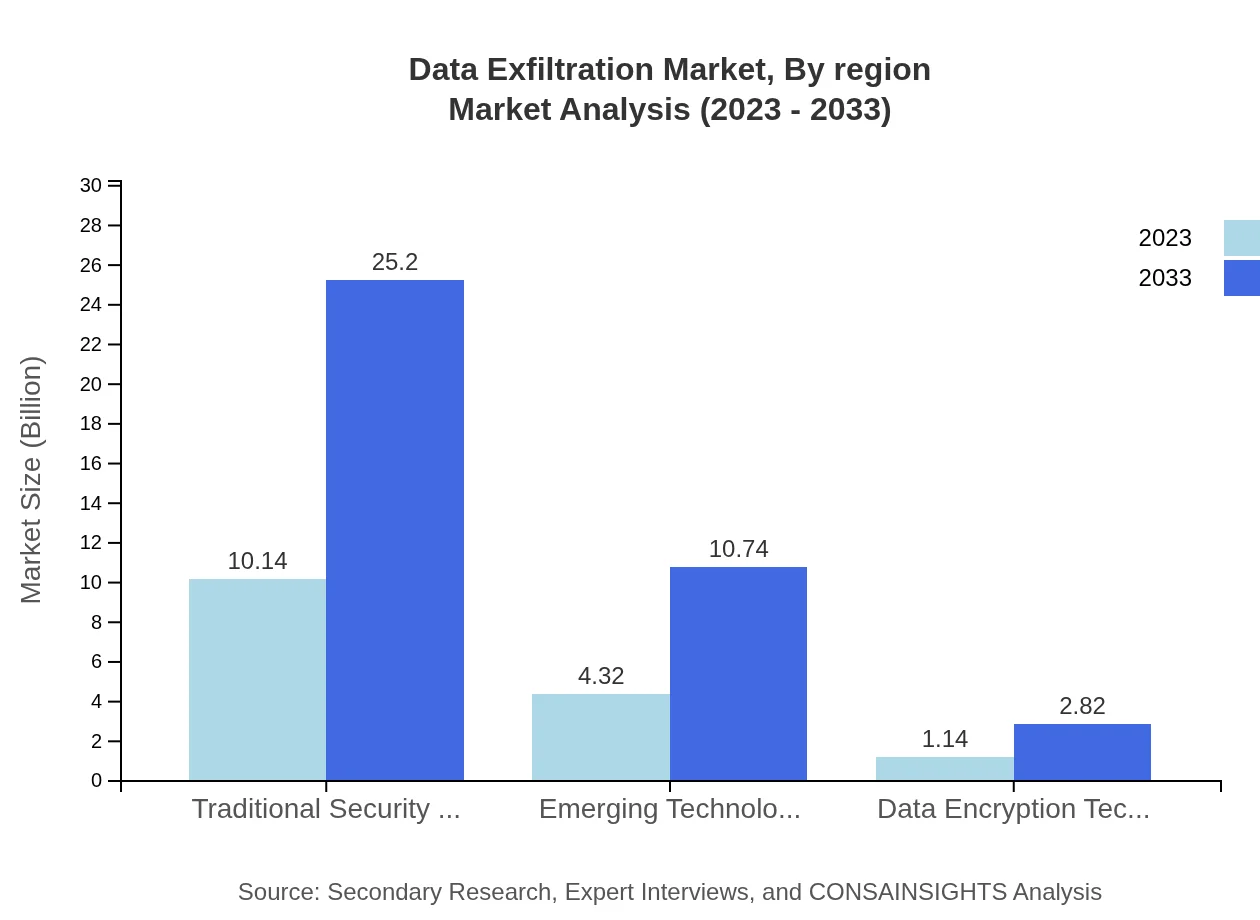
Data Exfiltration Market Analysis By Product
The Data Exfiltration market segment consists primarily of Traditional Security Technologies, Emerging Technologies, and Data Encryption Technologies. Traditional Security Technologies held the largest market share at 65.02% in 2023 while Emerging Technologies, comprising advanced AI-based solutions, are gaining momentum.
