Enterprise Key Management Market Report
Published Date: 31 January 2026 | Report Code: enterprise-key-management
Enterprise Key Management Market Size, Share, Industry Trends and Forecast to 2033
This report provides an in-depth analysis of the Enterprise Key Management (EKM) market from 2023 to 2033, focusing on market size, growth projections, trends, segmentation, and key players. It integrates data-driven insights to forecast future developments in the industry.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
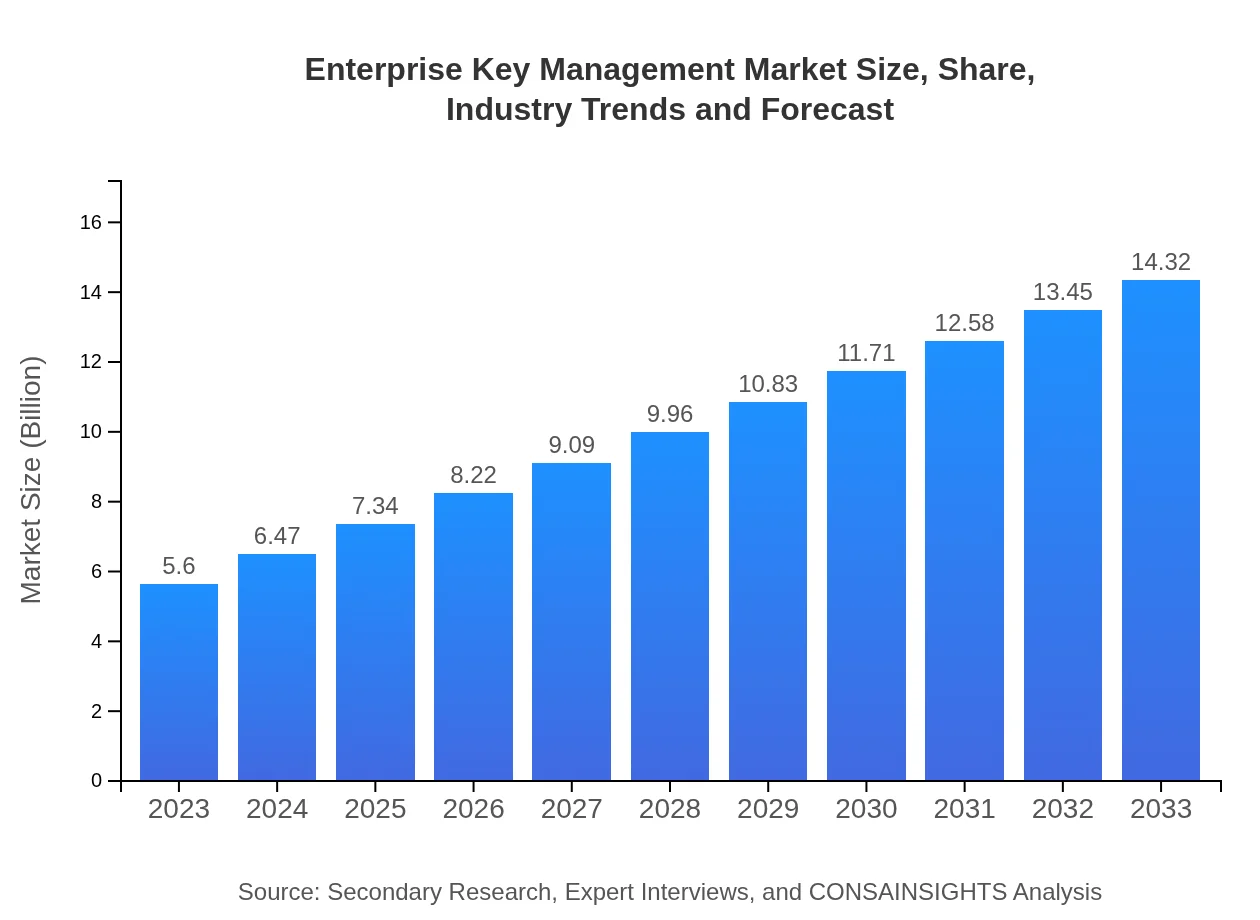
| 2023 Market Size | $5.60 Billion |
| CAGR (2023-2033) | 9.5% |
| 2033 Market Size | $14.32 Billion |
| Top Companies | Thales Group, IBM, Microsoft, Gemalto, Amazon Web Services (AWS) |
| Last Modified Date | 31 January 2026 |
Enterprise Key Management Market Overview
Customize Enterprise Key Management Market Report market research report
- ✔ Get in-depth analysis of Enterprise Key Management market size, growth, and forecasts.
