Endpoint Security Market Report
Published Date: 31 January 2026 | Report Code: endpoint-security
Endpoint Security Market Size, Share, Industry Trends and Forecast to 2033
This report provides a comprehensive analysis of the Endpoint Security market, including key insights, current trends, and growth forecasts from 2023 to 2033. It covers market size, segmentation, regional insights, industry challenges, and future opportunities.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
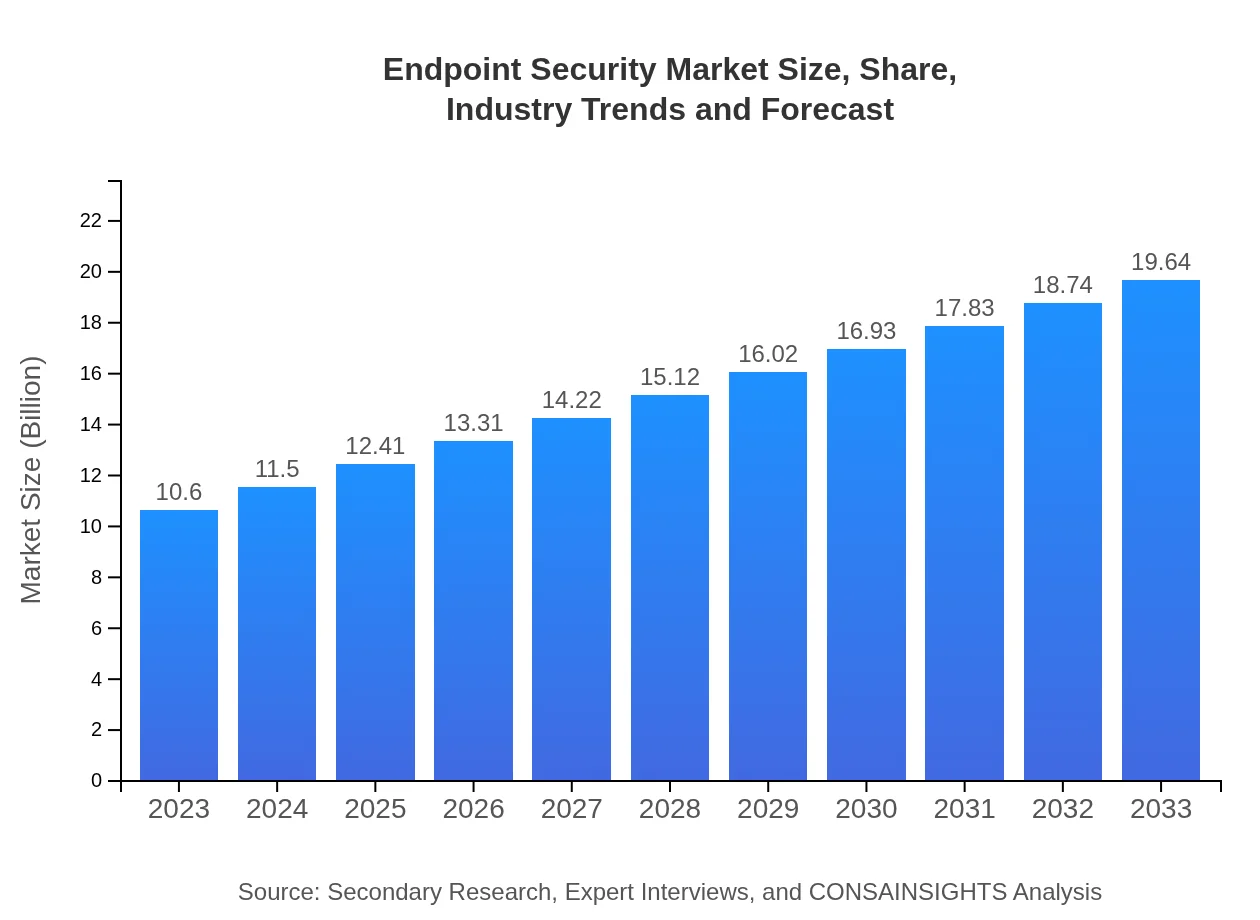
| 2023 Market Size | $10.60 Billion |
| CAGR (2023-2033) | 6.2% |
| 2033 Market Size | $19.64 Billion |
| Top Companies | Symantec Corporation, McAfee, LLC, CrowdStrike, Inc., Trend Micro Incorporated, Sophos Ltd. |
| Last Modified Date | 31 January 2026 |
Endpoint Security Market Overview
Customize Endpoint Security Market Report market research report
- ✔ Get in-depth analysis of Endpoint Security market size, growth, and forecasts.
