M2m Network Security Market Report
Published Date: 31 January 2026 | Report Code: m2m-network-security
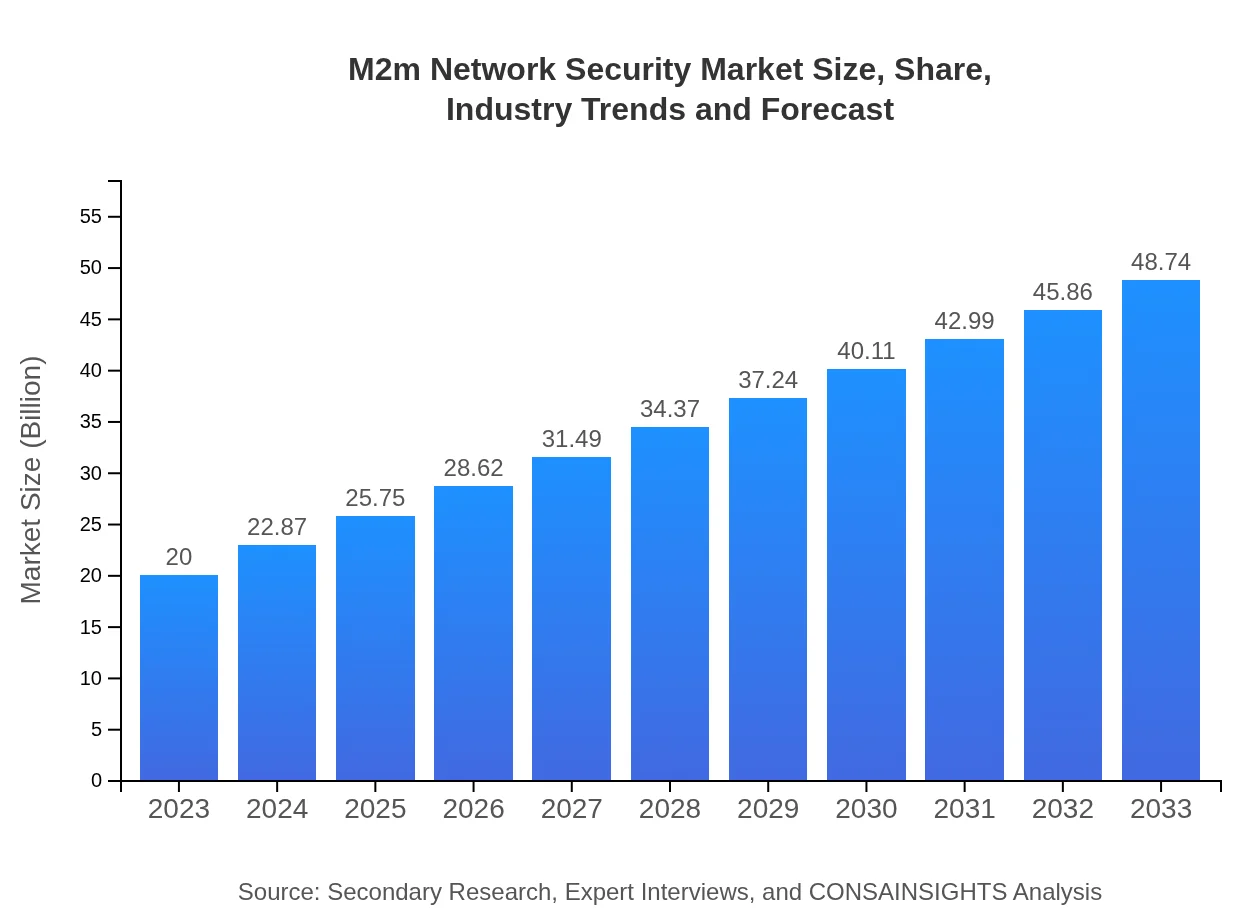
M2m Network Security Market Size, Share, Industry Trends and Forecast to 2033
This report provides a comprehensive analysis of the M2M Network Security market from 2023 to 2033, including market size, trends, segmentation, regional insights, industry analysis, and forecasts for growth and challenges.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
| 2023 Market Size | $20.00 Billion |
| CAGR (2023-2033) | 9% |
| 2033 Market Size | $48.74 Billion |
| Top Companies | Cisco Systems, Inc., IBM Security, Palo Alto Networks, Check Point Software Technologies Ltd. |
| Last Modified Date | 31 January 2026 |
M2M Network Security Market Overview
Customize M2m Network Security Market Report market research report
- ✔ Get in-depth analysis of M2m Network Security market size, growth, and forecasts.