- ✔ Understand Enterprise Key Management's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Enterprise Key Management
What is the Market Size & CAGR of the Enterprise Key Management market in 2033?
Enterprise Key Management Industry Analysis
Enterprise Key Management Market Segmentation and Scope
Tell us your focus area and get a customized research report.
Enterprise Key Management Market Analysis Report by Region
Europe Enterprise Key Management Market Report:
Europe's Enterprise Key Management market is expected to rise sharply from $1.76 billion in 2023 to $4.51 billion by 2033. The enhancement of data privacy laws, such as GDPR, has prompted organizations to adopt more comprehensive key management solutions.Asia Pacific Enterprise Key Management Market Report:
In the Asia Pacific region, the Enterprise Key Management market is anticipated to grow from $1.03 billion in 2023 to $2.63 billion by 2033. This growth is driven by the rapid expansion of cloud services and the adoption of digital security frameworks among businesses.North America Enterprise Key Management Market Report:
North America leads the EKM market with an estimation of $2.10 billion in 2023, expected to rise to $5.36 billion by 2033. The region's strong regulatory environment and high investment in cybersecurity infrastructure are significant growth factors.South America Enterprise Key Management Market Report:
The South American market is experiencing slow growth, projected to decline from a value of $0.01 billion in 2023 to -$0.02 billion in 2033. This trend indicates challenges in the market, possibly due to economic instability and lower investment in cybersecurity technologies.Middle East & Africa Enterprise Key Management Market Report:
The Middle East and Africa are projected to witness growth from $0.72 billion in 2023 to $1.84 billion by 2033. The increasing necessity for compliance with international data protection regulations and growing digital transformation initiatives are contributing to this growth.Tell us your focus area and get a customized research report.
Enterprise Key Management Market Analysis By Product
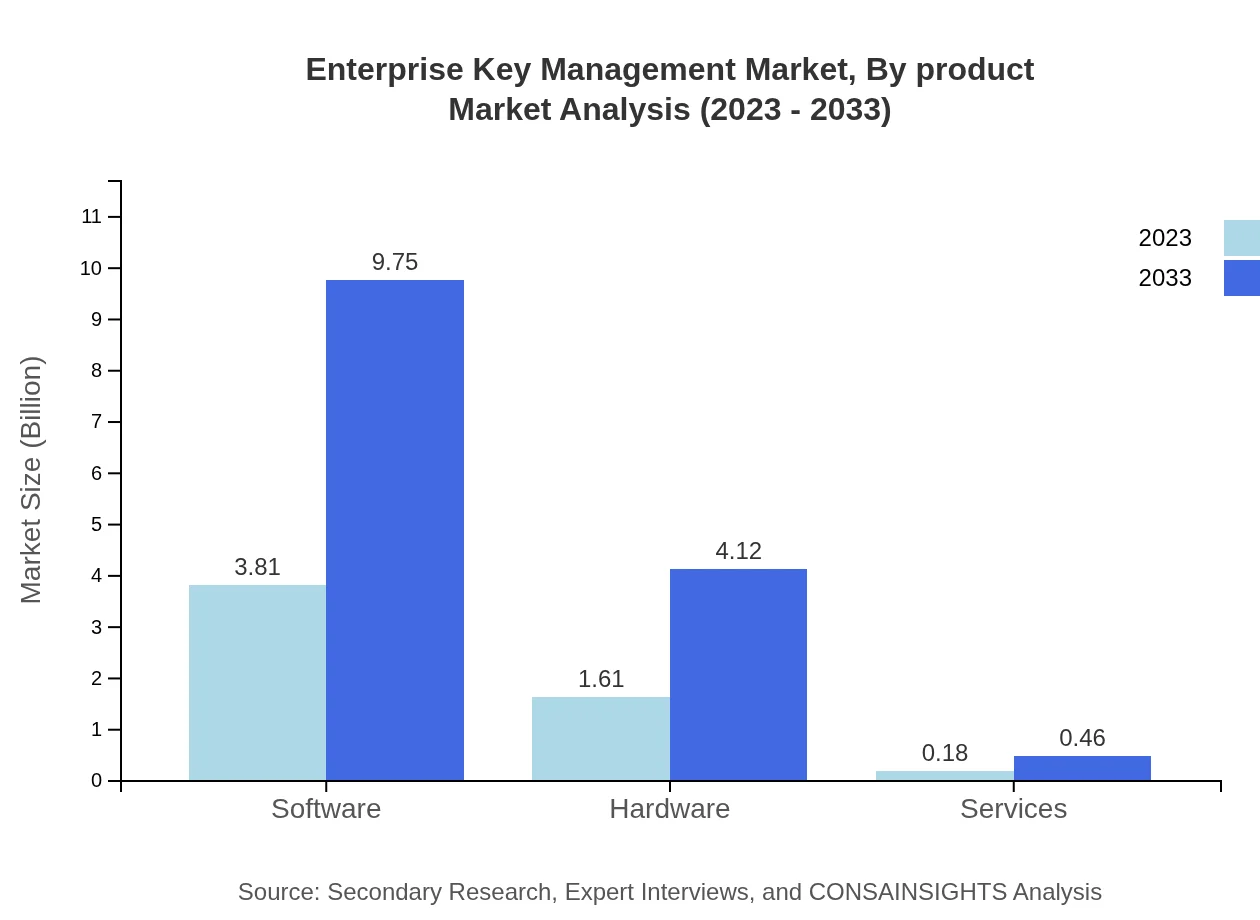
The product segment of the Enterprise Key Management market is subdivided into software, hardware, and services. Software solutions, leading the market with a share of 68.05% in 2023, are projected to grow at a rapid pace, moving from $3.81 billion in 2023 to $9.75 billion by 2033. Hardware components follow with a market size of $1.61 billion in 2023, expected to reach $4.12 billion in 2033, while services, while smaller, will grow from $0.18 billion to $0.46 billion during the same period.
Enterprise Key Management Market Analysis By Application Area
