Information Technology It Security As A Service Market Report
Published Date: 31 January 2026 | Report Code: information-technology-it-security-as-a-service
Information Technology It Security As A Service Market Size, Share, Industry Trends and Forecast to 2033
This report provides a comprehensive analysis of the Information Technology Security as a Service market for the forecast years of 2023 to 2033, detailing market size, trends, and insights across multiple segments and regions.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
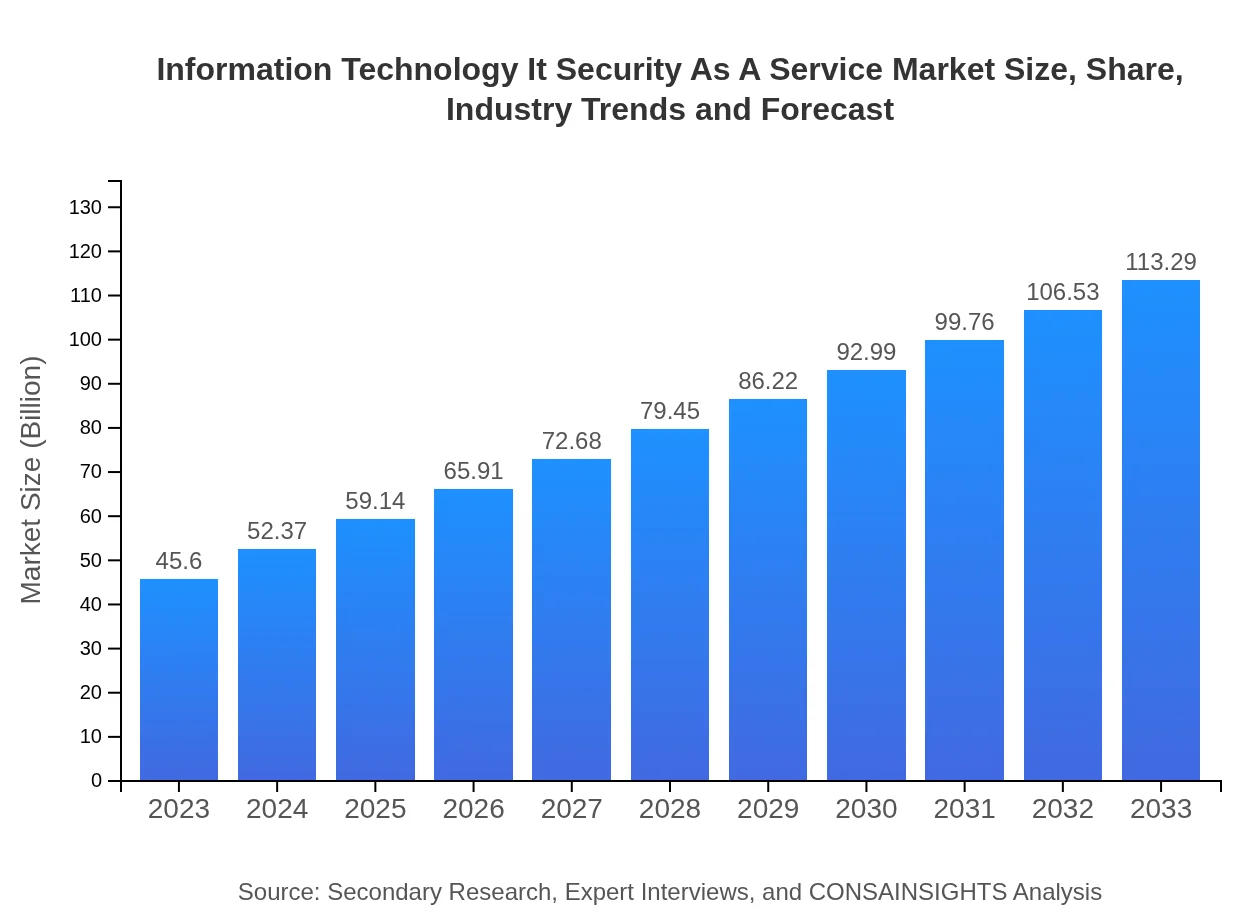
| 2023 Market Size | $45.60 Billion |
| CAGR (2023-2033) | 9.2% |
| 2033 Market Size | $113.29 Billion |
| Top Companies | Cisco Systems, Inc., IBM Corporation, Palo Alto Networks, Check Point Software Technologies Ltd., Fortinet, Inc. |
| Last Modified Date | 31 January 2026 |
Information Technology It Security As A Service Market Overview
Customize Information Technology It Security As A Service Market Report market research report
- ✔ Get in-depth analysis of Information Technology It Security As A Service market size, growth, and forecasts.
