Internet Of Things Iot Security Market Report
Published Date: 31 January 2026 | Report Code: internet-of-things-iot-security
Internet Of Things Iot Security Market Size, Share, Industry Trends and Forecast to 2033
This report provides a comprehensive analysis of the IoT Security market, covering market dynamics, regional insights, segmentation, and competitive landscape, with forecasts from 2023 to 2033.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
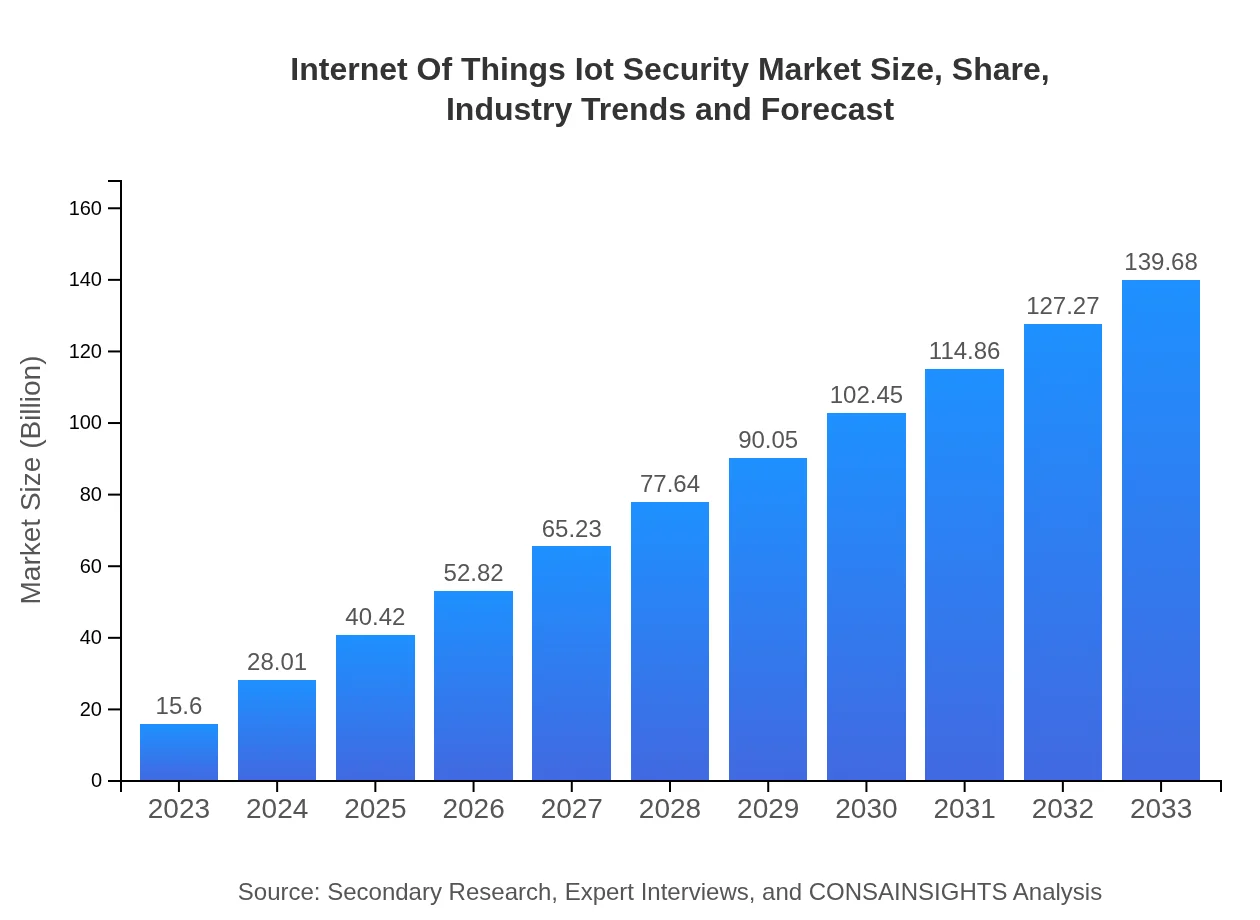
| 2023 Market Size | $15.60 Billion |
| CAGR (2023-2033) | 23% |
| 2033 Market Size | $139.68 Billion |
| Top Companies | Cisco Systems, Inc., IBM Corporation, Microsoft Corporation, Palo Alto Networks, Inc., Symantec Corporation |
| Last Modified Date | 31 January 2026 |
Internet Of Things Iot Security Market Overview
Customize Internet Of Things Iot Security Market Report market research report
- ✔ Get in-depth analysis of Internet Of Things Iot Security market size, growth, and forecasts.