- ✔ Understand Endpoint Security's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Endpoint Security
What is the Market Size & CAGR of Endpoint Security market in 2023?
Endpoint Security Industry Analysis
Endpoint Security Market Segmentation and Scope
Tell us your focus area and get a customized research report.
Endpoint Security Market Analysis Report by Region
Europe Endpoint Security Market Report:
Europe's Endpoint Security market is estimated at $2.98 billion in 2023, with expectations of growth to approximately $5.53 billion by 2033. Factors such as stringent regulations regarding data protection and a high focus on cybersecurity due to increasing cyber risks are fueling this growth.Asia Pacific Endpoint Security Market Report:
In the Asia Pacific region, the Endpoint Security market is poised for significant growth. With a market size of approximately $2.15 billion in 2023, it is projected to reach $3.99 billion by 2033. The increasing number of cybersecurity incidents, coupled with the rising adoption of digital technologies and remote working trends among organizations, is driving the demand for advanced endpoint protection solutions.North America Endpoint Security Market Report:
North America leads the Endpoint Security market, with a market size of around $3.70 billion in 2023, projected to reach $6.86 billion by 2033. The region's market dominance is supported by the presence of major cybersecurity players and the increasing adoption of advanced security technologies to combat sophisticated cyber threats.South America Endpoint Security Market Report:
The Endpoint Security market in South America is expected to grow from $0.79 billion in 2023 to approximately $1.47 billion by 2033. The market growth is attributed to the increasing need for cybersecurity solutions across various sectors, driven by digital transformation initiatives and the rise in cyberattacks targeting businesses.Middle East & Africa Endpoint Security Market Report:
The Middle East and Africa region is forecasted to see growth from a market size of $0.97 billion in 2023 to about $1.79 billion by 2033. The increasing investment in IT infrastructure and rising awareness around cybersecurity need are key drivers in this region's Endpoint Security market growth.Tell us your focus area and get a customized research report.
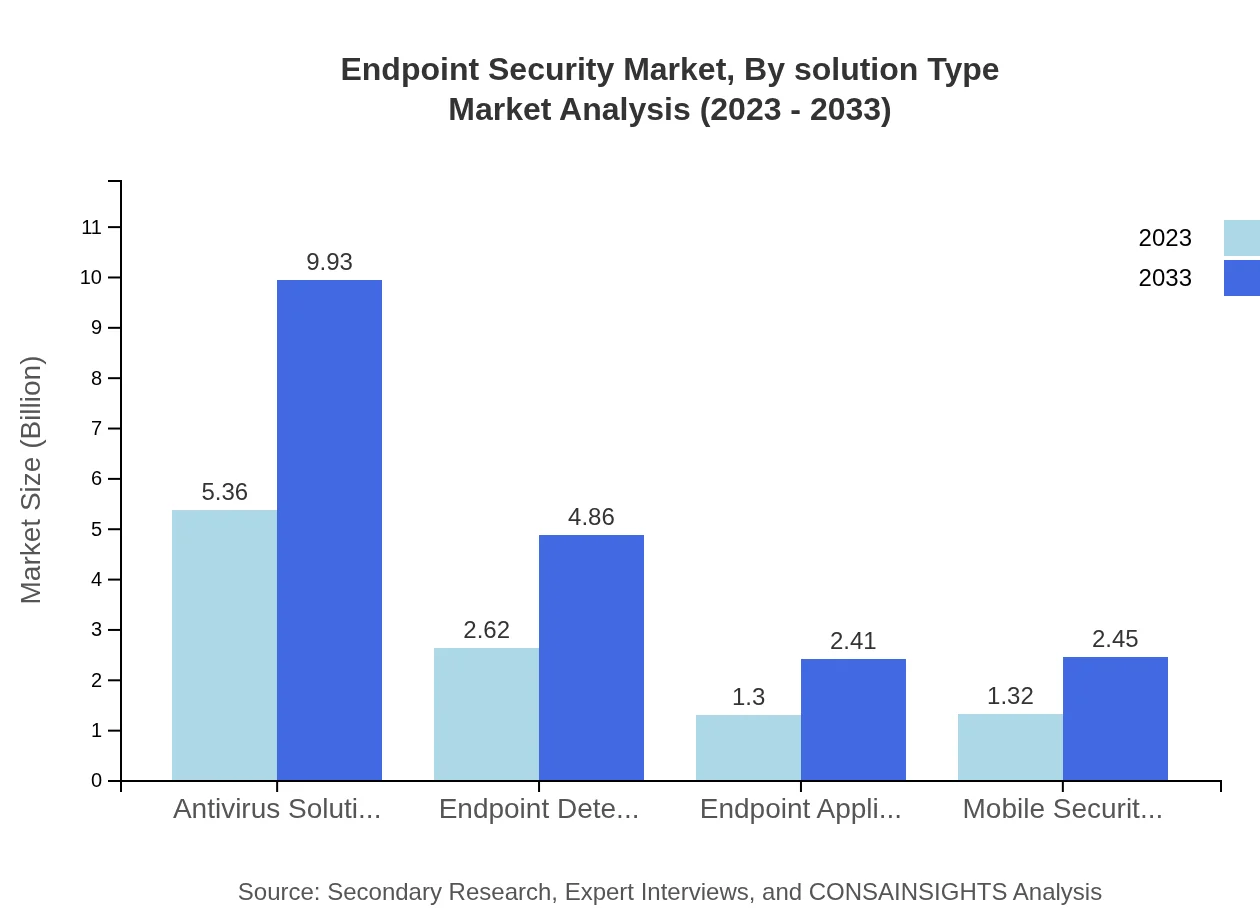
Endpoint Security Market Analysis By Solution Type
By solution type, the Endpoint Security market includes various segments such as Antivirus Solutions, Endpoint Detection and Response (EDR), and Cloud-Based Solutions. In 2023, Antivirus Solutions dominate the market with a size of $5.36 billion, accounting for approximately 50.54% market share. Following this, EDR holds a significant share of 24.73% with a market size of $2.62 billion. Cloud-Based Solutions show robust growth potential, expected to rise from $6.58 billion in 2023 to $12.20 billion by 2033, capturing a 62.1% share.
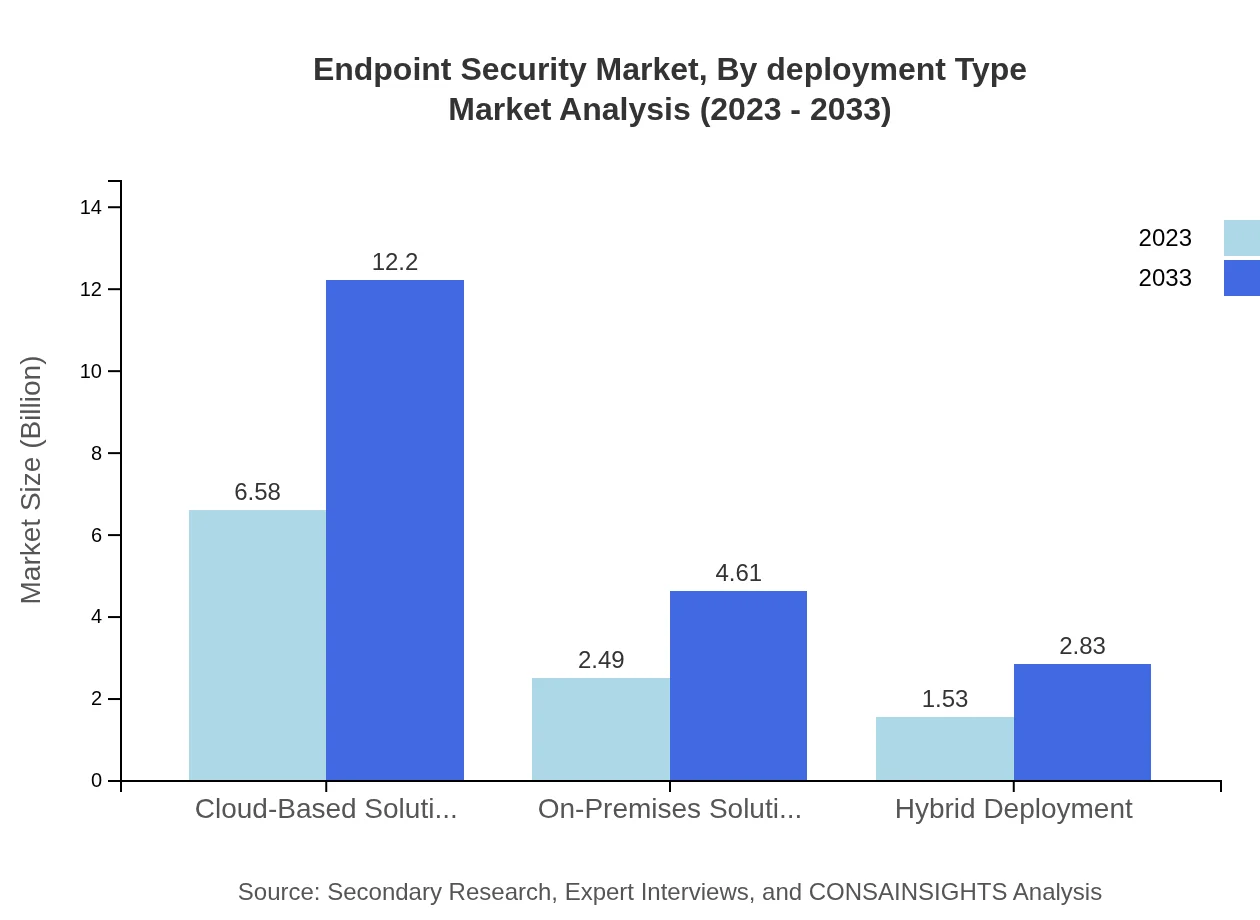
Endpoint Security Market Analysis By Deployment Type
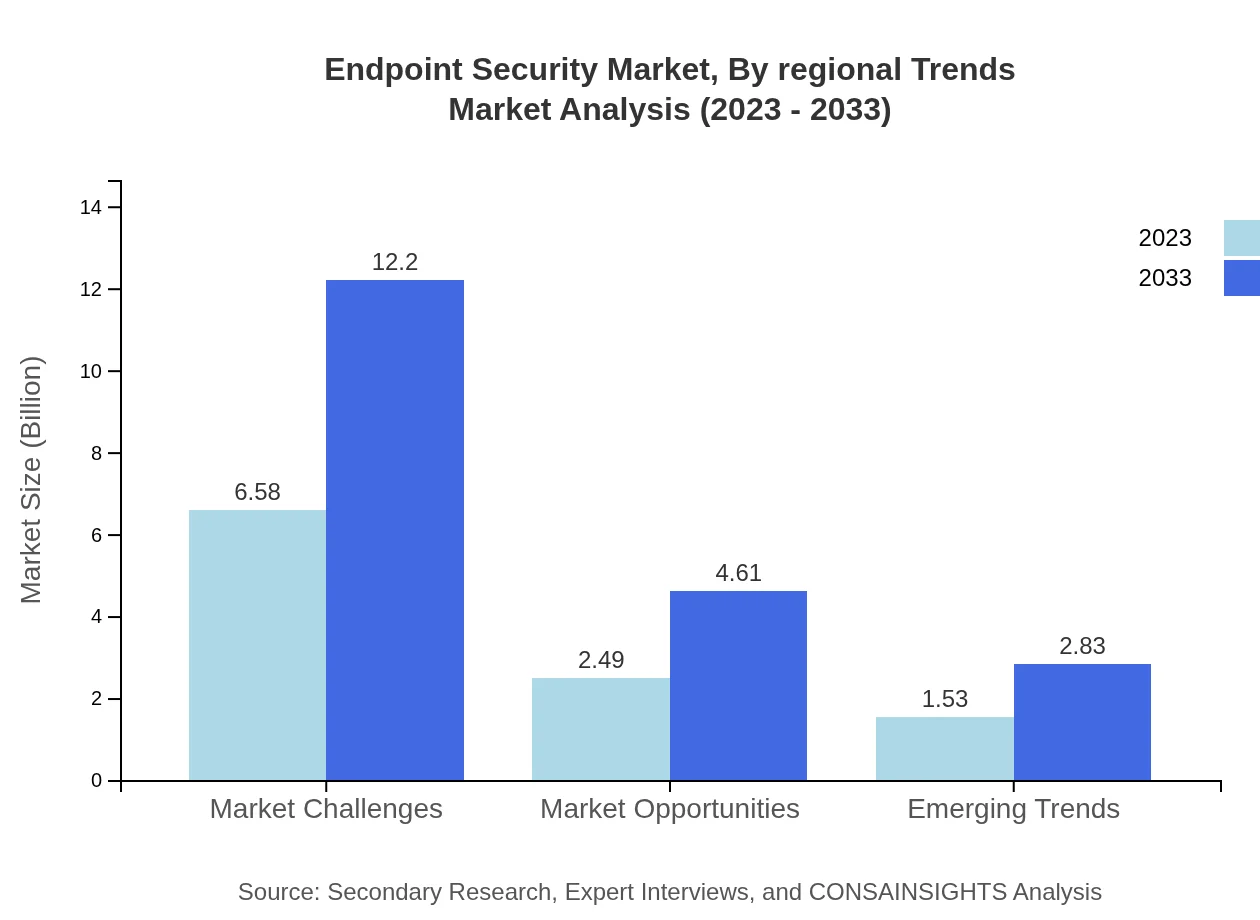
