Enterprise Mobility Security Market Report
Published Date: 31 January 2026 | Report Code: enterprise-mobility-security
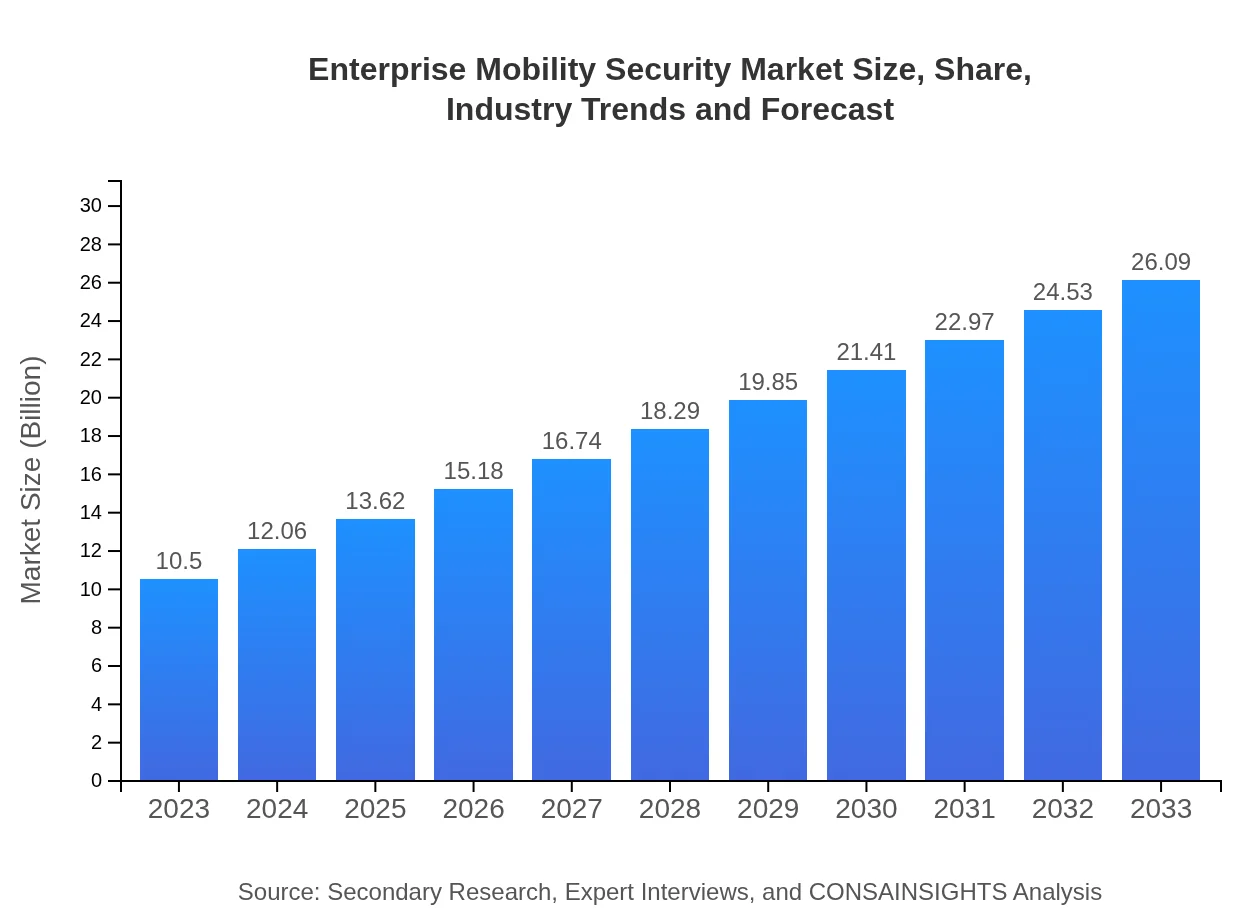
Enterprise Mobility Security Market Size, Share, Industry Trends and Forecast to 2033
This report provides an in-depth analysis of the Enterprise Mobility Security market from 2023 to 2033, covering key insights, market size forecasts, growth trends, and industry dynamics to help stakeholders make informed decisions.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
| 2023 Market Size | $10.50 Billion |
| CAGR (2023-2033) | 9.2% |
| 2033 Market Size | $26.09 Billion |
| Top Companies | IBM, Microsoft, VMware, Cisco, MobileIron |
| Last Modified Date | 31 January 2026 |
Enterprise Mobility Security Market Overview
Customize Enterprise Mobility Security Market Report market research report
- ✔ Get in-depth analysis of Enterprise Mobility Security market size, growth, and forecasts.