- ✔ Understand Internet Of Things Iot Security's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Internet Of Things Iot Security
What is the Market Size & CAGR of Internet Of Things Iot Security market in 2033?
Internet Of Things Iot Security Industry Analysis
Internet Of Things Iot Security Market Segmentation and Scope
Tell us your focus area and get a customized research report.
Internet Of Things Iot Security Market Analysis Report by Region
Europe Internet Of Things Iot Security Market Report:
The European IoT Security market is projected to expand from $5.56 billion in 2023 to a significant $49.82 billion by 2033. The region's emphasis on strong data protection regulations like GDPR and a mature infrastructure for IoT systems intensify demand for security solutions.Asia Pacific Internet Of Things Iot Security Market Report:
In 2023, the Asia Pacific IoT Security market is valued at $2.69 billion and is expected to soar to $24.05 billion by 2033. Rapid digital transformation, growing IoT adoption, and increased cyber threat awareness are driving this growth. Key markets such as China, Japan, and India lead in implementing IoT solutions in sectors like healthcare and automotive, thus boosting security investments.North America Internet Of Things Iot Security Market Report:
North America leads the IoT Security market with a valuation of $5.05 billion in 2023, anticipated to grow to $45.19 billion by 2033. The region's advanced technological landscape, compliance regulations, and high cyber threat landscape underscore the vast investment in IoT security solutions.South America Internet Of Things Iot Security Market Report:
Latin America's IoT Security market stands at $1.34 billion in 2023, projected to reach $12.00 billion by 2033. The growing infrastructure development and digital initiatives encourage security measures in IoT implementations, particularly in smart agriculture and transportation.Middle East & Africa Internet Of Things Iot Security Market Report:
The Middle East and Africa IoT Security market is valued at $0.96 billion in 2023 and is expected to reach $8.62 billion by 2033. Growing initiatives toward digital transformation and smart city projects fuel investments in security, particularly in UAE and South Africa.Tell us your focus area and get a customized research report.
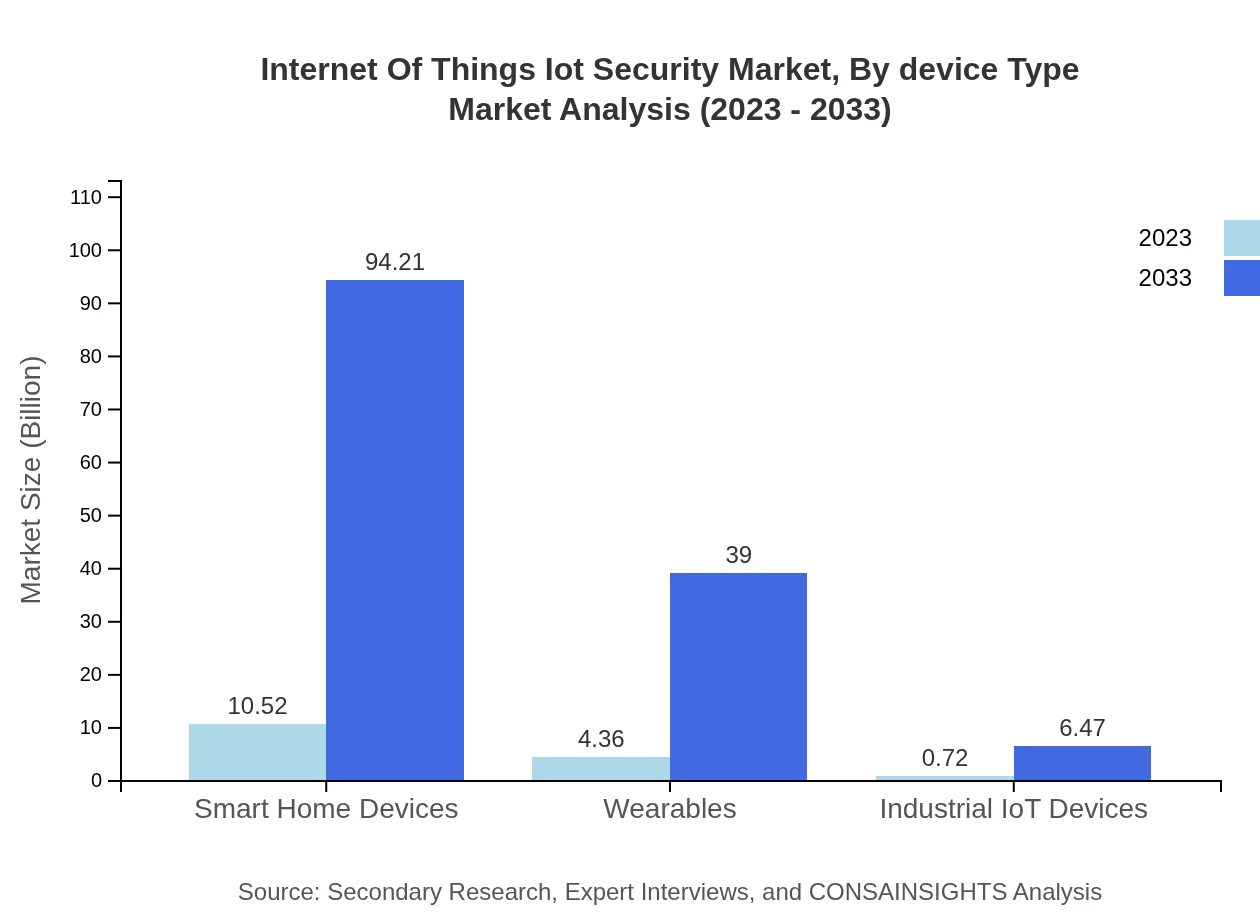
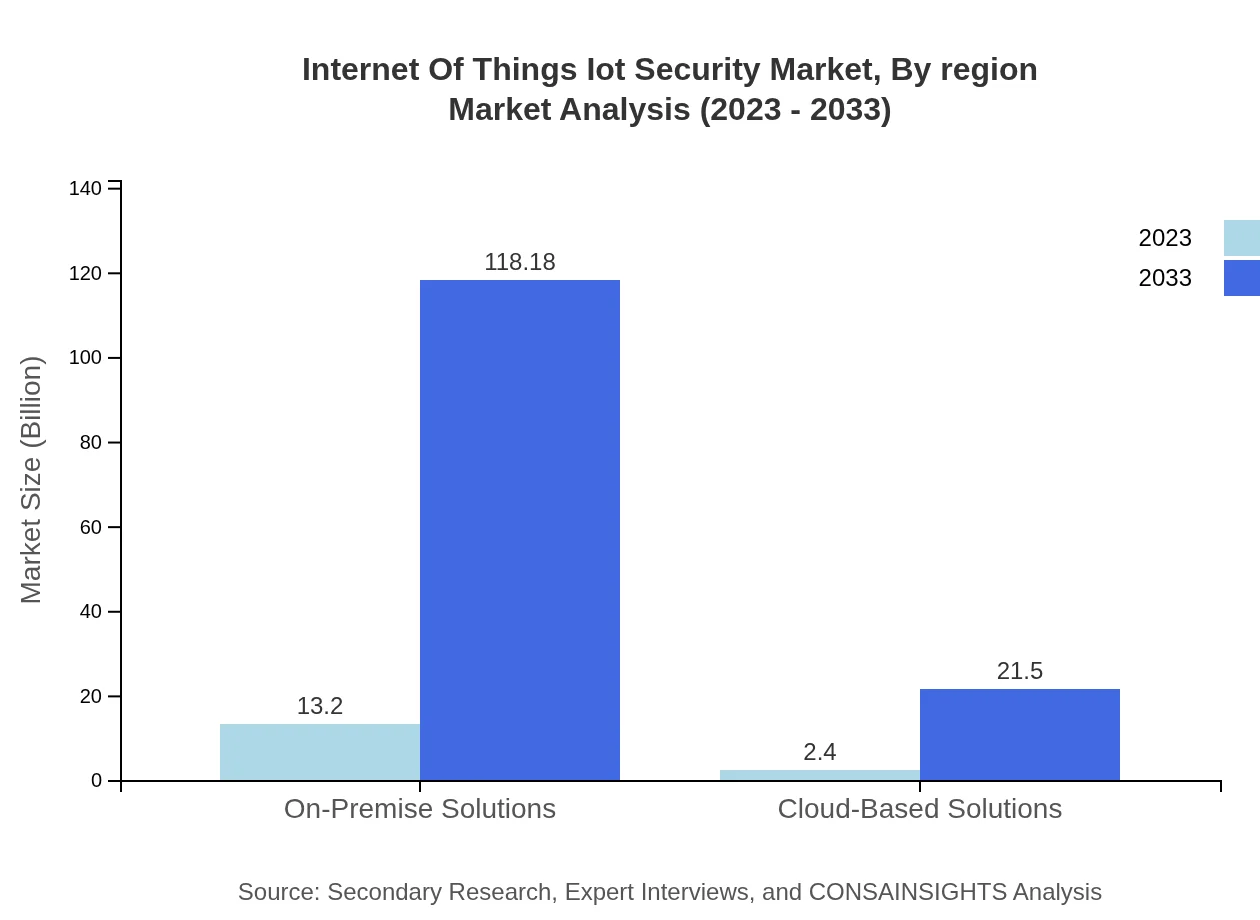
Internet Of Things Iot Security Market Analysis By Device Type
