File Integrity Monitoring Market Report
Published Date: 31 January 2026 | Report Code: file-integrity-monitoring
File Integrity Monitoring Market Size, Share, Industry Trends and Forecast to 2033
This report covers a comprehensive analysis of the File Integrity Monitoring market, including market size, regional insights, trends, and industry forecasts from 2023 to 2033. The insights provided will guide stakeholders in strategic decision-making.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
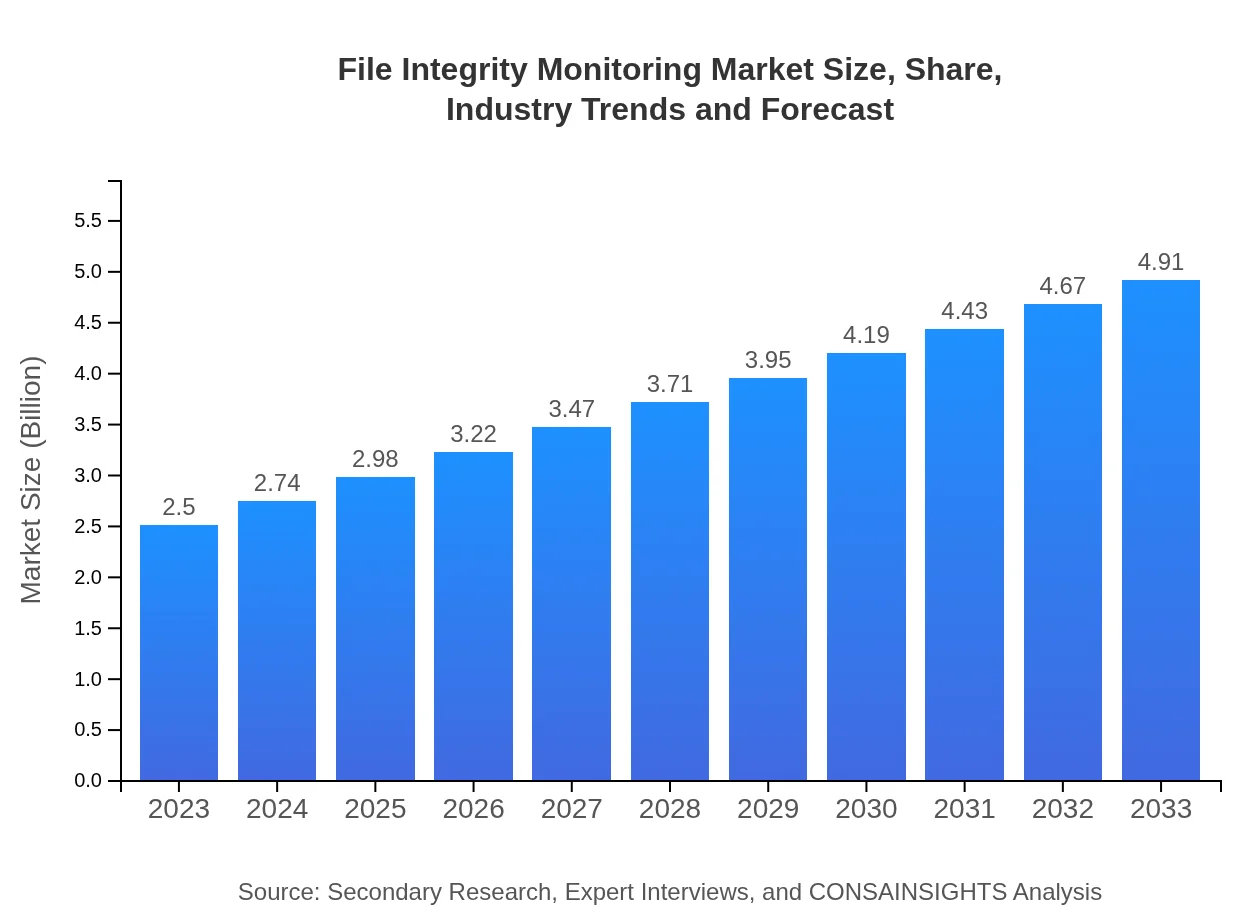
| 2023 Market Size | $2.50 Billion |
| CAGR (2023-2033) | 6.8% |
| 2033 Market Size | $4.91 Billion |
| Top Companies | IBM, McAfee, Splunk, Symantec, Trend Micro |
| Last Modified Date | 31 January 2026 |
File Integrity Monitoring Market Overview
Customize File Integrity Monitoring Market Report market research report
- ✔ Get in-depth analysis of File Integrity Monitoring market size, growth, and forecasts.