- ✔ Understand Enterprise Mobility Security's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Enterprise Mobility Security
What is the Market Size & CAGR of Enterprise Mobility Security market in 2023?
Enterprise Mobility Security Industry Analysis
Enterprise Mobility Security Market Segmentation and Scope
Tell us your focus area and get a customized research report.
Enterprise Mobility Security Market Analysis Report by Region
Europe Enterprise Mobility Security Market Report:
Europe is also on a growth trajectory, with the market expected to rise from $3.12 billion in 2023 to $7.75 billion by 2033. The introduction of GDPR and other data protection regulations compels organizations to enhance their mobile security protocols, contributing to the market's development.Asia Pacific Enterprise Mobility Security Market Report:
The Asia Pacific region is witnessing significant growth in the Enterprise Mobility Security market, expected to grow from $1.96 billion in 2023 to $4.88 billion by 2033. The rising smartphone penetration and a rapid digital transformation across industries are driving demand for comprehensive security solutions. Countries like China and India are at the forefront of this expansion, emphasizing mobile workforce safety and regulatory compliance.North America Enterprise Mobility Security Market Report:
North America holds the largest market share for Enterprise Mobility Security, projected to expand from $4.06 billion in 2023 to $10.08 billion by 2033. The region's advanced cybersecurity infrastructure, coupled with stringent regulatory policies, drives investment. Additionally, increased awareness of cyber threats among enterprises is fostering a proactive approach to mobile security.South America Enterprise Mobility Security Market Report:
The South American market presents unique challenges, with a projected decline from $0.10 billion in 2023 to $0.25 billion by 2033. Economic instability and lower adoption rates of advanced security technologies are hindering market growth. However, sectors such as banking and finance are beginning to prioritize mobile security measures, providing a potential area for revenue generation.Middle East & Africa Enterprise Mobility Security Market Report:
The Middle East and Africa are projected to experience growth from $1.46 billion in 2023 to $3.64 billion by 2033. Industries like oil and gas, as well as telecommunications, are increasingly focusing on safeguarding mobile interactions. Government initiatives to strengthen cybersecurity frameworks further support market growth.Tell us your focus area and get a customized research report.
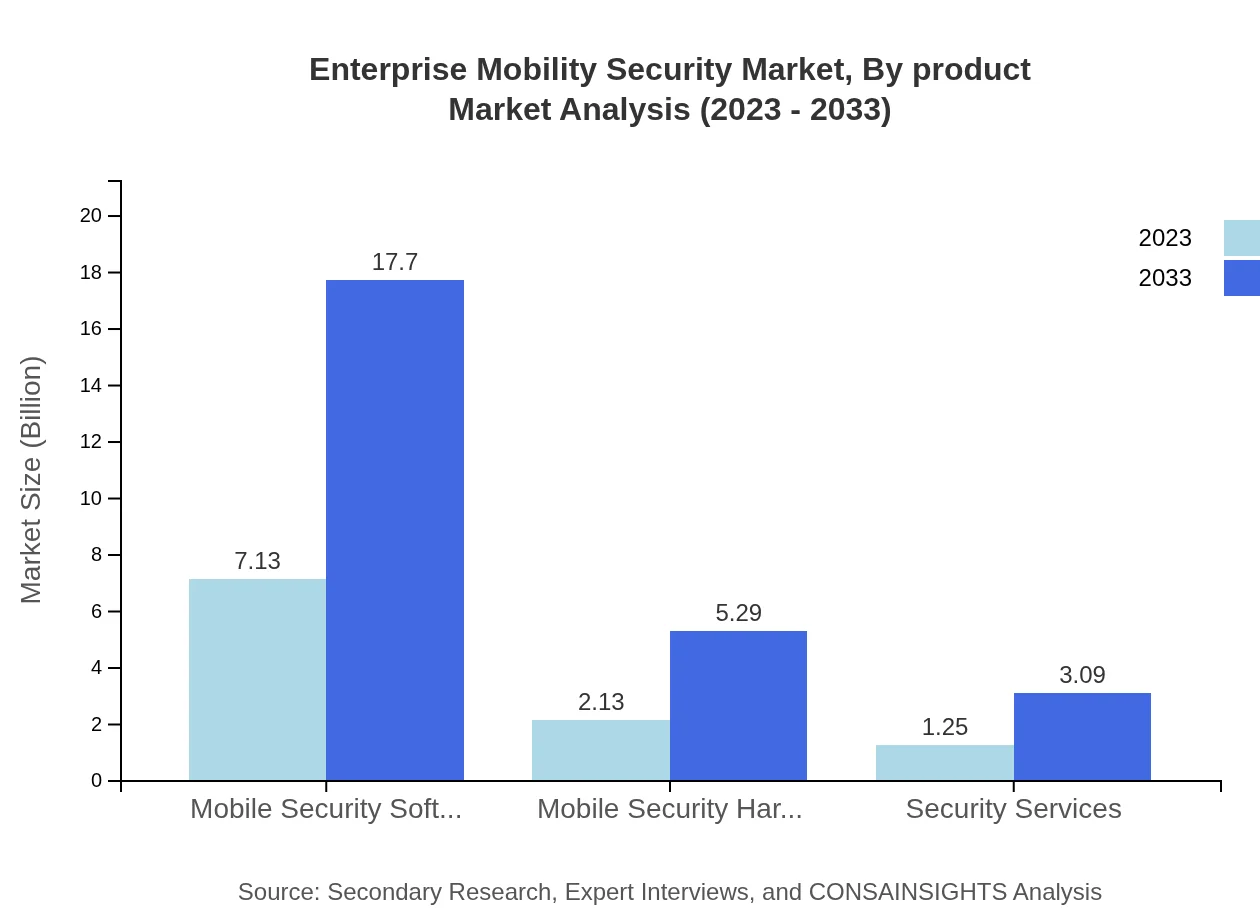
Enterprise Mobility Security Market Analysis By Product
Mobile Security Software remains the dominant segment, expected to grow from $7.13 billion in 2023 to $17.70 billion by 2033, reflecting its critical role in protecting data and ensuring compliant access. Mobile Security Hardware, although smaller in market size, is projected to increase from $2.13 billion to $5.29 billion, enhancing the physical security aspects of mobile devices. Security Services also exhibit growth, from $1.25 billion to $3.09 billion, proving crucial for organizations lacking in-house expertise.
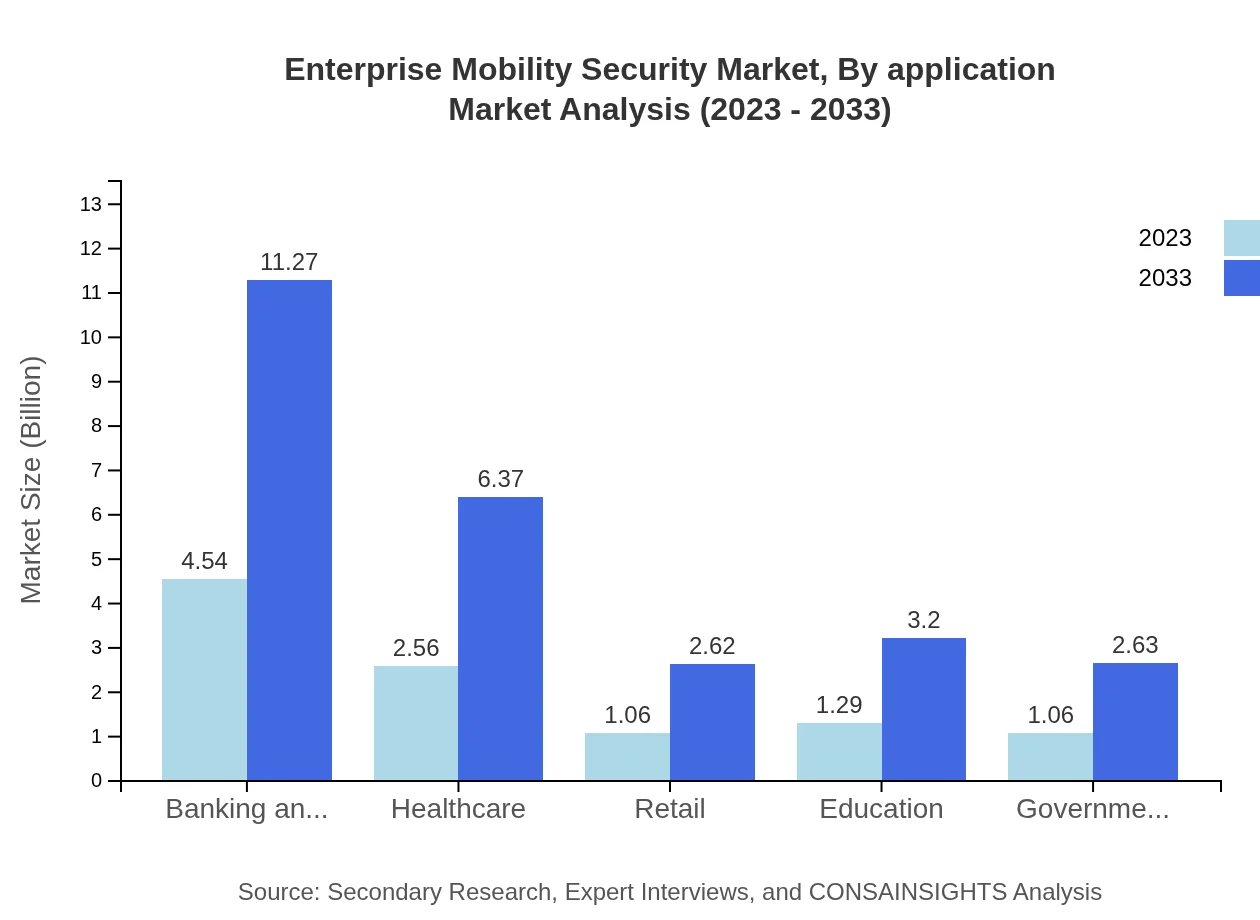
Enterprise Mobility Security Market Analysis By Application