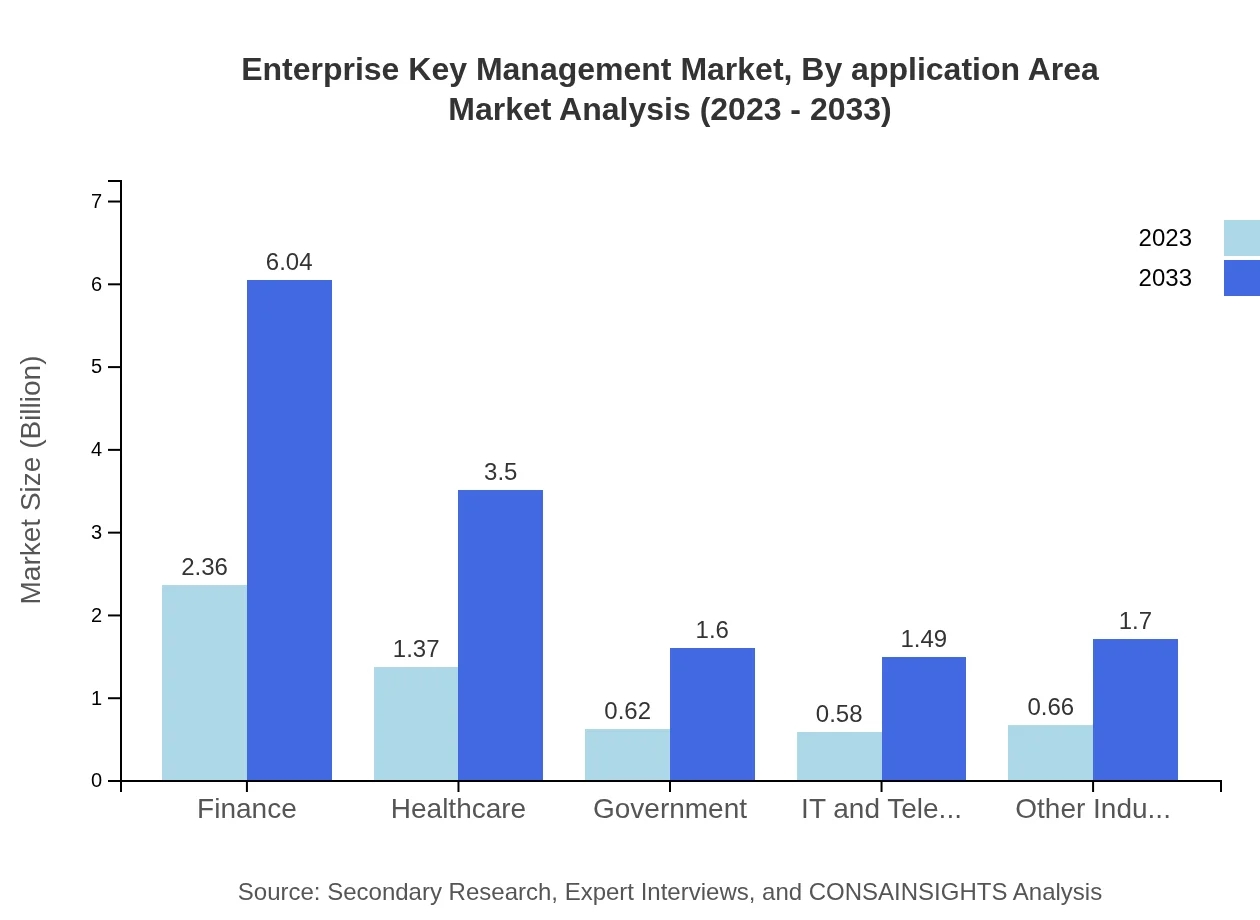
The application area segment highlights finance as the leading sector, slated to grow from $2.36 billion in 2023 to $6.04 billion by 2033, accounting for a substantial market share of 42.19%. Healthcare follows with expected growth from $1.37 billion to $3.50 billion, representing a 24.4% share, while government-related applications will grow from $0.62 billion to $1.60 billion with a consistent share of about 11.14%.
Enterprise Key Management Market Analysis By Deployment Type
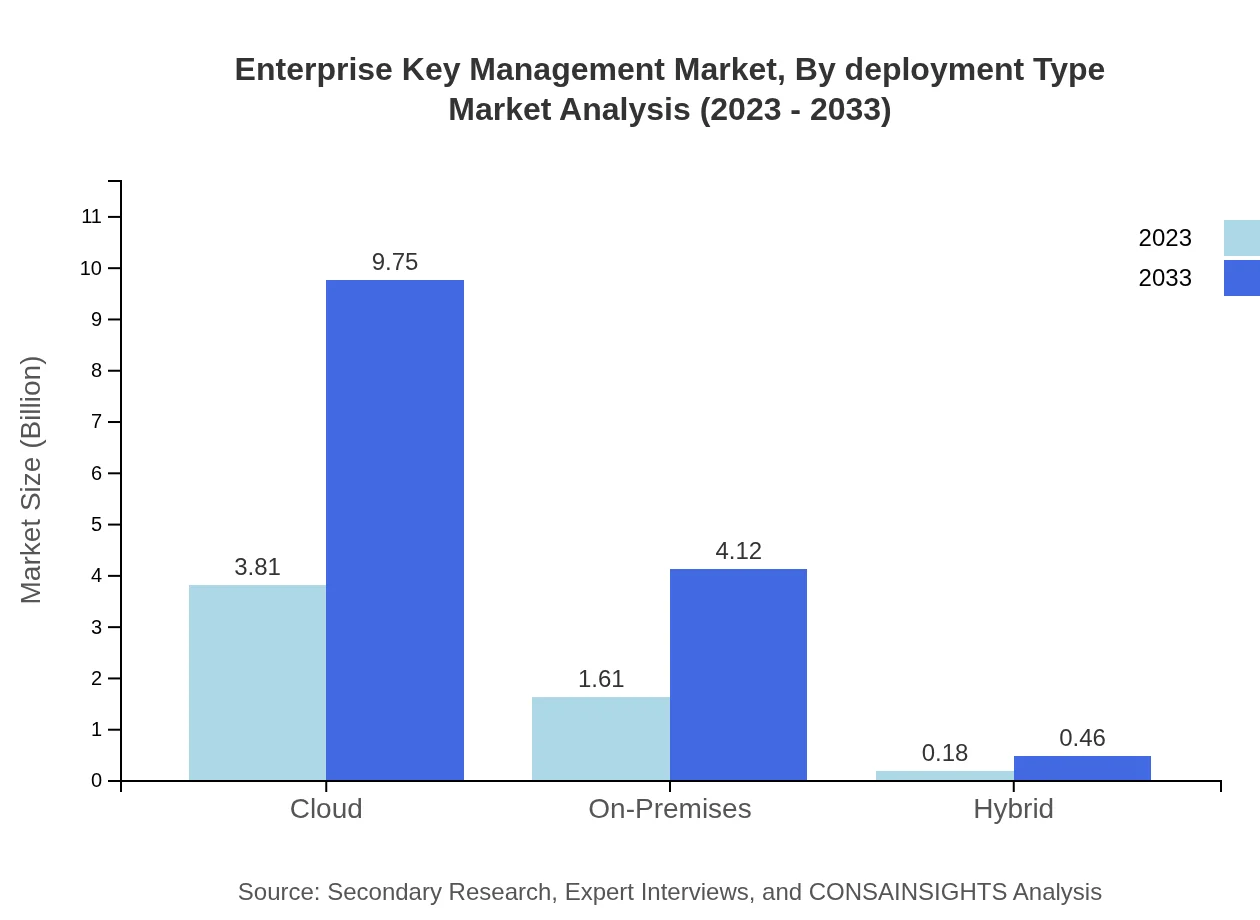
Deployment types in the EKM market include cloud, on-premises, and hybrid solutions. The cloud segment will dominate with a significant share of 68.05%, growing from $3.81 billion in 2023 to $9.75 billion by 2033. On-premises solutions follow with a share of 28.73%, moving from $1.61 billion to $4.12 billion, while hybrid solutions, though smaller, are forecasted to grow steadily from $0.18 billion to $0.46 billion.
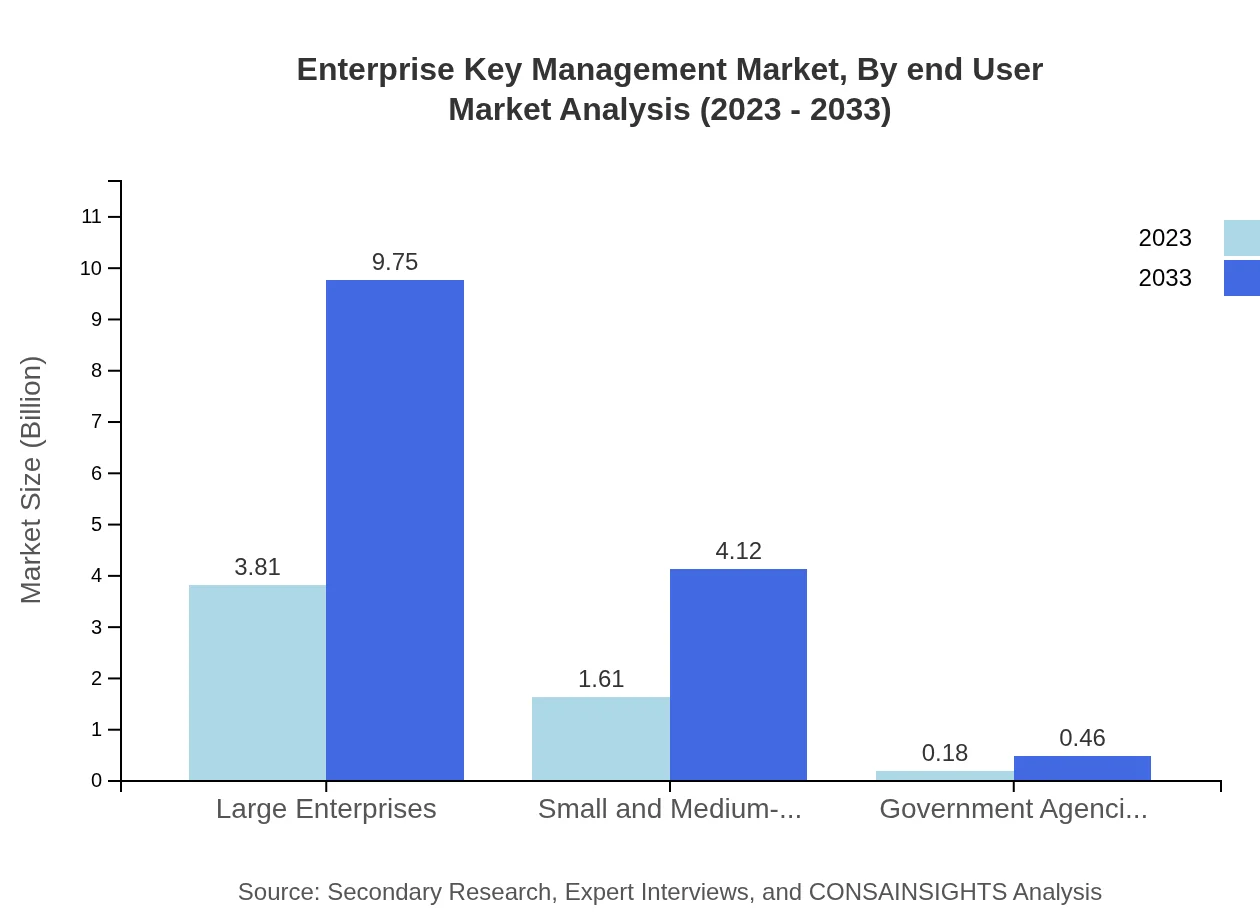
Enterprise Key Management Market Analysis By End User
End-user analysis reveals large organizations as the primary users of EKM solutions, projected to grow from $3.81 billion in 2023 to $9.75 billion by 2033, maintaining a share of 68.05%. Medium-sized organizations will increase from $1.61 billion to $4.12 billion, while small organizations, despite their relatively smaller share, will see consistent growth from $0.18 billion to $0.46 billion.