- ✔ Understand Information Technology It Security As A Service's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Information Technology It Security As A Service
What is the Market Size & CAGR of Information Technology It Security As A Service market in 2023?
Information Technology It Security As A Service Industry Analysis
Information Technology It Security As A Service Market Segmentation and Scope
Tell us your focus area and get a customized research report.
Information Technology It Security As A Service Market Analysis Report by Region
Europe Information Technology It Security As A Service Market Report:
Europe's market is projected to grow from $13.86 billion in 2023 to $34.43 billion by 2033. Stricter data protection regulations such as GDPR are driving organizations to seek advanced security as a service solutions to mitigate risks and ensure compliance.Asia Pacific Information Technology It Security As A Service Market Report:
In the Asia Pacific region, the Information Technology Security as a Service market is forecasted to grow from $8.86 billion in 2023 to $22.02 billion by 2033, reflecting a growing awareness of cybersecurity threats and regulations. Increased investments in digital transformation by various industries in countries like India and China are driving this growth.North America Information Technology It Security As A Service Market Report:
North America remains one of the largest markets, with the market size expected to grow from $14.91 billion in 2023 to $37.04 billion by 2033. The heightened threat landscape, regulatory pressure, and a strong presence of leading cybersecurity firms contribute to this significant increase.South America Information Technology It Security As A Service Market Report:
The South American market is set to expand from $3.13 billion in 2023 to $7.78 billion by 2033. The increase is mainly fueled by the rising number of cyberattacks and the need for companies to comply with international cybersecurity standards, leading to a higher adoption of managed security services.Middle East & Africa Information Technology It Security As A Service Market Report:
In the Middle East and Africa, the market for Information Technology Security as a Service is expected to rise significantly, growing from $4.84 billion in 2023 to $12.02 billion by 2033. This growth is attributed to increasing cyber threats and greater awareness of cybersecurity across various sectors.Tell us your focus area and get a customized research report.
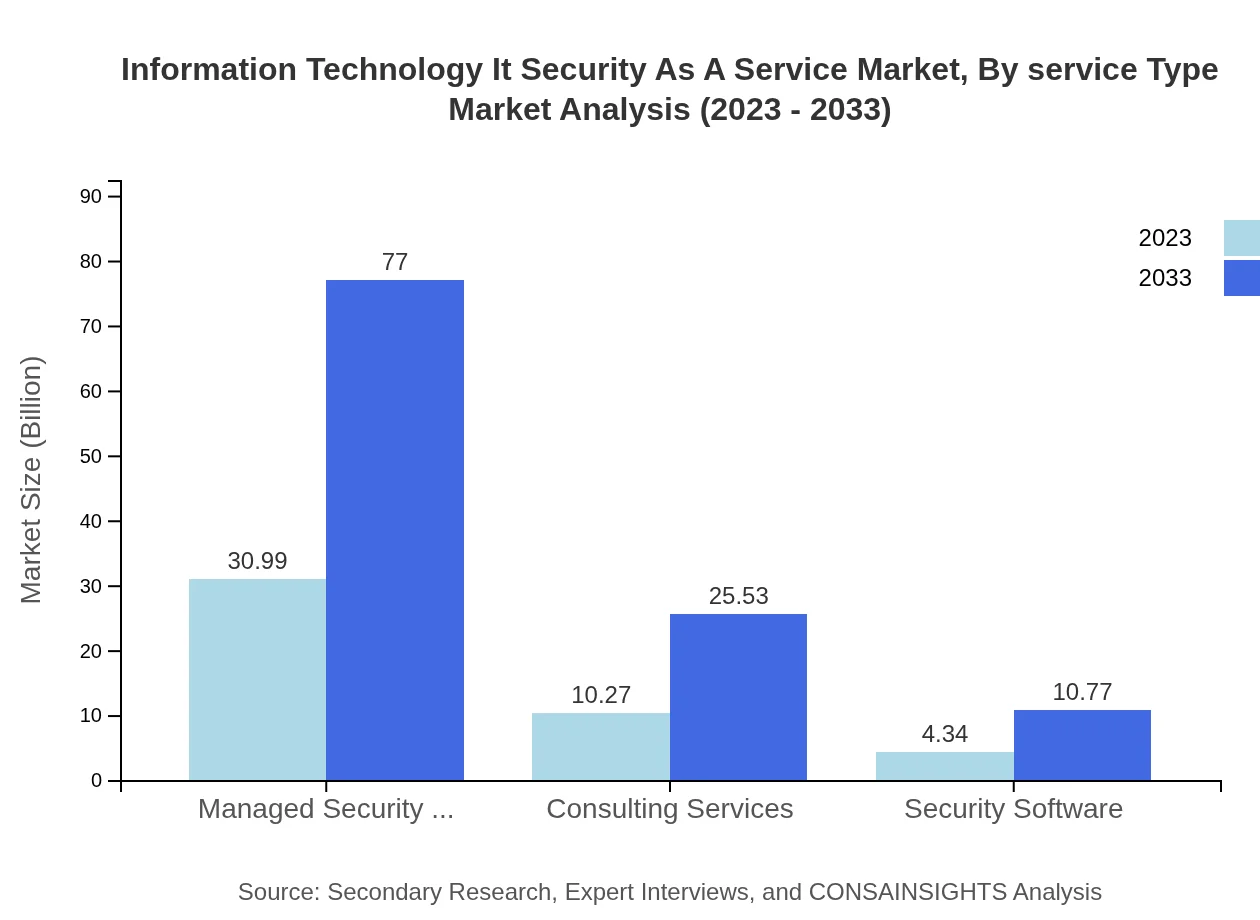
Information Technology It Security As A Service Market Analysis By Service Type