The market segmented by device type reveals strong growth for Managed Services, expected to grow from $13.20 billion in 2023 to $118.18 billion by 2033, accounting for 84.61% market share. Cloud-Based Solutions follow with significant growth from $2.40 billion to $21.50 billion. Smart Home Devices represent a considerable focus with shares of 67.45%, while On-Premise offerings also maintain noteworthy traction within business environments.
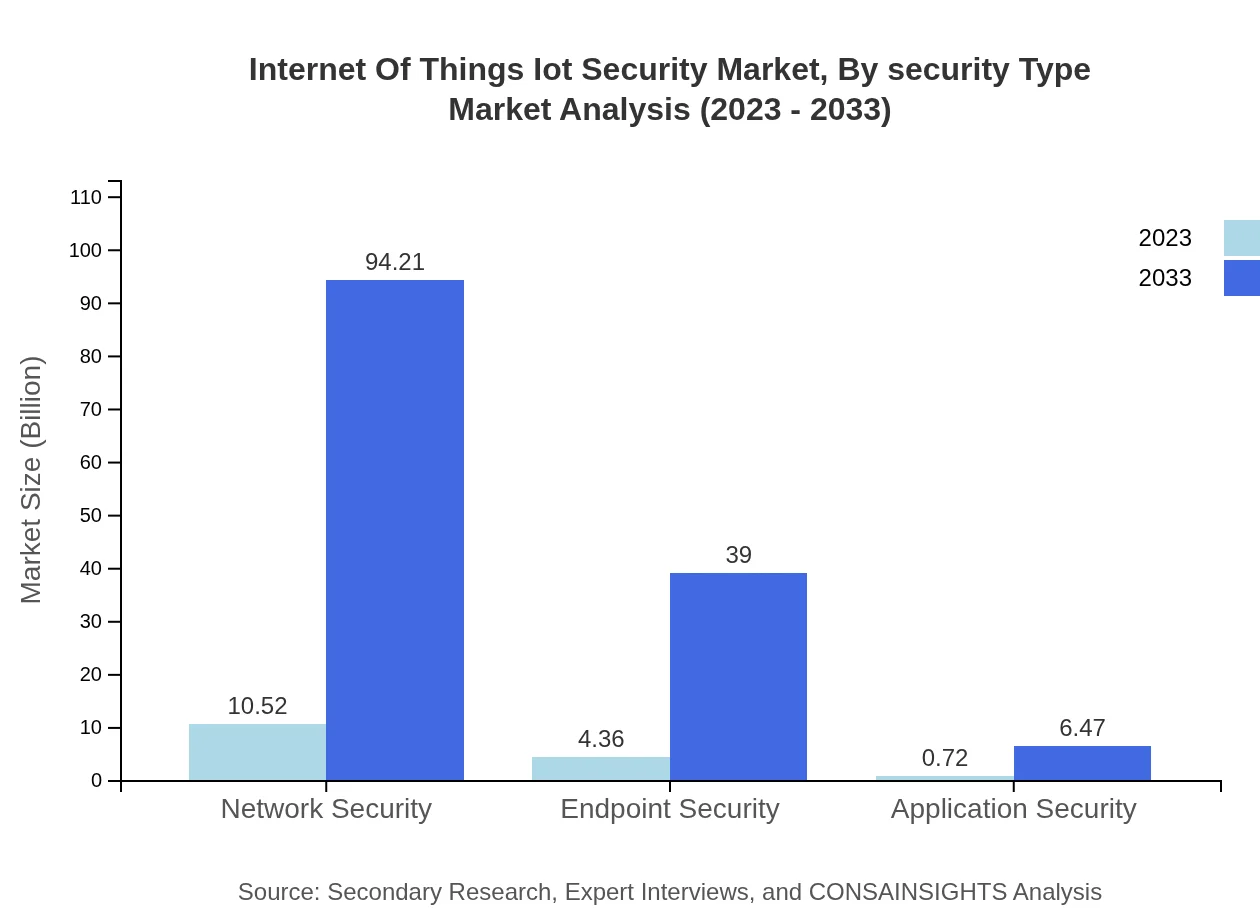
Internet Of Things Iot Security Market Analysis By Security Type
Endpoint Security currently stands at $4.36 billion in 2023, projected to escalate to $39.00 billion by 2033 with a consistent share of 27.92%. Network Security reinforces its position, moving from $10.52 billion to $94.21 billion while maintaining a 67.45% market share. Application Security, although smaller in size, grows to $6.47 billion significantly, addressing niche markets.
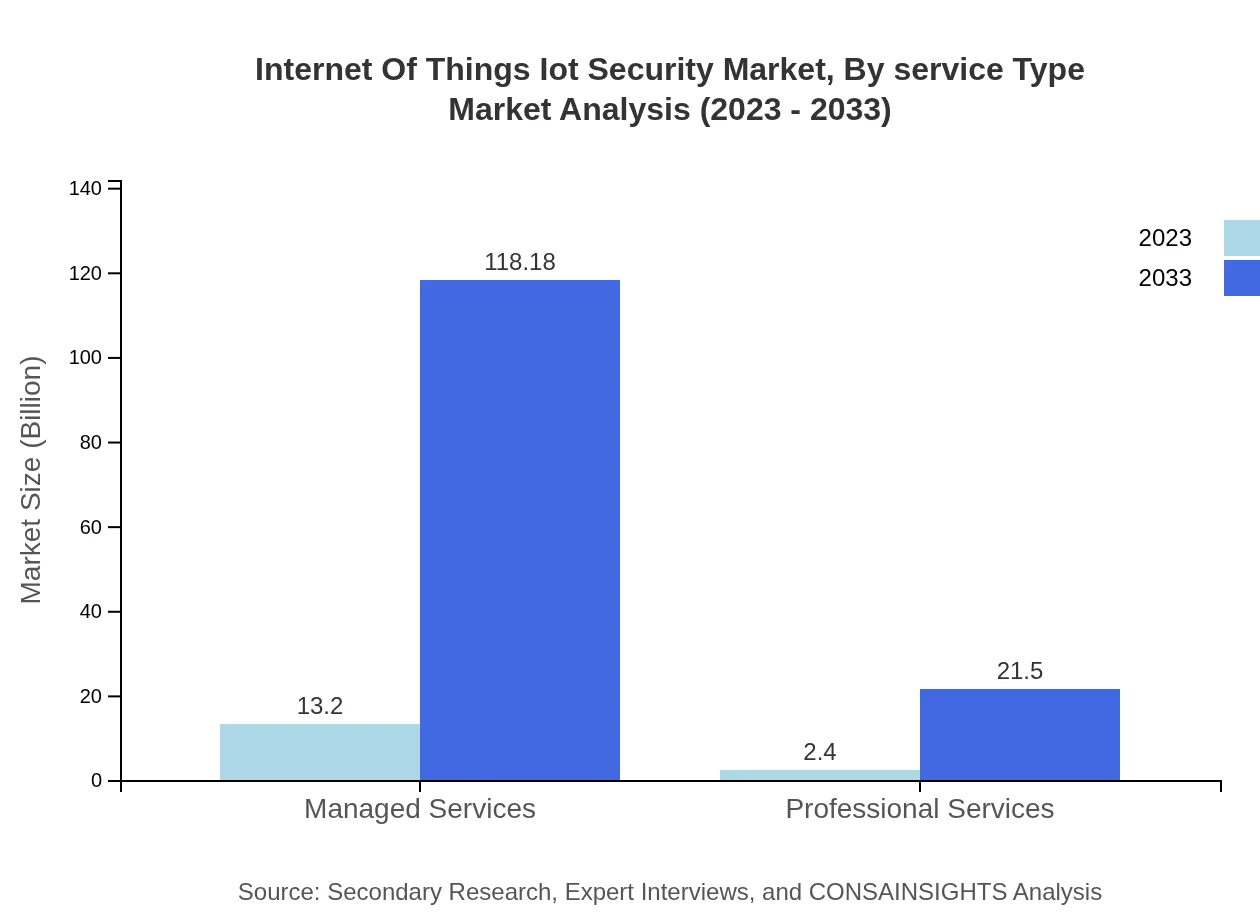
Internet Of Things Iot Security Market Analysis By Service Type
Managed Services dominate the share with $13.20 billion in 2023, growing to $118.18 billion and retaining 84.61% share. Professional Services show considerable growth from $2.40 billion in 2023 to $21.50 billion, supporting organizations in implementing robust security measures.
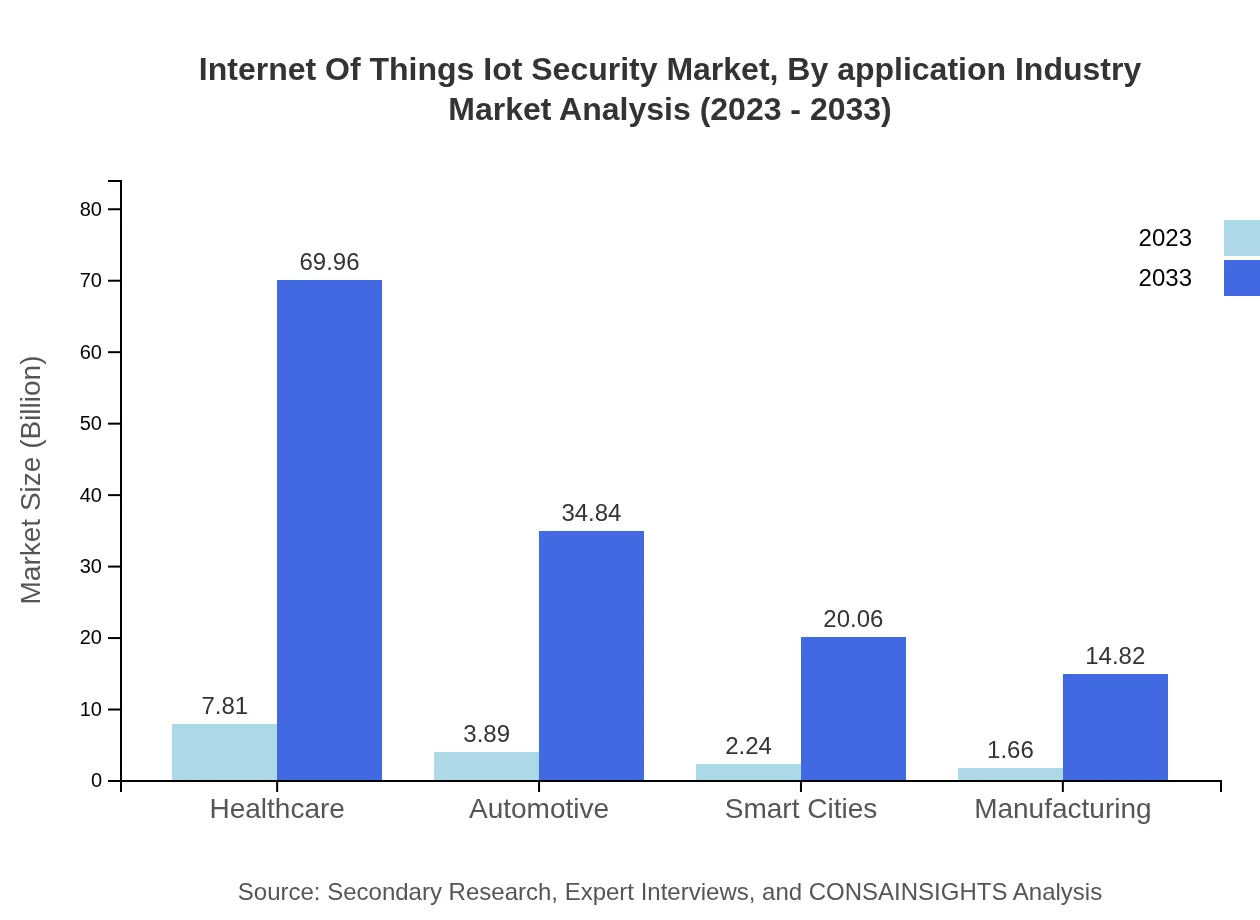
Internet Of Things Iot Security Market Analysis By Application Industry