The market is segmented by deployment type into cloud-based, on-premises, and hybrid deployment. Cloud-based solutions lead with a market size of $6.58 billion in 2023, expected to grow to $12.20 billion by 2033. On-premises solutions hold a significant 23.48% share, valued at $2.49 billion in 2023, growing to $4.61 billion by 2033. Hybrid deployment is also gaining traction, projected to increase from $1.53 billion to $2.83 billion over the same timeframe.
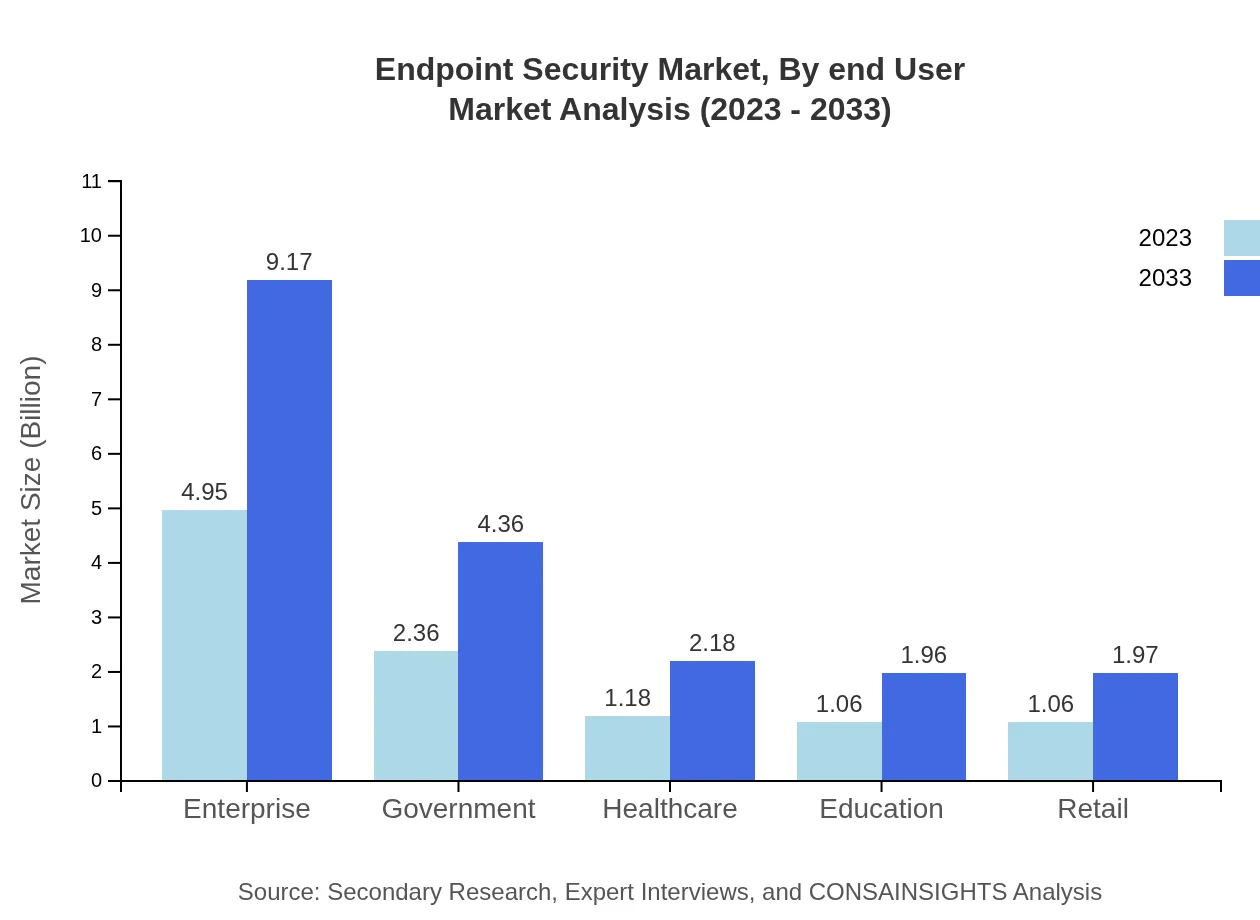
Endpoint Security Market Analysis By End User
Endpoint Security in the enterprise sector leads with a market size of $4.95 billion in 2023 (46.67% share) and is expected to rise to $9.17 billion by 2033. Government and healthcare sectors also represent significant portions of the market, with sizes of $2.36 billion and $1.18 billion, respectively, in 2023. The education and retail sectors lead to approximately $1.06 billion each in the same year, underlining the diverse applicability of endpoint security solutions across multiple sectors.
