Embedded Security Market Report
Published Date: 31 January 2026 | Report Code: embedded-security
Embedded Security Market Size, Share, Industry Trends and Forecast to 2033
This report provides a comprehensive analysis of the Embedded Security market from 2023 to 2033, including insights into market size, growth potential, segmentation, regional analysis, technology trends, and key players shaping the industry.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
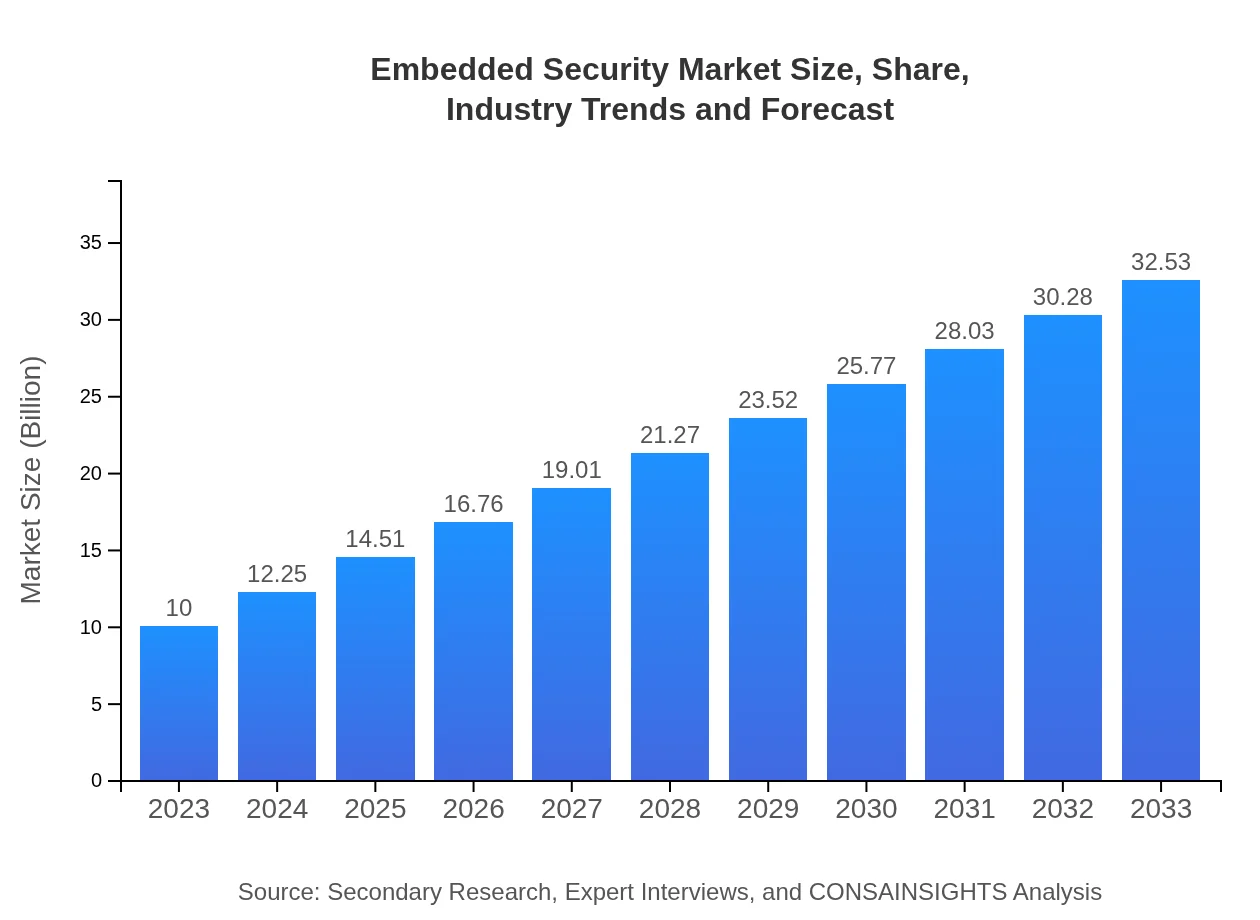
| 2023 Market Size | $10.00 Billion |
| CAGR (2023-2033) | 12% |
| 2033 Market Size | $32.53 Billion |
| Top Companies | Microsoft, IBM, Intel, Thales, NXP Semiconductors |
| Last Modified Date | 31 January 2026 |
Embedded Security Market Overview
Customize Embedded Security Market Report market research report
- ✔ Get in-depth analysis of Embedded Security market size, growth, and forecasts.