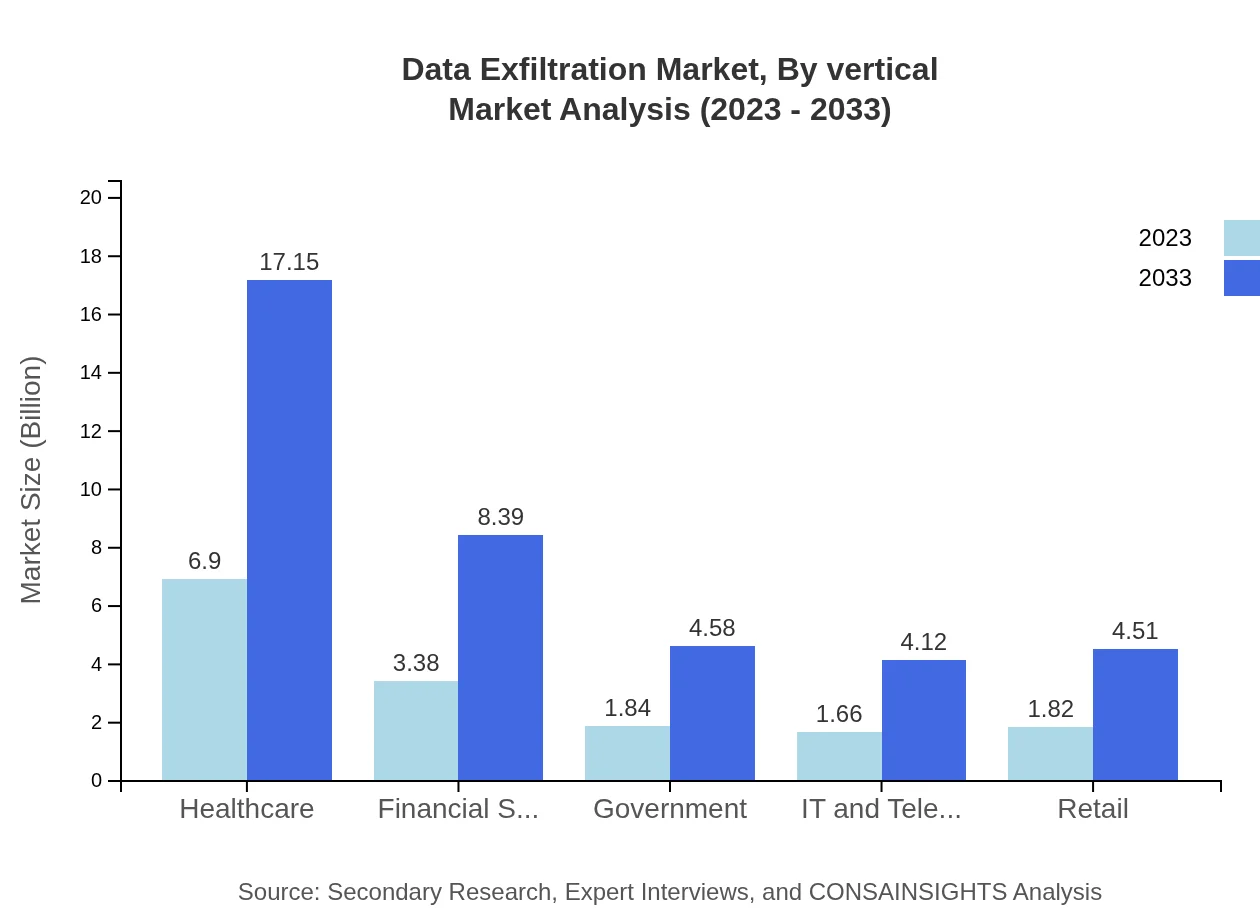
Data Exfiltration Market Analysis By Vertical
Different verticals such as Healthcare, Financial Services, IT and Telecom, and Retail have unique data protection needs. Notably, the Healthcare sector accounted for a significant share at 44.26% in 2023, highlighting the critical nature of data protection in this field.