- ✔ Understand M2m Network Security's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in M2m Network Security
What is the Market Size & CAGR of M2M Network Security market in 2023 and expected growth till 2033?
M2M Network Security Industry Analysis
M2M Network Security Market Segmentation and Scope
Tell us your focus area and get a customized research report.
M2M Network Security Market Analysis Report by Region
Europe M2m Network Security Market Report:
In Europe, the market size is expected to grow from USD 5.70 billion in 2023 to USD 13.89 billion by 2033. Increasing regulatory requirements for data protection and a surge in M2M applications across sectors are major contributors.Asia Pacific M2m Network Security Market Report:
In the Asia Pacific region, the M2M Network Security market was valued at USD 4.34 billion in 2023, projected to grow to USD 10.59 billion by 2033. The rapid digital transformation in countries like China and India, alongside a burgeoning IoT ecosystem, drives demand for robust security solutions.North America M2m Network Security Market Report:
North America is anticipated to continue leading the M2M Network Security market, with a projected growth from USD 6.53 billion in 2023 to USD 15.90 billion by 2033. The presence of key market players and rigorous cybersecurity regulations underpin this growth.South America M2m Network Security Market Report:
The South American market was valued at USD 1.75 billion in 2023, expected to increase to USD 4.27 billion by 2033. A growing awareness of cybersecurity threats, coupled with increased government initiatives to enhance digital infrastructure security, is expected to drive growth in this region.Middle East & Africa M2m Network Security Market Report:
The Middle East and Africa market is expected to grow from USD 1.68 billion in 2023 to USD 4.09 billion by 2033, fueled by increasing investments in digitalization and the need for secure communication infrastructures across various industries.Tell us your focus area and get a customized research report.
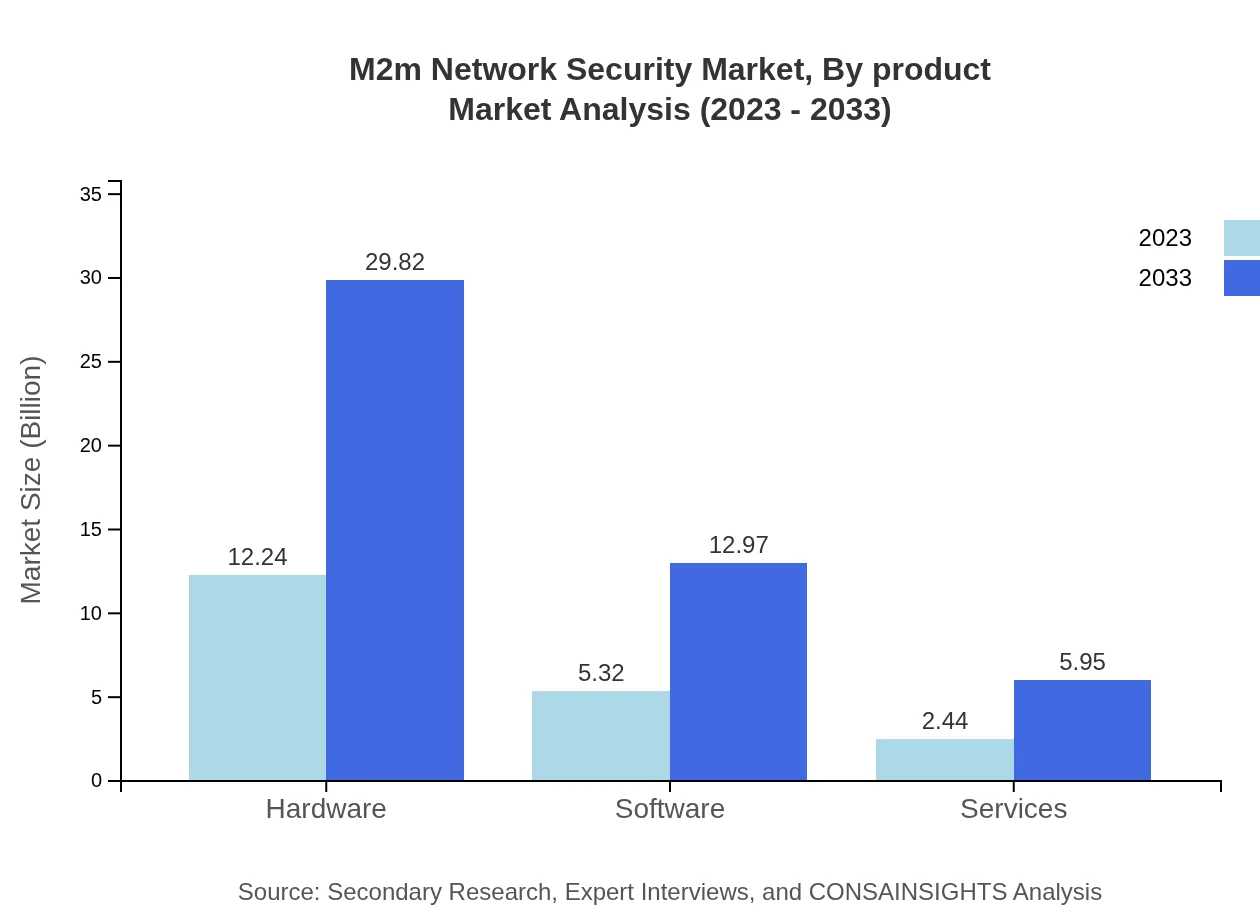
M2m Network Security Market Analysis By Product
Within the product segment, hardware dominates the M2M Network Security market with a size of USD 12.24 billion in 2023, expanding to USD 29.82 billion by 2033 at a significant market share of 61.18%. Software solutions and services also play crucial roles, with the software segment expected to grow from USD 5.32 billion to USD 12.97 billion, maintaining a 26.61% share. This highlights the increasing shift towards integrated security solutions.