- ✔ Understand Embedded Security's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Embedded Security
What is the Market Size & CAGR of Embedded Security market in 2023?
Embedded Security Industry Analysis
Embedded Security Market Segmentation and Scope
Tell us your focus area and get a customized research report.
Embedded Security Market Analysis Report by Region
Europe Embedded Security Market Report:
Europe is expected to see considerable growth in the Embedded Security market, escalating from USD 2.43 billion in 2023 to USD 7.90 billion by 2033. Regulatory requirements such as GDPR are prompting businesses to adopt enhanced security measures, driving the demand for embedded security solutions across various sectors.Asia Pacific Embedded Security Market Report:
The Asia Pacific region is witnessing robust growth in the Embedded Security market, projected from USD 1.91 billion in 2023 to USD 6.20 billion by 2033. The surge stems from rising IoT deployment and manufacturing sectors emphasizing security measures. Countries like China and India are investing significantly in cybersecurity infrastructure.North America Embedded Security Market Report:
The North America region is leading the Embedded Security market, with a growth forecast from USD 3.37 billion in 2023 to USD 10.96 billion by 2033. The presence of major technology firms and a strong focus on innovation in cybersecurity solutions contribute to this growth. The US government’s emphasis on national cybersecurity initiatives also boosts local demand.South America Embedded Security Market Report:
In South America, the Embedded Security market is projected to grow from USD 0.91 billion in 2023 to USD 2.95 billion by 2033. The region's increasing digitalization and the growing demand for smart devices are driving market expansion. Key players are entering the market to leverage opportunities in various sectors such as healthcare and retail.Middle East & Africa Embedded Security Market Report:
The Middle East and Africa market for Embedded Security will grow from USD 1.39 billion in 2023 to USD 4.52 billion by 2033, reflecting a growing awareness of cyber threats. Companies seek robust solutions amidst escalating cyber attack challenges, particularly in critical sectors like oil, gas, and telecommunications.Tell us your focus area and get a customized research report.
Embedded Security Market Analysis By Product
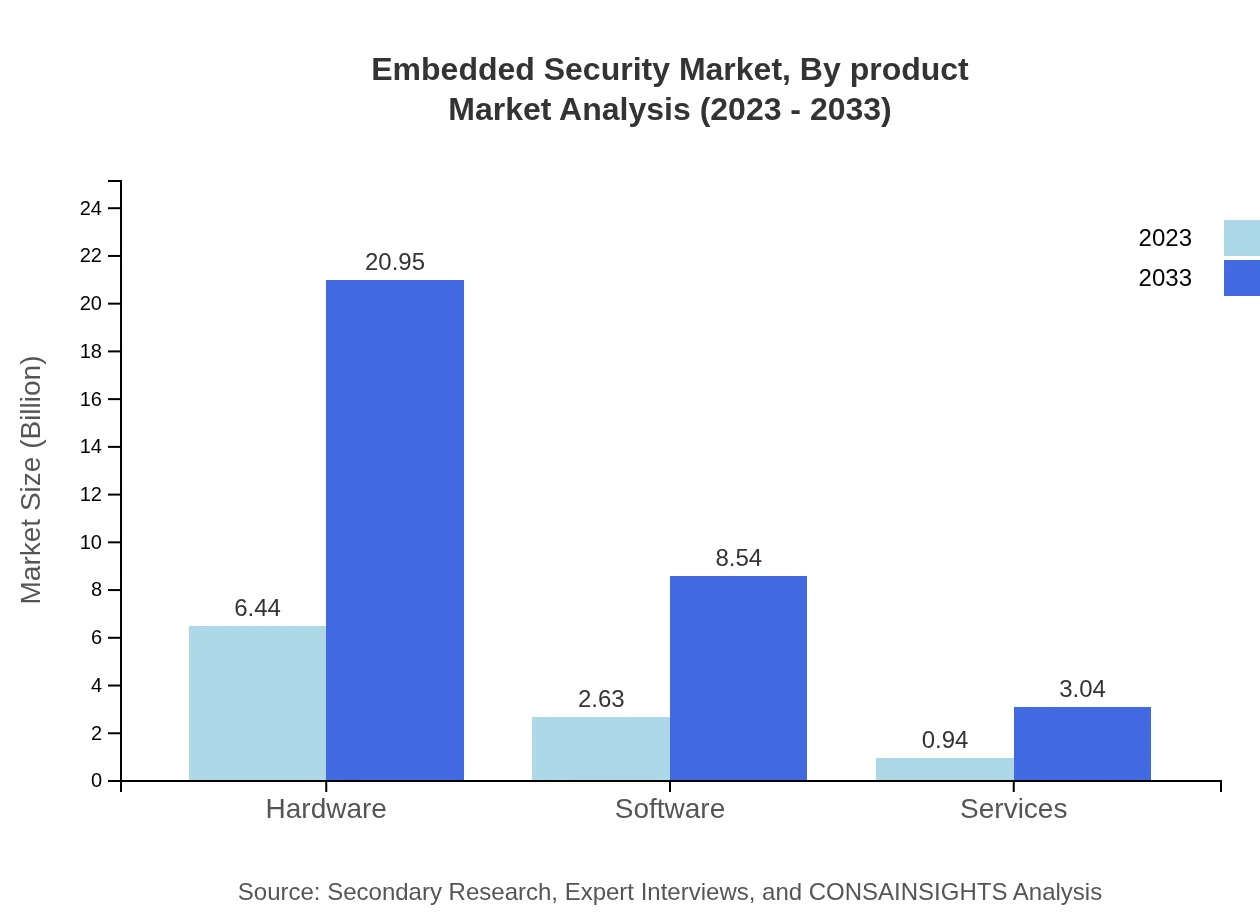
The Embedded Security market's product segmentation includes hardware, software, and services. In 2023, hardware accounted for 64.39% of the market share worth USD 6.44 billion, projected to grow to USD 20.95 billion by 2033, maintaining its significant share. Software-based security solutions and service offerings comprise 26.26% and 9.35%, respectively, with steady growth anticipated.