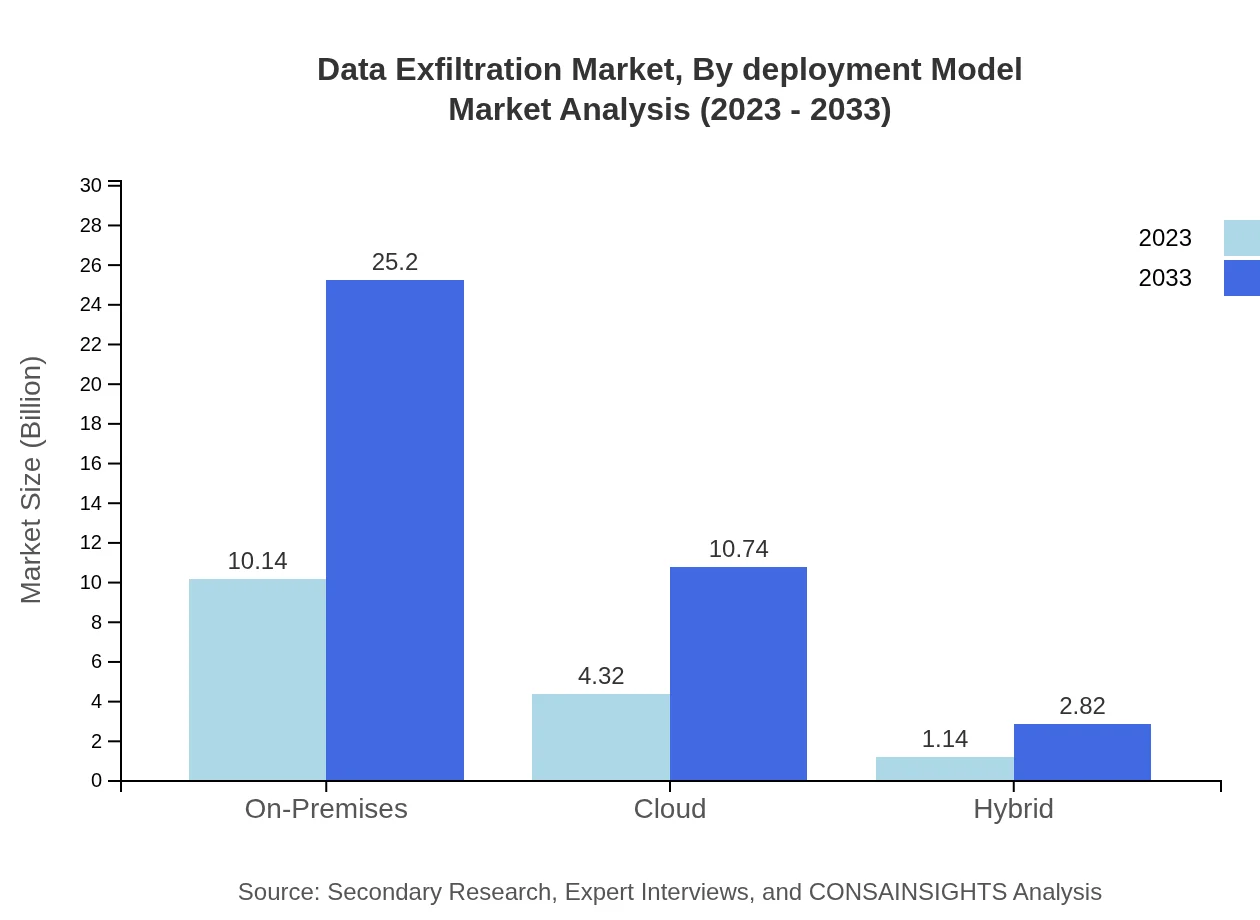
Data Exfiltration Market Analysis By Deployment Model
The market segments into On-Premises, Cloud, and Hybrid models. On-Premises solutions dominate with a market share of 65.02%, emphasizing enterprises' preference for localized data protection, while Cloud solutions are steadily gaining traction.
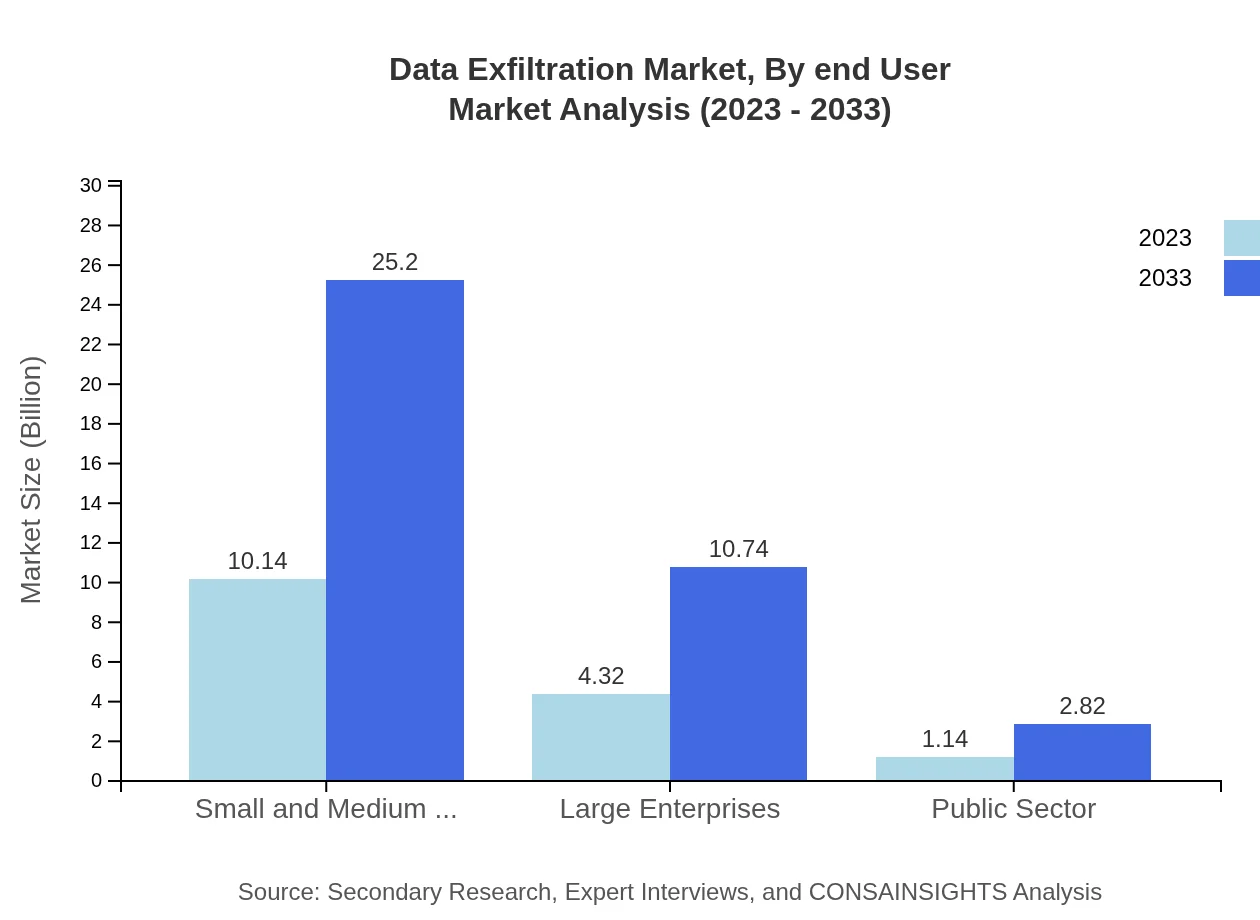
Data Exfiltration Market Analysis By End User
End-users of Data Exfiltration solutions include Small and Medium Businesses (SMBs), Large Enterprises, and the Public Sector. SMBs represent an essential segment with significant investments in data protection technologies as they increasingly recognize the risks of data loss.
Data Exfiltration Market Analysis By Region
Emerging Technologies such as Artificial Intelligence and Machine Learning are pivotal in the Data Exfiltration market, with opportunities for innovation and adaptation in response to new security challenges posed by rapid technology shifts in the industry.
Data Exfiltration Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Data Exfiltration Industry
Symantec:
A leader in cybersecurity solutions, Symantec offers various data protection products, including DLP, endpoint, and encryption technologies tailored for enterprise-level security.Cisco:
Cisco specializes in network security solutions, offering a range of products that include firewalls and intrusion prevention systems to protect against data exfiltration.McAfee:
Known for its wide array of cybersecurity solutions, McAfee provides comprehensive data protection and anti-malware technologies designed to secure data across various platforms.Trend Micro:
Trend Micro emphasizes advanced threat protection technologies to address the challenges of data exfiltration and safeguard sensitive information.We're grateful to work with incredible clients.









FAQs
What is the market size of data Exfiltration?
