Iot Security Market Report
Published Date: 31 January 2026 | Report Code: iot-security
Iot Security Market Size, Share, Industry Trends and Forecast to 2033
This report provides an in-depth analysis of the IoT Security market from 2023 to 2033, highlighting market size, trends, regional insights, segmentation, and forecasts. Key industry players and technological advancements are also discussed, offering valuable insights for stakeholders.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
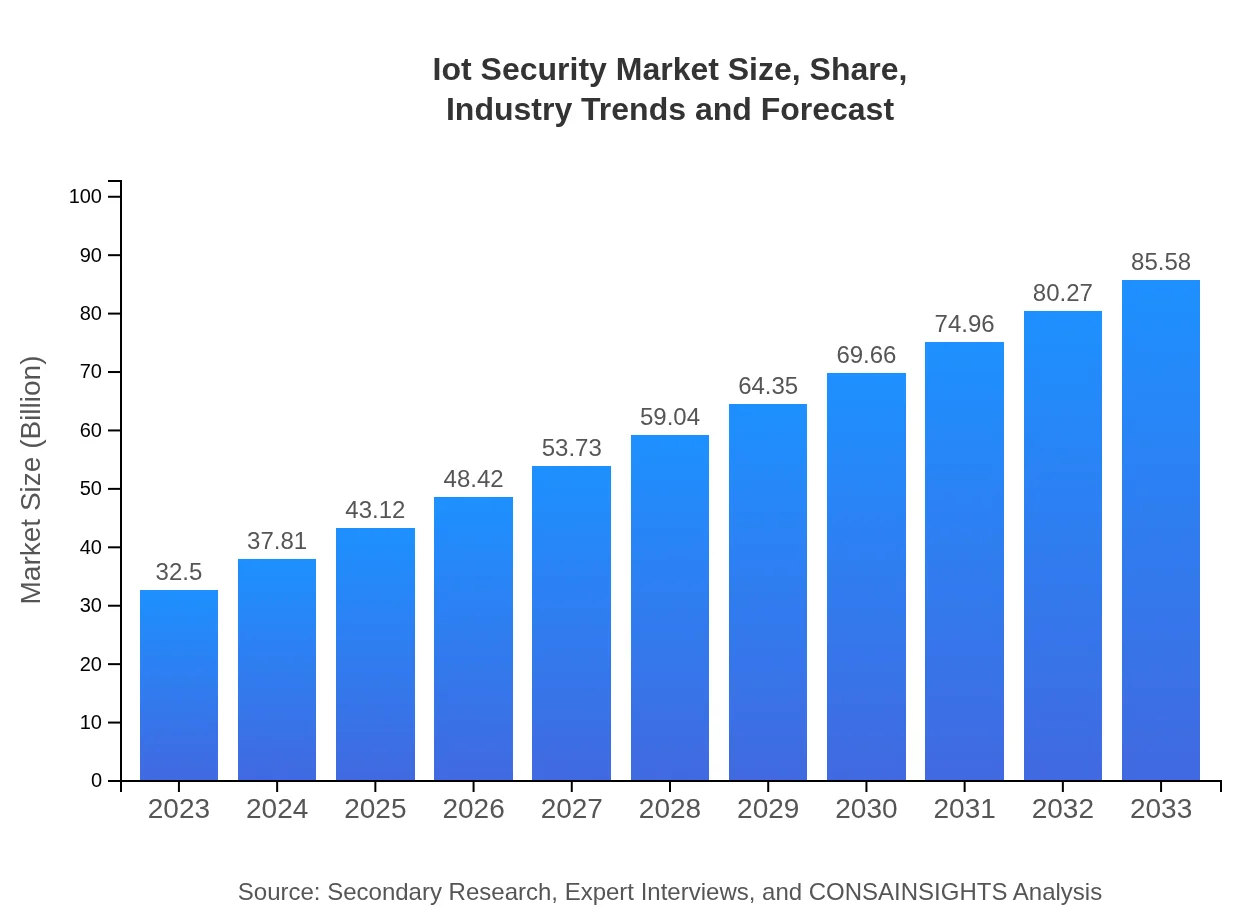
| 2023 Market Size | $32.50 Billion |
| CAGR (2023-2033) | 9.8% |
| 2033 Market Size | $85.58 Billion |
| Top Companies | Cisco Systems Inc., IBM Corporation, McAfee LLC, Symantec Corporation, Fortinet, Inc. |
| Last Modified Date | 31 January 2026 |
IoT Security Market Overview
Customize Iot Security Market Report market research report
- ✔ Get in-depth analysis of Iot Security market size, growth, and forecasts.
