Hardware Security Modules Market Report
Published Date: 31 January 2026 | Report Code: hardware-security-modules
Hardware Security Modules Market Size, Share, Industry Trends and Forecast to 2033
This report provides a comprehensive analysis of the Hardware Security Modules (HSM) market, detailing market size, growth forecasts from 2023 to 2033, an overview of the industry's landscape, and vital insights into regional trends and key players.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
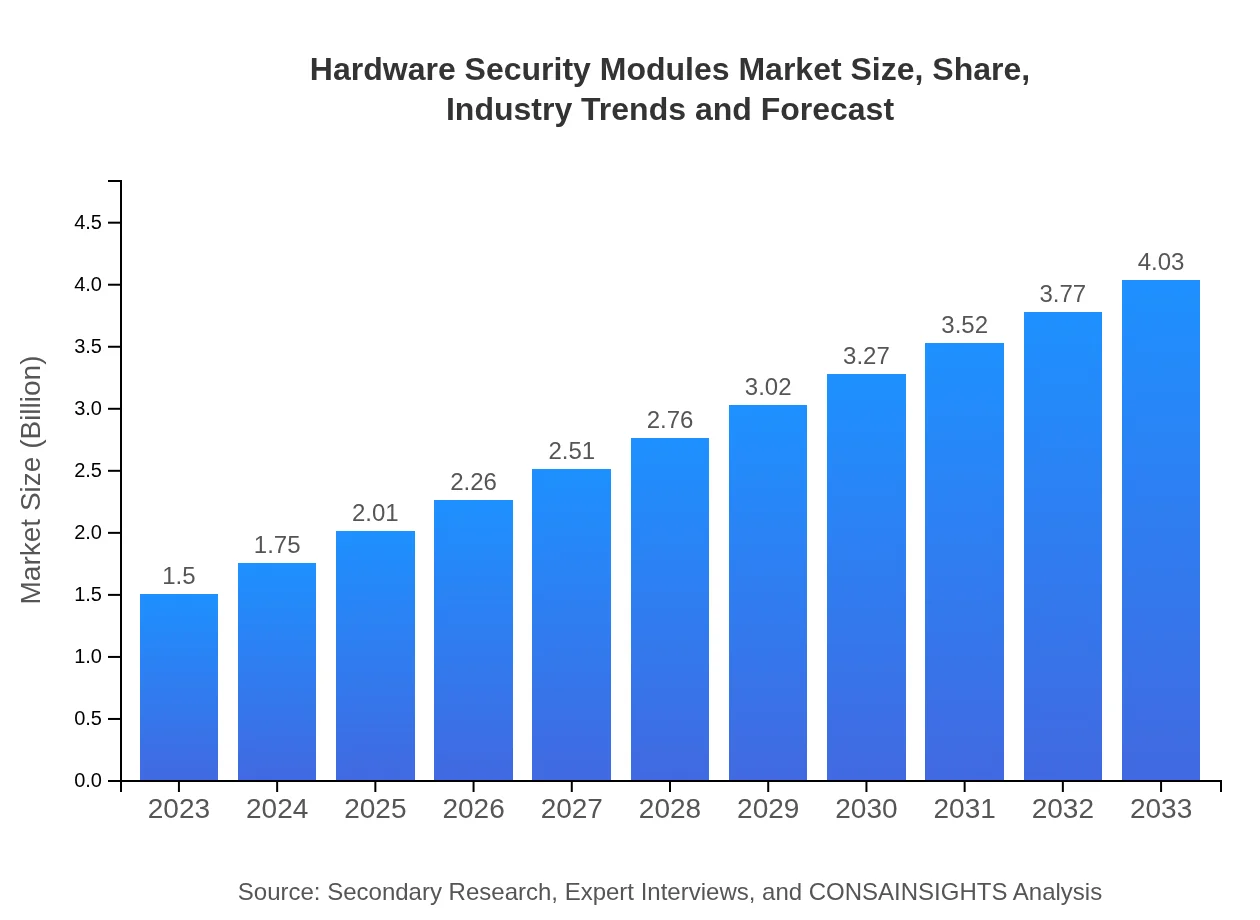
| 2023 Market Size | $1.50 Billion |
| CAGR (2023-2033) | 10% |
| 2033 Market Size | $4.03 Billion |
| Top Companies | Thales Group, Gemalto (part of Thales), IBM Corporation, Entrust Datacard, Microchip Technology |
| Last Modified Date | 31 January 2026 |
Hardware Security Modules Market Overview
Customize Hardware Security Modules Market Report market research report
- ✔ Get in-depth analysis of Hardware Security Modules market size, growth, and forecasts.
