Deception Technology Market Report
Published Date: 31 January 2026 | Report Code: deception-technology
Deception Technology Market Size, Share, Industry Trends and Forecast to 2033
This report covers the Deception Technology market, providing insights into market size, trends, segmentation, and regional analysis. It forecasts growth from 2023 to 2033, helping stakeholders make informed decisions based on current and future market conditions.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
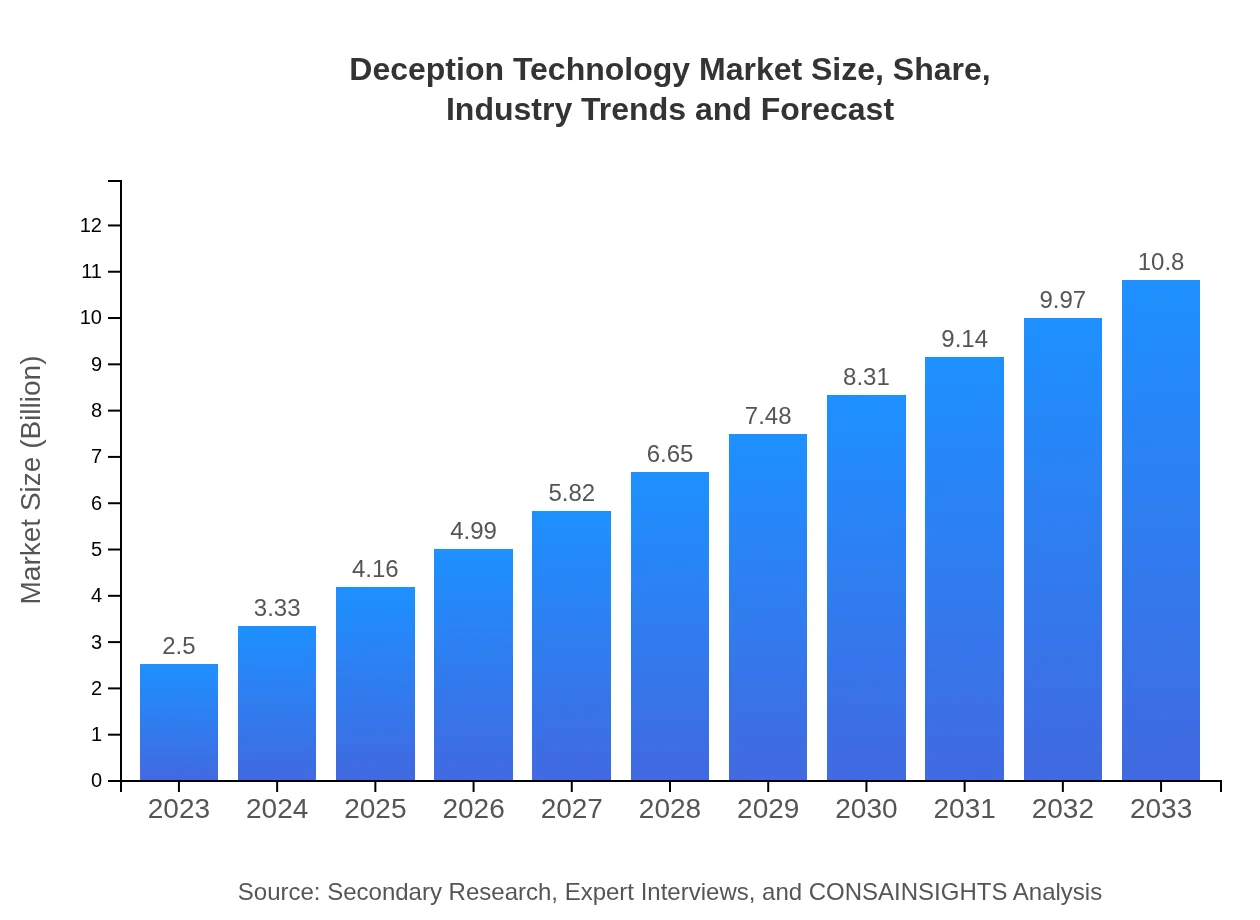
| 2023 Market Size | $2.50 Billion |
| CAGR (2023-2033) | 15% |
| 2033 Market Size | $10.80 Billion |
| Top Companies | Illusive Networks, Guardicore, Attivo Networks, Honeywell , Cymmetria |
| Last Modified Date | 31 January 2026 |
Deception Technology Market Overview
Customize Deception Technology Market Report market research report
- ✔ Get in-depth analysis of Deception Technology market size, growth, and forecasts.