- ✔ Understand Iot Security's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Iot Security
What is the Market Size & CAGR of IoT Security market in 2023?
IoT Security Industry Analysis
IoT Security Market Segmentation and Scope
Tell us your focus area and get a customized research report.
IoT Security Market Analysis Report by Region
Europe Iot Security Market Report:
In 2023, Europe's IoT Security market stands at $11.59 billion and is expected to grow to $30.53 billion by 2033. Factors such as stringent data protection regulations (GDPR) and growing implementation of smart technologies underscore significant market growth. The region emphasizes strong governmental support for cybersecurity initiatives.Asia Pacific Iot Security Market Report:
In 2023, the IoT Security market in the Asia Pacific region is valued at $5.50 billion, projected to grow to $14.49 billion by 2033. The rapid adoption of IoT technologies, especially in nations like China and India, bolstered by government initiatives and growing technological infrastructure, drives this growth. However, challenges regarding cybersecurity awareness and fragmented regulations may pose obstacles.North America Iot Security Market Report:
North America leads the IoT Security market with a valuation of $10.97 billion in 2023, projected to grow to $28.89 billion by 2033. This growth is driven by a robust demand for advanced security solutions in industries such as finance, healthcare, and critical infrastructure, alongside a strong regulatory framework.South America Iot Security Market Report:
The IoT Security market in South America is valued at $2.85 billion in 2023 and is expected to reach $7.51 billion by 2033. The region is witnessing gradual adoption of IoT solutions across agriculture and smart cities, despite facing challenges like budget constraints and technological disparities among countries.Middle East & Africa Iot Security Market Report:
The Middle East and Africa market for IoT Security is projected to rise from $1.58 billion in 2023 to $4.16 billion by 2033. The growth is supported by increased digital transformation efforts, especially in the UAE and Saudi Arabia, although there are concerns regarding the availability of skilled cybersecurity professionals.Tell us your focus area and get a customized research report.
Iot Security Market Analysis By Product Type
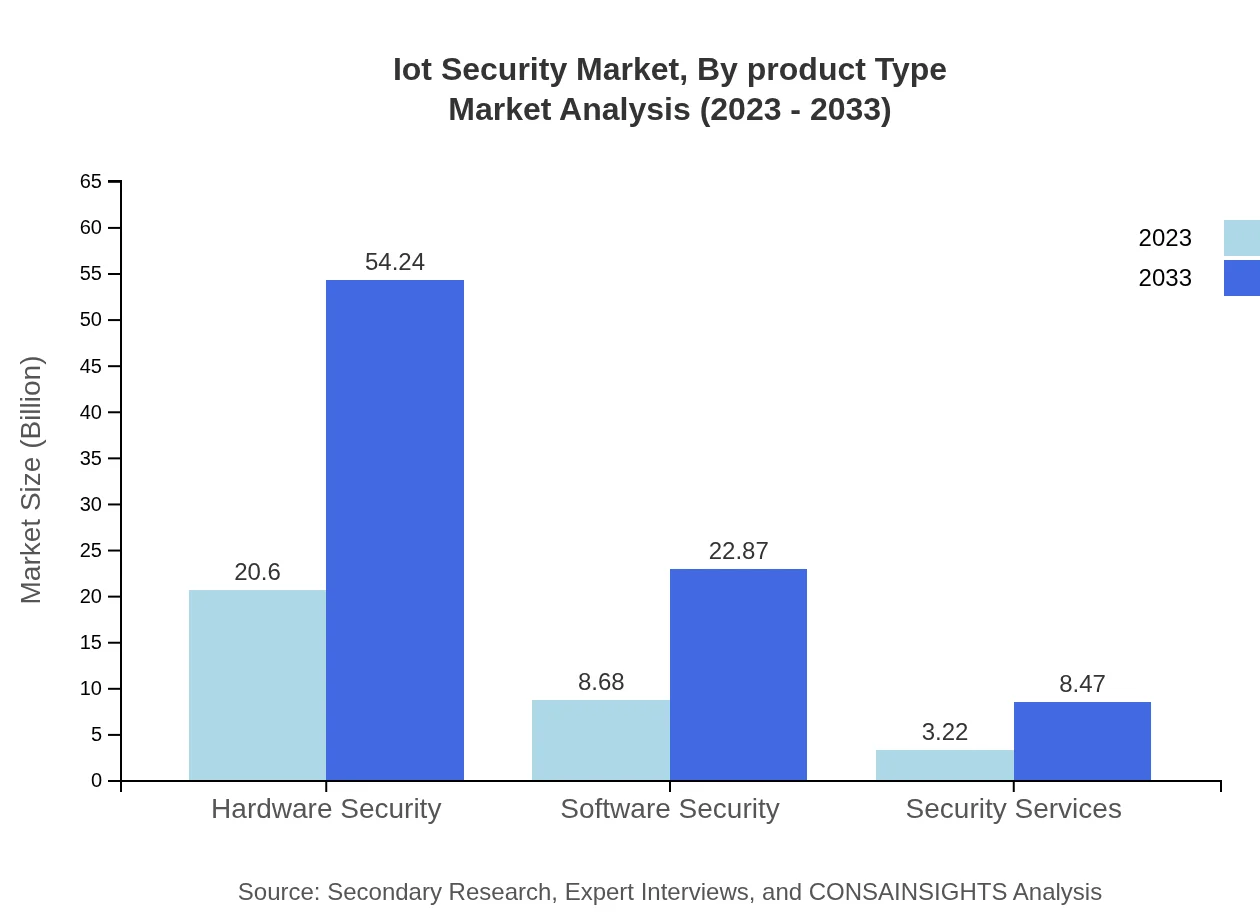
The IoT Security market is segmented by product type into Hardware Security, Software Security, and Security Services. Hardware security is projected to dominate the market with a substantial market share estimated at 63.38% in 2023 and 63.38% in 