Iot Iam Market Report
Published Date: 31 January 2026 | Report Code: iot-iam
Iot Iam Market Size, Share, Industry Trends and Forecast to 2033
This report provides an in-depth analysis of the IoT Identity and Access Management (IAM) market from 2023 to 2033, highlighting market size, trends, technology impacts, and forecasts across different regions and segments.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
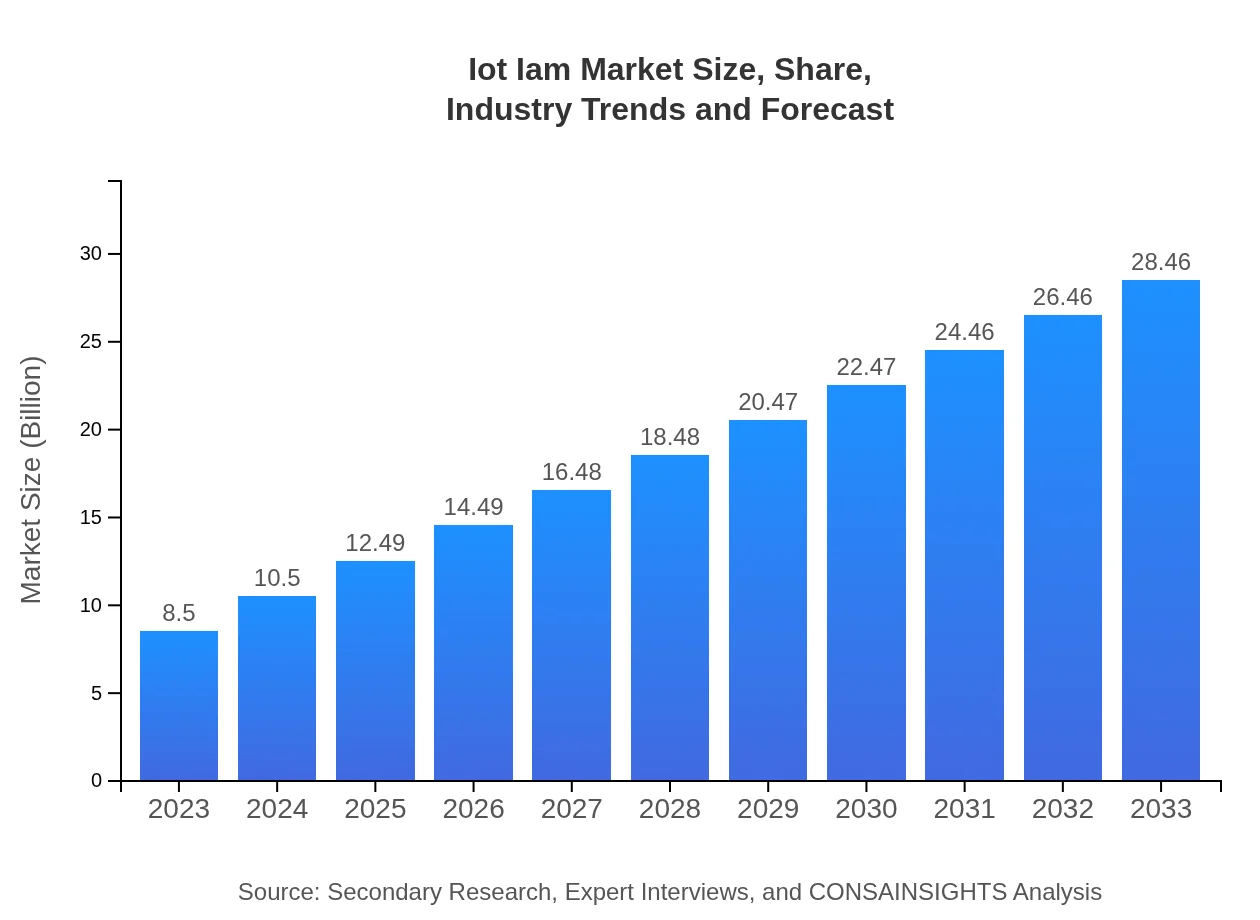
| 2023 Market Size | $8.50 Billion |
| CAGR (2023-2033) | 12.3% |
| 2033 Market Size | $28.46 Billion |
| Top Companies | Okta, Microsoft, IBM, Amazon Web Services, Cisco |
| Last Modified Date | 31 January 2026 |
IoT IAM Market Overview
Customize Iot Iam Market Report market research report
- ✔ Get in-depth analysis of Iot Iam market size, growth, and forecasts.