- ✔ Understand File Integrity Monitoring's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in File Integrity Monitoring
What is the Market Size & CAGR of File Integrity Monitoring market in 2023?
File Integrity Monitoring Industry Analysis
File Integrity Monitoring Market Segmentation and Scope
Tell us your focus area and get a customized research report.
File Integrity Monitoring Market Analysis Report by Region
Europe File Integrity Monitoring Market Report:
In Europe, the market will expand from USD 0.64 billion in 2023 to USD 1.25 billion in 2033. The General Data Protection Regulation (GDPR) has driven significant investments in compliance-related technologies. Countries like Germany, the UK, and France are spearheading the adoption of advanced FIM solutions as organizations strive to meet stringent data protection laws.Asia Pacific File Integrity Monitoring Market Report:
The Asia Pacific region is witnessing a surge in the File Integrity Monitoring market, driven by rapid digitalization and increasing regulatory pressures. The market size is projected to grow from USD 0.50 billion in 2023 to USD 0.98 billion in 2033. Governments are imposing stricter compliance regulations, prompting organizations to adopt sophisticated FIM tools, particularly in countries like India and China, where cybersecurity is gaining significant attention.North America File Integrity Monitoring Market Report:
The North America region holds the largest share of the File Integrity Monitoring market, projected to grow from USD 0.92 billion in 2023 to USD 1.81 billion by 2033. The United States is the leading market due to the high prevalence of data breaches and stringent regulatory frameworks like HIPAA and PCI DSS, compelling enterprises to invest in robust file monitoring solutions.South America File Integrity Monitoring Market Report:
In South America, the FIM market is gradually growing, with an expected increase from USD 0.13 billion in 2023 to USD 0.26 billion in 2033. Brazil and Argentina are leading the charge, primarily due to rising internet usage and awareness around data protection regulations. However, challenges such as limited budgets and resources affect growth in smaller organizations.Middle East & Africa File Integrity Monitoring Market Report:
The Middle East and Africa region is expected to witness growth from USD 0.31 billion in 2023 to USD 0.61 billion by 2033. Increasing cyber threats and a growing emphasis on compliance are driving demand. Countries in the GCC, such as the UAE and Saudi Arabia, are leading initiatives to enhance their cybersecurity infrastructure, thereby bolstering the FIM market.Tell us your focus area and get a customized research report.
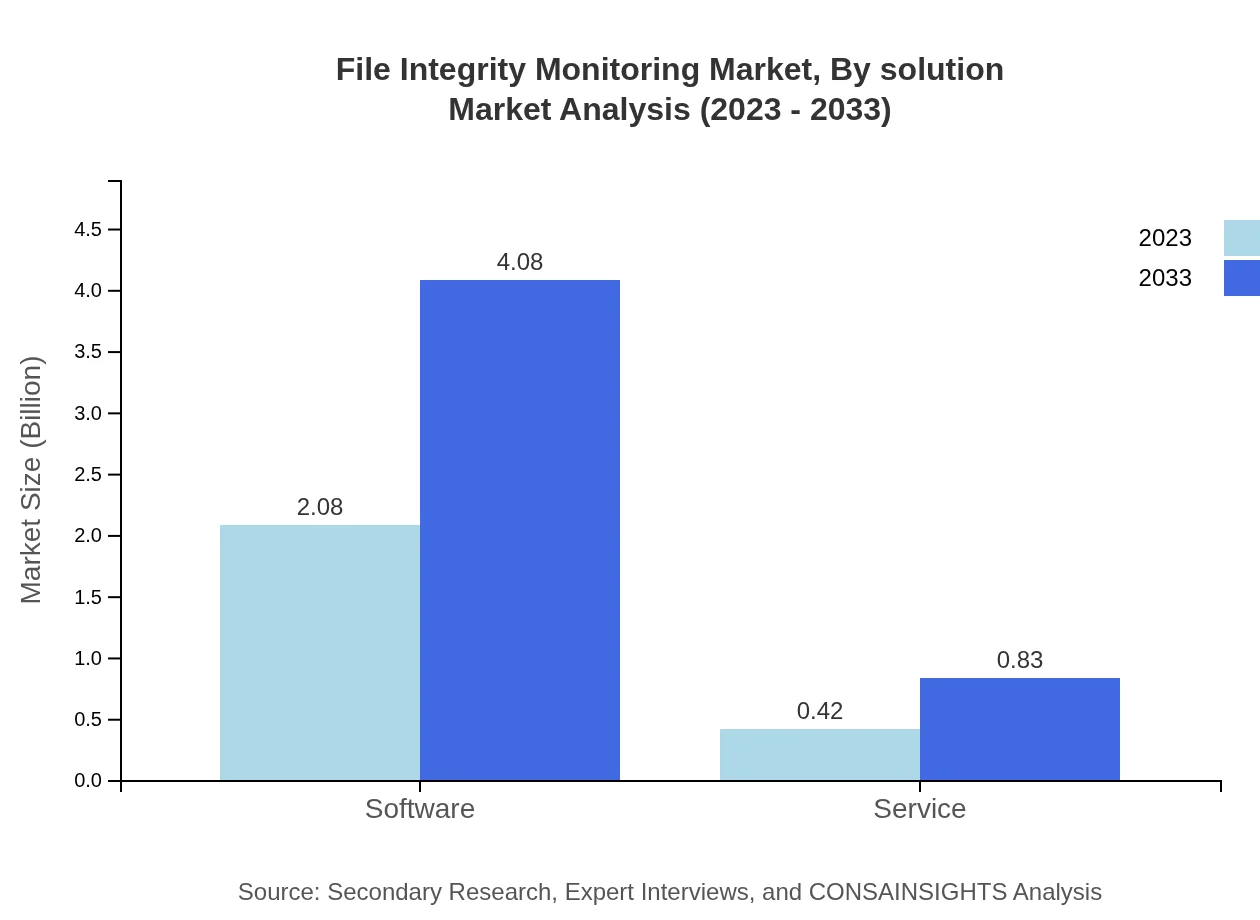
File Integrity Monitoring Market Analysis By Solution