Embedded Security Market Analysis By Application
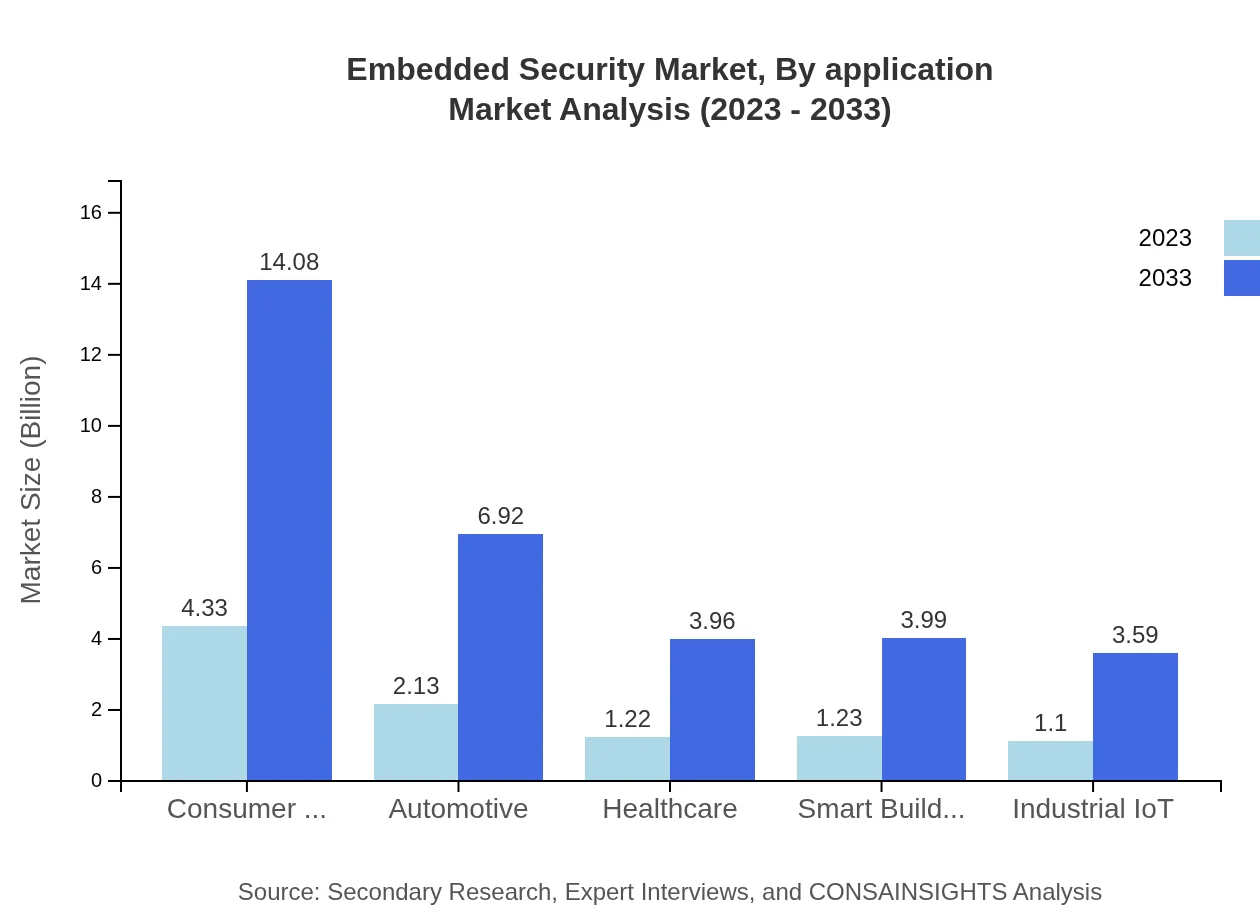
Applications are segmented into automotive, industrial, consumer goods, healthcare and life sciences, IT and telecom, and smart buildings. For automotive applications, the market size grew from USD 4.33 billion in 2023 to USD 14.08 billion by 2033, enjoying a significant 43.29% share as manufacturers prioritize integrating security into vehicles. Healthcare applications also represent substantial growth potential, moving from USD 1.23 billion to USD 3.99 billion.
Embedded Security Market Analysis By Technology
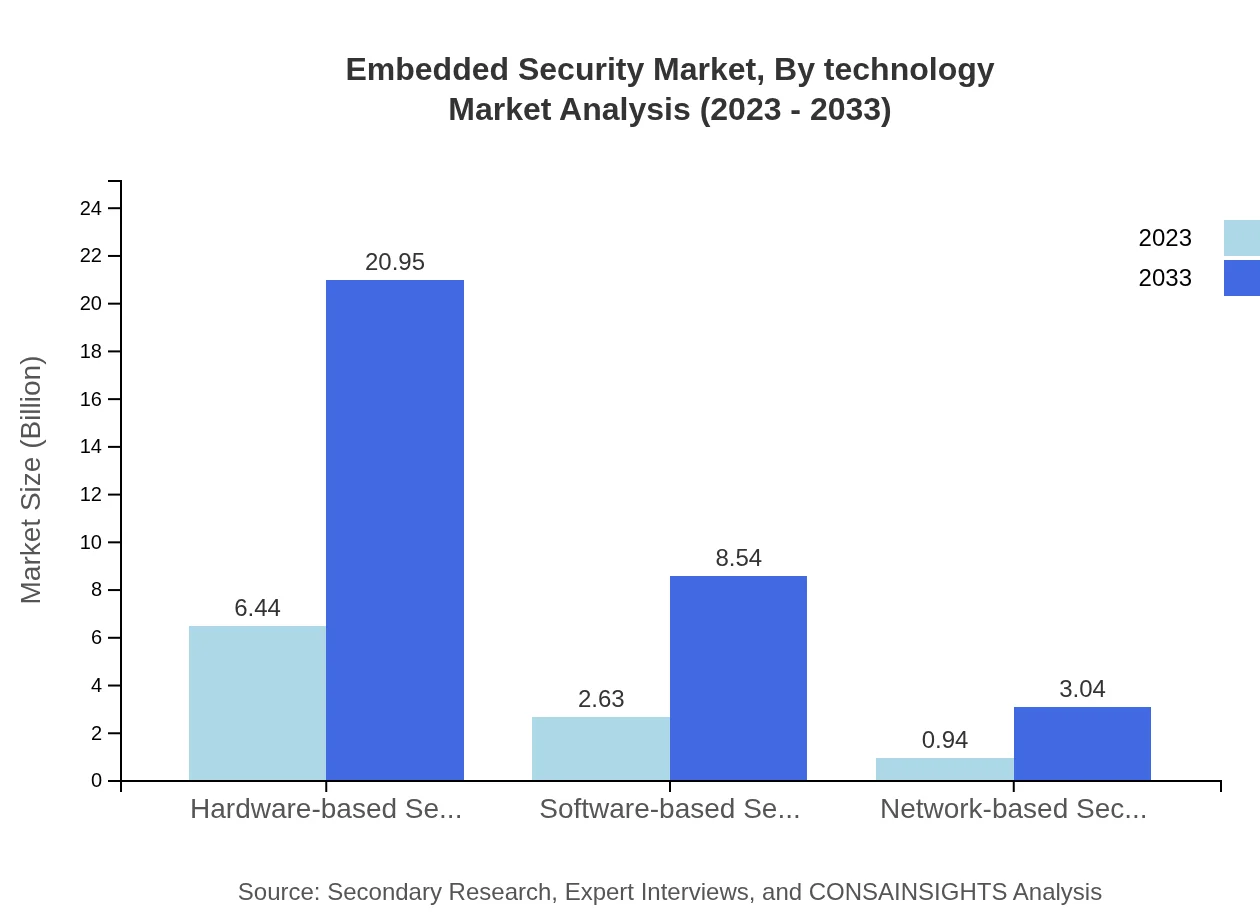
The Embedded Security market can be segmented by technology into hardware-based security, software-based security, and network-based security solutions. The hardware-based security market leads with 64.39% in 2023, reaching USD 6.44 billion and projected to grow to USD 20.95 billion by 2033. Software-based security solutions while having a smaller share at 26.26%, are expected to significantly expand due to innovations in software solutions.
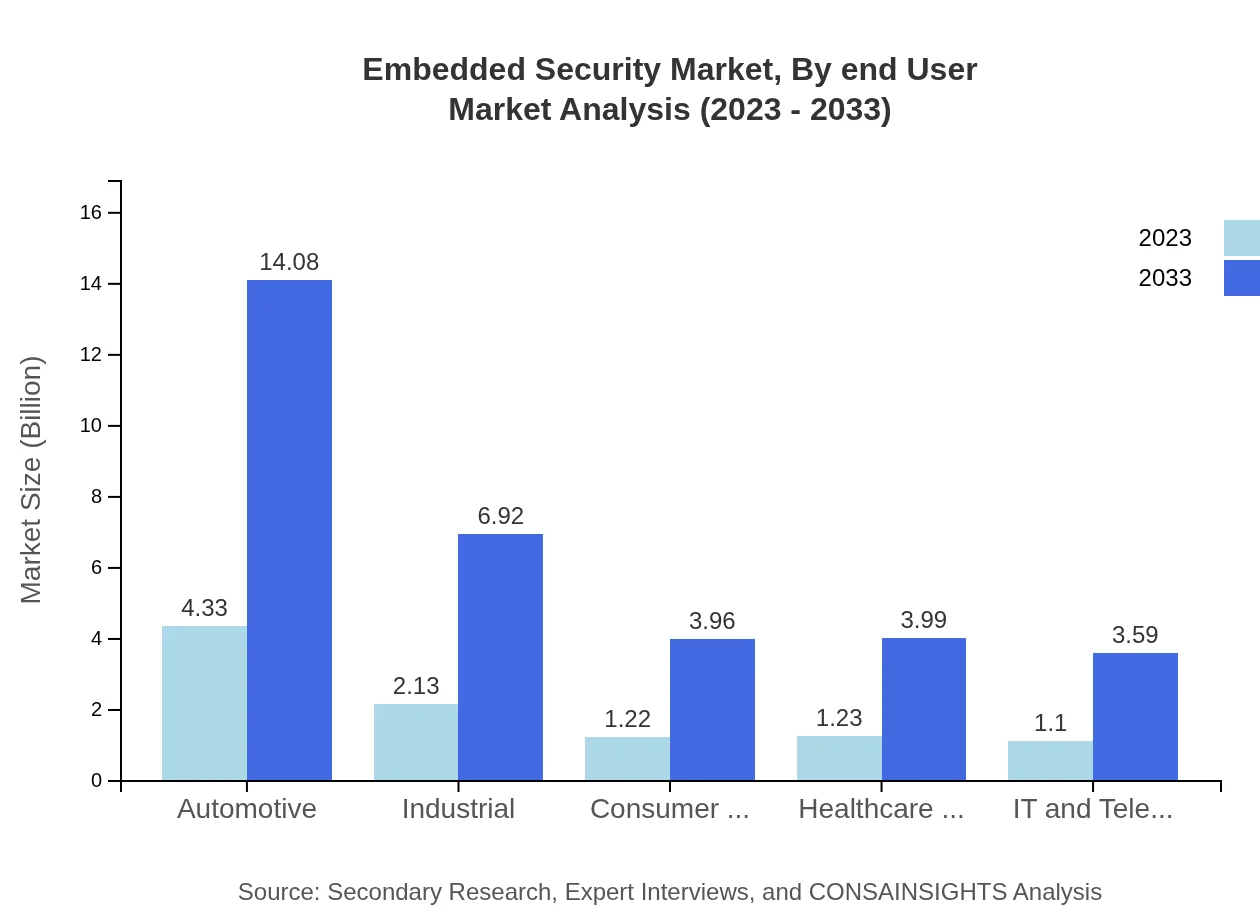
Embedded Security Market Analysis By End User
