Iam Security Services Market Report
Published Date: 31 January 2026 | Report Code: iam-security-services
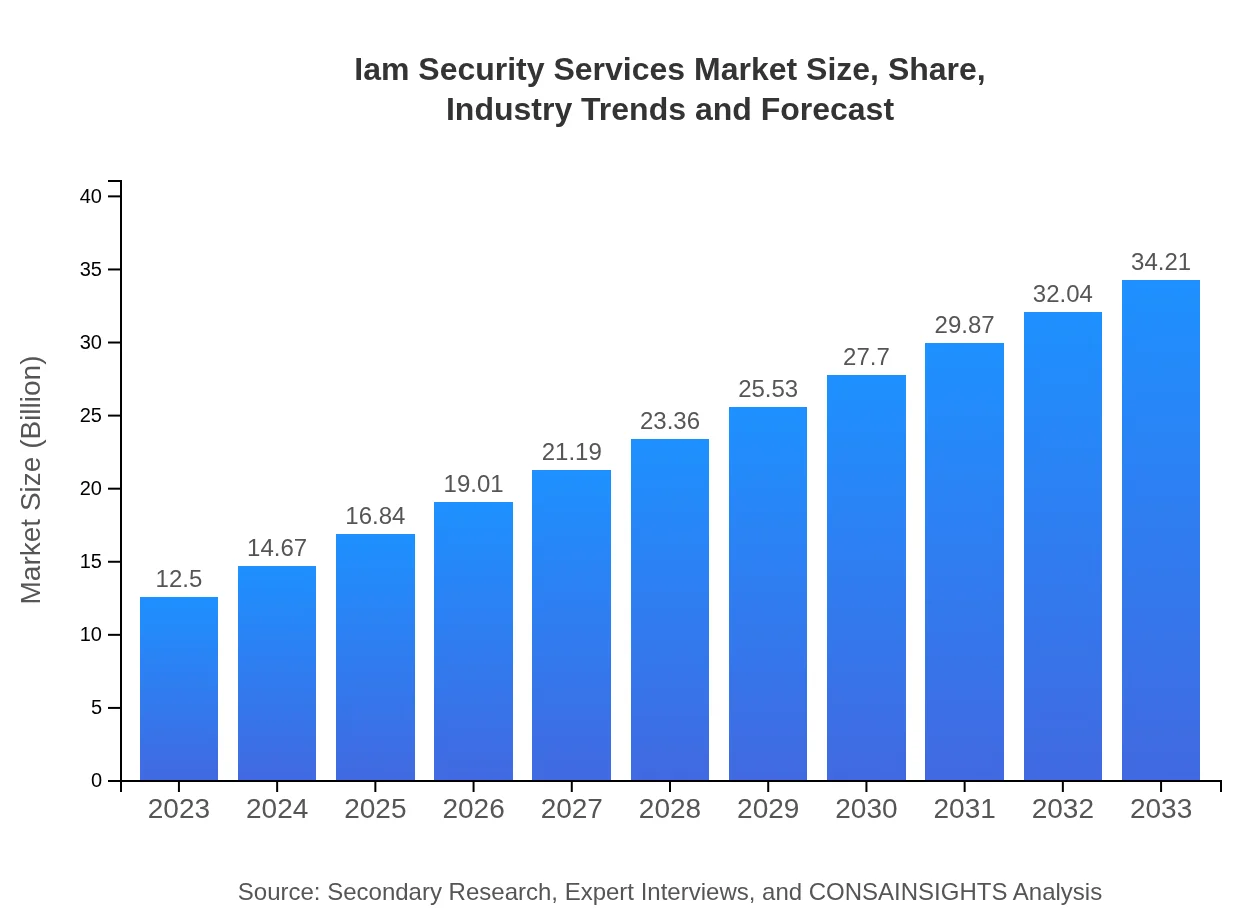
Iam Security Services Market Size, Share, Industry Trends and Forecast to 2033
This report provides a detailed analysis of the Iam Security Services market from 2023 to 2033, highlighting market trends, size, growth potential, and key players. Insights on regional performance and technological advancements are included to give a comprehensive view of the industry's future.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
| 2023 Market Size | $12.50 Billion |
| CAGR (2023-2033) | 10.2% |
| 2033 Market Size | $34.21 Billion |
| Top Companies | IBM Corporation, Microsoft Corporation, Okta, Inc., SailPoint Technologies, Ping Identity Corporation |
| Last Modified Date | 31 January 2026 |
Iam Security Services Market Overview
Customize Iam Security Services Market Report market research report
- ✔ Get in-depth analysis of Iam Security Services market size, growth, and forecasts.
- ✔ Understand Iam Security Services's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Iam Security Services
What is the Market Size & CAGR of Iam Security Services market in 2023 and 2033?
Iam Security Services Industry Analysis
Iam Security Services Market Segmentation and Scope
Tell us your focus area and get a customized research report.