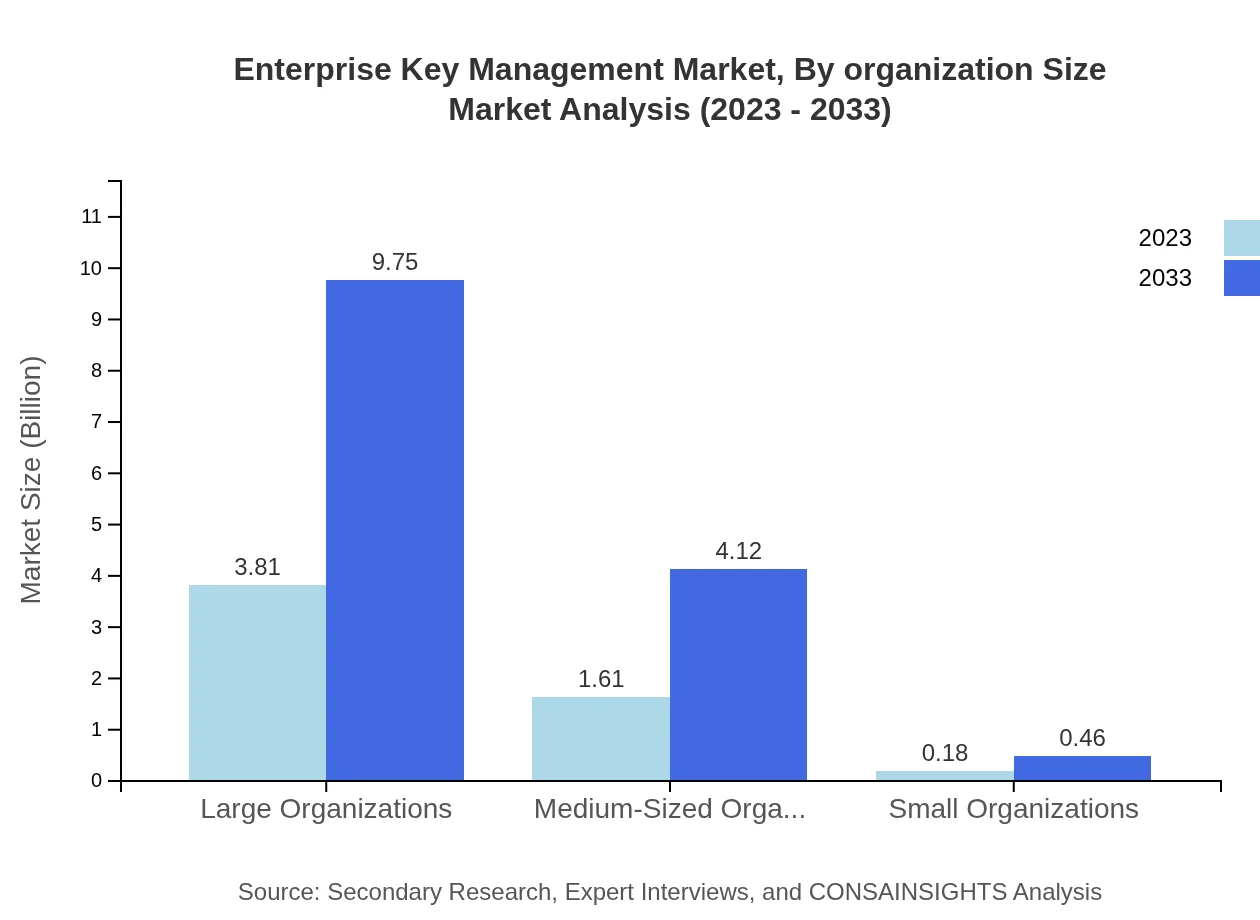
Enterprise Key Management Market Analysis By Organization Size
The organization size segment categorizes the market into large, medium-sized, and small organizations. Large enterprises dominate the landscape with a size of $3.81 billion in 2023, expected to grow to $9.75 billion by 2033. Medium-sized enterprises will increase from $1.61 billion in 2023 to $4.12 billion, while small enterprises will expand marginally from $0.18 billion to $0.46 billion over the forecast period.
Enterprise Key Management Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in the Enterprise Key Management Industry
Thales Group:
Thales Group is a global leader in cybersecurity solutions and provides advanced encryption and key management systems catering to various industries. Their comprehensive solutions are known for reliability and extensive features.IBM:
IBM offers a robust suite of enterprise security solutions, including key management services that assist organizations in managing encryption keys effectively, ensuring compliance, and securing sensitive information.Microsoft:
Microsoft provides a cloud-based key management solution integrated into its Azure platform, allowing organizations to manage their cryptographic keys securely while leveraging the scalability and flexibility of the cloud.Gemalto:
Gemalto, now part of Thales, specializes in digital security and provides key management solutions designed to protect sensitive data across multiple environments, focusing on innovative and adaptive technologies.Amazon Web Services (AWS):
AWS offers key management services embedded within its cloud offerings, enabling customers to easily create and control encryption keys using a highly scalable and secure environment.We're grateful to work with incredible clients.









FAQs
What is the market size of enterprise Key Management?
The Enterprise Key Management market is valued at approximately $5.6 billion in 2023 and is projected to grow at a CAGR of 9.5% through 2033, emphasizing its increasing importance in securing digital assets.
What are the key market players or companies in this enterprise Key Management industry?
Key players in the Enterprise Key Management industry include Thales e-Security, IBM Corporation, Microsoft, and AWS. These companies lead the market due to their innovative solutions and robust infrastructure supporting enterprise-level security.
What are the primary factors driving the growth in the enterprise Key Management industry?
Growth in the Enterprise Key Management sector is driven by increasing cybersecurity threats, regulatory compliance requirements, and the demand for secure cloud services, making key management crucial for safeguarding sensitive information.
Which region is the fastest Growing in the enterprise Key Management?
Asia Pacific is experiencing rapid growth in the Enterprise Key Management sector, projected to increase from $1.03 billion in 2023 to $2.63 billion by 2033, reflecting greater adoption of security solutions in emerging markets.
Does ConsaInsights provide customized market report data for the enterprise Key Management industry?
Yes, ConsaInsights offers customized market report data tailored to specific needs in the Enterprise Key Management industry, helping businesses make informed strategic decisions based on unique market dynamics.
What deliverables can I expect from this enterprise Key Management market research project?
From this Enterprise Key Management market research project, you can expect comprehensive reports detailing market size, growth forecasts, competitive analysis, and strategic recommendations for stakeholders in the key management landscape.
What are the market trends of enterprise Key Management?
Key trends in the Enterprise Key Management market include the shift towards cloud-based solutions, increasing focus on automation and AI for security, and growing compliance regulations that necessitate stronger key management practices.