Encryption Software Market Report
Published Date: 31 January 2026 | Report Code: encryption-software
Encryption Software Market Size, Share, Industry Trends and Forecast to 2033
This report provides a comprehensive overview of the Encryption Software market, detailing current trends, future forecasts, regional analyses, and market segmentation insights from 2023 to 2033.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
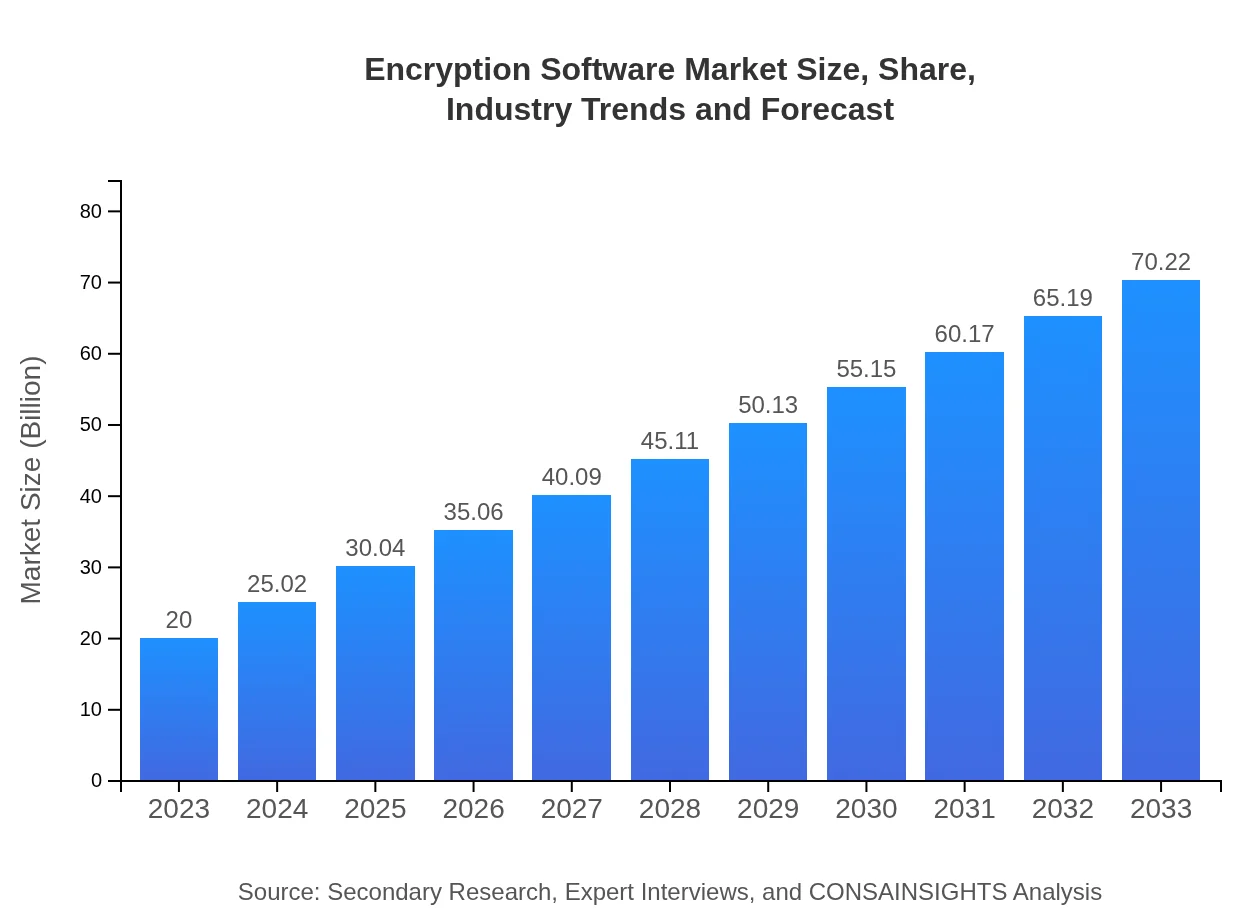
| 2023 Market Size | $20.00 Billion |
| CAGR (2023-2033) | 12.8% |
| 2033 Market Size | $70.22 Billion |
| Top Companies | Symantec Corporation, McAfee LLC, IBM Corporation, Microsoft Corporation, Thales Group |
| Last Modified Date | 31 January 2026 |
Encryption Software Market Overview
Customize Encryption Software Market Report market research report
- ✔ Get in-depth analysis of Encryption Software market size, growth, and forecasts.