The data-exfiltration market is projected to grow from $15.6 billion in 2023, with a CAGR of 9.2%, indicating a robust demand for advanced security solutions over the next decade.
What are the key market players or companies in this data Exfiltration industry?
Key players in the data-exfiltration industry include leading cybersecurity firms that enhance data protection across various sectors, providing innovative solutions for businesses looking to secure sensitive information.
What are the primary factors driving the growth in the data Exfiltration industry?
Major growth drivers include increasing cyber threats, rising data privacy regulations, and the growing need for organizations to implement robust data security measures to protect sensitive information from unauthorized access.
Which region is the fastest Growing in the data Exfiltration market?
The fastest-growing region in the data-exfiltration market is Europe, projected to expand from $5.32 billion in 2023 to $13.22 billion by 2033, reflecting significant investment in cybersecurity.
Does ConsaInsights provide customized market report data for the data Exfiltration industry?
Yes, ConsaInsights offers customized market report data tailored to client needs in the data-exfiltration industry, ensuring relevant and actionable insights for strategic decision-making.
What deliverables can I expect from this data Exfiltration market research project?
Deliverables include comprehensive market analysis, trend assessments, competitive landscape evaluations, and segmented data insights, providing a thorough overview of the data-exfiltration market.
What are the market trends of data Exfiltration?
Market trends in data-exfiltration indicate an increasing reliance on cloud security solutions, advanced encryption technologies, and proactive threat monitoring, reflecting the shifting landscape of cybersecurity.