Hardware Encryption Market Report
Published Date: 31 January 2026 | Report Code: hardware-encryption
Hardware Encryption Market Size, Share, Industry Trends and Forecast to 2033
This report provides an in-depth analysis of the Hardware Encryption market from 2023 to 2033, focusing on market trends, size, and forecasts while presenting insights into industry dynamics and competitive landscape.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
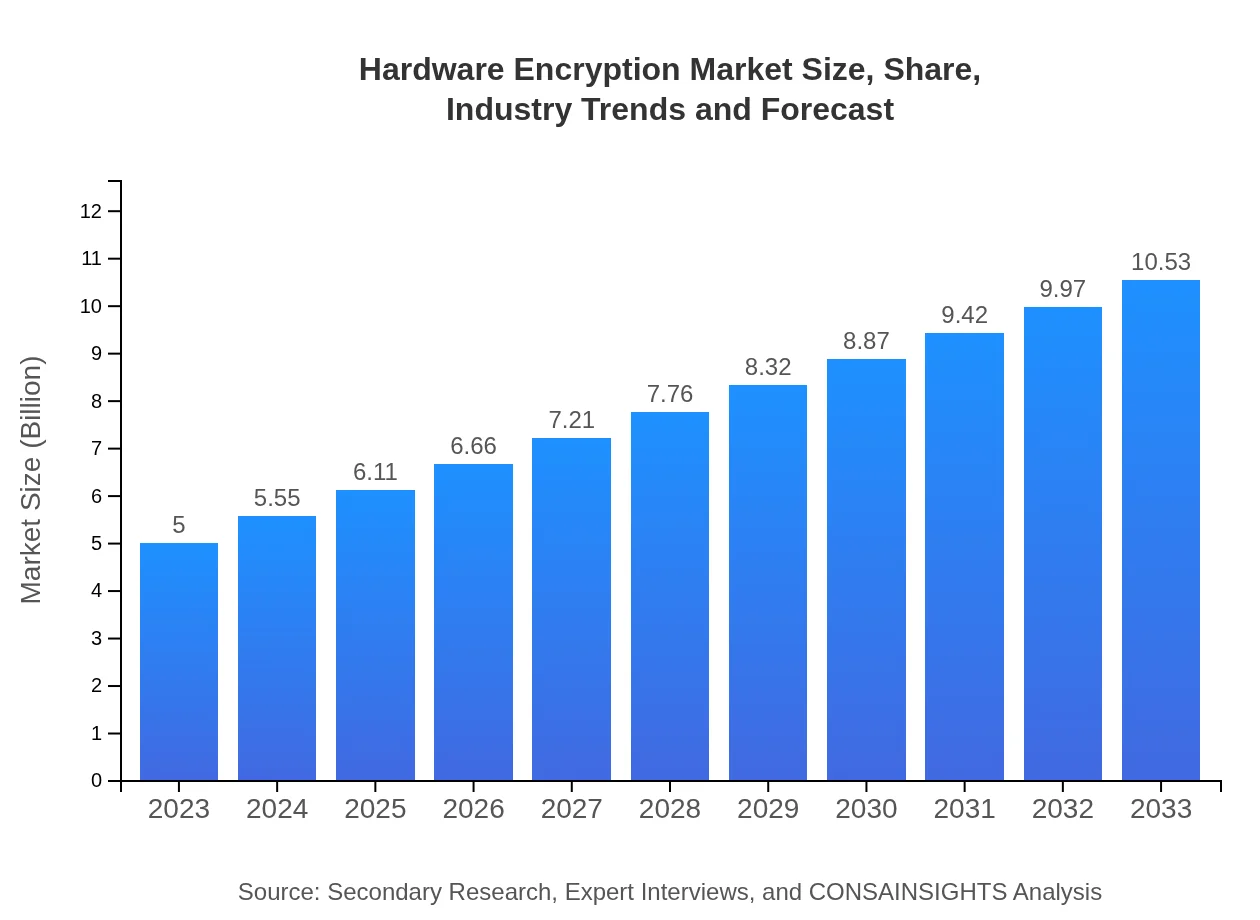
| 2023 Market Size | $5.00 Billion |
| CAGR (2023-2033) | 7.5% |
| 2033 Market Size | $10.53 Billion |
| Top Companies | Symantec Corporation, IBM Corporation, Thales Group, Fortinet, Gemalto |
| Last Modified Date | 31 January 2026 |
Hardware Encryption Market Overview
Customize Hardware Encryption Market Report market research report
- ✔ Get in-depth analysis of Hardware Encryption market size, growth, and forecasts.