- ✔ Understand Hardware Security Modules's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Hardware Security Modules
What is the Market Size & CAGR of Hardware Security Modules market in 2023?
Hardware Security Modules Industry Analysis
Hardware Security Modules Market Segmentation and Scope
Tell us your focus area and get a customized research report.
Hardware Security Modules Market Analysis Report by Region
Europe Hardware Security Modules Market Report:
Europe's HSM market is expected to grow from $0.48 billion in 2023 to $1.28 billion by 2033. Increased focus on GDPR compliance and growing security concerns among organizations fuel market demand.Asia Pacific Hardware Security Modules Market Report:
In the Asia Pacific region, the Hardware Security Modules market is growing, with a projected market size of $0.29 billion in 2023 expected to increase to $0.78 billion by 2033. The growth is propelled by rapid digital transformation and increased cyber threats, which prompt businesses to mandate robust security solutions.North America Hardware Security Modules Market Report:
North America dominates the HSM market, with expected growth from $0.51 billion in 2023 to $1.36 billion by 2033. The region’s advanced digital infrastructure, coupled with stringent data security regulations, continues to drive this market's expansion.South America Hardware Security Modules Market Report:
The South American market remains smaller but poised for growth, with an increase from $0.09 billion in 2023 to $0.23 billion by 2033. The rise in data protection regulations is driving demand for HSMs in sectors such as finance and healthcare.Middle East & Africa Hardware Security Modules Market Report:
The Middle East and Africa region shows a notable increase in market size from $0.14 billion in 2023 to $0.38 billion by 2033. Increased investments in cybersecurity and awareness of digital threats are driving the adoption of HSMs.Tell us your focus area and get a customized research report.
Hardware Security Modules Market Analysis By Type
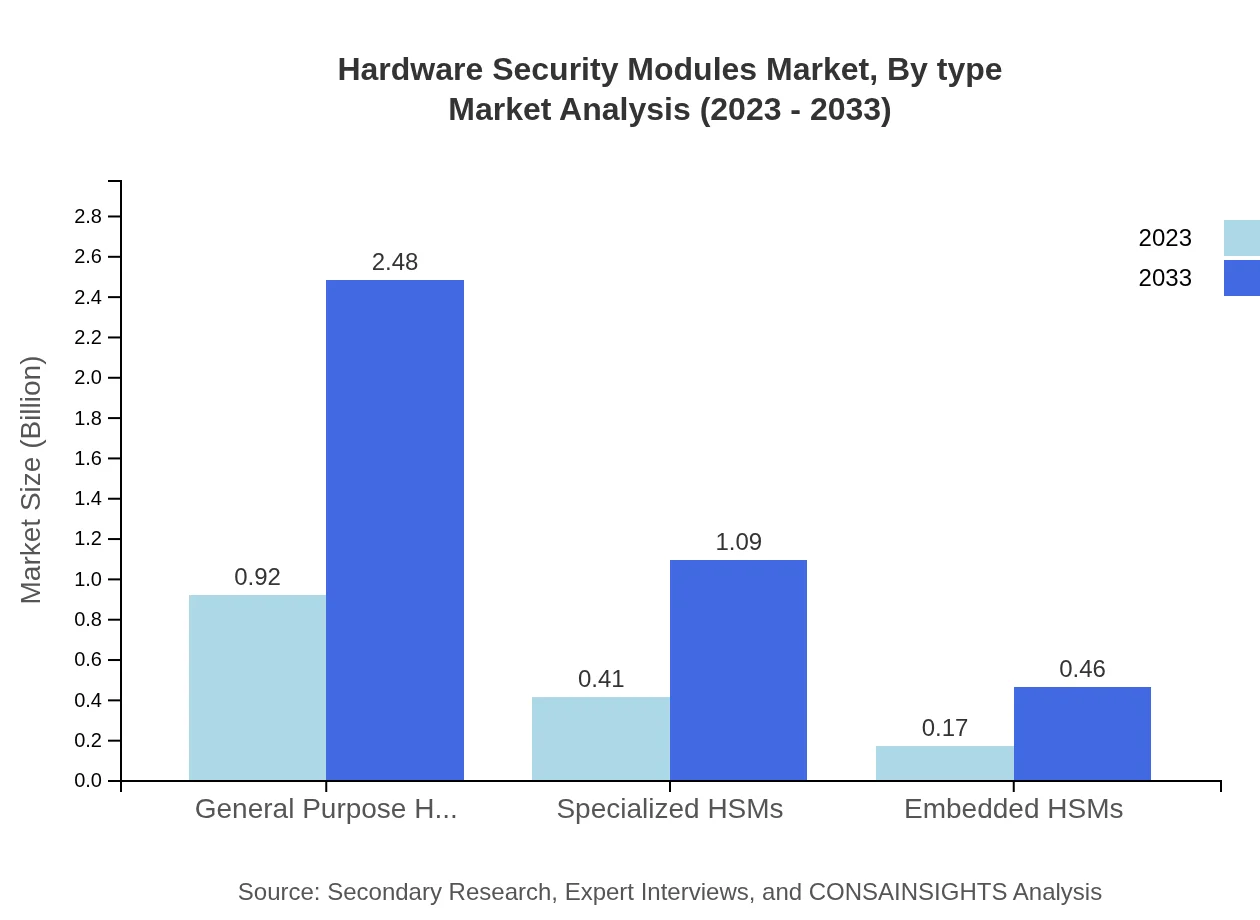
The Hardware Security Modules market can be categorized into three main types: General Purpose HSMs, Specialized HSMs, and Embedded HSMs. General Purpose HSMs dominate the market, expected to grow from $0.92 billion in 2023 to $2.48 billion by 2033, capturing 61.56% market share. Specialized HSMs, while smaller, represent a significant segment, increasing from $0.41 billion to $1.09 billion, maintaining a 27.07% share. Embedded HSMs cater to specific applications, with a projected market growth from $0.17 billion to $0.46 billion, accounting for 11.37% of the total market.