The IT Security as a Service market, categorized by service type, shows that Managed Security Services dominate the market, accounting for a considerable share due to their comprehensive protection offerings. Consulting services also play a significant role, especially in regulatory compliance sectors. Security Software is gaining traction as organizations seek to automate their security measures.
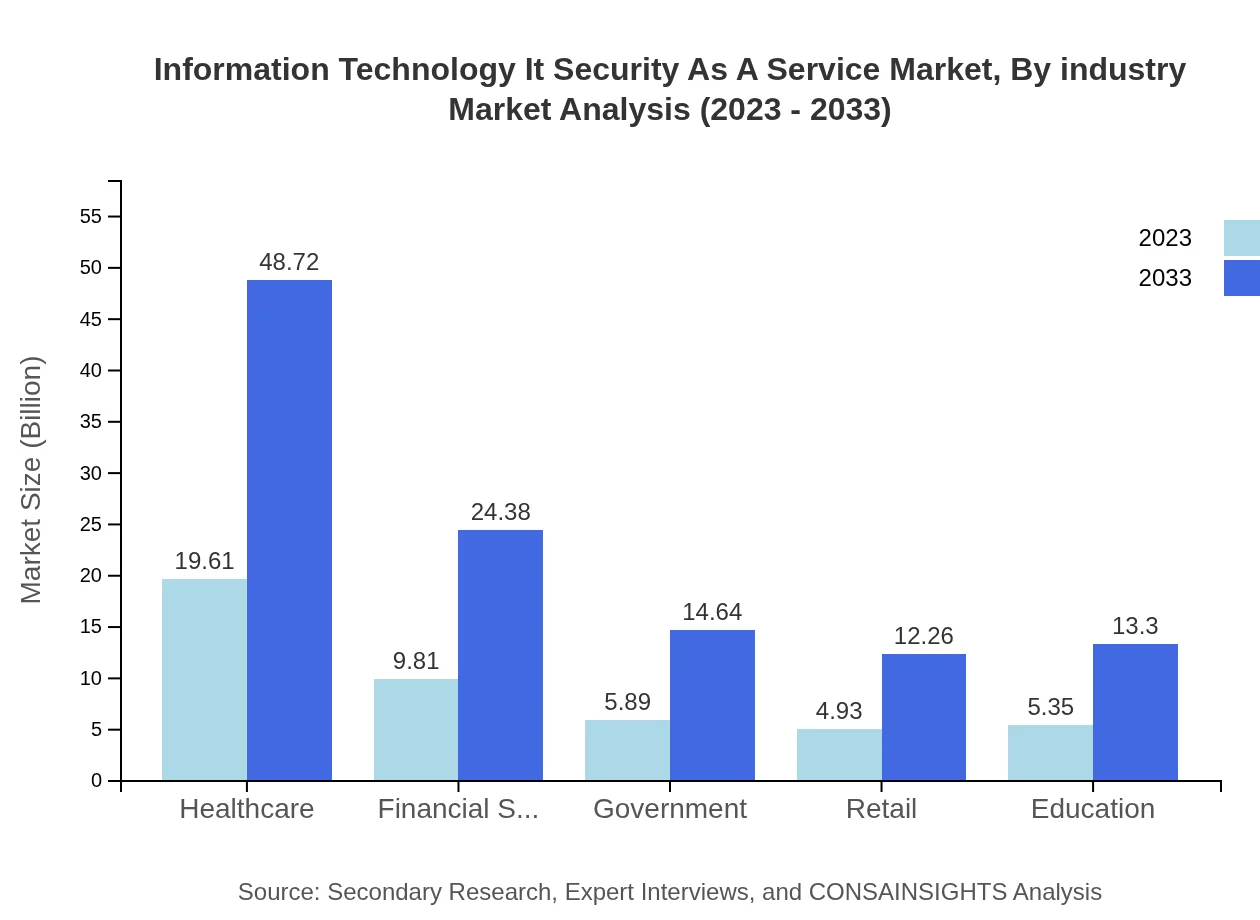
Information Technology It Security As A Service Market Analysis By Industry
In the IT Security as a Service market segmented by industry, the healthcare sector shows one of the largest market shares, driven by stringent regulations like HIPAA. Financial services follow closely, as they handle sensitive data and face constant threats from cybercriminals. Government and education sectors are also significant contributors due to increasing challenges in safeguarding data.
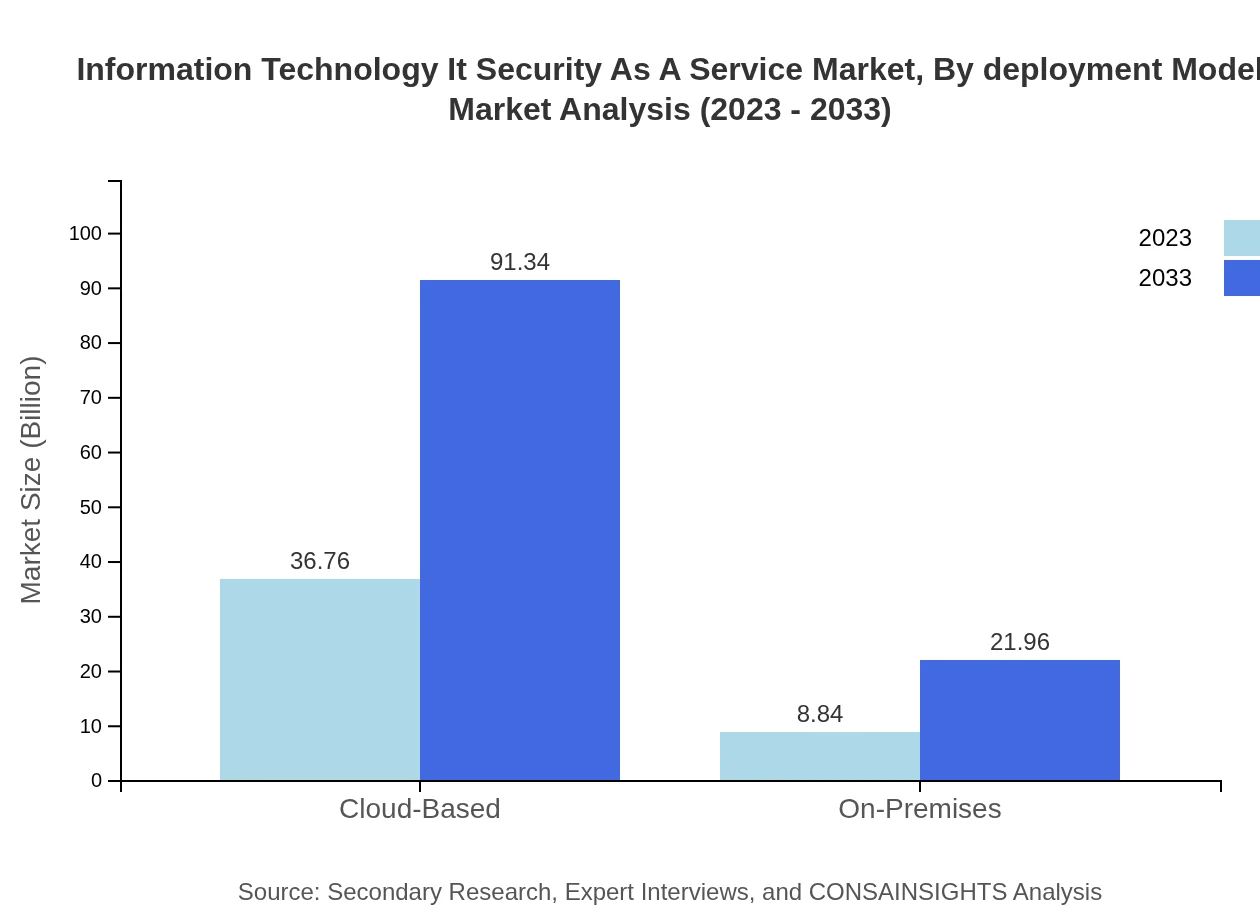
Information Technology It Security As A Service Market Analysis By Deployment Model
The deployment model analysis reveals a substantial preference for cloud-based solutions, capturing 80.62% of the market in 2023. Companies are transitioning to cloud environments for better scalability and cost-effectiveness. In contrast, on-premises solutions are less favored but still necessary for some organizations with specific compliance needs.
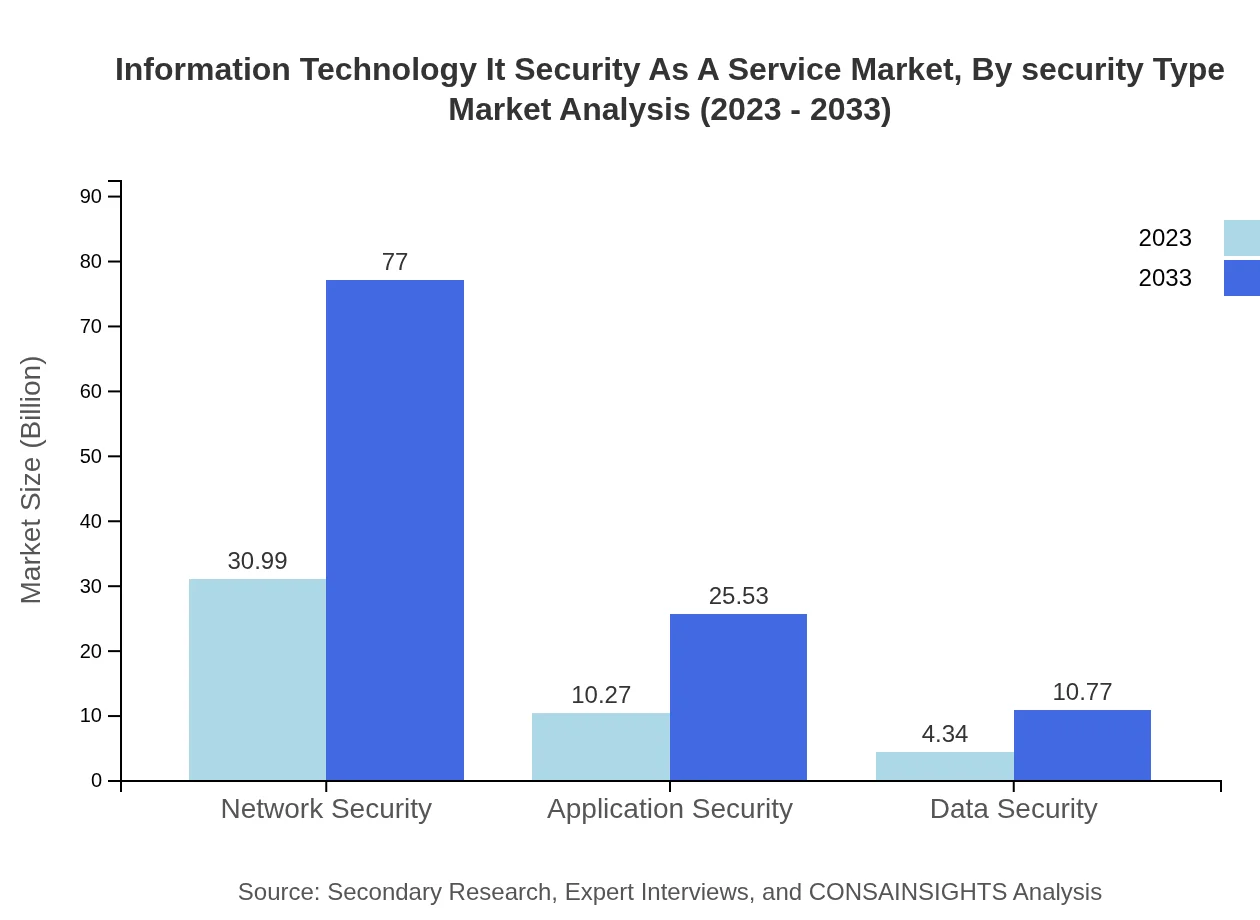
Information Technology It Security As A Service Market Analysis By Security Type