- ✔ Understand Iot Iam's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Iot Iam
What is the Market Size & CAGR of IoT IAM market in 2023?
IoT IAM Industry Analysis
IoT IAM Market Segmentation and Scope
Tell us your focus area and get a customized research report.
IoT IAM Market Analysis Report by Region
Europe Iot Iam Market Report:
In Europe, the IoT IAM market is valued at $2.24 billion in 2023 and is anticipated to grow to $7.50 billion by 2033, achieving a CAGR of 12.9%. Stringent data protection regulations such as GDPR are compelling enterprises to adopt IAM solutions.Asia Pacific Iot Iam Market Report:
In the Asia-Pacific region, the market is estimated to be $1.67 billion in 2023 and is projected to reach $5.57 billion by 2033, growing at a CAGR of 13.2%. Factors contributing to this growth include increased IoT penetration and government initiatives promoting smart technologies.North America Iot Iam Market Report:
North America holds the largest share of the IoT IAM market, starting at $3.17 billion in 2023 and projected to grow to $10.60 billion by 2033, translating to a CAGR of 12.3%. The leading role of technology firms and high awareness of cyber security are significant factors in this growth.South America Iot Iam Market Report:
The South American market is expected to expand from $0.51 billion in 2023 to $1.71 billion by 2033, at a CAGR of 13.0%. The rise in mobile device usage and investment in IoT infrastructure is driving demand for IAM solutions.Middle East & Africa Iot Iam Market Report:
The Middle East and Africa region is set to grow from $0.92 billion in 2023 to $3.07 billion by 2033, with a CAGR of 12.4%. The rise in smart city initiatives and increased investment in digital transformation are catalysts for this market growth.Tell us your focus area and get a customized research report.
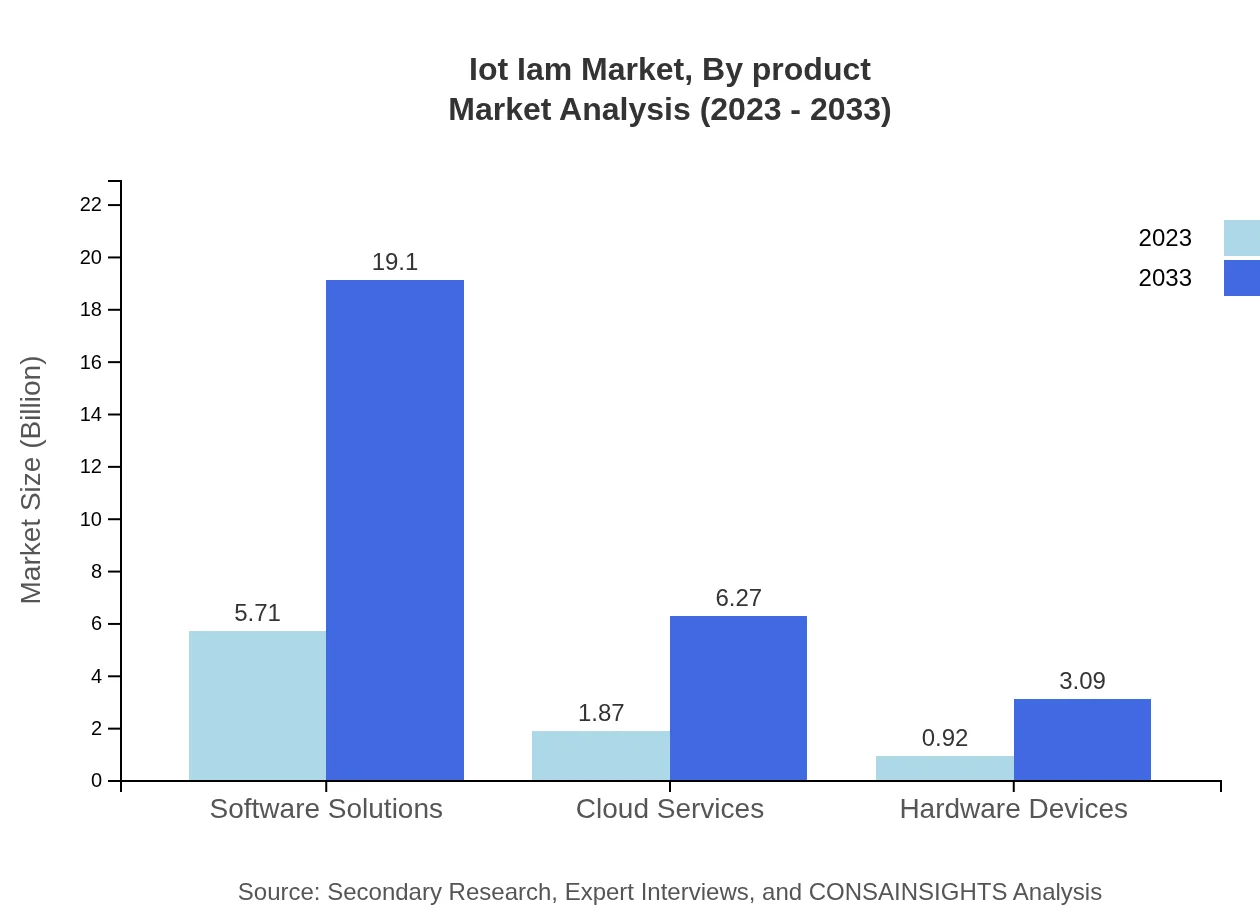
Iot Iam Market Analysis By Product
The IoT IAM market, categorized by product types, comprises Software Solutions, Cloud Services, and Hardware Devices. Software Solutions dominate the market with a projected size of $5.71 billion in 2023, expected to grow to $19.10 billion by 2033, showcasing a significant market share of 67.12% over the forecast period. Cloud Services are anticipated to expand from $1.87 billion to $6.27 billion, maintaining a 22.03% share. Hardware Devices, although smaller at $0.92 billion growing to $3.09 billion, contribute to the market's diverse needs.