2033, highlighting its foundational importance in protecting devices. Software security, with a current share of 26.72%, and security services at 9.9%, also contribute significantly to the overall market.
Iot Security Market Analysis By Application
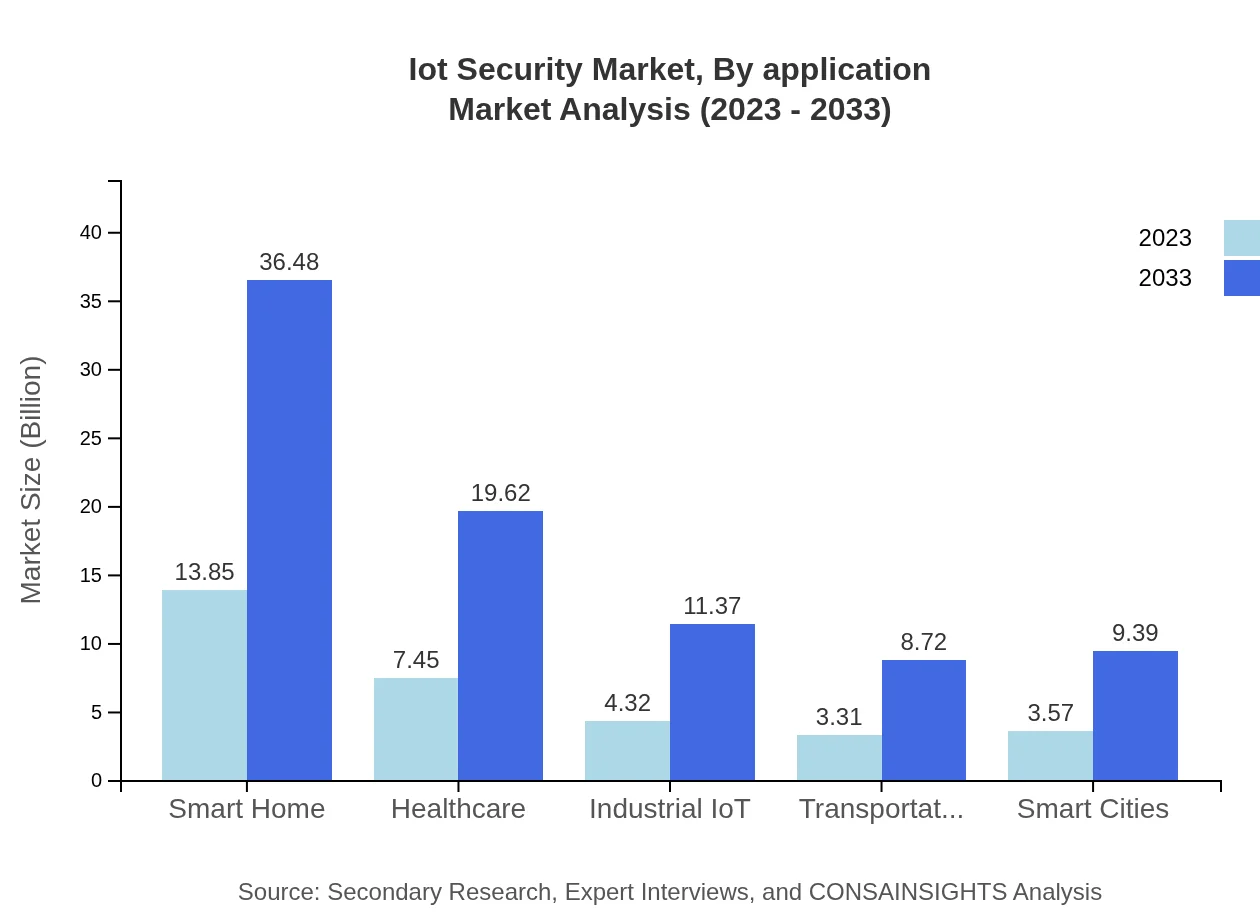
The market is segmented by application into categories like Smart Home, Healthcare, and Industrial IoT. The Smart Home segment shares the largest market size of 13.85 billion in 2023 and will grow to 36.48 billion by 2033. Healthcare is also a critical application area, with market sizes of $7.45 billion in 2023 and projected growth to $19.62 billion by 2033.
Iot Security Market Analysis By Deployment Mode
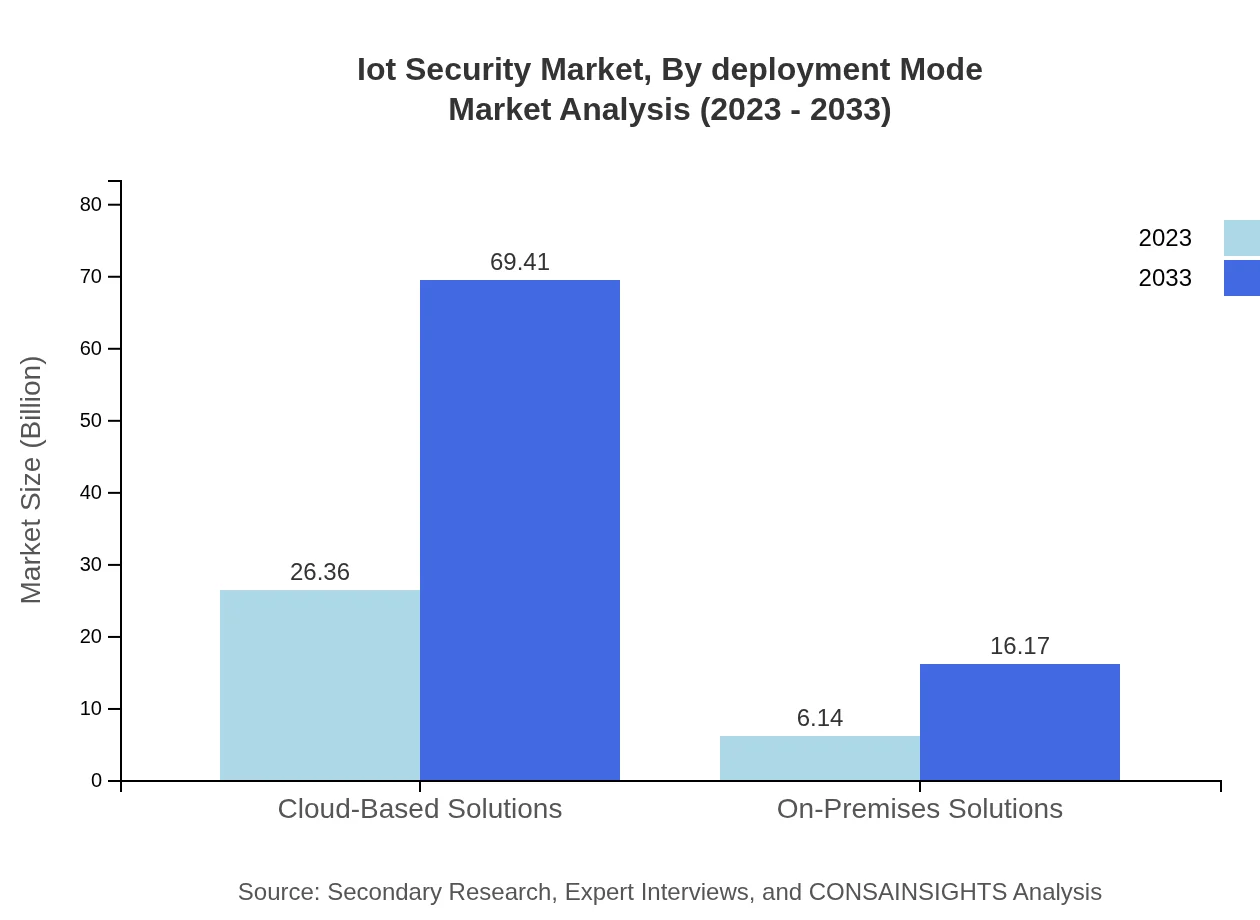
Within IoT Security, deployment modes are crucial and are divided into Cloud-Based Solutions and On-Premises Solutions. Cloud-based solutions have a significant market size of $26.36 billion in 2023, expected to increase to $69.41 billion in 2033, accounting for 81.1% market share. On-premises solutions, although smaller, are also seeing growth with a current market size of $6.14 billion and expected growth to $16.17 billion.
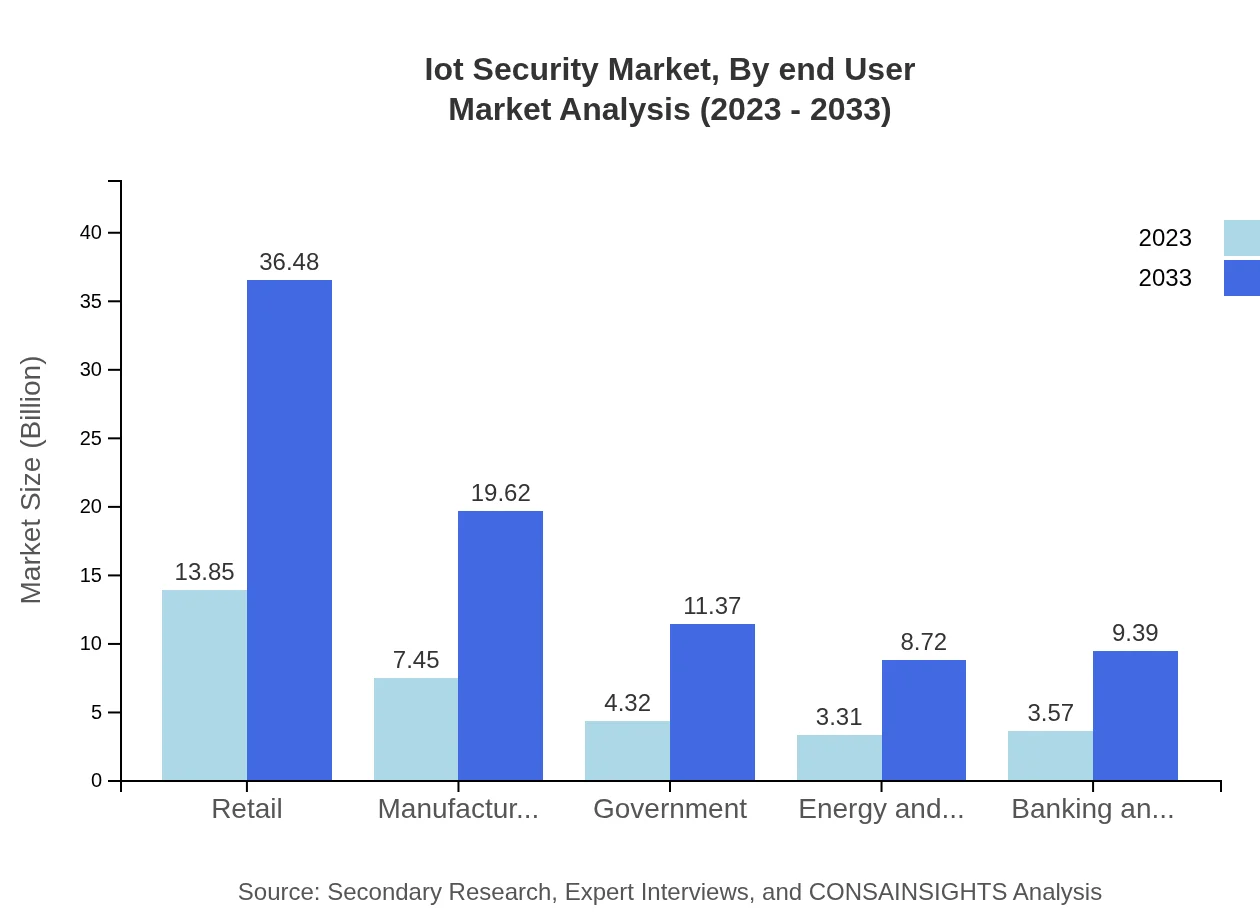
Iot Security Market Analysis By End User