Different sectors show varying needs for mobility security, with Banking and Financial Services expected to lead with size growing from $4.54 billion to $11.27 billion. Healthcare follows closely, with a significant increase from $2.56 billion to $6.37 billion as regulatory compliance necessitates strong security measures. Retail and Education sectors also show promising growth as mobile transactions increase and learning technologies expand.
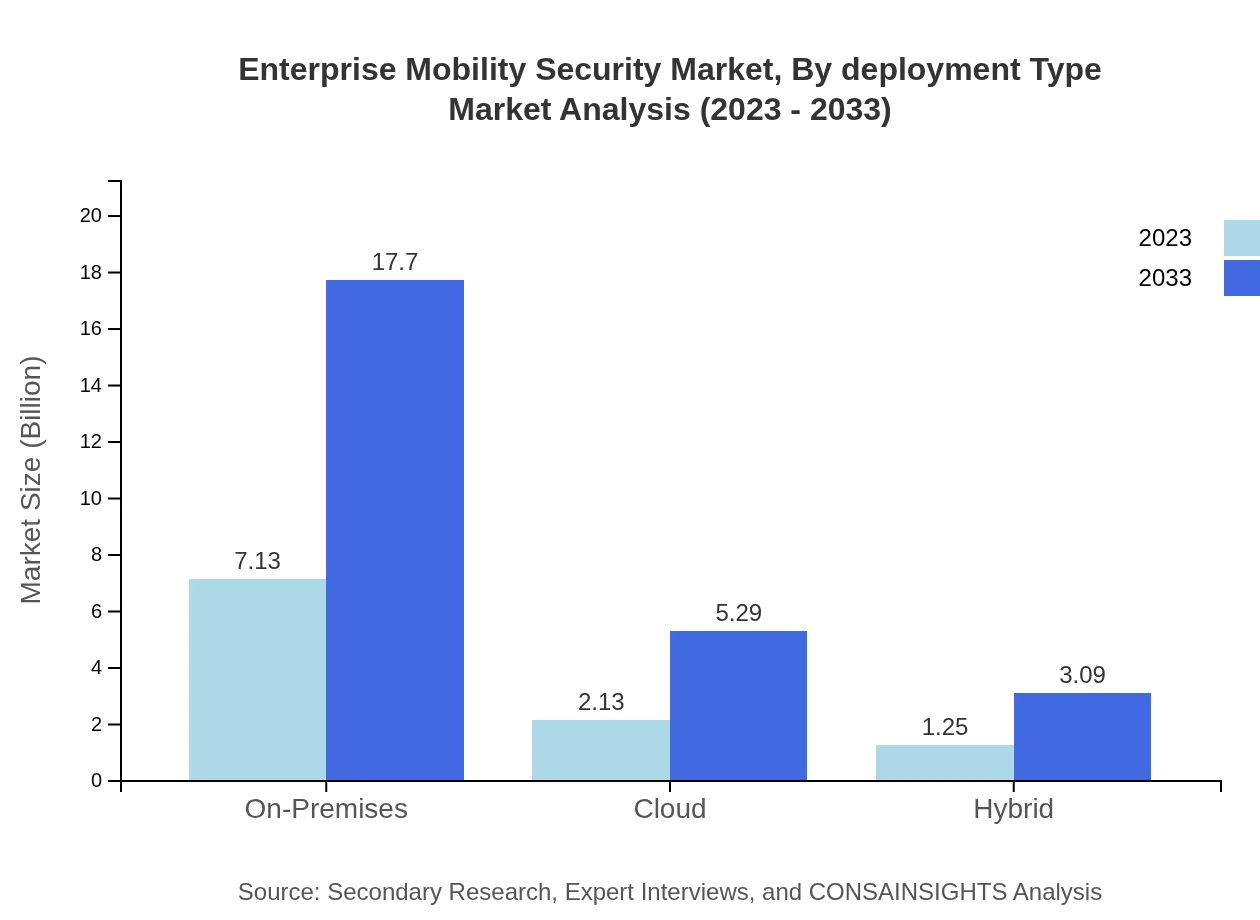
Enterprise Mobility Security Market Analysis By Deployment Type
On-Premises solutions currently dominate the market, projected to maintain a size of $7.13 billion to $17.70 billion due to preferences for control. However, cloud-based solutions are gaining traction, expected to grow from $2.13 billion to $5.29 billion, as organizations seek flexibility. Hybrid solutions will also remain relevant, anticipated to rise from $1.25 billion to $3.09 billion, satisfying varying organizational preferences.
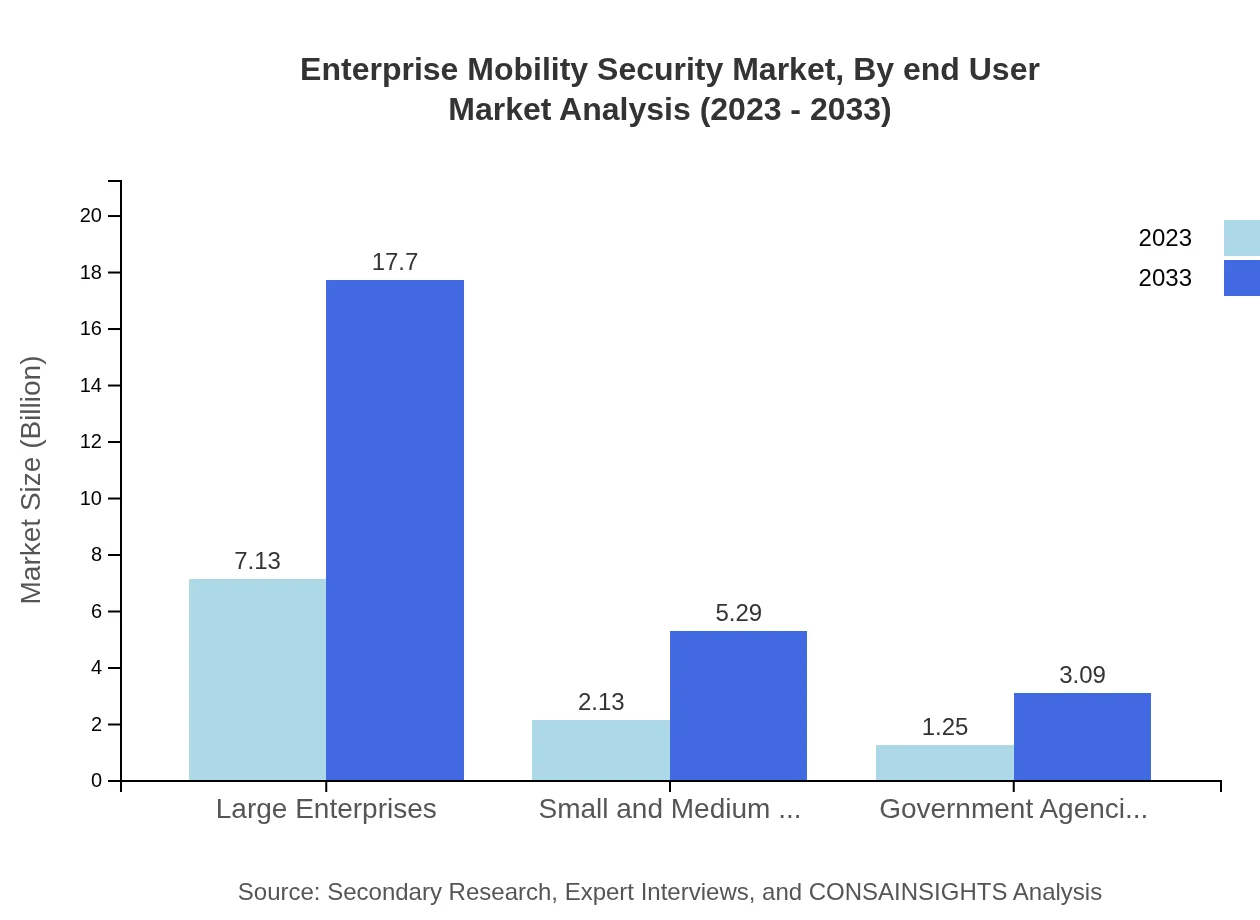
Enterprise Mobility Security Market Analysis By End User
Large Enterprises continue to have significant influence over the market, with growth from $7.13 billion to $17.70 billion strongly driven by their extensive mobile device deployments. On the other hand, Small and Medium Enterprises are emerging, growing from $2.13 billion to $5.29 billion, as more SMEs recognize the necessity of robust mobile security in a digitizing world. Government agencies are also investing in mobile security, projected to grow from $1.25 billion to $3.09 billion.
Enterprise Mobility Security Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Enterprise Mobility Security Industry