In the FIM market segmentation, Software solutions dominate with a market size of USD 2.08 billion in 2023, expected to rise to USD 4.08 billion by 2033, accounting for 83.06% market share. Service solutions are also significant, expected to grow from USD 0.42 billion to USD 0.83 billion during the forecast period, reflecting the increasing reliance on managed security services.
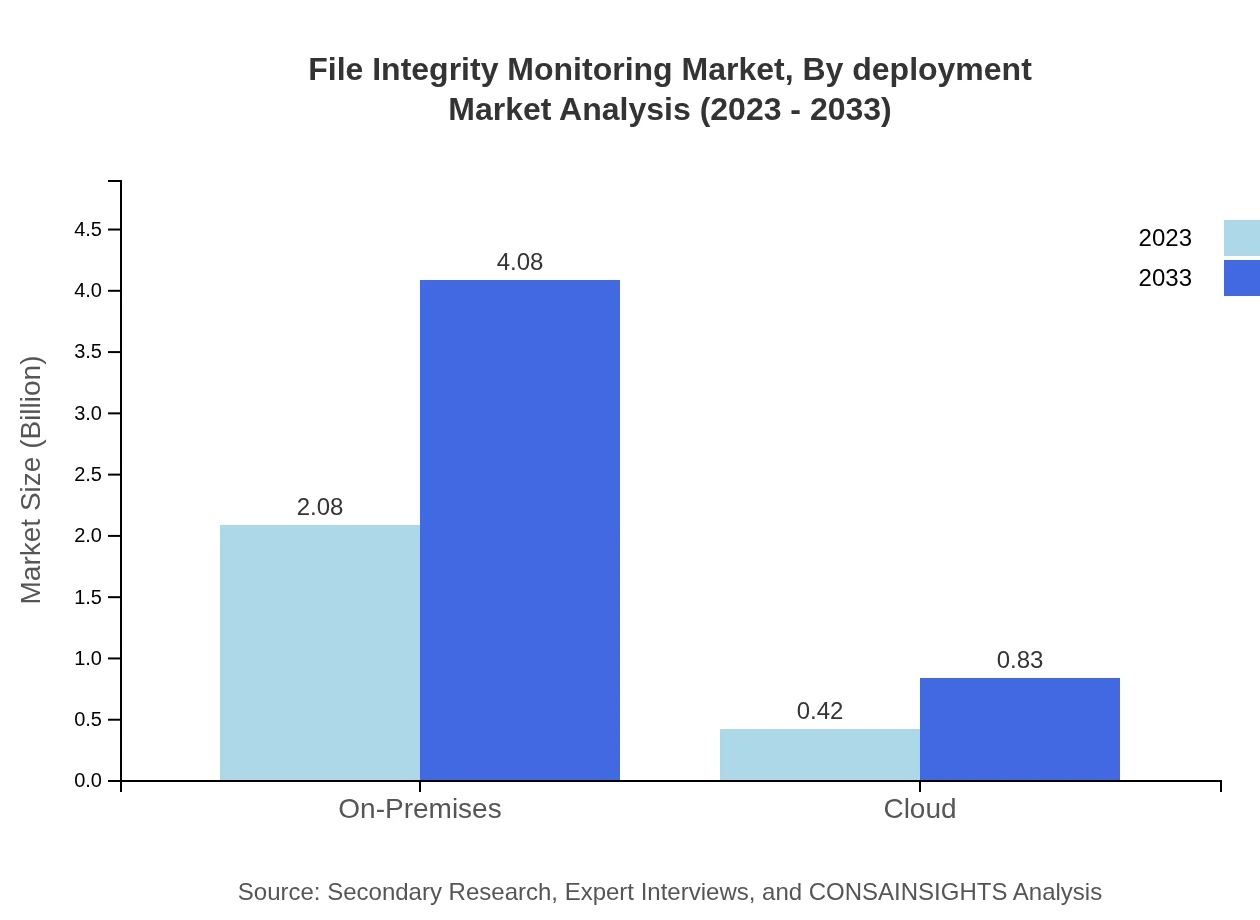
File Integrity Monitoring Market Analysis By Deployment
The deployment analysis reveals that On-Premises solutions are the largest segment, accounting for USD 2.08 billion in 2023 and projected to grow to USD 4.08 billion by 2033 (83.06% share). Cloud-based deployments, while a smaller segment at USD 0.42 billion in 2023, are expected to grow to USD 0.83 billion by 2033 (16.94% share), driven by the flexibility and scalability they offer.
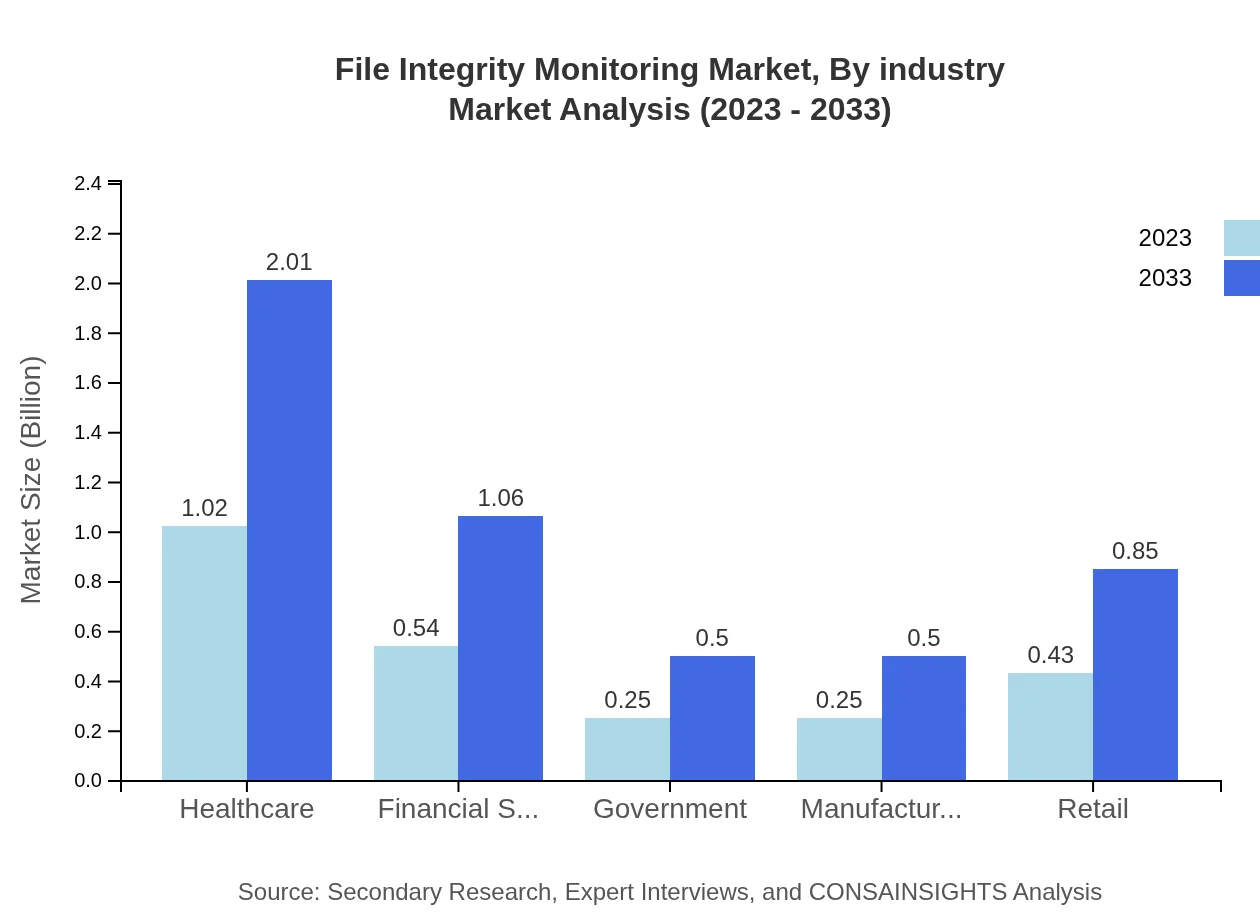
File Integrity Monitoring Market Analysis By Industry
The healthcare sector leads the FIM market with a projected size of USD 1.02 billion in 2023, reaching USD 2.01 billion by 2033 (40.89% share). Financial services follow closely, from USD 0.54 billion to USD 1.06 billion (21.65% share), reflecting the critical need for data security in these industries amid rising regulations and breaches.
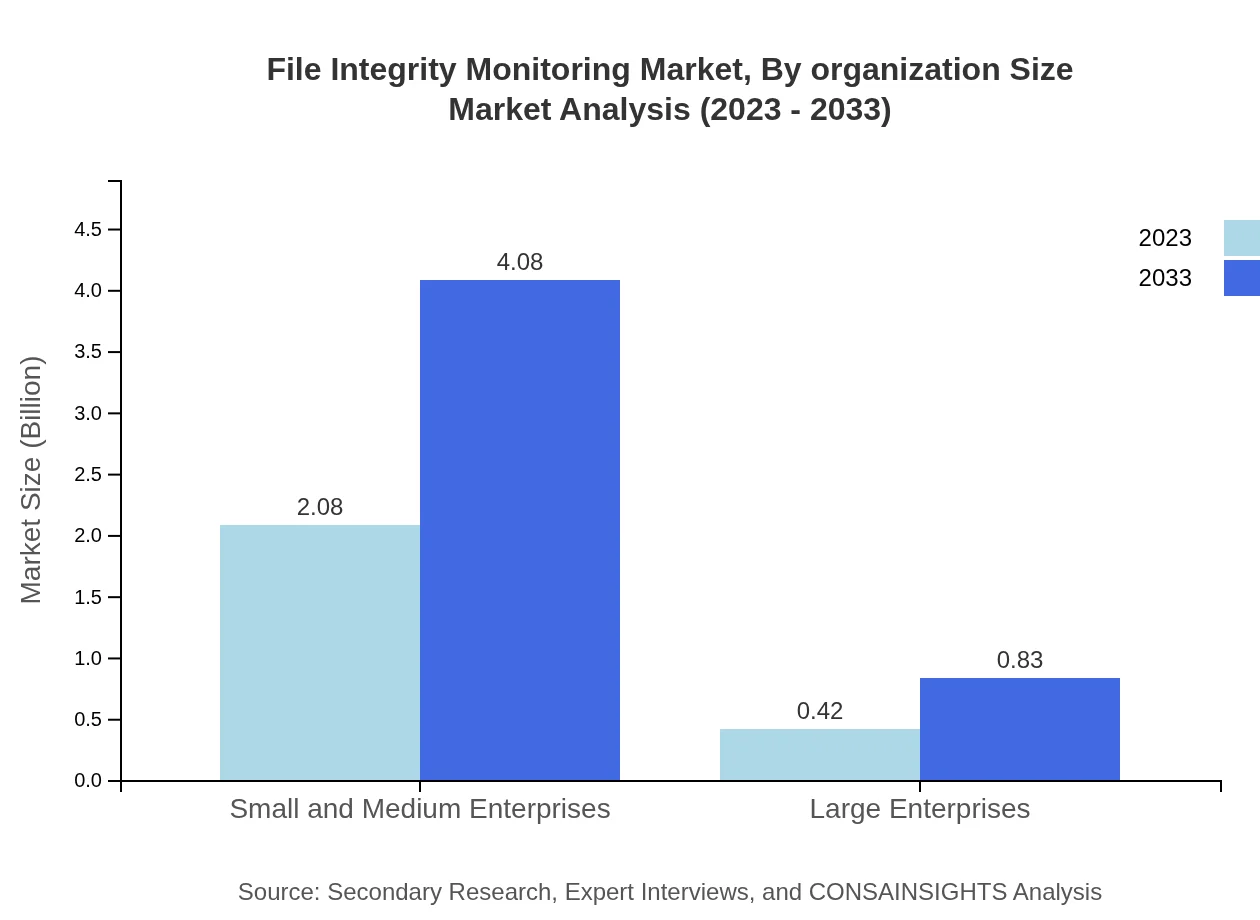
File Integrity Monitoring Market Analysis By Organization Size