The IoT Security market is segmented into end-users such as Government, Retail, and Banking & Finance. The Retail sector leads the market with an initial size of 13.85 billion in 2023 and growing to 36.48 billion by 2033. The financial sector also shows strong potential with growth projected from $3.57 billion in 2023 to $9.39 billion by 2033.
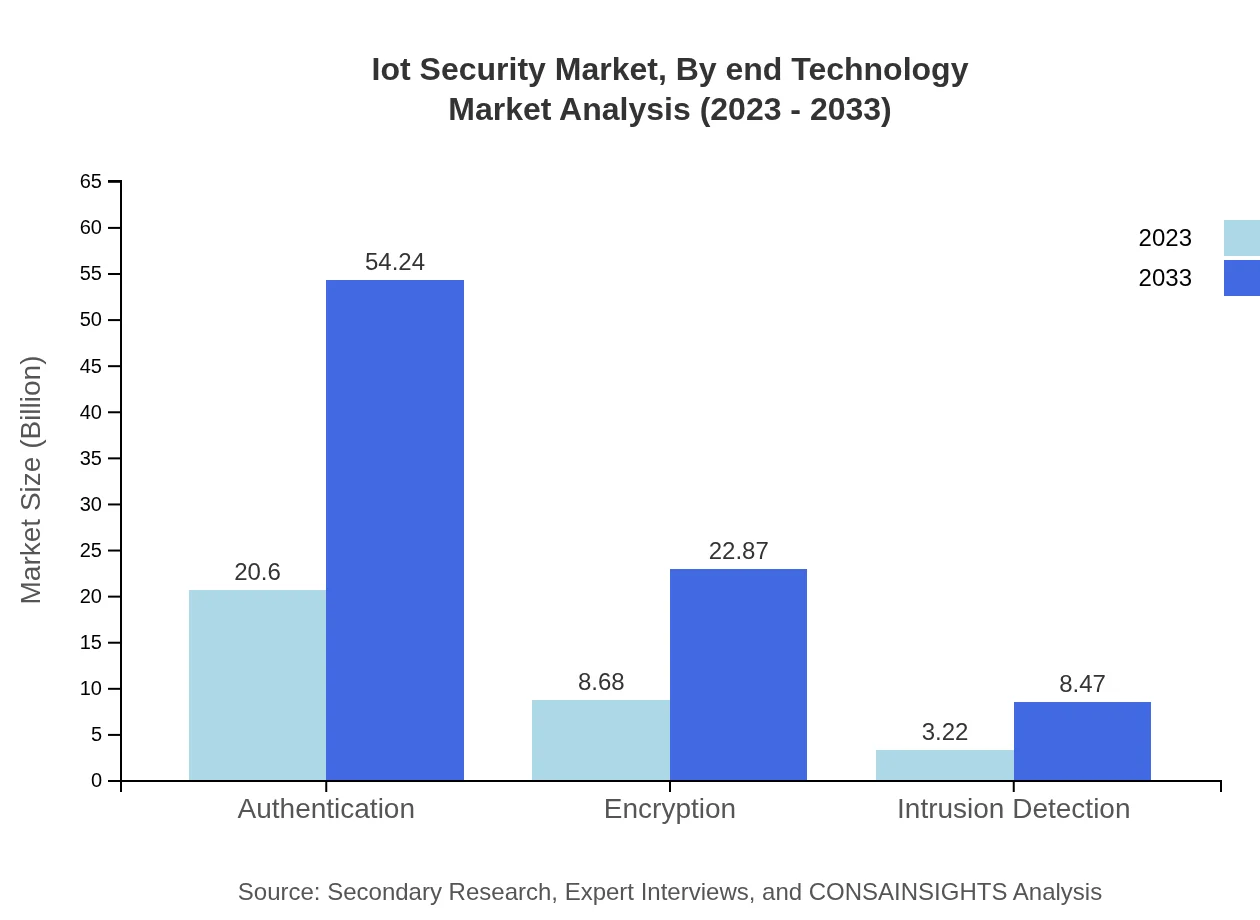
Iot Security Market Analysis By End Technology
Segmentation by technology focuses on Authentication, Encryption, and Intrusion Detection. Authentication technologies dominate the market, valued at $20.60 billion in 2023 and expected to reach $54.24 billion by 2033. Encryption solutions also show growth from $8.68 billion to $22.87 billion during the same period.
IoT Security Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in IoT Security Industry
Cisco Systems Inc.:
Cisco provides an extensive portfolio of IoT security solutions, focusing on networking hardware and software that ensures secure connections across various IoT devices.IBM Corporation:
IBM offers AI-driven IoT security services, helping businesses protect their IoT assets through advanced analytics and security management solutions.McAfee LLC:
McAfee specializes in cybersecurity for IoT devices, providing comprehensive protection against emerging cyber threats tailored to consumer and enterprise markets.Symantec Corporation:
Symantec delivers competitive IoT security solutions focusing on protection for devices, data, and privacy across multiple application sectors.Fortinet, Inc.:
Fortinet is recognized for its high-performance cybersecurity solutions, specifically designed to secure complex IoT ecosystems from threats.We're grateful to work with incredible clients.









FAQs
What is the market size of IoT Security?
The IoT Security market is valued at $32.5 billion in 2023 and is projected to grow at a CAGR of 9.8%, indicating a robust increase through 2033, reflecting the rising demand for security solutions in IoT environments.
What are the key market players or companies in the IoT Security industry?
Key players in the IoT Security industry include IBM, Cisco, Symantec, and more. These companies are pivotal in providing innovative security solutions tailored to address IoT vulnerabilities and enhance overall network security.
What are the primary factors driving the growth in the IoT Security industry?
The growth in the IoT Security industry is driven by increasing cyber threats, the proliferation of IoT devices, regulatory compliance requirements, and rising awareness about data privacy and security among consumers and enterprises.
Which region is the fastest Growing in the IoT Security?
The fastest-growing region in the IoT Security market is predicted to be Europe, expanding from a valuation of $11.59 billion in 2023 to $30.53 billion by 2033, fueled by stringent regulations and heightened security needs.
Does ConsaInsights provide customized market report data for the IoT Security industry?
Yes, ConsaInsights offers customized market report data for the IoT Security industry, allowing businesses to access tailored insights and analysis to meet specific strategic needs and understand market dynamics.
What deliverables can I expect from this IoT Security market research project?
Deliverables from the IoT Security market research project include comprehensive market analysis, detailed reports on trends, competitive landscape assessments, and forecasts for market segments to inform strategic decisions.
What are the market trends of IoT Security?
Market trends in IoT Security indicate growth in cloud-based solutions, with significant investments towards improving authentication methods and encryption technologies, as organizations prioritize safeguarding their devices and data.
What are the market segments in IoT Security?
Market segments in IoT Security include Retail, Manufacturing, Government, and Healthcare. Each sector shows significant growth, with notable values such as Retail moving from $13.85 billion in 2023 to $36.48 billion by 2033.