Examining the market through the lens of security types indicates network security as the leading segment, driven by the increasing number of threats. Application security and data security are gaining momentum as businesses strive to protect their applications and sensitive information from breaches.
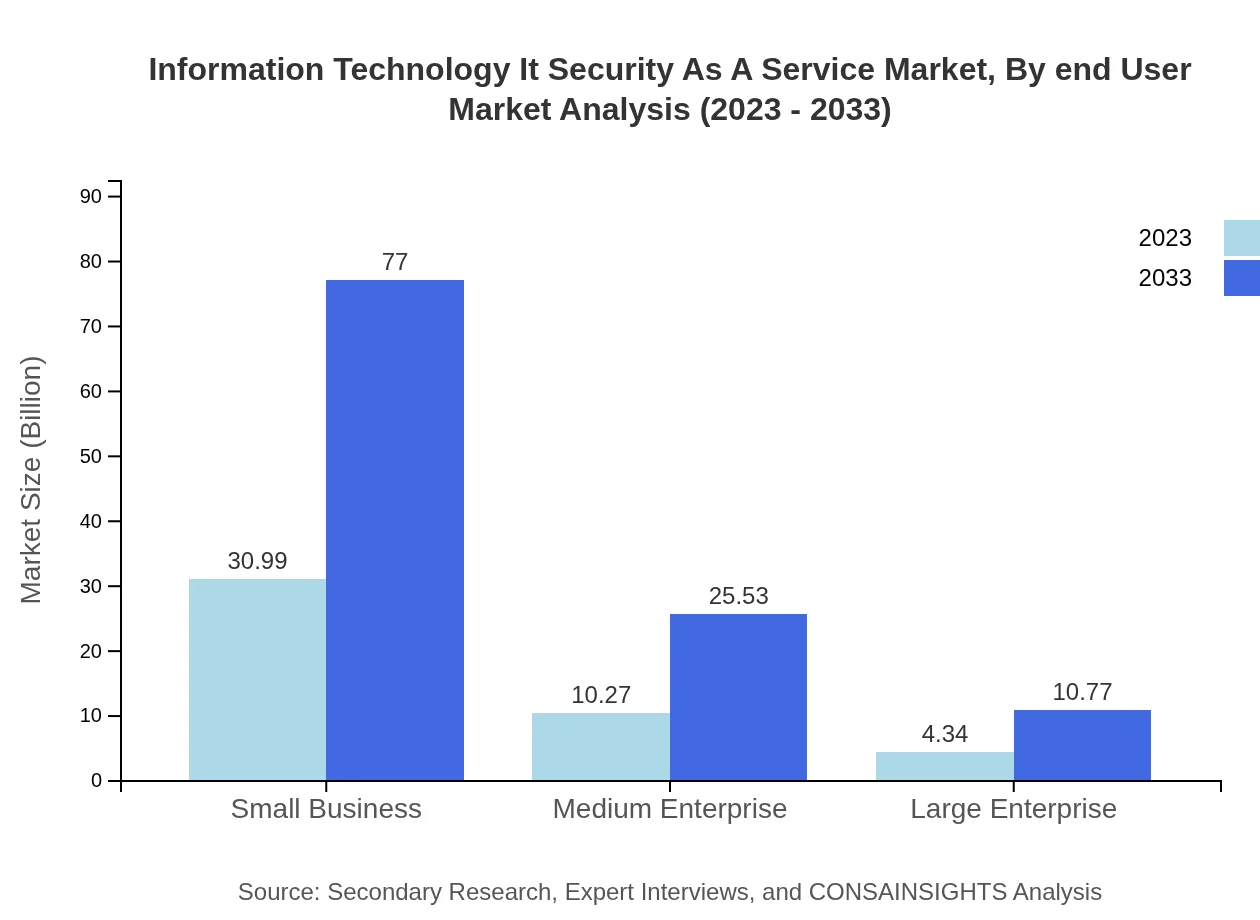
Information Technology It Security As A Service Market Analysis By End User
When assessed by end-user segmentation, small businesses account for a significant share due to their unique vulnerabilities. Medium-sized and large enterprises also contribute meaningfully, with large organizations investing heavily in integrated security solutions due to their complex IT environments.
Information Technology It Security As A Service Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Information Technology It Security As A Service Industry
Cisco Systems, Inc.:
A leader in cybersecurity solutions, Cisco offers various managed security services and software, supporting businesses in protecting their networks.IBM Corporation:
Known for its robust cybersecurity solutions, IBM utilizes advanced technologies to protect organizations from evolving cyber threats.Palo Alto Networks:
Palo Alto Networks specializes in next-generation firewalls and cloud-based security solutions, maintaining a strong emphasis on innovation.Check Point Software Technologies Ltd.:
Check Point provides comprehensive security solutions spanning networks, mobile, cloud, and endpoint security.Fortinet, Inc.:
As a prominent player in network security, Fortinet offers innovative IT security solutions that secure enterprise-level networks.We're grateful to work with incredible clients.









FAQs
What is the market size of information Technology It Security As A Service?
The Information Technology (IT) Security as a Service market is valued at approximately $45.6 billion in 2023. The market is projected to grow at a CAGR of 9.2%, indicating significant growth potential in the upcoming years, reaching a more substantial market size by 2033.
What are the key market players or companies in this information Technology It Security As A Service industry?
Key players in the IT Security as a Service sector include leading technology companies such as IBM, Cisco, McAfee, Palo Alto Networks, and CrowdStrike. These companies leverage advanced cybersecurity technologies to offer robust security solutions and services.
What are the primary factors driving the growth in the information Technology It Security As A Service industry?
Major growth factors include the increasing frequency of cyberattacks, regulatory compliance requirements, and businesses' growing reliance on cloud services. Furthermore, the rising demand for automated security solutions enhances the industry's growth potential.
Which region is the fastest Growing in the information Technology It Security As A Service?
North America is currently the fastest-growing region in the IT Security as a Service market, with a market size of $14.91 billion in 2023, expected to soar to $37.04 billion by 2033, driven by strong investments in cybersecurity.
Does ConsaInsights provide customized market report data for the information Technology It Security As A Service industry?
Yes, ConsaInsights offers customized market report data tailored to the specific needs of clients in the IT Security as a Service industry. This includes insights on market trends, competitive analysis, and forecasts.
What deliverables can I expect from this information Technology It Security As A Service market research project?
Deliverables from the IT Security as a Service market research project typically include comprehensive market reports, data analytics, competitor benchmarking, trend analyses, and strategic recommendations tailored to support informed decision-making.
What are the market trends of information Technology It Security As A Service?
Current trends in the IT Security as a Service industry include the shift towards cloud-based security solutions, growing demand for managed services, increased focus on compliance, and the integration of AI and machine learning for enhanced security capabilities.