- ✔ Understand Hardware Encryption's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Hardware Encryption
What is the Market Size & CAGR of Hardware Encryption market in 2023?
Hardware Encryption Industry Analysis
Hardware Encryption Market Segmentation and Scope
Tell us your focus area and get a customized research report.
Hardware Encryption Market Analysis Report by Region
Europe Hardware Encryption Market Report:
The European hardware encryption market is also poised for growth, with expectations of increasing from $1.37 billion in 2023 to $2.89 billion by 2033. This is largely due to the enforcement of the GDPR and a strong focus on data protection compliance across various sectors.Asia Pacific Hardware Encryption Market Report:
The Asia Pacific region is projected to experience significant growth in the hardware encryption market, with a market size of $1.09 billion in 2023, increasing to $2.29 billion by 2033. This growth is driven by rising digitalization, a surge in cyberattacks, and the adoption of security solutions by enterprises.North America Hardware Encryption Market Report:
North America holds the largest market share in the hardware encryption sector, with a market size of $1.69 billion in 2023, projected to nearly double to $3.56 billion by 2033. The presence of major companies, combined with stringent compliance regulations driving enterprises to invest in data security, supports this growth.South America Hardware Encryption Market Report:
In South America, the hardware encryption market is expected to grow from $0.45 billion in 2023 to $0.95 billion by 2033. Increasing awareness around data protection vulnerabilities and rising mobile device penetration will fuel demand for encryption solutions.Middle East & Africa Hardware Encryption Market Report:
In the Middle East and Africa, the hardware encryption market is projected to rise from $0.39 billion in 2023 to $0.83 billion by 2033. Growing cybersecurity threats and an increasing number of cybersecurity initiatives by governments and private sectors are propelling this growth.Tell us your focus area and get a customized research report.
Hardware Encryption Market Analysis By Product
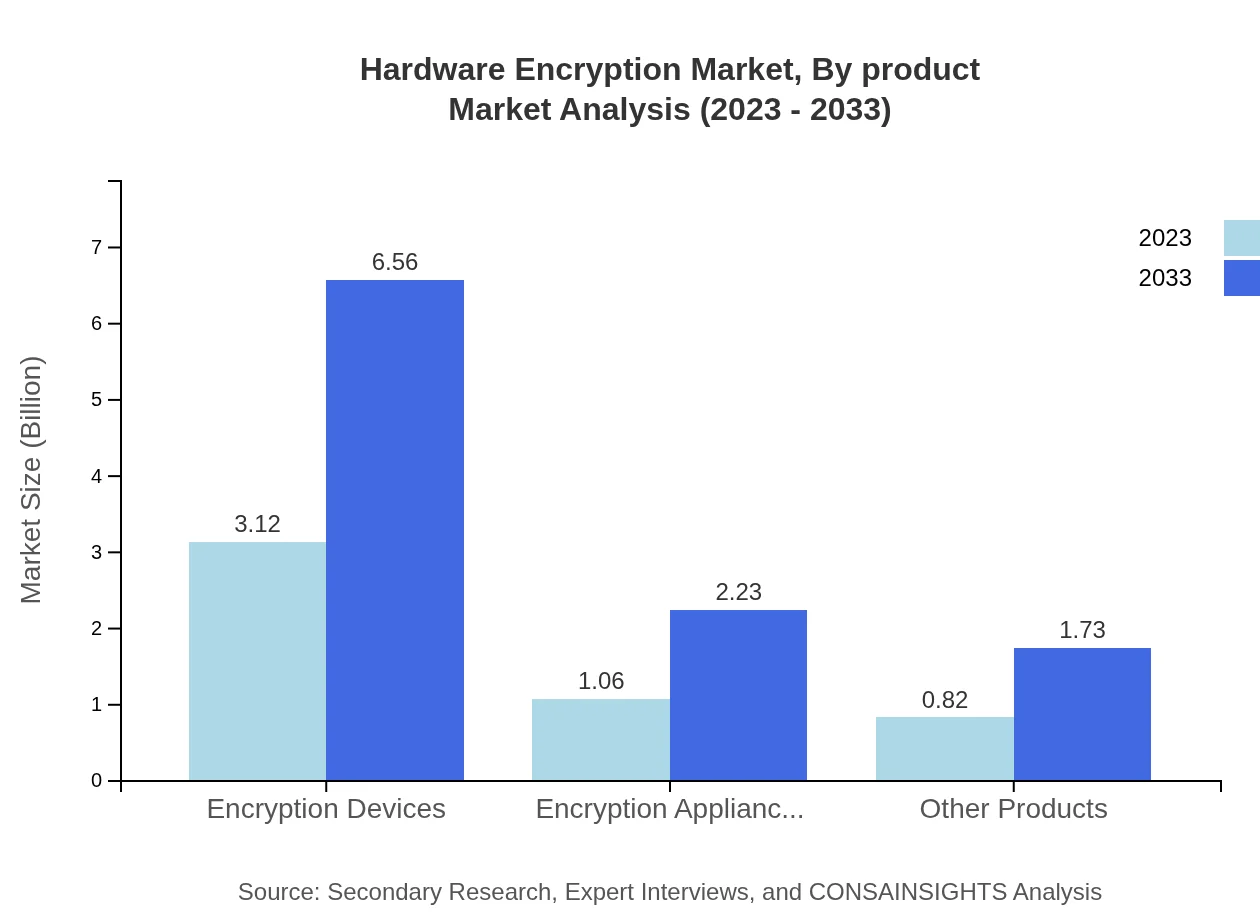
In the Hardware Encryption market, encryption devices emerged as the largest segment with a market size of $3.12 billion in 2023 and projected to grow to $6.56 billion by 2033. Encryption appliances