- ✔ Understand Encryption Software's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Encryption Software
What is the Market Size & CAGR of Encryption Software market in 2023?
Encryption Software Industry Analysis
Encryption Software Market Segmentation and Scope
Tell us your focus area and get a customized research report.
Encryption Software Market Analysis Report by Region
Europe Encryption Software Market Report:
Europe's market, valued at $6.09 billion in 2023 and expected to grow to $21.39 billion by 2033, is driven by rigorous data protection regulations such as GDPR. The increasing number of data breaches has heightened the focus on cybersecurity, prompting businesses across various sectors to invest heavily in encryption technologies.Asia Pacific Encryption Software Market Report:
In the Asia Pacific, the Encryption Software market was valued at $3.44 billion in 2023 and is expected to grow to $12.08 billion by 2033. The region is witnessing an increase in cyber threats and stringent data compliance laws, driving demand for enhanced security solutions. Additionally, the growing adoption of cloud services in countries like India and China is significantly contributing to market growth.North America Encryption Software Market Report:
North America holds one of the largest shares of the Encryption Software market, starting at $7.56 billion in 2023 and anticipated to reach $26.54 billion by 2033. The region's growth is propelled by high adoption rates of advanced security technologies, a strong presence of major software vendors, and significant investments by enterprises in data protection measures.South America Encryption Software Market Report:
The South American market for Encryption Software, starting at $0.69 billion in 2023 and projected to rise to $2.44 billion by 2033, is rapidly expanding due to increasing awareness of data vulnerabilities. The adoption of encryption in sectors such as finance and healthcare is expected to accelerate, influenced by both local regulations and global compliance standards.Middle East & Africa Encryption Software Market Report:
The Middle East and Africa (MEA) region is projected to grow from $2.21 billion in 2023 to $7.77 billion by 2033. The growing adoption of cloud services, coupled with increasing concerns about data privacy and regulatory compliance, is favorably influencing the demand for encryption solutions in this region.Tell us your focus area and get a customized research report.
Encryption Software Market Analysis By Product
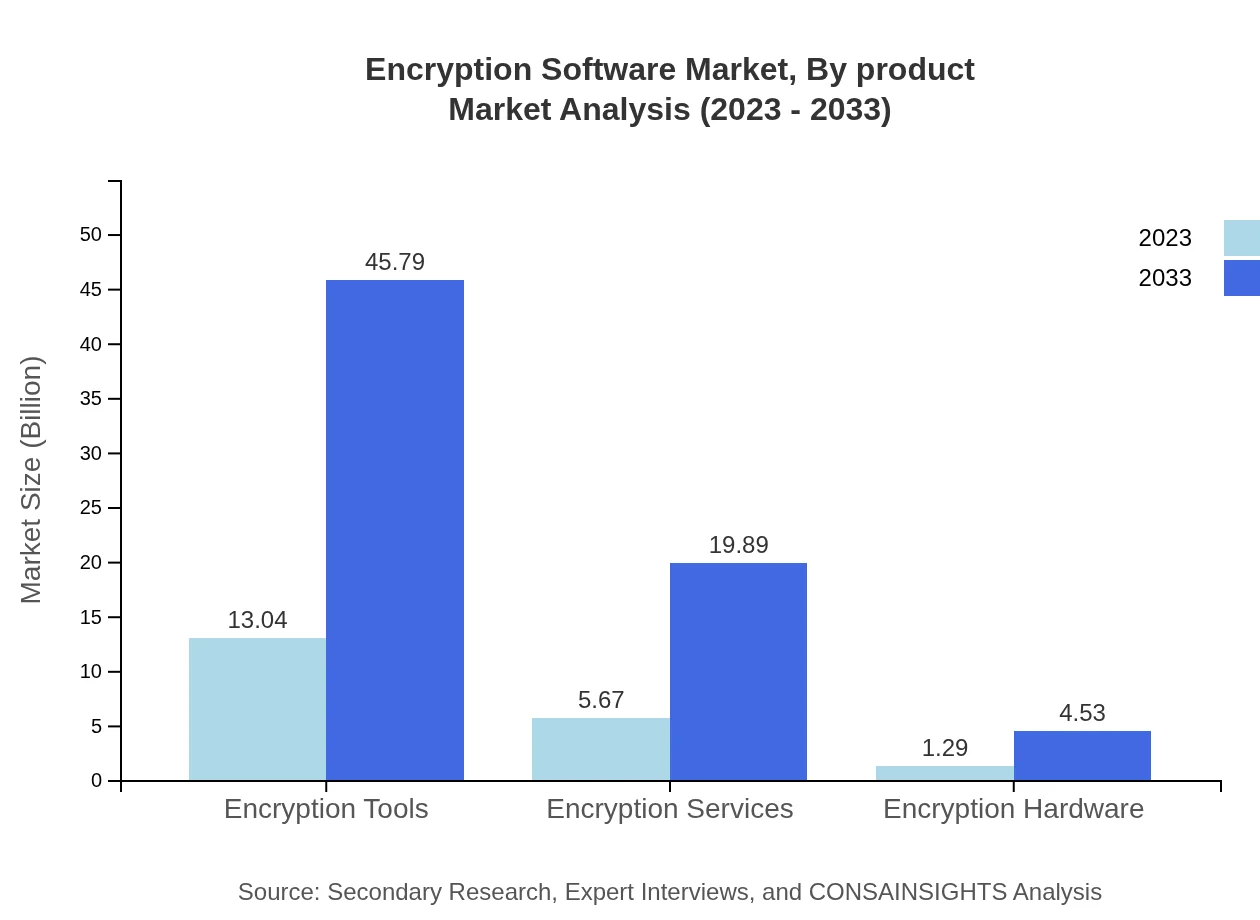
The Encryption Software Market is segmented into three main products: Encryption Tools, Encryption Services, and Encryption Hardware. Encryption Tools dominate the market with a size of $13.04 billion in 2023, growing to $45.79 billion by 2033. These tools are crucial in safeguarding data in transit and at rest. Encryption Services, starting at $5.67 billion with a growth projection to $19.89 billion by 2033, are essential for organizations seeking managed and specialized encryption solutions. Encryption Hardware, while smaller at $1.29 billion in 2023, is expected to grow to $4.53 billion, emphasizing a niche but critical area of market demand.
Encryption Software Market Analysis By Application
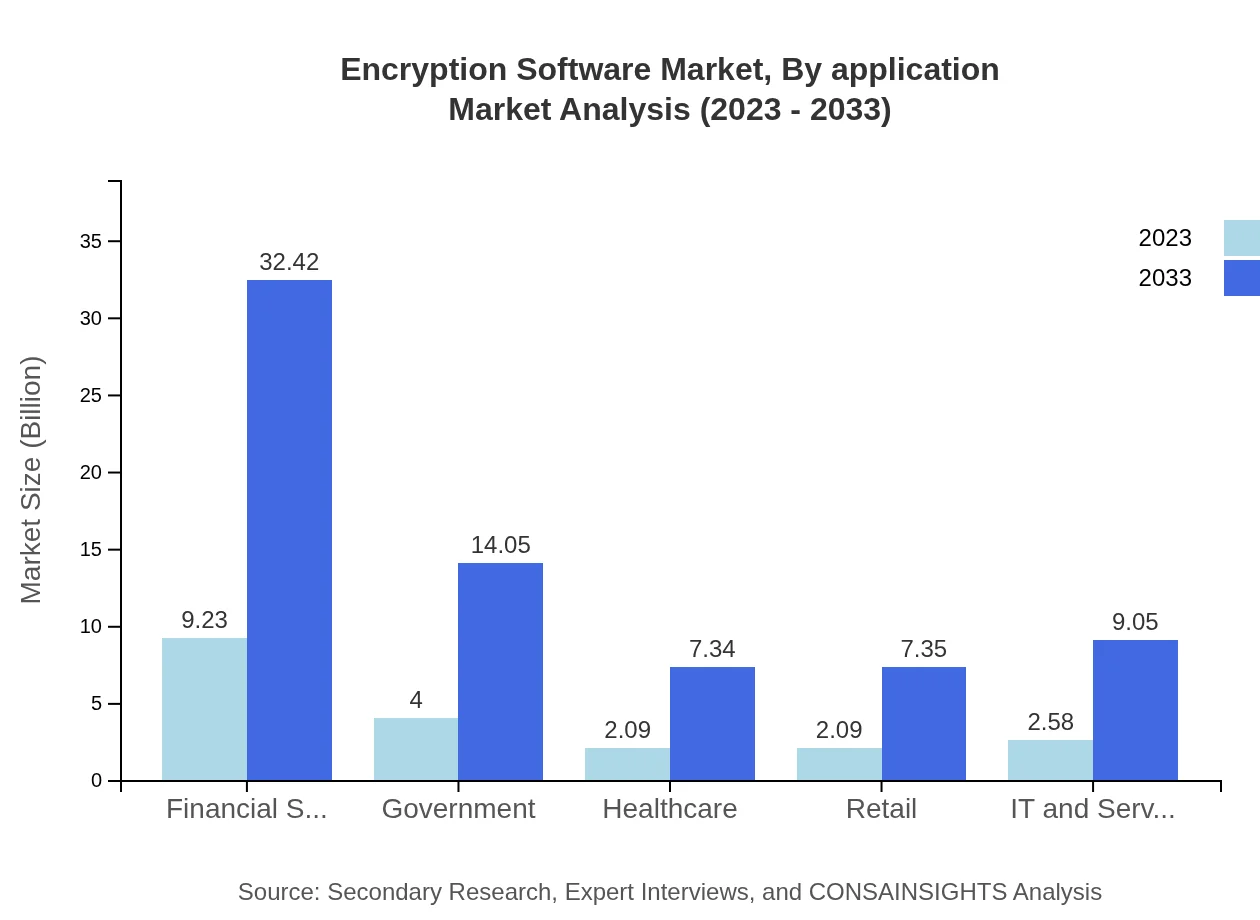