IBM:
IBM is a leading player in the Enterprise Mobility Security market, offering a comprehensive range of solutions including mobile device management and advanced threat detection capabilities.Microsoft:
Microsoft provides Enterprise Mobility + Security solutions, integrating identity and access management, device management, and information protection to help organizations secure their mobile operations.VMware:
VMware is known for its innovative approach to mobile security, providing solutions that enable secure application delivery and promote efficient management of mobile environments.Cisco:
Cisco offers a suite of mobile security solutions designed to protect and manage mobile devices, networks, and data traffic for enterprises globally.MobileIron:
MobileIron specializes in mobile security solutions, focusing on device management, secure access, and application security for enterprises.We're grateful to work with incredible clients.









FAQs
What is the market size of enterprise Mobility Security?
The global enterprise mobility security market is valued at $10.5 billion in 2023, with a projected CAGR of 9.2%. This growth reflects increasing investments in security solutions for mobile devices and applications over the next decade.
What are the key market players or companies in the enterprise Mobility Security industry?
Some key players in the enterprise mobility security market include IBM, Microsoft, VMware, Citrix, and MobileIron. These companies provide a range of solutions that effectively address mobile security challenges in organizations across various sectors.
What are the primary factors driving the growth in the enterprise Mobility Security industry?
The growth in the enterprise mobility security industry is driven by the rise in mobile device usage, increasing cyber threats, regulatory compliance necessities, and the need for businesses to protect sensitive data accessed through mobile applications.
Which region is the fastest Growing in the enterprise Mobility Security?
North America is the fastest-growing region in the enterprise mobility security market, with a projected market increase from $4.06 billion in 2023 to $10.08 billion by 2033, driven by high adoption of mobile technologies and cybersecurity initiatives.
Does ConsaInsights provide customized market report data for the enterprise Mobility Security industry?
Yes, ConsaInsights offers customized market report data tailored to the specific needs of clients in the enterprise mobility security sector, enabling them to gain insights that align with their strategic objectives and market interests.
What deliverables can I expect from this enterprise Mobility Security market research project?
Deliverables from the enterprise mobility security market research project typically include comprehensive market analysis reports, trend insights, competitive landscape assessments, segment-specific data, and detailed forecasts for strategic decision-making.
What are the market trends of enterprise Mobility Security?
Current trends in the enterprise mobility security market include a shift toward cloud-based security solutions, increased integration of AI and machine learning in security protocols, and a rise in demand for comprehensive mobile device management solutions.