For organization sizes, SMEs represent the majority share with a market size of USD 2.08 billion in 2023, growing to USD 4.08 billion by 2033 (83.06% share), driven by the increasing adoption of FIM solutions for compliance and security. Large enterprises, while contributing a smaller share, are expected to grow from USD 0.42 billion to USD 0.83 billion, representing 16.94% of the market.
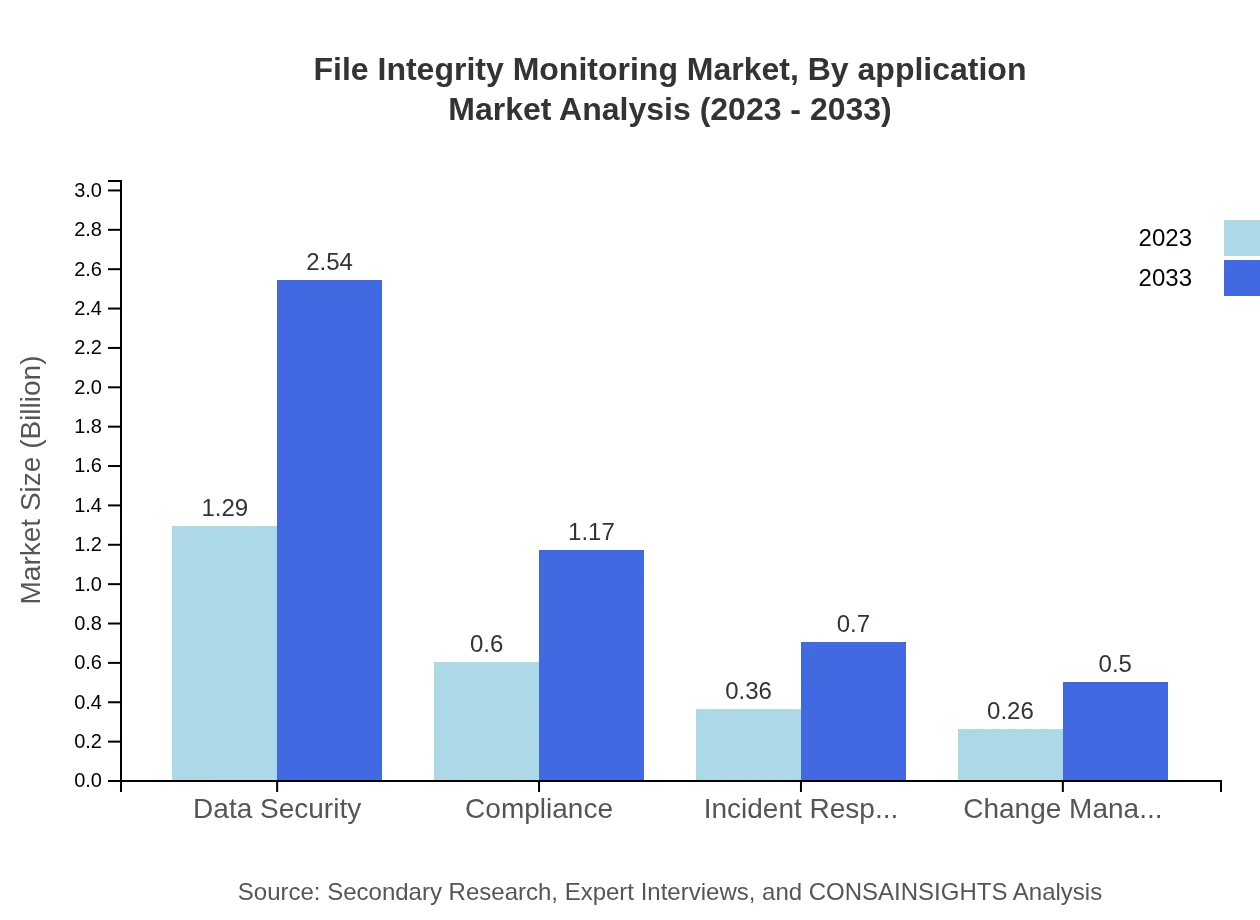
File Integrity Monitoring Market Analysis By Application
The FIM applications are segmented broadly into Data Security, Compliance, Incident Response, Change Management, and more. Data Security leads with a market size of USD 1.29 billion in 2023 and projected growth to USD 2.54 billion by 2033, capturing 51.68% of the market, driven by increasing data breaches and compliance demands.
File Integrity Monitoring Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in File Integrity Monitoring Industry
IBM:
IBM provides integrated security solutions, including FIM, enabling organizations to monitor file changes while ensuring compliance with data protection regulations.McAfee:
McAfee's FIM solutions focus on detecting unauthorized file changes and protecting sensitive data in real-time, catering to various industries with robust security needs.Splunk:
Splunk offers comprehensive FIM capabilities as part of its security information and event management (SIEM) approach, empowering organizations to respond swiftly to potential threats.Symantec:
Symantec delivers FIM solutions that help in monitoring file integrity changes across systems, ensuring regulatory compliance and data security for enterprises.Trend Micro:
Trend Micro provides innovative FIM technologies that integrate seamlessly into broader security frameworks, focusing on providing actionable insights from file integrity data.We're grateful to work with incredible clients.









FAQs
What is the market size of file Integrity Monitoring?
The global file integrity monitoring market is estimated to be valued at approximately $2.5 billion in 2023, with a projected compound annual growth rate (CAGR) of 6.8%, reaching a potential market size of around $4.7 billion by 2033.
What are the key market players or companies in this file Integrity Monitoring industry?
Key players in the file integrity monitoring industry include leading technology firms that specialize in cybersecurity solutions, data management, and software services. Companies such as IBM, McAfee, and Tripwire play prominent roles in this market, delivering robust solutions.
What are the primary factors driving the growth in the file integrity monitoring industry?
Driving factors for growth in file integrity monitoring include increasing concerns over data breaches, evolving regulatory compliance landscape, demand for enhanced data security solutions across industries, and a rising need for real-time monitoring of critical IT infrastructure.
Which region is the fastest Growing in the file Integrity Monitoring?
The fastest-growing region in the file integrity monitoring market is projected to be North America, expected to grow from $0.92 billion in 2023 to $1.81 billion by 2033, driven by high demand for advanced security solutions and significant investment in cybersecurity.
Does ConsaInsights provide customized market report data for the file Integrity Monitoring industry?
Yes, ConsaInsights offers customized market report data tailored for the file integrity monitoring industry, enabling businesses to receive relevant insights, specific market analysis, and strategic recommendations based on their unique needs and requirements.
What deliverables can I expect from this file Integrity Monitoring market research project?
Deliverables for a market research project on file integrity monitoring include detailed market size reports, growth forecasts, competitor analysis, trend identification, regional market insights, and strategic recommendations specifically designed to aid decision-making.
What are the market trends of file Integrity Monitoring?
Market trends in file integrity monitoring include increasing adoption of cloud-based solutions, growth in software-driven services, a focus on regulatory compliance, and an emphasis on automation and AI-driven monitoring solutions to enhance data protection effectiveness.