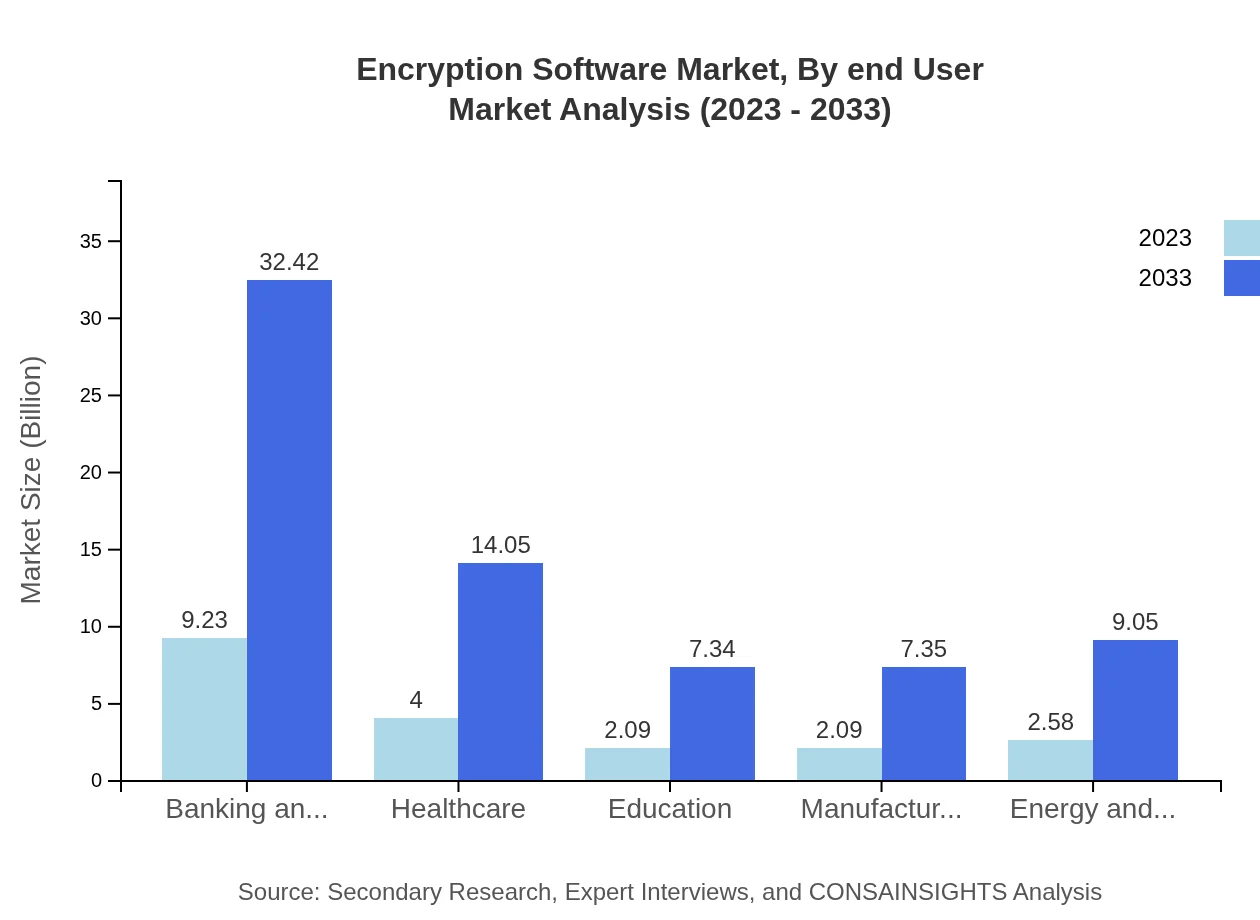
The major applications of Encryption Software include Banking and Financial Services, Healthcare, Education, Manufacturing, and Government sectors. The Banking sector leads with a market size of $9.23 billion in 2023, expected to grow to $32.42 billion by 2033. The Healthcare segment follows, with a size of $4.00 billion and projected to reach $14.05 billion. Educational institutions are also increasing encryption investments to protect sensitive student and staff data, starting at $2.09 billion and expected to rise to $7.34 billion. Manufacturing and Government sectors also reflect strong growth trajectories.
Encryption Software Market Analysis By Deployment Model
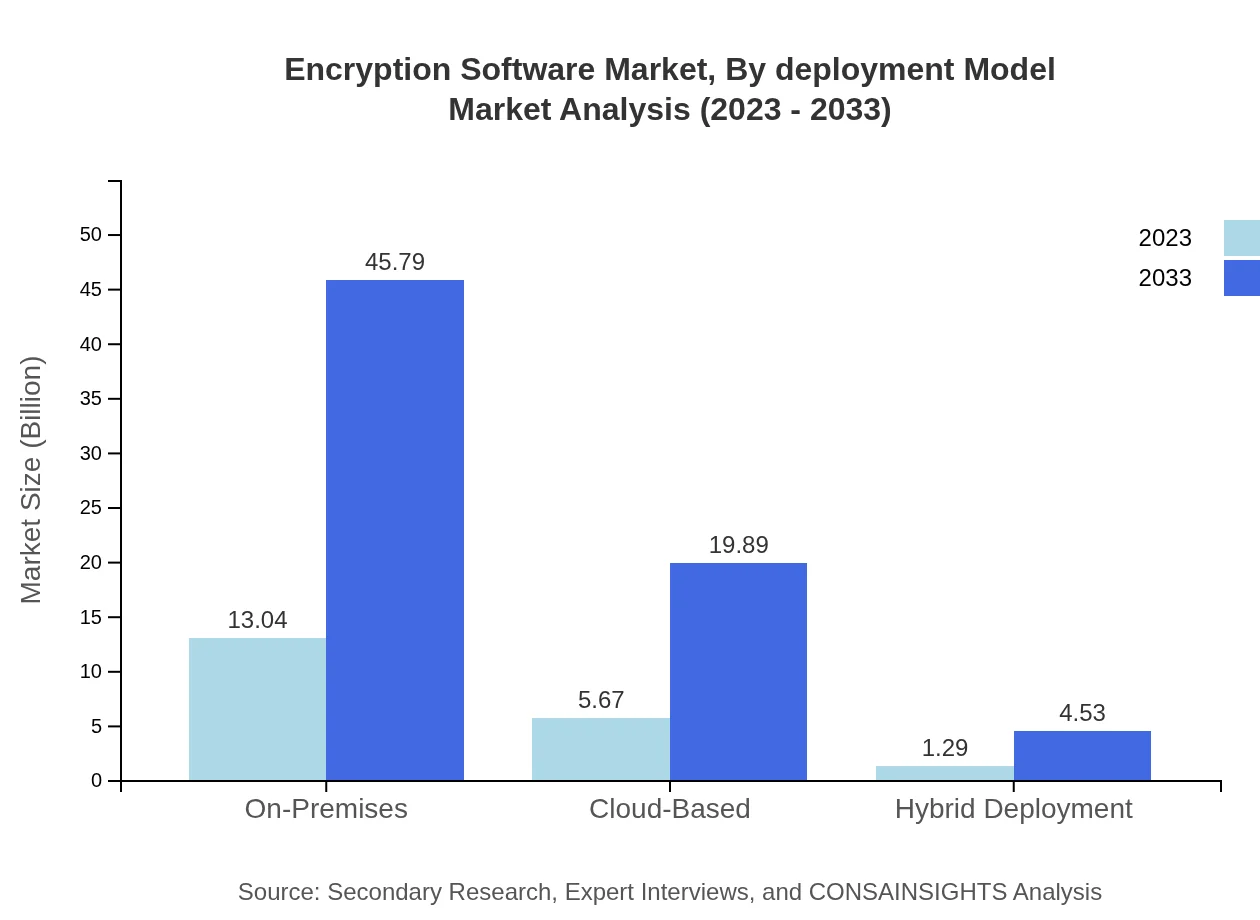
The market is segmented by deployment models into On-Premises, Cloud-Based, and Hybrid Deployment. The On-Premises deployment remains the largest, starting at $13.04 billion and expected to grow to $45.79 billion by 2033. Cloud-Based solutions are gaining traction, moving from $5.67 billion to $19.89 billion, driven by the acceleration toward digital transformation. Hybrid Deployment, currently valued at $1.29 billion, is anticipated to grow to $4.53 billion, appealing to organizations looking for flexible security options.
Encryption Software Market Analysis By End User
The key end-user industries for Encryption Software include Banking and Financial Services, Healthcare, Education, IT & Services, and Government. Banking and Financial Services comprise 46.17% of the market share, with significant growth expected in coming years. The Healthcare industry is also expanding due to rising regulations for patient data protection. IT & Services along with Government sectors are emphasizing encryption to safeguard confidential information, contributing to a diverse end-user landscape that enhances market resilience.