Healthcare leads with a market size of $7.81 billion in 2023, expanding to $69.96 billion by 2033, due to increasing regulations and adoption of IoT in patient care. Automotive and Smart Cities also showcase significant growth, reflecting the rise in connected devices within urban infrastructures.
Internet Of Things Iot Security Market Analysis By Region
The market persists in enhancing security across various regions and industries. Each has discerning needs and expectations for IoT device security tailored to specific applications. The prominence of industry regulations, data protection, and emerging digital transformation initiatives emphasize the need for robust IoT security in all deployments.
Internet Of Things Iot Security Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Internet Of Things Iot Security Industry
Cisco Systems, Inc.:
Cisco is a leading player in networking and cybersecurity solutions, substantially investing in IoT security with innovative products catering to the evolving landscape of connected devices.IBM Corporation:
IBM specializes in advanced security solutions, leveraging AI and analytics to provide real-time risk assessments and automated responses against IoT vulnerabilities.Microsoft Corporation:
Microsoft offers robust cloud-based IoT security solutions integrated into its Azure platform, allowing clients to secure their IoT deployments effectively from potential threats.Palo Alto Networks, Inc.:
Palo Alto Networks focuses on next-generation security measures, providing comprehensive protection against various threats amidst the rapid proliferation of IoT devices.Symantec Corporation:
Symantec is an established leader in cybersecurity services, delivering enterprise-grade solutions for securing IoT applications and networks.We're grateful to work with incredible clients.









FAQs
What is the market size of Internet of Things (IoT) Security?
The Internet of Things (IoT) Security market is projected to reach approximately $15.6 billion by 2033, exhibiting a robust CAGR of 23%. This growth reflects the increasing necessity for enhanced security measures in interconnected devices.
What are the key market players or companies in the IoT Security industry?
Key players in the IoT Security industry include major technology firms providing comprehensive security solutions. They focus on device security, network protection, and innovative security protocols tailored to IoT architecture.
What are the primary factors driving the growth in the IoT Security industry?
The growth in the IoT Security industry is driven by factors such as the proliferation of connected devices, the rise in cyber threats, regulatory compliance needs, and increasing consumer awareness regarding data privacy and security.
Which region is the fastest Growing in the IoT Security market?
The fastest-growing region in the IoT Security market is Europe, with a market size projected to grow from $5.56 billion in 2023 to $49.82 billion by 2033 due to heightened security regulations and consumer demand for safer IoT technologies.
Does ConsInsights provide customized market report data for the IoT Security industry?
Yes, ConsInsights offers customized market report data tailored to the specific needs of clients in the IoT Security industry, enabling businesses to gain insights that align with their unique strategic goals.
What deliverables can I expect from this IoT Security market research project?
Deliverables from the IoT Security market research project include comprehensive reports, market forecasts, competitive analysis, consumer insights, and trends that inform strategic decision-making.
What are the market trends of IoT Security?
Significant market trends in IoT Security include the growing adoption of cloud-based solutions, increased focus on network security, and advancements in endpoint protection to address emerging vulnerabilities in connected devices.