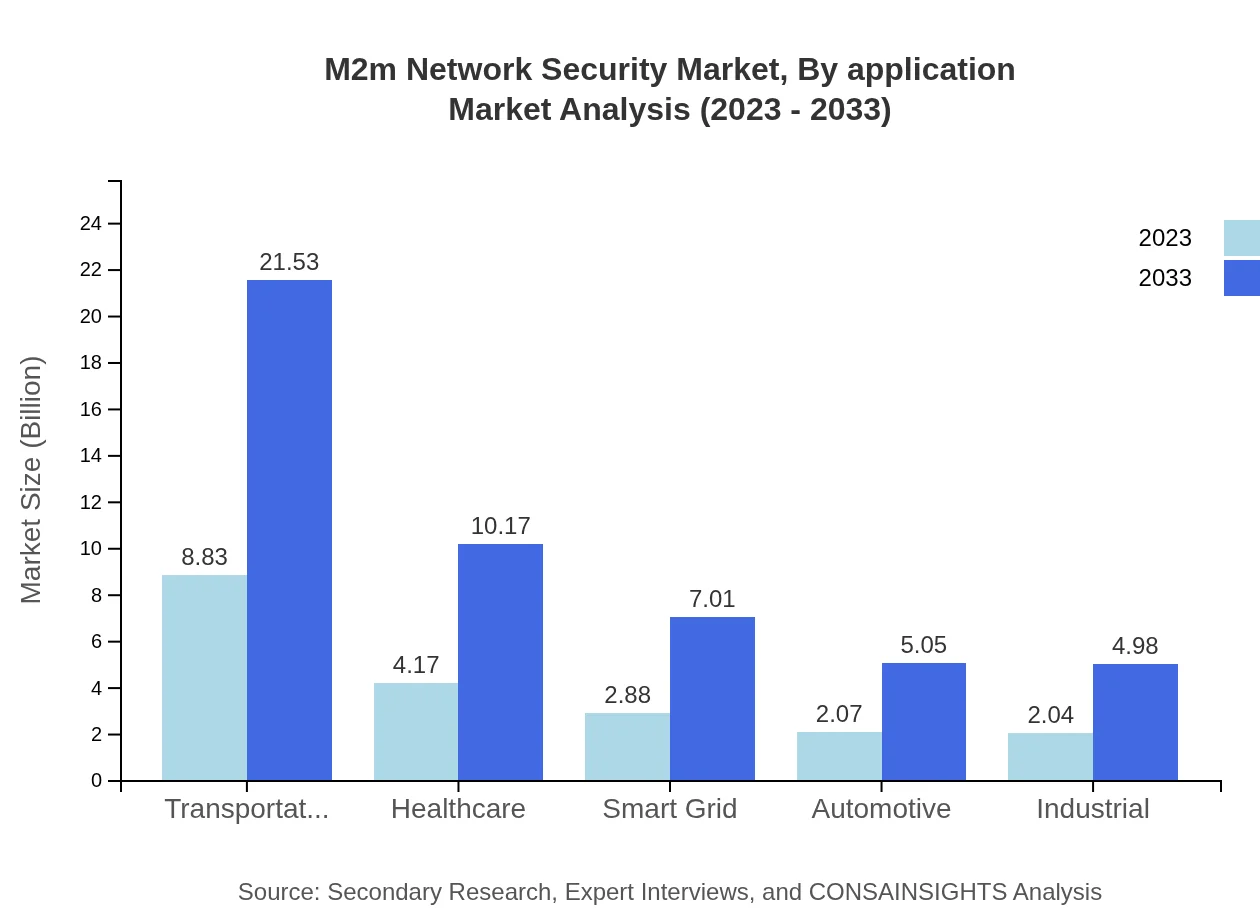
M2m Network Security Market Analysis By Application
Various applications such as manufacturing, healthcare, and transportation are exploring M2M Network Security solutions. Manufacturing leads with a market size of USD 8.83 billion in 2023, expected to grow to USD 21.53 billion by 2033 and accounting for a considerable share. The healthcare sector's engagement with M2M technologies stresses the need for stringent security measures due to the sensitivity of patient data.
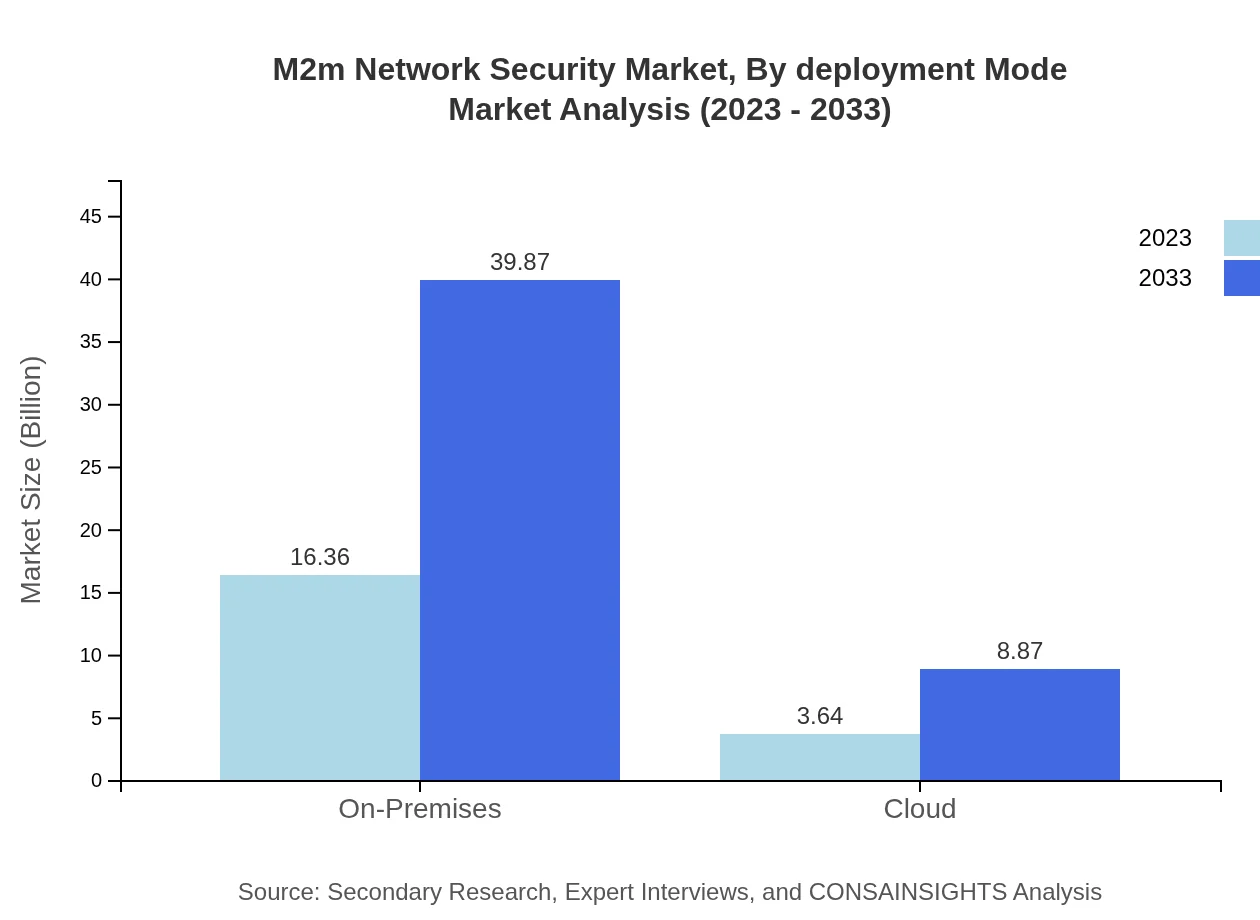
M2m Network Security Market Analysis By Deployment Mode
The market is split between on-premises and cloud solutions, with on-premises security solutions making up USD 16.36 billion in 2023 and anticipated to rise to USD 39.87 billion by 2033. The cloud segment, initially at USD 3.64 billion, is projected to grow, reflecting the market's push towards flexibility and scalability.
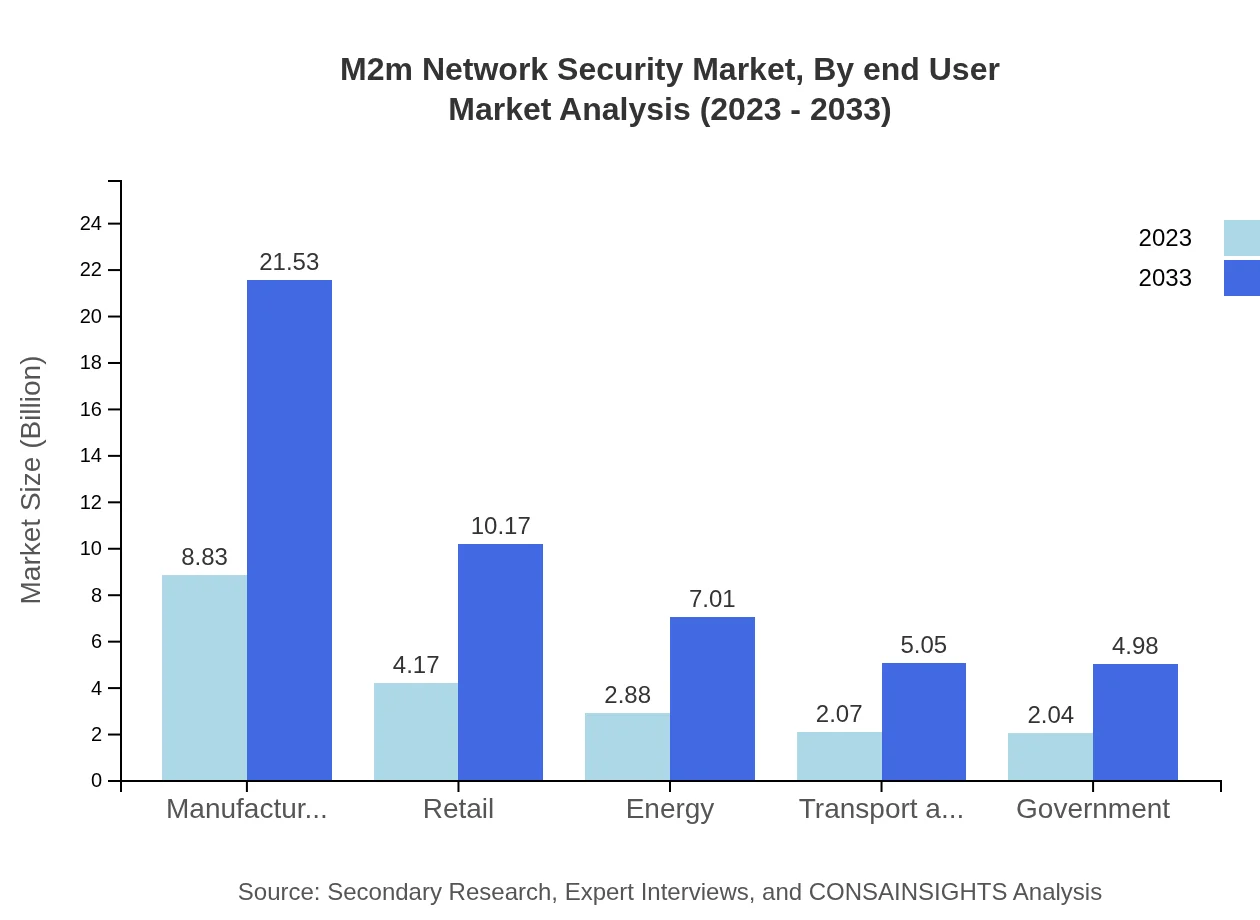
M2m Network Security Market Analysis By End User