- ✔ Understand Deception Technology's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Deception Technology
What is the Market Size & CAGR of Deception Technology market in 2023?
Deception Technology Industry Analysis
Deception Technology Market Segmentation and Scope
Tell us your focus area and get a customized research report.
Deception Technology Market Analysis Report by Region
Europe Deception Technology Market Report:
The European market is set to grow from $0.88 billion in 2023 to $3.82 billion by 2033. European nations are increasingly prioritizing cybersecurity strategies, especially with the implementation of GDPR. This regulatory pressure, combined with a high rate of cyber threats, has spurred significant investments in advanced cybersecurity solutions, including deception technology.Asia Pacific Deception Technology Market Report:
In the Asia Pacific region, the Deception Technology market is anticipated to grow from $0.42 billion in 2023 to $1.80 billion by 2033. The rising adoption of digital technologies in countries like China and India, coupled with increasing concerns over data breaches, is driving the demand. Enhanced investment in cybersecurity infrastructure by enterprises and government initiatives to promote cyber resilience further support market growth.North America Deception Technology Market Report:
North America represents a significant portion of the Deception Technology market, projected to rise from $0.85 billion in 2023 to $3.69 billion by 2033. The region is home to major cybersecurity firms that are continuously innovating their products. High-profile data breaches and stringent regulations are inspiring organizations to adopt deception technologies to strengthen their security postures.South America Deception Technology Market Report:
The South American Deception Technology market is expected to expand from $0.24 billion in 2023 to $1.04 billion by 2033. Growing awareness regarding data privacy and security is leading organizations to invest in advanced cybersecurity measures. Sectors like finance and e-commerce are driving this growth, as they face escalating cyber threats and regulatory demands.Middle East & Africa Deception Technology Market Report:
In the Middle East and Africa, the Deception Technology market is projected to increase from $0.10 billion in 2023 to $0.45 billion by 2033. The growing threat landscape due to rising cybercrime and initiatives taken by governments to improve cybersecurity frameworks are key drivers for market growth in this region.Tell us your focus area and get a customized research report.
Deception Technology Market Analysis By Product Type
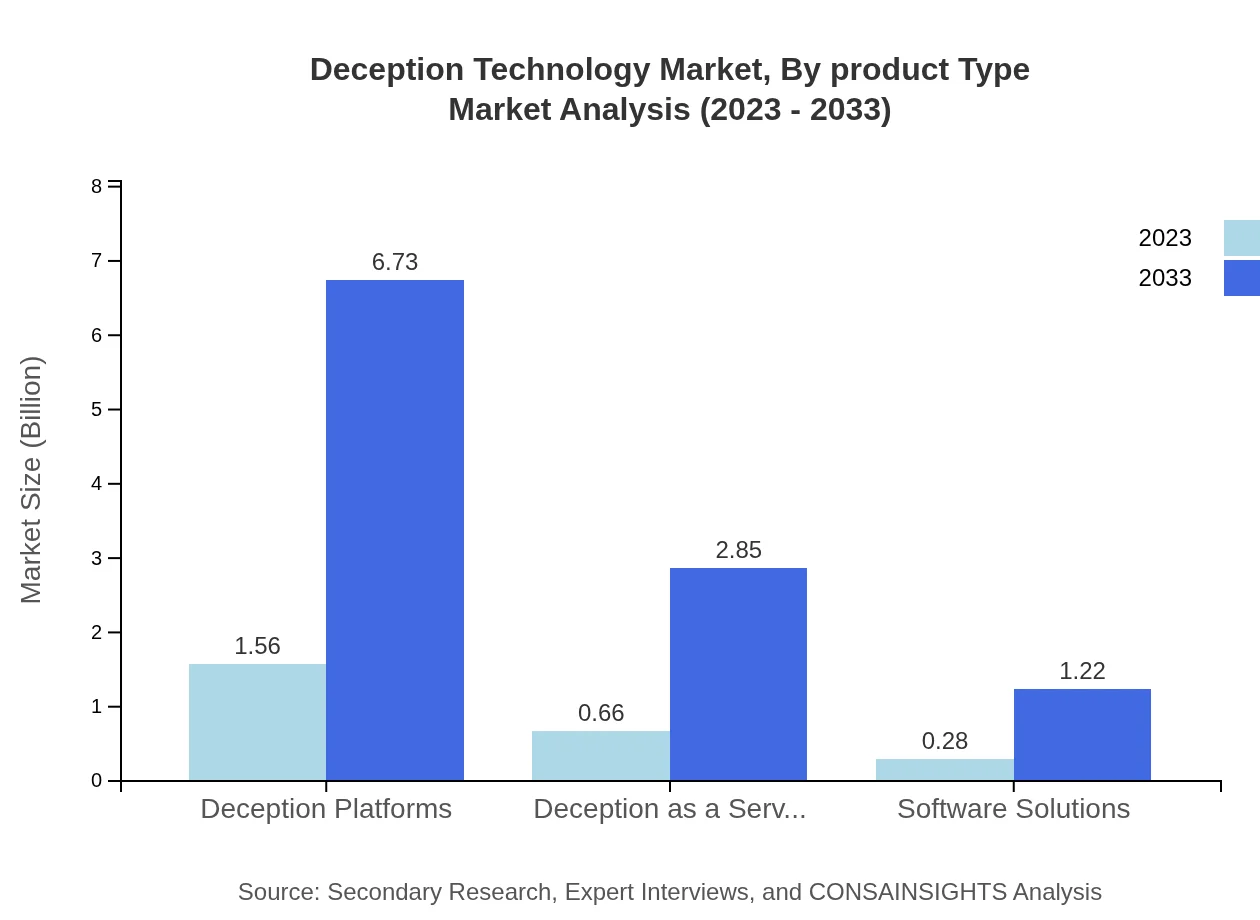