Hardware Security Modules Market Analysis By Deployment
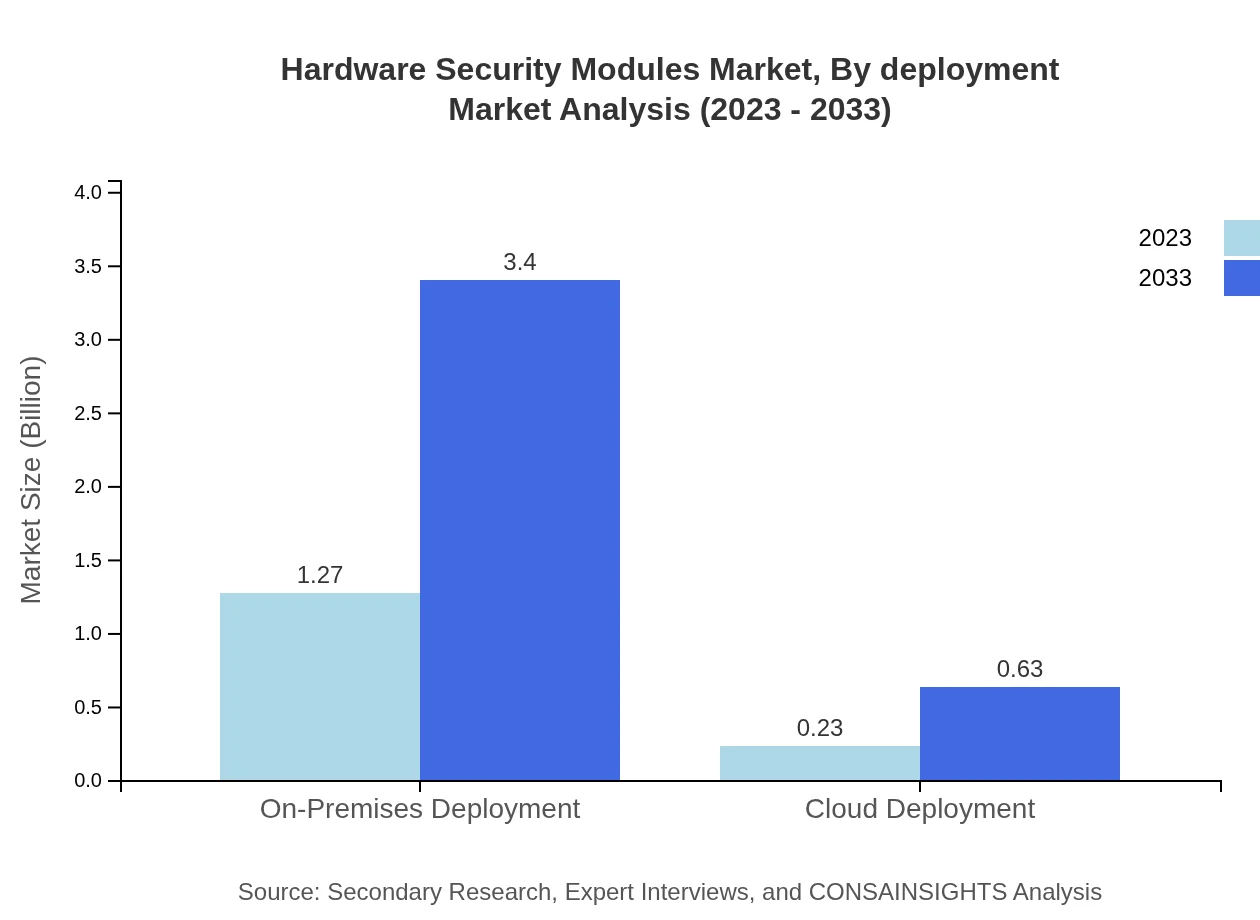
Deployment modes are classified into On-Premises and Cloud. On-Premises HSMs dominate, expecting to grow significantly from $1.27 billion in 2023 to $3.40 billion by 2033, holding an 84.34% market share. In contrast, Cloud Deployment is anticipated to grow more rapidly from $0.23 billion to $0.63 billion, representing an increasing trend in scalable security solutions with a 15.66% share.
Hardware Security Modules Market Analysis By Application
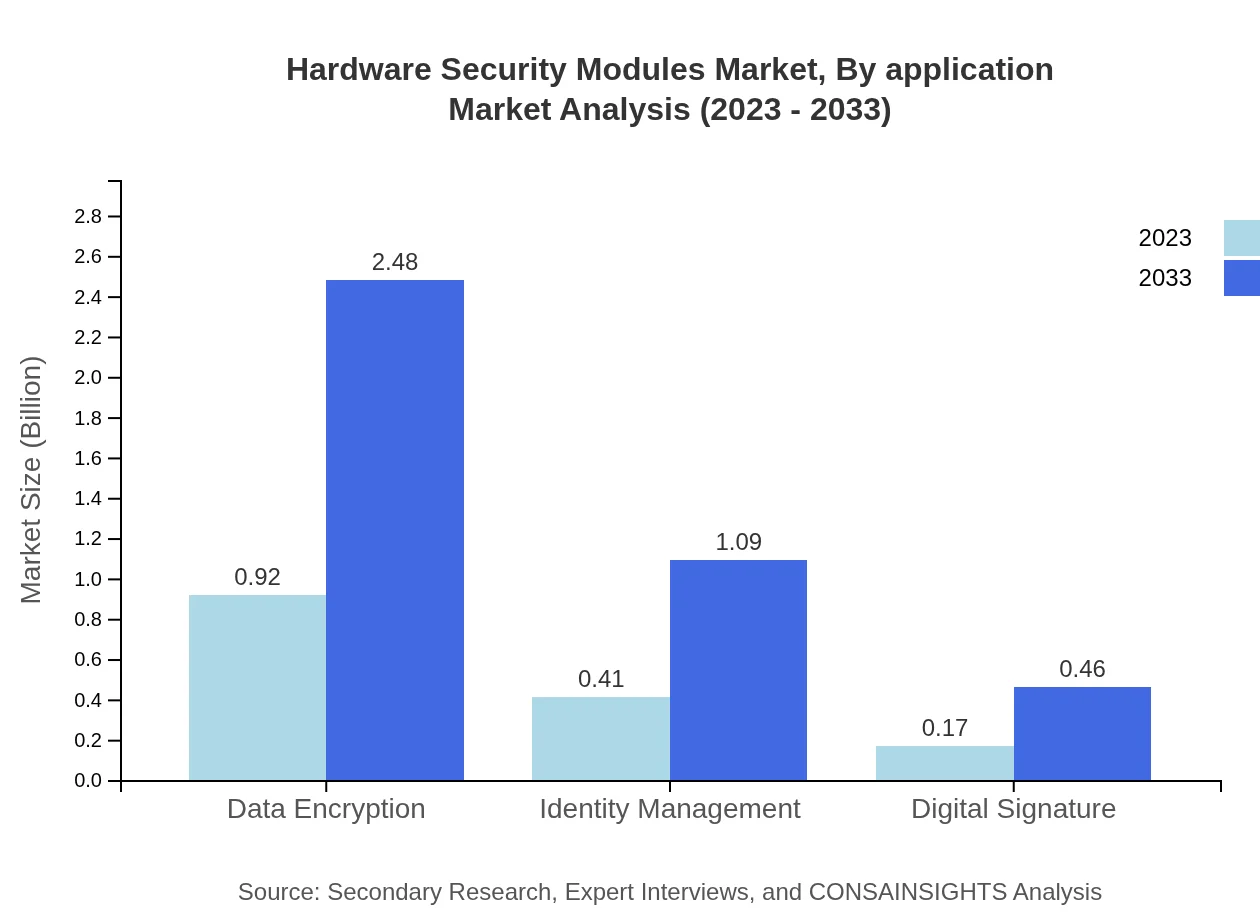
Applications of HSMs span several domains, including Data Encryption, Identity Management, and Digital Signatures. Data Encryption leads the segment with a market growth from $0.92 billion to $2.48 billion (61.56% share). Identity Management follows closely with growth from $0.41 billion to $1.09 billion (27.07% share), while Digital Signature applications grow from $0.17 billion to $0.46 billion, representing 11.37% share.
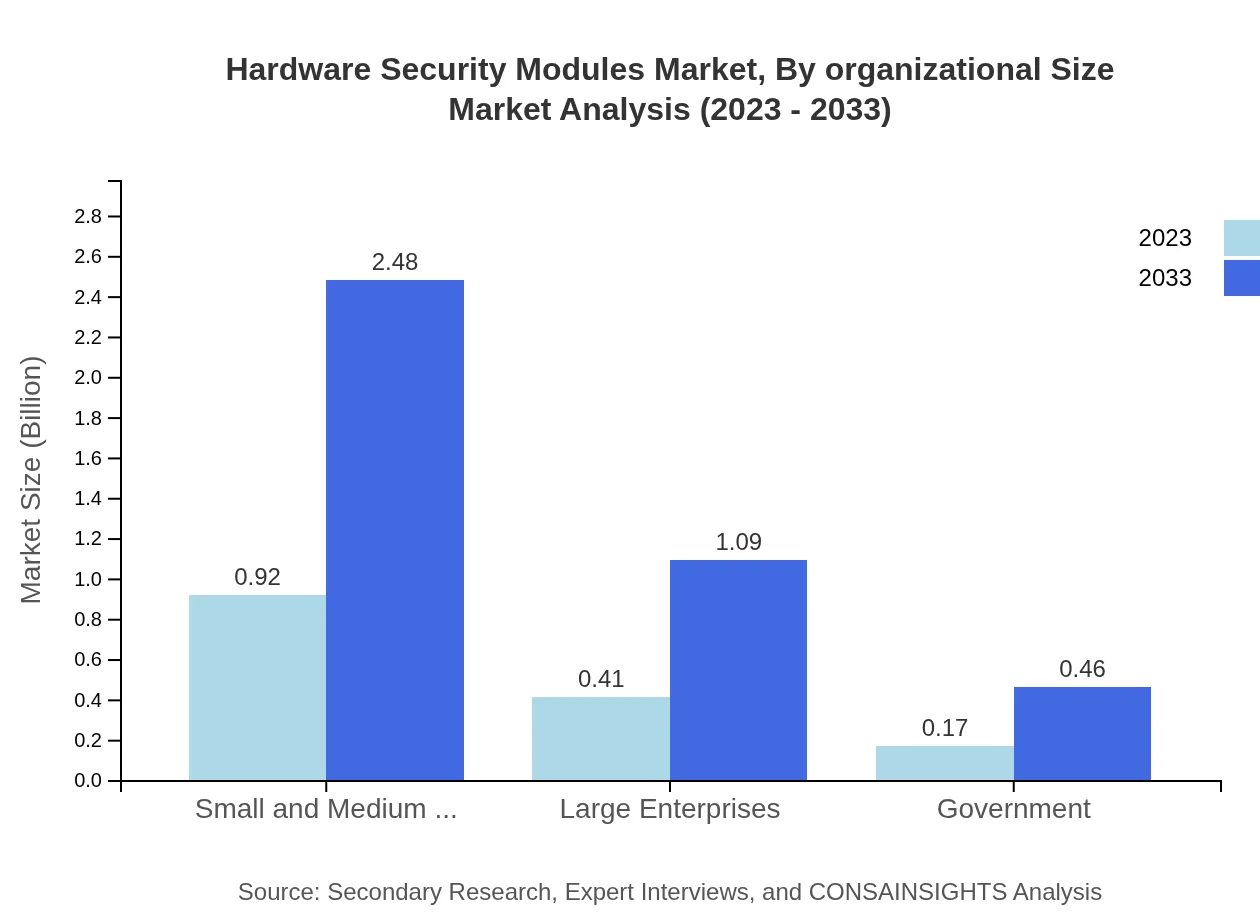
Hardware Security Modules Market Analysis By Organizational Size