End-user segmentation includes automotive, healthcare, industrial IoT, and consumer electronics. Automotive remains a crucial segment, expanding from USD 2.13 billion in 2023 to USD 6.92 billion illustrating a 21.26% market share. Each end-user industry highlights diverse security requirements, driving tailored product solutions and innovation.
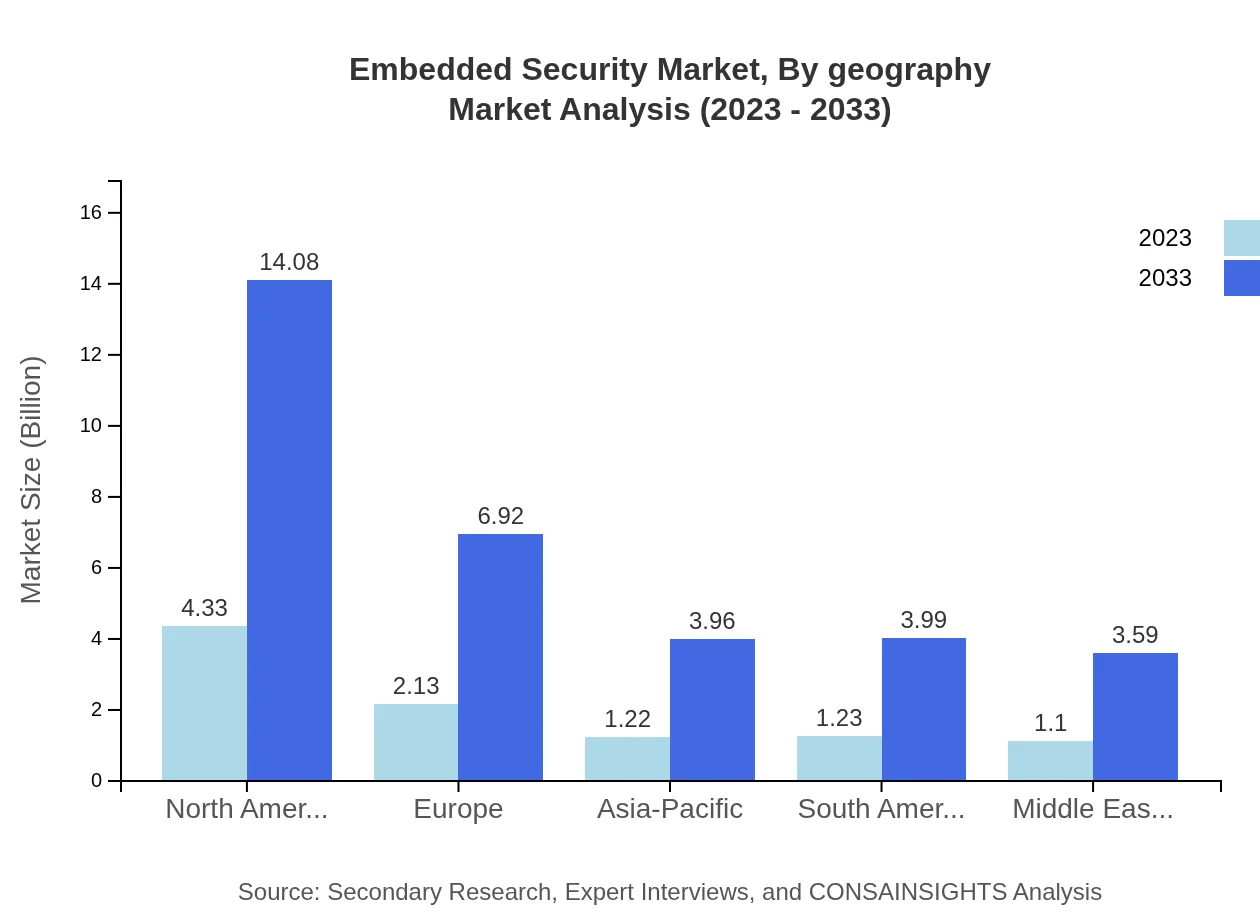
Embedded Security Market Analysis By Geography
Geographically, North America holds the largest market share by value, followed closely by Europe and Asia-Pacific. North America's focus on technological advancements and stringent regulations form a solid foundation for market growth, while Europe increases its market presence through robust privacy laws. Meanwhile, the Asia Pacific region showcases significant expansion opportunities driven by rising smartphone usage and IoT applications.
Embedded Security Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Embedded Security Industry
Microsoft:
Microsoft is a leading player in cybersecurity, providing end-to-end security solutions integrated with their enterprise solutions to enhance the security of embedded systems.IBM:
IBM offers comprehensive security solutions focusing on risk management, threat detection, and data protection, essential for embedded devices across industries.Intel:
Intel plays a pivotal role in Embedded Security with hardware solutions that enhance security on devices through secure hardware enclaves and associated services.Thales:
Thales specializes in advanced cybersecurity solutions for embedded systems in defense, aerospace, and automotive sectors, focusing on secure data transmission.NXP Semiconductors:
NXP provides secure embedded solutions with a comprehensive portfolio of hardware security components, driving the growth of secure IoT applications.We're grateful to work with incredible clients.









FAQs
What is the market size of embedded Security?
The embedded security market size is projected to reach USD 10 billion by 2033, growing at a CAGR of 12% from 2023, when it was valued at USD 10 billion.
What are the key market players or companies in this embedded Security industry?
Key players in the embedded security market include companies such as Microsoft, Intel Corporation, NXP Semiconductors, STMicroelectronics, and Texas Instruments, which are at the forefront of technological advancements and product development.
What are the primary factors driving the growth in the embedded Security industry?
The growth in the embedded security market is driven by increasing demand for IoT devices, heightened data security concerns, advancements in hardware security technologies, and regulatory compliance requirements across sectors like automotive and healthcare.
Which region is the fastest Growing in the embedded Security?
North America is the fastest-growing region in the embedded security market, expected to grow from USD 4.33 billion in 2023 to USD 14.08 billion by 2033, driven by technological innovation and a robust demand for security solutions.
Does ConsaInsights provide customized market report data for the embedded Security industry?
Yes, ConsaInsights offers customized market report data tailored to the specific needs of clients in the embedded security industry, including detailed analysis, forecasts, and insights that align with their strategic objectives.
What deliverables can I expect from this embedded Security market research project?
From this market research project, you can expect comprehensive reports, trend analysis, segment breakdowns, strategic insights, and actionable recommendations aimed at optimizing decision-making and strategic planning.
What are the market trends of embedded Security?
Market trends in embedded security include the growth of hardware-based solutions, increasing emphasis on software-based security, advancements in network security, and rising demand within sectors such as automotive and consumer electronics.