Endpoint Security Market Analysis By Regional Trends
The Endpoint Security market is influenced by trends such as a heightened emphasis on real-time threat analysis, AI and machine learning integration into security solutions, and an increasing focus on regulatory compliance across industries. The rise in remote working arrangements is also contributing to increased investment in advanced endpoint protection solutions. Organizations are increasingly adopting a proactive approach to cybersecurity, shifting from reactive measures to preventative solutions to safeguard their networks and data.
Endpoint Security Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Endpoint Security Industry
Symantec Corporation:
Symantec is a world leader in cybersecurity solutions, offering a robust suite of endpoint protection services. Their offerings include advanced threat detection and response, which leverage machine learning technology.McAfee, LLC:
McAfee provides comprehensive endpoint security solutions geared towards businesses of all sizes. Their solutions encompass antivirus, EDR, and cloud-based security products which protect against a wide range of cyber threats.CrowdStrike, Inc.:
CrowdStrike is known for its innovative approach to cybersecurity, particularly in the EDR space. Their cloud-native platform comprises advanced threat intelligence capabilities and proactive defense mechanisms.Trend Micro Incorporated:
Trend Micro specializes in endpoint security, offering integrated solutions that include antivirus, file integrity monitoring, and vulnerability assessment tailored for enterprise-level customers.Sophos Ltd.:
Sophos provides next-gen cybersecurity solutions, focusing on simplifying endpoint security management with their automated systems that protect against advanced malware and ransomware attacks.We're grateful to work with incredible clients.









FAQs
What is the market size of endpoint Security?
The global endpoint security market is valued at approximately $10.6 billion in 2023, with a projected CAGR of 6.2%. Expected to reach significant milestones by 2033, this market reflects the growing concerns over cybersecurity.
What are the key market players or companies in this endpoint Security industry?
Key players in the endpoint security industry include established tech giants specializing in cybersecurity solutions. Their innovative offerings drive competition, ensuring robust security features and continual enhancements to address emerging threats.
What are the primary factors driving the growth in the endpoint security industry?
Several factors contribute to the endpoint security market's growth, including increasing cyber threats, the rise of remote work, and advancements in security technologies, which cumulatively spur demand for more sophisticated protection solutions.
Which region is the fastest Growing in the endpoint security?
The North American region is witnessing the fastest growth in endpoint security, projected to expand from $3.70 billion in 2023 to $6.86 billion by 2033, driven by significant investments in cybersecurity infrastructure.
Does ConsaInsights provide customized market report data for the endpoint Security industry?
Yes, ConsaInsights offers customized market reports that cater to specific needs and requirements within the endpoint security industry, ensuring tailored insights for businesses seeking targeted market data.
What deliverables can I expect from this endpoint Security market research project?
Deliverables from the endpoint security market research project typically include comprehensive analytical reports, market forecasts, segment analysis, competitive landscape profiles, and insights into emerging trends to inform strategic decision-making.
What are the market trends of endpoint security?
Current trends in the endpoint security market include a shift towards cloud-based solutions, increased adoption of Artificial Intelligence for threat detection, and a heightened focus on mobile security, reflecting evolving consumer needs.