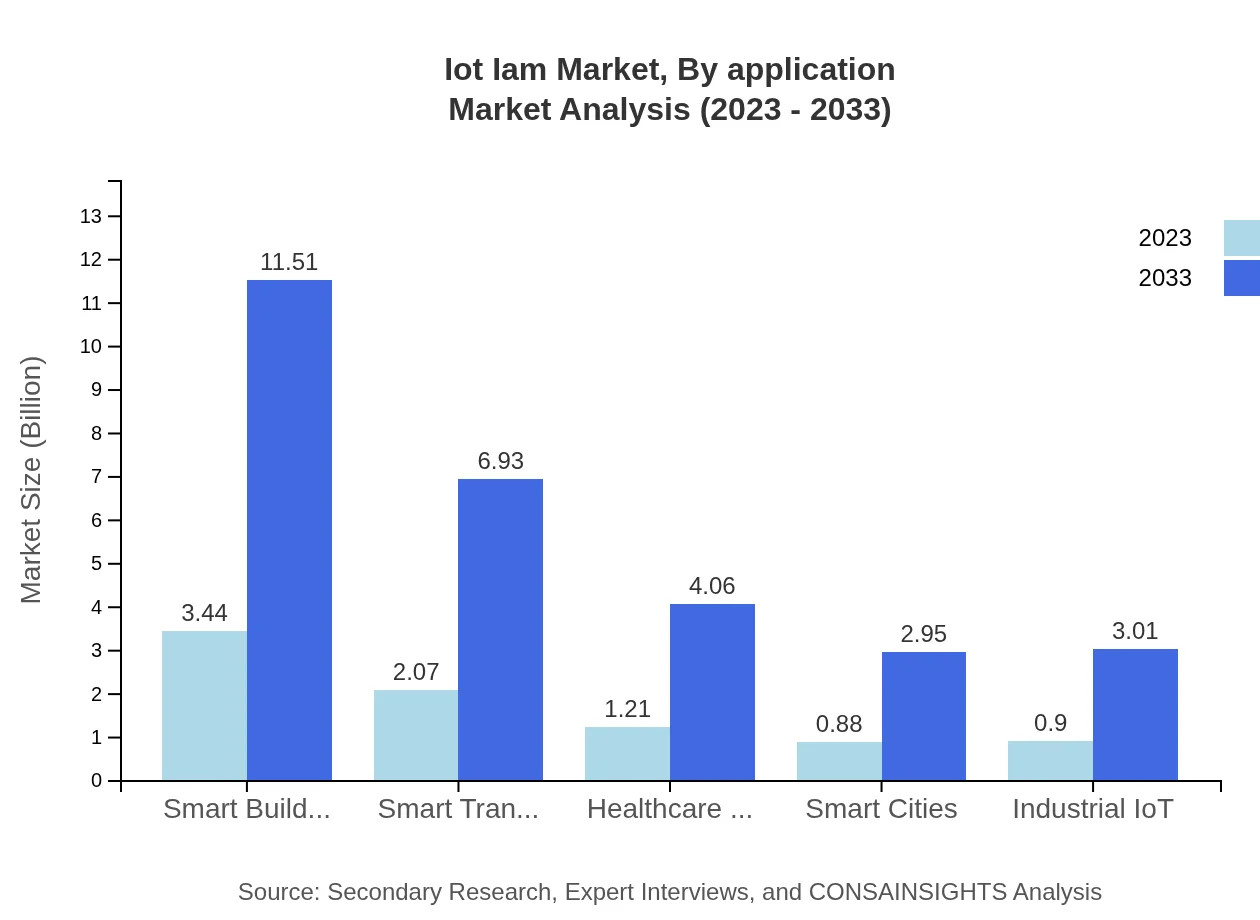
Iot Iam Market Analysis By Application
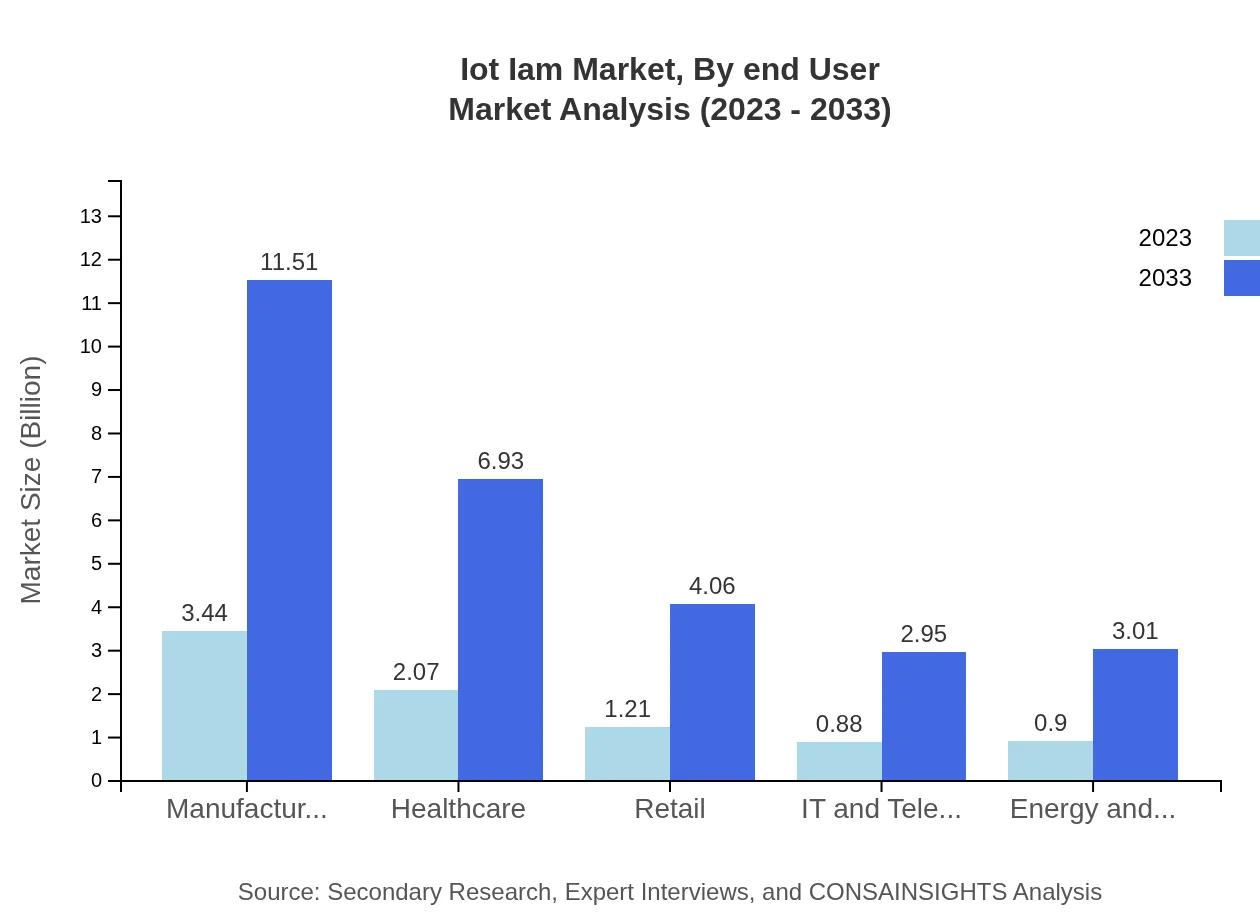
Different applications of IoT IAM include healthcare, manufacturing, retail, and smart cities. The manufacturing segment is the largest, estimated to be $3.44 billion in 2023 and likely reaching $11.51 billion by 2033, representing a 40.44% market share. Followed by healthcare at $2.07 billion growing to $6.93 billion, and retail from $1.21 billion to $4.06 billion, all showcasing the critical need for effective IAM solutions across varied applications.
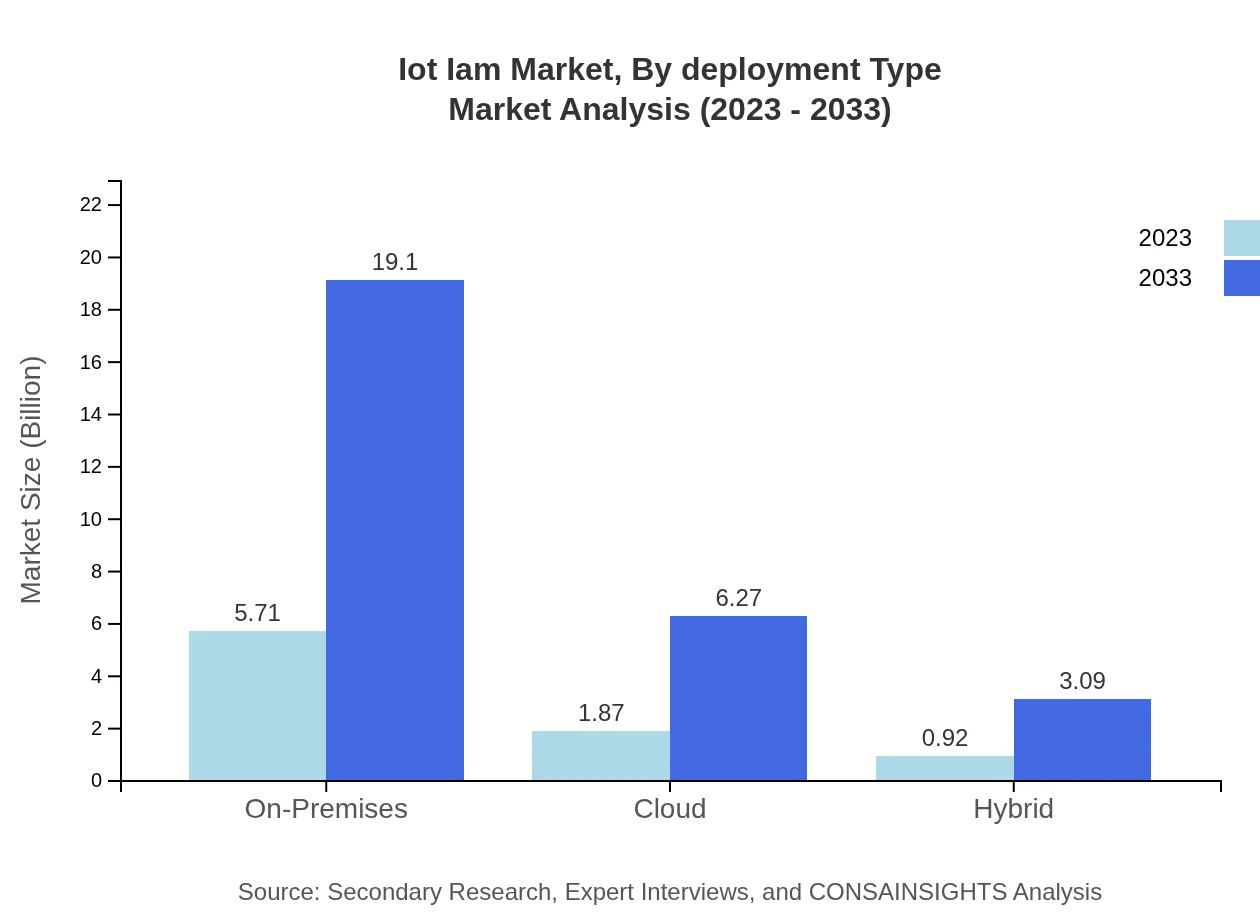
Iot Iam Market Analysis By Deployment Type
The deployment landscape includes On-Premises, Cloud, and Hybrid models. On-Premises solutions lead the market, starting at $5.71 billion in 2023 and expected to grow to $19.10 billion by 2033. Cloud deployment also shows strong growth, from $1.87 billion to $6.27 billion, while Hybrid remains a smaller segment, expanding from $0.92 billion to $3.09 billion, catering to organizations with flexible needs.
Iot Iam Market Analysis By End User