In the Deception Technology market, the product type segment includes categories such as Deception Platforms, Deception as a Service, and Software Solutions. Deception Platforms lead the market, expected to grow from $1.56 billion in 2023 to $6.73 billion by 2033, capturing a significant market share. Deception as a Service (DaaS), gaining traction for its low-cost model, is projected to expand from $0.66 billion in 2023 to $2.85 billion by 2033. Software solutions, while smaller, are also anticipated to see growth, reflecting organizations' transition towards integrated security frameworks.
Deception Technology Market Analysis By Industry Vertical
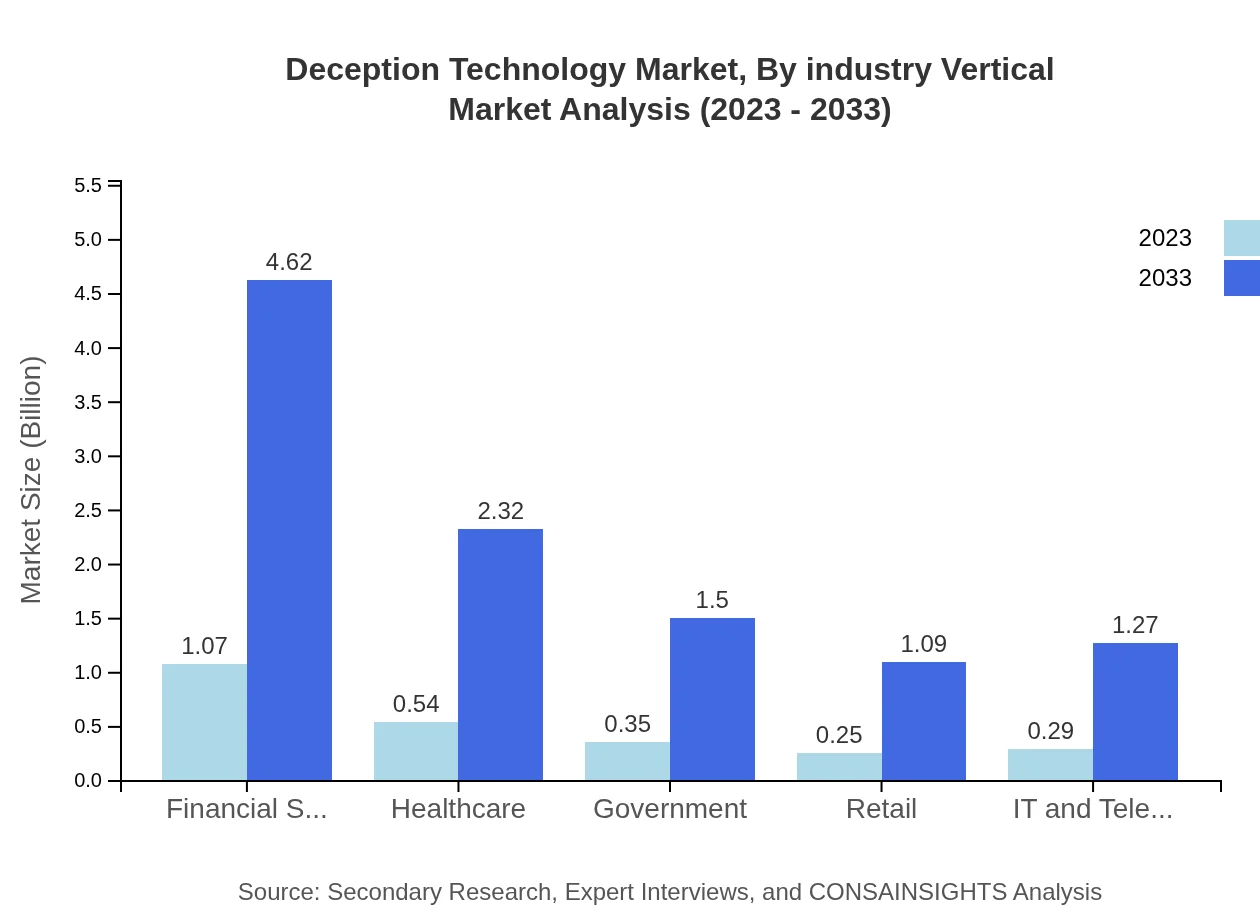
The industry vertical analysis identifies sectors such as Financial Services, Healthcare, Government, and Retail as major consumers of Deception Technology. Financial Services dominate the market, expected to grow from $1.07 billion in 2023 to $4.62 billion by 2033, primarily due to regulatory pressures and the need for data protection. Other sectors are also witnessing rising investments as organizations recognize the value of proactive threat detection.
Deception Technology Market Analysis By Deployment Model
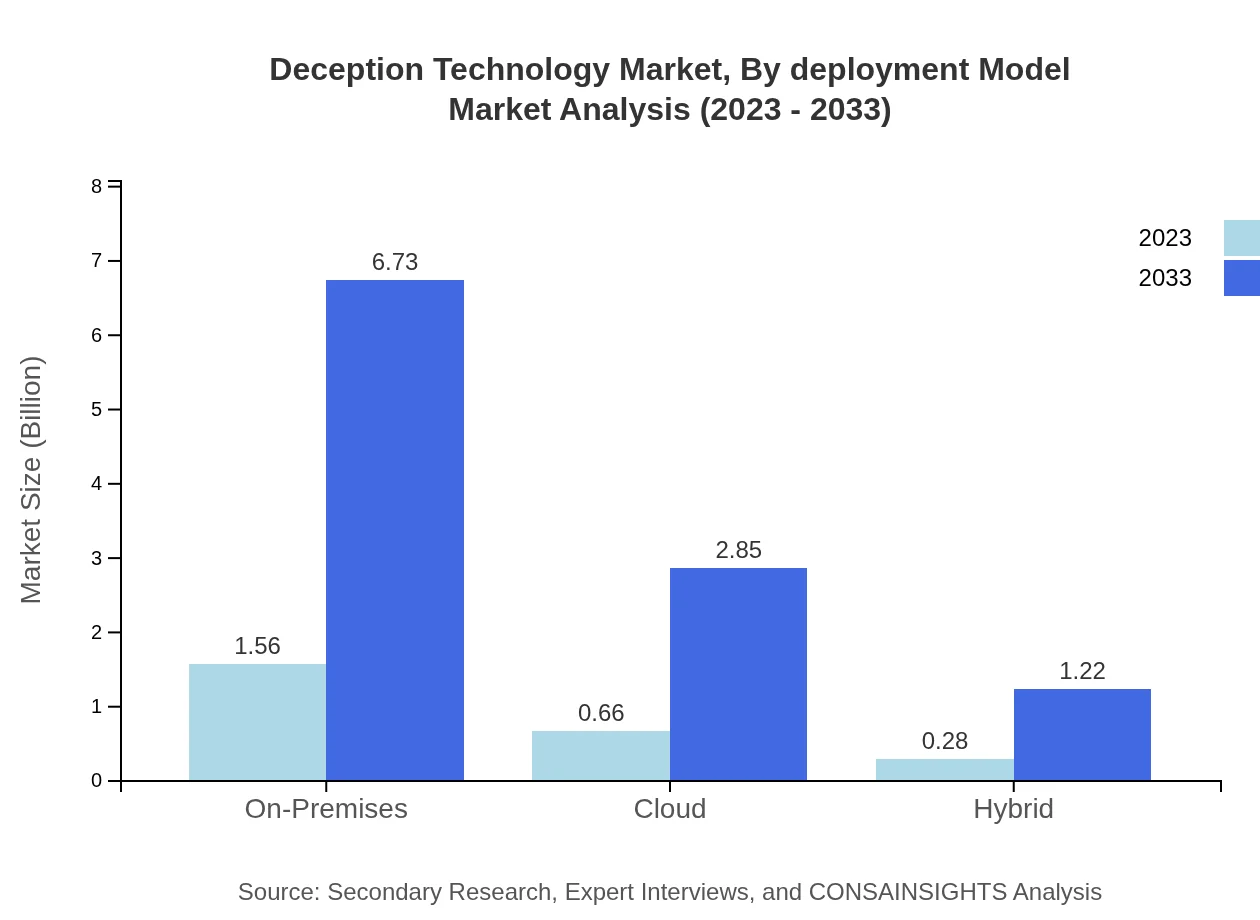