follow, growing from $1.06 billion in 2023 to $2.23 billion by 2033. Other products contribute significantly, reflecting the diverse requirements across various applications and end-users.
Hardware Encryption Market Analysis By Application
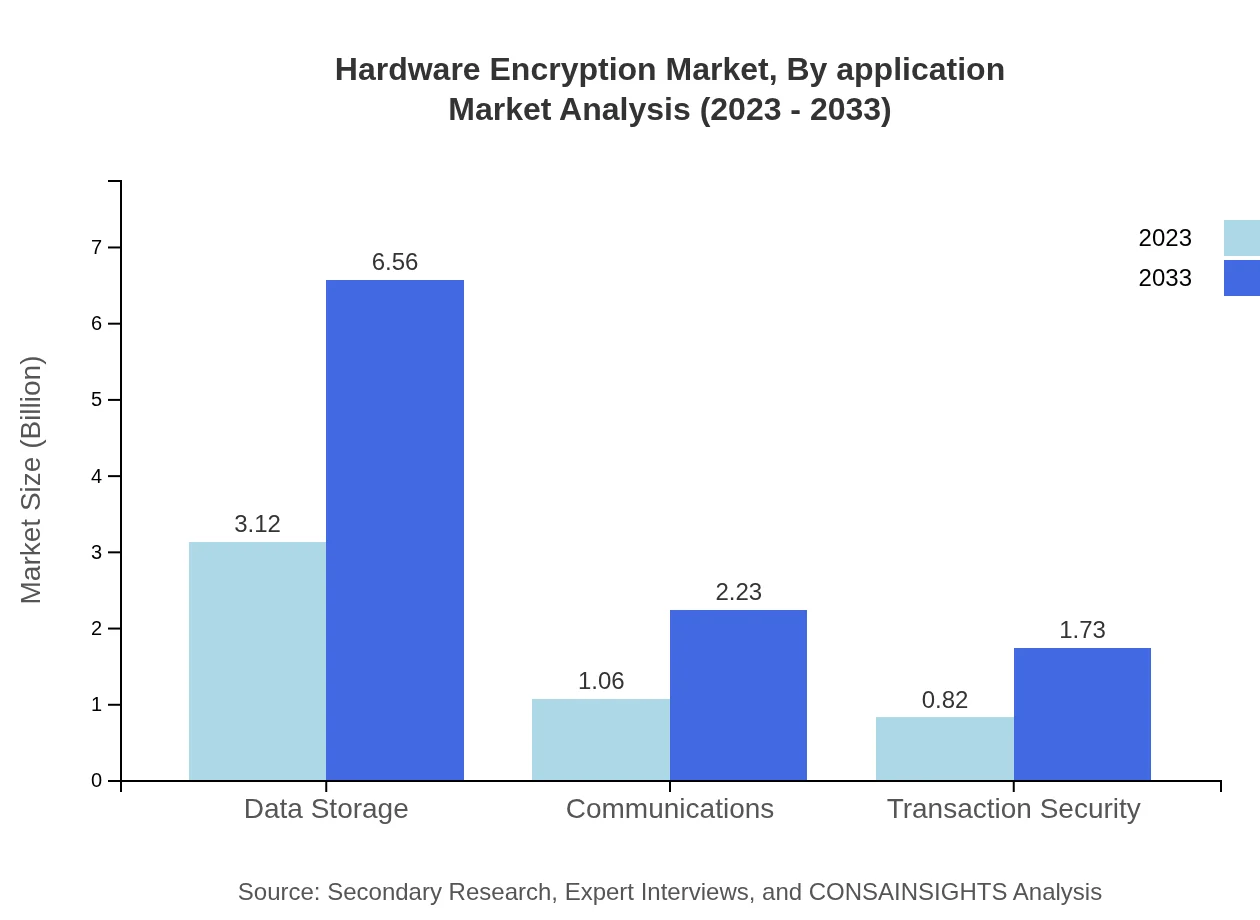
The primary applications of hardware encryption are in data storage, communications, and transaction security. The data storage segment is projected to maintain a substantial size, correlating with the growth in data breaches. Communications and transaction security are also critical segments, driven by the need for secure exchanges of sensitive information between parties.
Hardware Encryption Market Analysis By End User
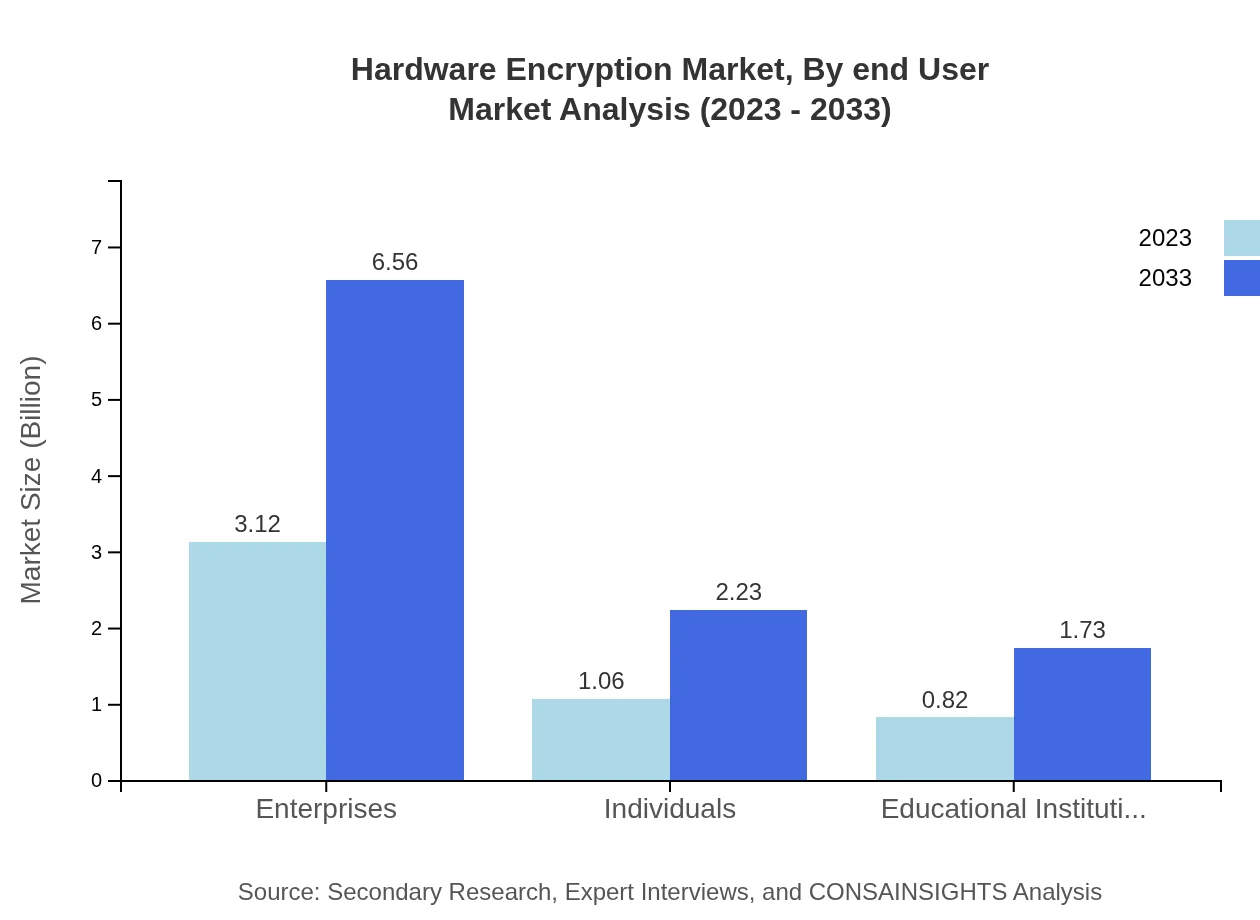
Enterprises represent the largest portion of the end-user market, expected to make up 62.37% of market share in 2023, with growth to 62.37% in 2033. Individuals and educational institutions also contribute, emphasizing the overall demand for personal and institutional data security solutions.
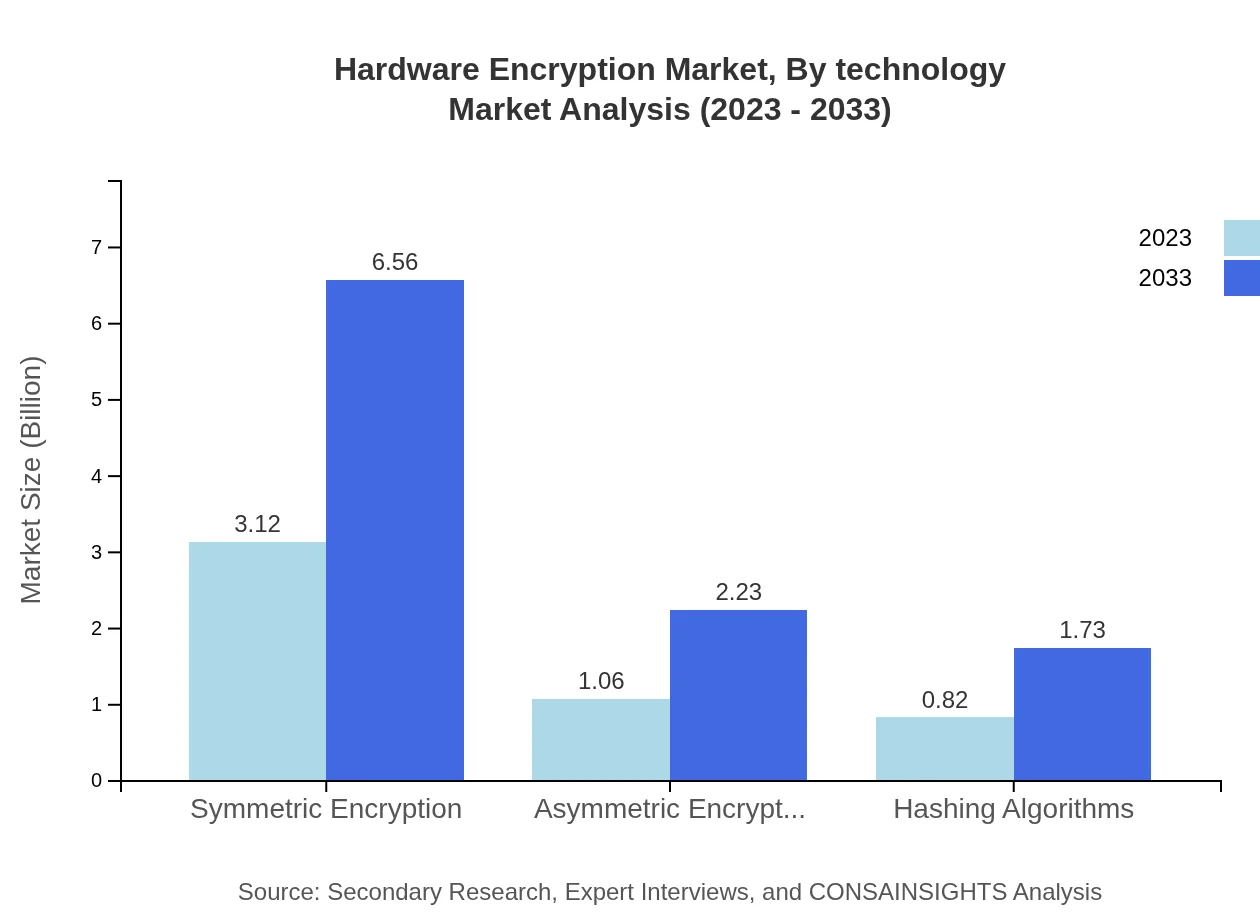
Hardware Encryption Market Analysis By Technology