Encryption Software Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Encryption Software Industry
Symantec Corporation:
A leading provider of cybersecurity solutions, known for their comprehensive encryption software that secures data across various platforms.McAfee LLC:
McAfee provides a wide range of cybersecurity solutions, including encryption tools that help organizations protect sensitive data from breaches.IBM Corporation:
IBM offers advanced encryption solutions as part of its broader cybersecurity portfolio, helping businesses ensure data protection.Microsoft Corporation:
Microsoft provides encryption features integrated into its cloud services, enhancing data security for users across various industries.Thales Group:
Thales specializes in data protection and encryption, offering services that meet regulatory requirements while enhancing overall data security.We're grateful to work with incredible clients.









FAQs
What is the market size of encryption Software?
The encryption software market is projected to reach approximately $20 billion by 2033, with a compound annual growth rate (CAGR) of 12.8% from 2023. This growth reflects an increasing demand for data protection across industries.
What are the key market players or companies in the encryption Software industry?
Key players in the encryption software industry include companies like Symantec, McAfee, IBM, Microsoft, and Thales. These firms provide comprehensive solutions that cater to a diverse range of security needs.
What are the primary factors driving the growth in the encryption Software industry?
Factors driving growth in the encryption software industry include rising concerns over data breaches, stringent compliance regulations, and the increasing adoption of IoT and cloud technologies, which heighten the need for robust data protection.
Which region is the fastest Growing in the encryption Software?
The North American region is currently the fastest-growing market for encryption software, projected to increase from $7.56 billion in 2023 to around $26.54 billion by 2033, reflecting a strong focus on data security.
Does ConsaInsights provide customized market report data for the encryption Software industry?
Yes, ConsaInsights offers customized market report data tailored to specific needs in the encryption software industry, allowing clients to gain insights that are relevant to their unique business and market conditions.
What deliverables can I expect from this encryption Software market research project?
Deliverables typically include detailed market analysis reports, regional insights, competitive landscape assessments, growth forecasts, and strategic recommendations to inform decision-making in the encryption software sector.
What are the market trends of encryption Software?
Current trends in the encryption software market include increased investment in cloud-based solutions, a shift towards hybrid deployment models, and a growing emphasis on AI-enhanced security features as organizations prioritize data confidentiality.