The segmentation by organizational size includes Small and Medium Enterprises (SMEs) and Large Enterprises. SMEs dominate, with a market increase from $0.92 billion to $2.48 billion (61.56% share), driven by the growing emphasis on affordable security solutions. Large Enterprises are also vital, with growth from $0.41 billion to $1.09 billion (27.07% share), reflecting a continued investment in extensive security infrastructures.
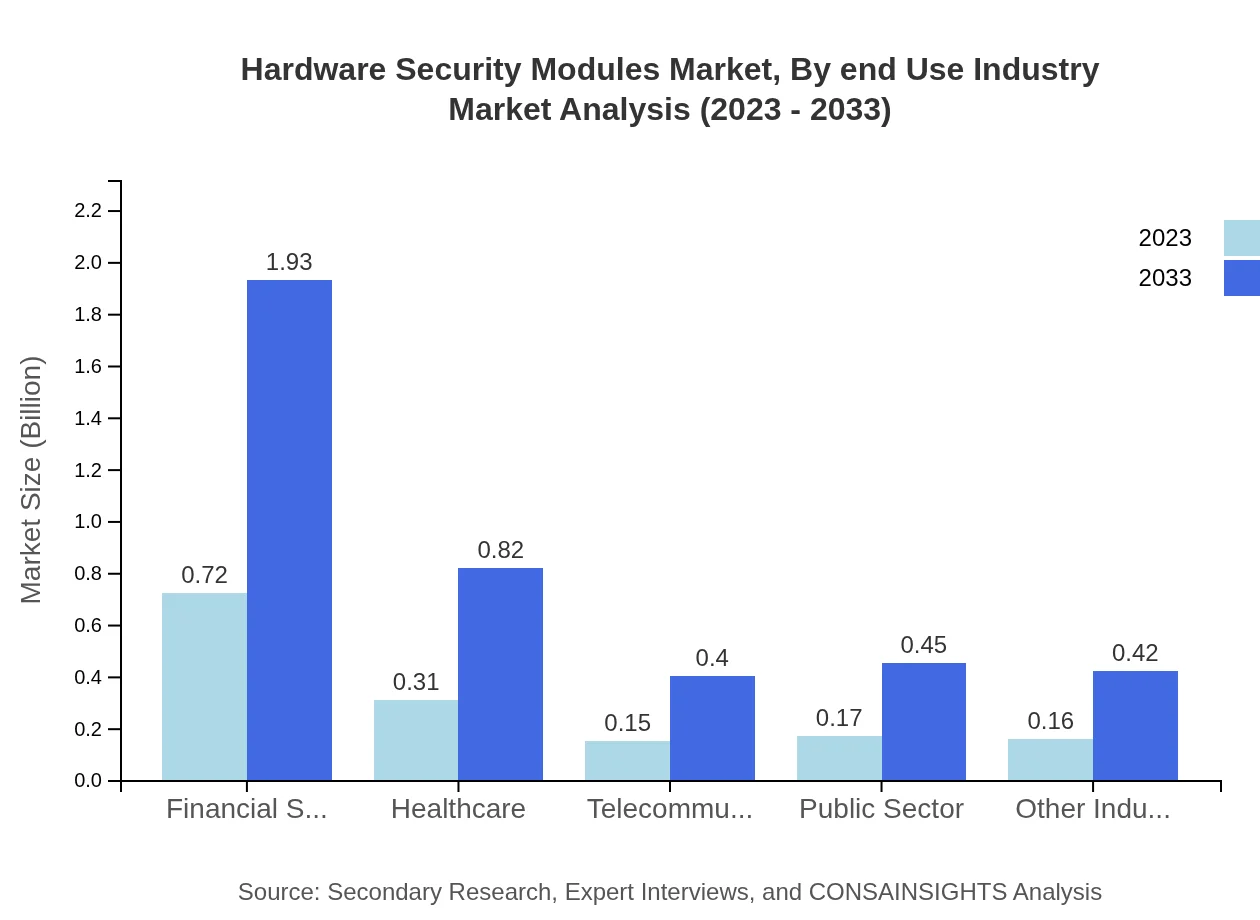
Hardware Security Modules Market Analysis By End Use Industry
Various industries leverage HSMs significantly, with Financial Services leading at $0.72 billion growing to $1.93 billion (47.92% share). Other sectors include Healthcare ($0.31 billion to $0.82 billion, 20.39% share), Telecommunications ($0.15 billion to $0.40 billion, 10.05% share), Public Sector ($0.17 billion to $0.45 billion, 11.12% share), and Other Industries ($0.16 billion to $0.42 billion, 10.52% share).
Hardware Security Modules Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Hardware Security Modules Industry
Thales Group:
A global leader in data security, offering advanced HSMs to secure transactions and safeguard digital assets across various industries.Gemalto (part of Thales):
Specializes in HSM solutions for secure data encryption and digital signatures, serving a diverse range of industries.IBM Corporation:
Provides a range of HSM solutions alongside enterprise security solutions, ensuring robust protection for financial and government institutions.Entrust Datacard:
Focuses on providing secure identity and access solutions, integrating HSM capabilities into their product offerings.Microchip Technology:
Delivers embedded security solutions, including HSMs, paving the way for secure IoT devices and connected systems.We're grateful to work with incredible clients.









FAQs
What is the market size of hardware Security Modules?
The global market size for Hardware Security Modules (HSMs) is currently valued at approximately $1.5 billion, with a projected CAGR of 10% from 2023 to 2033, indicating significant industry growth.
What are the key market players or companies in this hardware Security Modules industry?
Key market players in the hardware-security-modules industry include established giants, emerging companies, and specialized providers contributing to innovations and solution development across various sectors.
What are the primary factors driving the growth in the hardware Security Modules industry?
The growth of the hardware-security-modules industry is primarily driven by increasing cybersecurity threats, the rising need for data protection regulations, and the growing demand for secure payment solutions across various industries.
Which region is the fastest Growing in the hardware Security Modules?
North America is currently the fastest-growing region for hardware security modules, with a market growth from $0.51 billion in 2023 to $1.36 billion by 2033, representing a robust development in technology adoption.
Does ConsaInsights provide customized market report data for the hardware Security Modules industry?
Yes, ConsaInsights offers customized market report data tailored to specific needs within the hardware security modules industry, providing in-depth analysis and insights that fit individual business requirements.
What deliverables can I expect from this hardware Security Modules market research project?
From this market research project, you can expect detailed reports, analysis of trends, forecasts, regional insights, competitor analysis, and specific data segmented by application and deployment types.
What are the market trends of hardware Security Modules?
Current market trends in hardware security modules include increased demand for cloud deployment, innovative security solutions in financial services, and rising integration of HSMs with emerging technologies to enhance data security.