The Hardware Encryption market is distinguishable by technology types such as symmetric encryption, asymmetric encryption, and hashing algorithms. Symmetric encryption is expected to dominate the market share, with sustained growth through 2033, while asymmetric encryption and hashing algorithms also serve significant roles in diverse application areas.
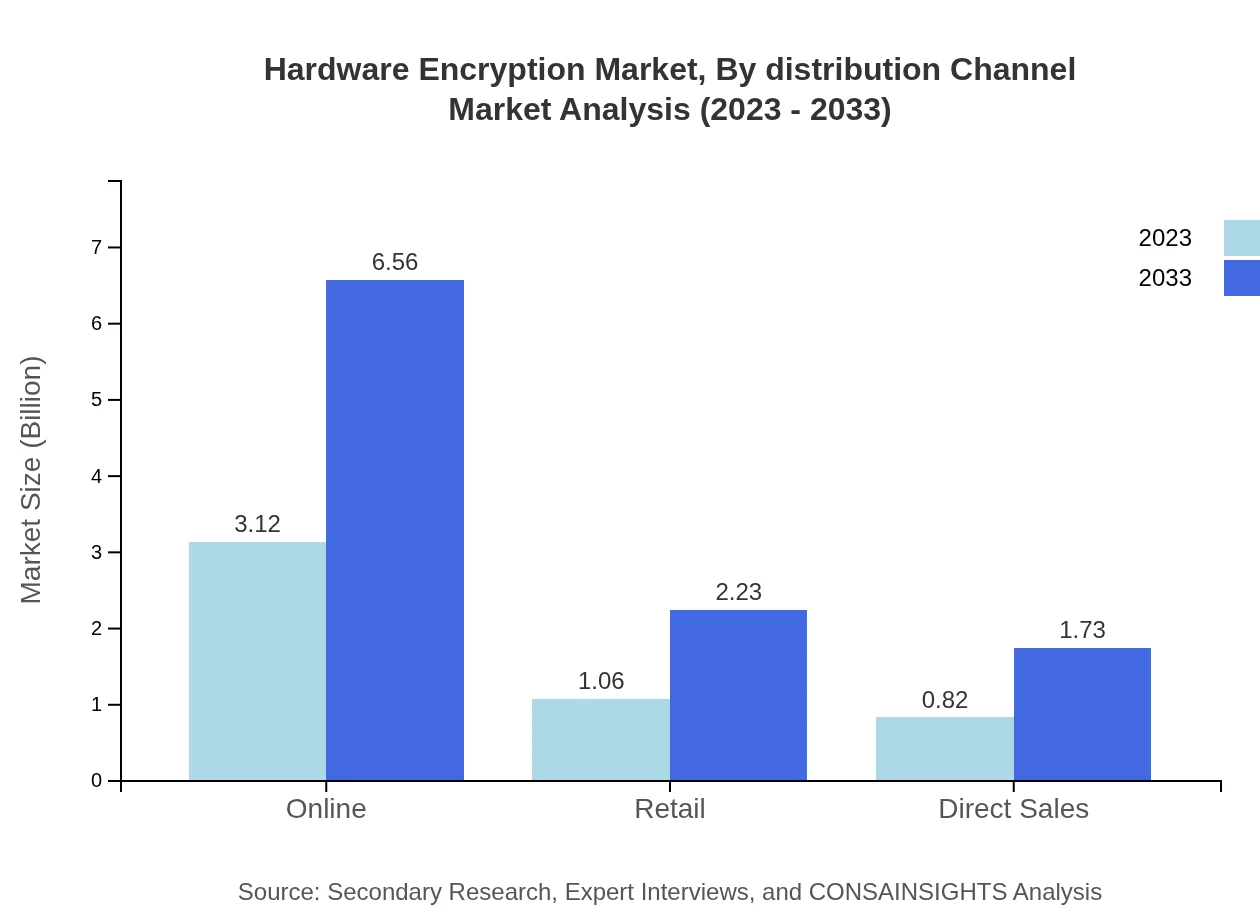
Hardware Encryption Market Analysis By Distribution Channel
The distribution of hardware encryption products occurs through multiple channels including direct sales, online retail, and retail outlets. Direct sales maintain a significant share, but online channels are witnessing rapid growth due to the increasing trend of e-commerce. Retail outlets continue to provide accessibility to end-users, enhancing market penetration.
Hardware Encryption Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Hardware Encryption Industry
Symantec Corporation:
Symantec provides comprehensive cybersecurity solutions, including advanced hardware encryption products, helping businesses protect sensitive information from threats.IBM Corporation:
IBM is a leader in technology and consulting, offering hardware encryption solutions that ensure data security and comply with various regulations.Thales Group:
Thales Group specializes in data security and encryption technologies, providing a range of hardware solutions to protect digital assets.Fortinet:
Fortinet delivers cybersecurity solutions, including hardware encryption products, designed to protect networks and sensitive data from cyber threats.Gemalto:
Gemalto, now part of Thales, focuses on providing digital security solutions, including encryption technologies across various sectors.We're grateful to work with incredible clients.









FAQs
What is the market size of hardware Encryption?
The global hardware encryption market is valued at approximately $5 billion in 2023 and is expected to grow at a CAGR of 7.5%, reaching significant market size by 2033.
What are the key market players or companies in this hardware Encryption industry?
Key players in the hardware encryption market include major technology firms specializing in cybersecurity, data storage solutions, and encryption technology products, although specific companies would be detailed in a comprehensive market report.
What are the primary factors driving the growth in the hardware Encryption industry?
Factors driving growth include increasing data breach incidents, rising concerns over data privacy, regulatory compliance requirements, and the growing demand for secure communication across various sectors.
Which region is the fastest Growing in the hardware Encryption?
North America is expected to be the fastest-growing region in the hardware encryption market, with market size projected to grow from $1.69 billion in 2023 to $3.56 billion by 2033.
Does ConsaInsights provide customized market report data for the hardware Encryption industry?
Yes, ConsaInsights offers customized market reports tailored to specific needs in the hardware encryption industry, catering to various clients' demands for detailed insights and analysis.
What deliverables can I expect from this hardware Encryption market research project?
Deliverables typically include comprehensive market analysis reports, detailed segmentation data, trend analysis, forecasts, and regional insights tailored to the hardware encryption sector.
What are the market trends of hardware Encryption?
Current trends include the rising adoption of encryption devices for secure data storage, a shift towards asymmetric encryption methods for enhanced security, and increased investment in digital transformation across enterprises.