Analyzing end-user industries, the transportation sector stands out with a size of USD 8.83 billion in 2023, surging to USD 21.53 billion by 2033. The critical nature of data integrity and security across transportation networks substantiates significant investment in M2M security. Industries such as healthcare and energy also present robust growth potential due to regulatory compliance demands.
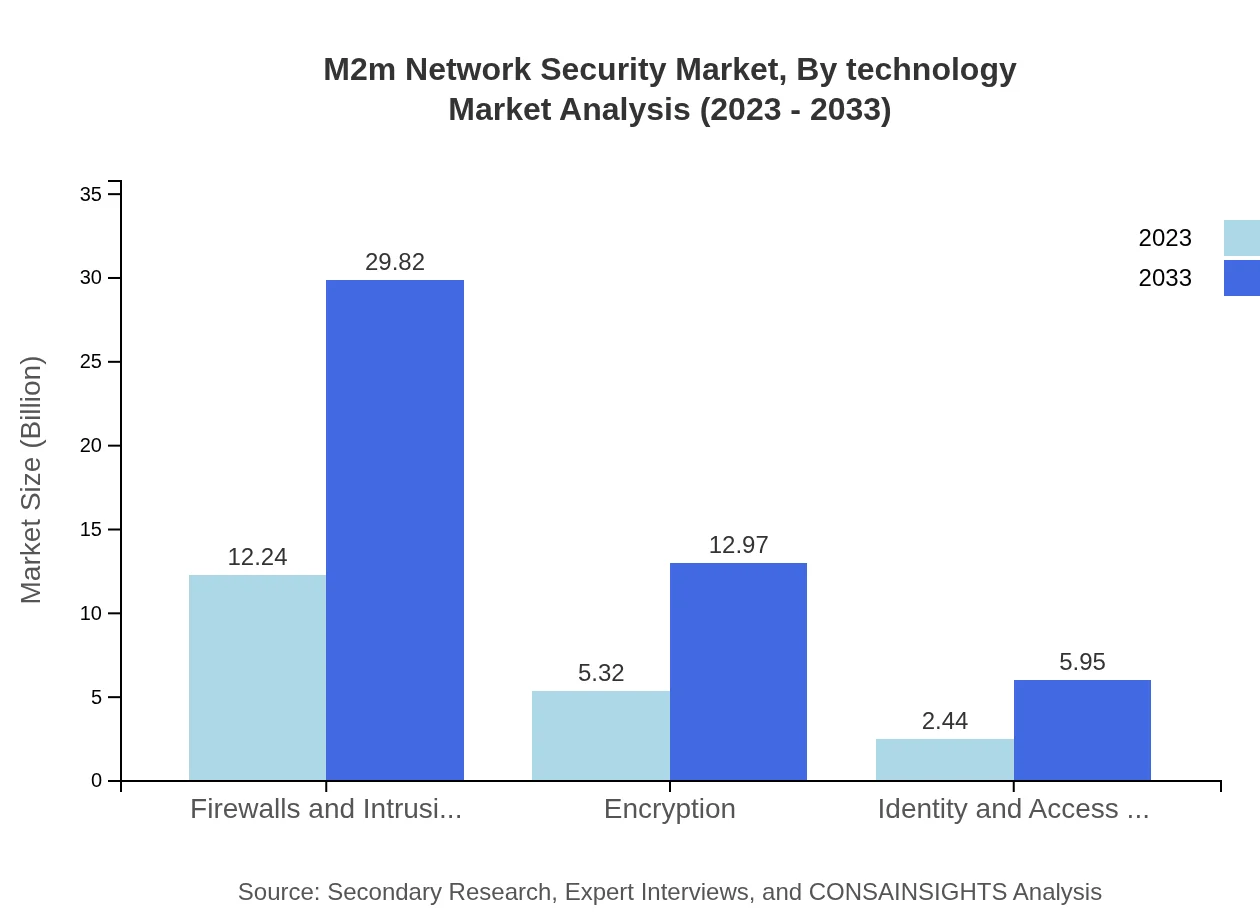
M2m Network Security Market Analysis By Technology
Technological advancements in M2M security closely relate to developments in encryption, identity, and access management (IAM). The encryption segment is valued at USD 5.32 billion in 2023 and projected to reach USD 12.97 billion by 2033. Emergent technologies such as AI and machine learning are increasingly incorporated into M2M security systems, enhancing their adaptability to threats.
M2M Network Security Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in M2M Network Security Industry
Cisco Systems, Inc.:
Cisco provides a comprehensive suite of M2M security solutions designed to protect IoT networks from external threats, utilizing advanced encryption and fortified access controls.IBM Security:
IBM Security offers innovative M2M security solutions employing AI and analytics to predict and mitigate security breaches in real-time.Palo Alto Networks:
Palo Alto Networks specializes in next-generation firewalls and M2M security protocols, emphasizing threat intelligence and proactive security measures.Check Point Software Technologies Ltd.:
Check Point provides M2M security solutions focusing on protecting connected devices with high-performance cybersecurity frameworks.We're grateful to work with incredible clients.









FAQs
What is the market size of M2M Network Security?
The M2M Network Security market is valued at approximately $20 billion in 2023, with a projected CAGR of 9% from 2023 to 2033, indicating significant growth driven by increasing connectivity and security demands.
What are the key market players or companies in the M2M Network Security industry?
Key players in the M2M Network Security market include Cisco Systems, IBM Corporation, and Intel Corporation, which are recognized for their innovative solutions and robust product offerings, helping to shape industry standards.
What are the primary factors driving the growth in the M2M Network Security industry?
Growth in the M2M Network Security industry is primarily driven by the rise in IoT applications, increasing cyber threats, regulatory compliance requirements, and the demand for secure connectivity in sectors like healthcare, manufacturing, and transportation.
Which region is the fastest Growing in the M2M Network Security market?
The Asia Pacific region is anticipated to be the fastest-growing market for M2M Network Security, expanding from $4.34 billion in 2023 to $10.59 billion by 2033, driven by technological advancements and increasing adoption in various industries.
Does ConsaInsights provide customized market report data for the M2M Network Security industry?
Yes, ConsaInsights offers customized market report data tailored to specific needs in the M2M Network Security industry, allowing clients to gain unique insights and strategic recommendations based on their business objectives.
What deliverables can I expect from this M2M Network Security market research project?
Deliverables from the M2M Network Security market research project include comprehensive market analysis, segmentation insights, competitive landscape assessment, regional evaluations, and future trends that facilitate informed decision-making.
What are the market trends of M2M Network Security?
Current trends in the M2M Network Security market include the increasing reliance on cloud-based security solutions, a heightened focus on endpoint security, and the integration of artificial intelligence to enhance threat detection and response.