Iam Security Services Market Analysis Report by Region
Europe Iam Security Services Market Report:
The European market is projected to expand from $3.70 billion in 2023 to $10.13 billion by 2033. This growth is influenced by stringent data protection regulations like GDPR and a rising awareness of data security, driving organizations to adopt comprehensive IAM solutions.Asia Pacific Iam Security Services Market Report:
The Asia Pacific region is projected to show significant growth in the Iam Security Services market, increasing from $2.19 billion in 2023 to $6.00 billion by 2033. This growth is driven by the rapid adoption of digital services, government initiatives for enhanced cybersecurity frameworks, and increased awareness of identity management solutions among enterprises in countries like India and China, making it a critical market for IAM suppliers.North America Iam Security Services Market Report:
North America remains the largest market for Iam Security Services, with its size anticipated to grow from $4.87 billion in 2023 to $13.33 billion by 2033. High investments in cybersecurity, stringent regulatory requirements, and the presence of key market players contribute to this region's significant growth potential.South America Iam Security Services Market Report:
In South America, the market is expected to grow from $0.50 billion in 2023 to approximately $1.37 billion by 2033. The growth in this region is fueled by an uptick in digital transformation initiatives and increased investments in cybersecurity infrastructure, albeit at a slower pace compared to developed markets.Middle East & Africa Iam Security Services Market Report:
In the Middle East and Africa, the market size is expected to increase from $1.24 billion in 2023 to $3.39 billion by 2033. Growth in this region is driven by increasing cybersecurity threats, government regulations mandating stronger security measures, and greater emphasis on data privacy.Tell us your focus area and get a customized research report.
Iam Security Services Market Analysis Identity_management
Global IAM Security Services Market, By Product Market Analysis (2023 - 2033)
Identity Management is a key segment in the Iam Security Services market, estimated to reach $21.53 billion by 2033 from $7.87 billion in 2023, capturing 62.94% of the market share. This segment's growth is attributed to the increasing need for user authentication and identity verification systems that ensure secure access to resources.
Iam Security Services Market Analysis Access_management
Global IAM Security Services Market, By Application Market Analysis (2023 - 2033)
Access Management is another vital segment, expected to grow from $3.09 billion in 2023 to $8.46 billion in 2033, holding 24.72% of the market share. The growing demand for secure access control mechanisms among enterprises drives this segment's expansion.
Iam Security Services Market Analysis Security_services
Global IAM Security Services Market, By Deployment Mode Market Analysis (2023 - 2033)
Security Services, which include comprehensive authentication and authorization solutions, are projected to reach $4.22 billion by 2033 from $1.54 billion in 2023, making up 12.34% of the market share as organizations focus on protecting sensitive information.
Iam Security Services Market Analysis Bfsis
Global IAM Security Services Market, By End-User Industry Market Analysis (2023 - 2033)
The BFSI (Banking, Financial Services, and Insurance) sector remains a crucial segment, expected to grow from $6.07 billion in 2023 to $16.60 billion by 2033, representing 48.52% of the market share. This growth reflects the industry's stringent compliance requirements and risk management strategies.
Iam Security Services Market Analysis Healthcare
Global IAM Security Services Market Trends Market Analysis (2023 - 2033)
Healthcare remains an emerging segment, with revenue expected to rise from $2.54 billion in 2023 to $6.96 billion by 2033. The segment captures 20.33% of the market share, driven by the need for enhanced patient data privacy and compliance with health regulations.
Iam Security Services Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Iam Security Services Industry
IBM Corporation:
IBM provides a comprehensive suite of IAM solutions, including identity governance, access management, and privileged access management, designed to protect enterprises from security threats.Microsoft Corporation:
Microsoft offers robust IAM services integrated with its Azure cloud platform, facilitating secure identity management and access controls for organizations across various sectors.Okta, Inc.:
Okta specializes in identity and access management solutions, supporting enterprises in managing user identities and ensuring secure access to applications.SailPoint Technologies:
SailPoint is renowned for its identity governance solutions, enabling organizations to manage, unify, and secure user identities across complex IT environments.Ping Identity Corporation:
Ping Identity focuses on intelligent identity solutions, empowering organizations to provide secure access to their applications and services amidst growing cybersecurity threats.We're grateful to work with incredible clients.









FAQs
What is the market size of iam Security Services?
The IAM security services market is projected to grow from $12.5 billion in 2023 to significantly higher figures by 2033, with a Compound Annual Growth Rate (CAGR) of approximately 10.2% over the forecast period.
What are the key market players or companies in this iam Security Services industry?
Key players in the IAM security services market include global leaders such as IBM, Microsoft, Oracle, and Cisco. These companies are driving innovation and setting benchmarks through their extensive service offerings and robust security technologies.
What are the primary factors driving the growth in the iam Security Services industry?
Growth in the IAM security services industry is largely driven by the rising demand for secure access controls, stringent regulatory compliance mandates, and the increasing threat of cyberattacks, compelling businesses to implement robust identity management solutions.
Which region is the fastest Growing in the iam Security Services?
Among the regions, Europe is the fastest-growing market for IAM security services, expanding from approximately $3.70 billion in 2023 to an estimated $10.13 billion by 2033, showcasing significant investment in cybersecurity initiatives.
Does ConsaInsights provide customized market report data for the iam Security Services industry?
Yes, ConsaInsights offers customized market report data tailored to specific needs within the IAM security services industry, allowing clients to access targeted insights and actionable data that align with their strategic objectives.
What deliverables can I expect from this iam Security Services market research project?
Deliverables from an IAM security services market research project include an in-depth market analysis report, key trends identification, competitive landscape assessments, along with segmented data insights across various regions and applications.
What are the market trends of iam Security Services?
Current market trends in IAM security services include increased adoption of cloud-based solutions, focusing on user experience and convenience, growing emphasis on identity governance, and the integration of advanced technologies like AI and machine learning for enhanced security.