End-user industries for IoT IAM include finance, healthcare, manufacturing, and IT & Telecom. The finance industry is poised for growth as it seeks advanced IAM solutions to protect sensitive financial data. Healthcare follows closely, emphasizing the necessity for secure data management while complying with regulations.
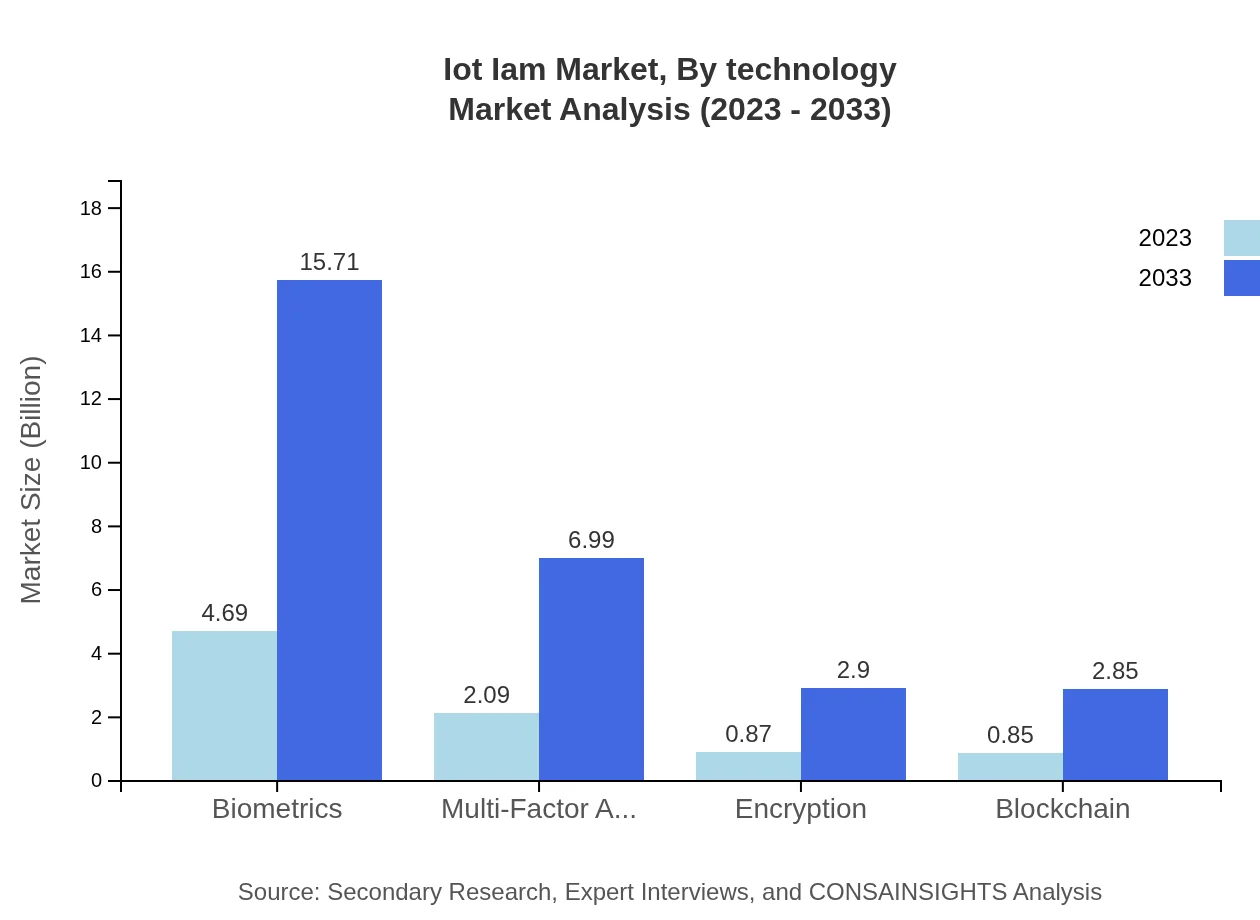
Iot Iam Market Analysis By Technology
Technological advancements driving the IoT IAM market include biometrics, multi-factor authentication (MFA), encryption, and blockchain solutions. Biometrics led the market at $4.69 billion in 2023, projected to reach $15.71 billion by 2033. MFA and encryption solutions also demonstrate notable growth, meeting increasing security demands efficiently.
IoT IAM Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in IoT IAM Industry
Okta:
Leader in identity and access management solutions, known for its robust cloud IAM solution that integrates seamlessly with numerous IoT platforms.Microsoft:
A key player with Azure's IAM capabilities, providing comprehensive solutions that address security needs in IoT ecosystems.IBM:
Offers Watson IoT with integrated IAM features that enhance security for device management and connectivity.Amazon Web Services:
Provides scalable IAM solutions that support the rapid expansion of IoT across industries, with access control integrated into its cloud services.Cisco:
A pioneer in networking security, Cisco provides IAM solutions that ensure secure device interactions in IoT networks.We're grateful to work with incredible clients.









FAQs
What is the market size of iot Iam?
The IoT IAM market is projected to reach $8.5 billion by 2033, growing at a CAGR of 12.3%. In 2023, the market size stands at $8.5 billion, indicating substantial growth potential through the next decade.
What are the key market players or companies in this iot Iam industry?
Key players in the IoT IAM industry include leading technology companies and cybersecurity firms that specialize in identity management solutions, which offer software and integrated security related to IoT devices. Their strategies shape competitive dynamics.
What are the primary factors driving the growth in the iot Iam industry?
Factors driving growth in the IoT IAM industry include increasing IoT device adoption, rising cybersecurity threats, regulatory compliance needs, and the need for improved access control and user authentication mechanisms in connected environments.
Which region is the fastest Growing in the iot Iam?
Asia Pacific is the fastest-growing region in the IoT IAM market, projected to grow from $1.67 billion in 2023 to $5.57 billion by 2033. In comparison, North America is also significant, expanding from $3.17 to $10.60 billion.
Does ConsaInsights provide customized market report data for the iot Iam industry?
Yes, ConsaInsights offers customized market report data tailored to specific client needs within the IoT IAM industry. This includes detailed analysis, forecasting, segment insights, and regional specifics to aid strategic decision-making.
What deliverables can I expect from this iot Iam market research project?
Deliverables from the IoT IAM market research project typically include comprehensive market analysis, trend reports, segmentation data, growth forecasts, and strategic recommendations to enhance business planning and market entry strategies.
What are the market trends of iot Iam?
Market trends in the IoT IAM sector include a shift toward cloud-based solutions, increased adoption of multi-factor authentication, and growth in software solutions. Biometrics and AI-driven security measures are also becoming prevalent.