Deployment models are a critical segmentation, encompassing On-Premises, Cloud, and Hybrid approaches. The On-Premises model is poised to maintain its lead, from $1.56 billion in 2023 to $6.73 billion by 2033, owing to existing security infrastructure investments. Cloud-based and Hybrid models, capturing attention for their flexibility, are projected to rise significantly, adapting to the needs of modern organizations.
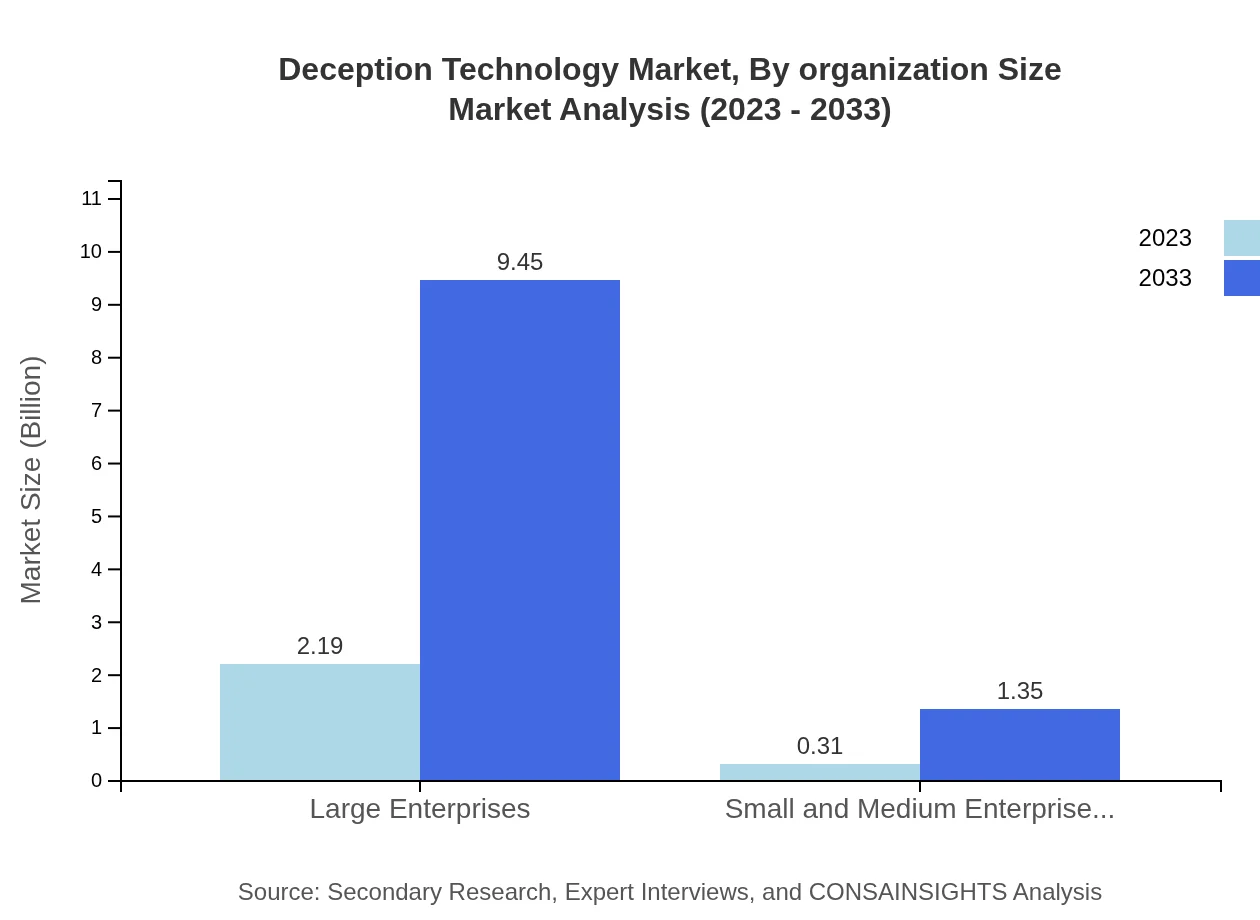
Deception Technology Market Analysis By Organization Size
The market analysis also examines organization sizes, where Large Enterprises account for the majority share, projecting growth from $2.19 billion in 2023 to $9.45 billion by 2033. Small and Medium Enterprises (SMEs) are also experiencing growth, particularly due to increasing affordability and awareness of cybersecurity threats, expected to grow considerably in the same period.
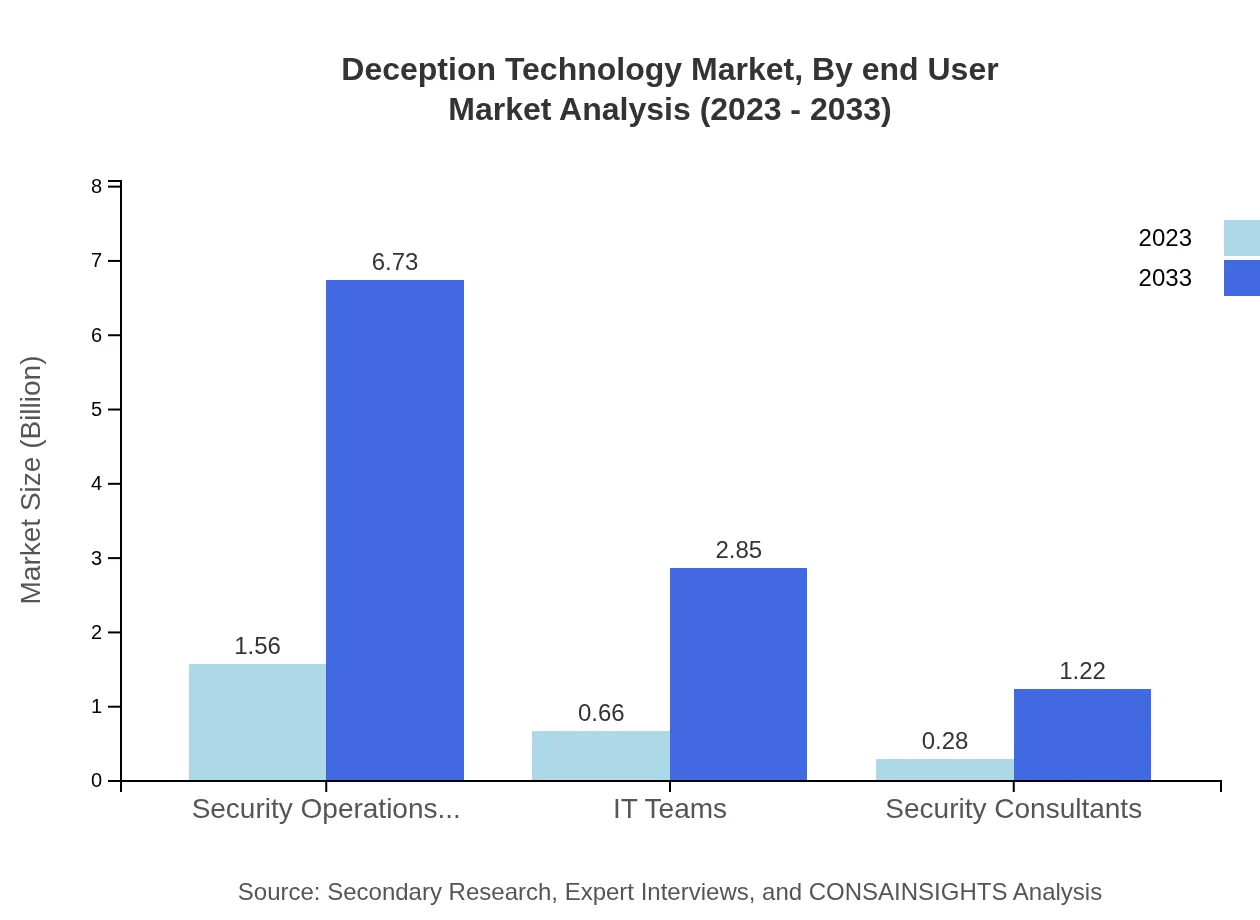
Deception Technology Market Analysis By End User
End-users of Deception Technology vary across sectors including finance, healthcare, government, retail, and IT & Telecom. The financial services sector is a leading end-user, reflecting an emphasis on safeguarding sensitive customer data. Each end-user segment contributes significantly to market expansion as awareness increases regarding cyber risk management.
Deception Technology Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Deception Technology Industry
Illusive Networks:
A pioneer in deception technology, Illusive Networks specializes in delivering proactive cybersecurity solutions that disrupt cyber attackers' exploitation attempts.Guardicore:
Guardicore offers a comprehensive platform for data center and cloud security with a focus on deception technology to enhance threat detection and response capabilities.Attivo Networks:
Attivo Networks provides Identity Detection and Response solutions, utilizing deception technology to combat identity and credential theft, making significant strides in the cybersecurity space.Honeywell :
Honeywell integrates deception technology within its advanced security solutions, enabling organizations to enhance security protocols against cyber threats.Cymmetria:
Cymmetria specializes in deception-based cybersecurity solutions, using a combination of deception technology and threat intelligence to protect enterprises.We're grateful to work with incredible clients.









FAQs
What is the market size of deception Technology?
The global deception technology market is valued at approximately $2.5 billion in 2023, with a projected CAGR of 15% leading to substantial growth by 2033.
What are the key market players or companies in this deception Technology industry?
Key players in the deception technology industry include established cybersecurity firms, emerging start-ups specializing in advanced threat detection, and technology conglomerates that integrate deception technologies into their security portfolios.
What are the primary factors driving the growth in the deception technology industry?
Growth is primarily driven by increasing cyber threats, the need for advanced security measures, regulatory compliance demands, and the rising adoption of cloud services across various sectors.
Which region is the fastest Growing in deception technology?
Asia Pacific is the fastest-growing region in deception technology, projected to grow from $0.42 billion in 2023 to $1.80 billion by 2033, indicating a robust CAGR.
Does ConsaInsights provide customized market report data for the deception Technology industry?
Yes, ConsaInsights offers customized market reports tailored to specific needs and requirements in the deception technology industry, ensuring detailed insights and analyses.
What deliverables can I expect from this deception Technology market research project?
Expect comprehensive reports including market size and forecasts, competitor analysis, trend identification, regional insights, and detailed segmentation data tailored for strategic decision-making.
What are the market trends of deception Technology?
Current market trends include the increasing convergence of deception technology with AI-driven analytics, growing awareness among enterprises, and the shift towards cloud-based solutions in cybersecurity.