Mobile Encryption Market Report
Published Date: 31 January 2026 | Report Code: mobile-encryption
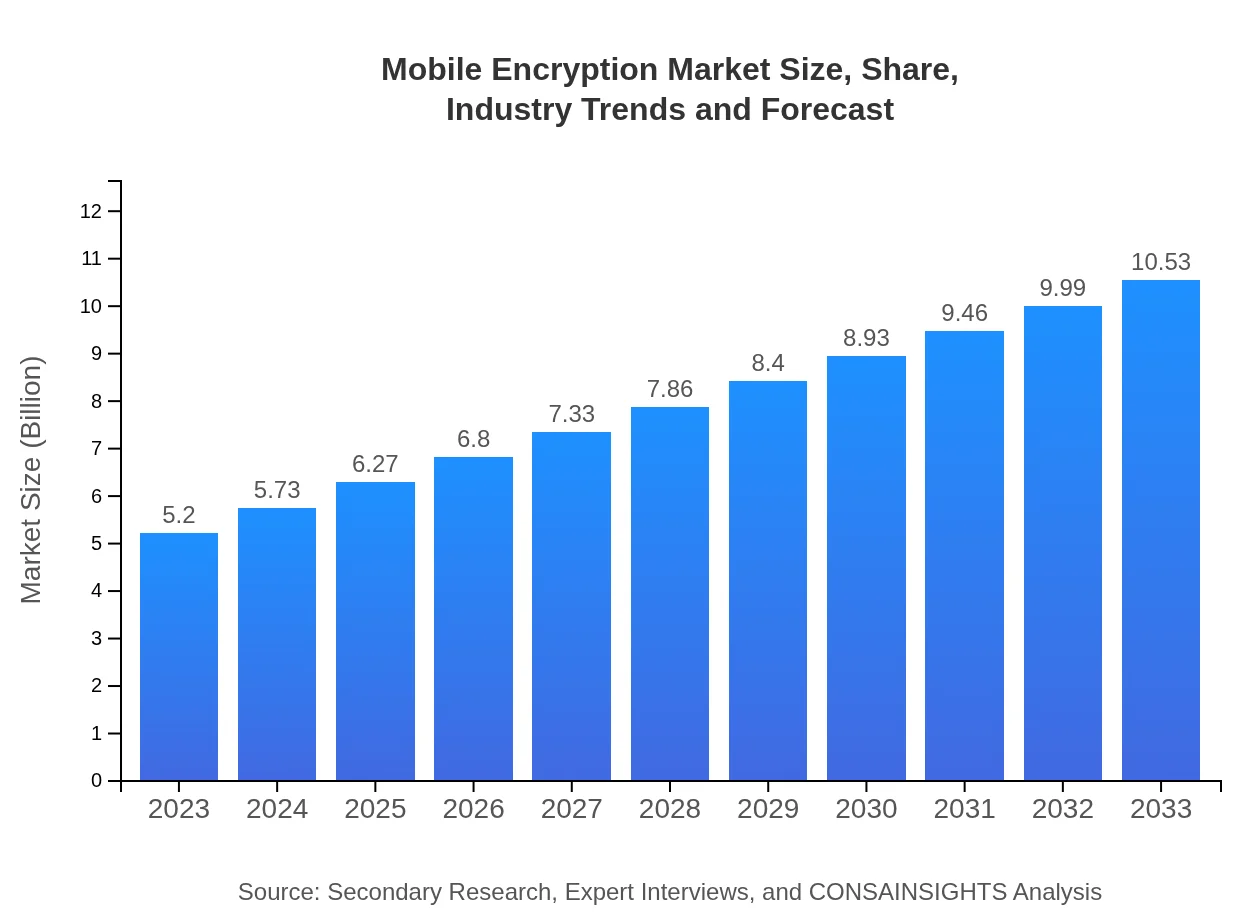
Mobile Encryption Market Size, Share, Industry Trends and Forecast to 2033
This report provides a comprehensive analysis of the Mobile Encryption market, detailing its size, growth trends, segmentation, and region-specific insights from 2023 to 2033, alongside an examination of key players and future forecasts.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
| 2023 Market Size | $5.20 Billion |
| CAGR (2023-2033) | 7.1% |
| 2033 Market Size | $10.53 Billion |
| Top Companies | Symantec Corporation, McAfee LLC, IBM Corporation, Qualys, Inc., Microsoft Corporation |
| Last Modified Date | 31 January 2026 |
Mobile Encryption Market Overview
Customize Mobile Encryption Market Report market research report
- ✔ Get in-depth analysis of Mobile Encryption market size, growth, and forecasts.
- ✔ Understand Mobile Encryption's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Mobile Encryption
What is the Market Size & CAGR of Mobile Encryption market in 2023?
Mobile Encryption Industry Analysis
Mobile Encryption Market Segmentation and Scope
Tell us your focus area and get a customized research report.
Mobile Encryption Market Analysis Report by Region
Europe Mobile Encryption Market Report:
In Europe, the Mobile Encryption market is valued at $1.46 billion in 2023, expected to grow to $2.96 billion by 2033. The European Union's strict data protection laws, including GDPR, necessitate strong encryption measures. Furthermore, businesses are increasingly recognizing the financial ramifications of data breaches, thus, prioritizing investment in encryption technologies.Asia Pacific Mobile Encryption Market Report:
The Asia Pacific region accounted for a market size of approximately $1.08 billion in 2023, which is expected to nearly double to around $2.18 billion by 2033. This growth is largely driven by the increasing smartphone penetration, an expanding digital ecosystem, and stringent data protection regulations across countries. Governments are increasingly mandating data privacy laws, further pushing enterprises to adopt encryption technologies.North America Mobile Encryption Market Report:
North America is leading the Mobile Encryption market, starting at $1.71 billion in 2023 and projecting to reach $3.46 billion by 2033. The presence of key technology players, advanced infrastructure, and strict regulatory frameworks contribute to this growth. Companies in the region are investing heavily in research and development to innovate new encryption solutions to meet increasing security demands.South America Mobile Encryption Market Report:
In South America, the market for Mobile Encryption is set to rise from $0.45 billion in 2023 to $0.92 billion by 2033. The rise is attributed to increased mobile internet usage and growing awareness of data privacy concerns among consumers and businesses alike. Moreover, ongoing digital transformation in the region's economies supports the demand for robust encryption solutions.Middle East & Africa Mobile Encryption Market Report:
The Middle East and Africa region is predicted to grow from $0.50 billion in 2023 to $1.01 billion by 2033. Accelerated digital adoption across various sectors and rising cybersecurity threats are catalyzing the demand for mobile encryption solutions in this region. Increased investments in IT infrastructure and security solutions are also contributing factors.Tell us your focus area and get a customized research report.
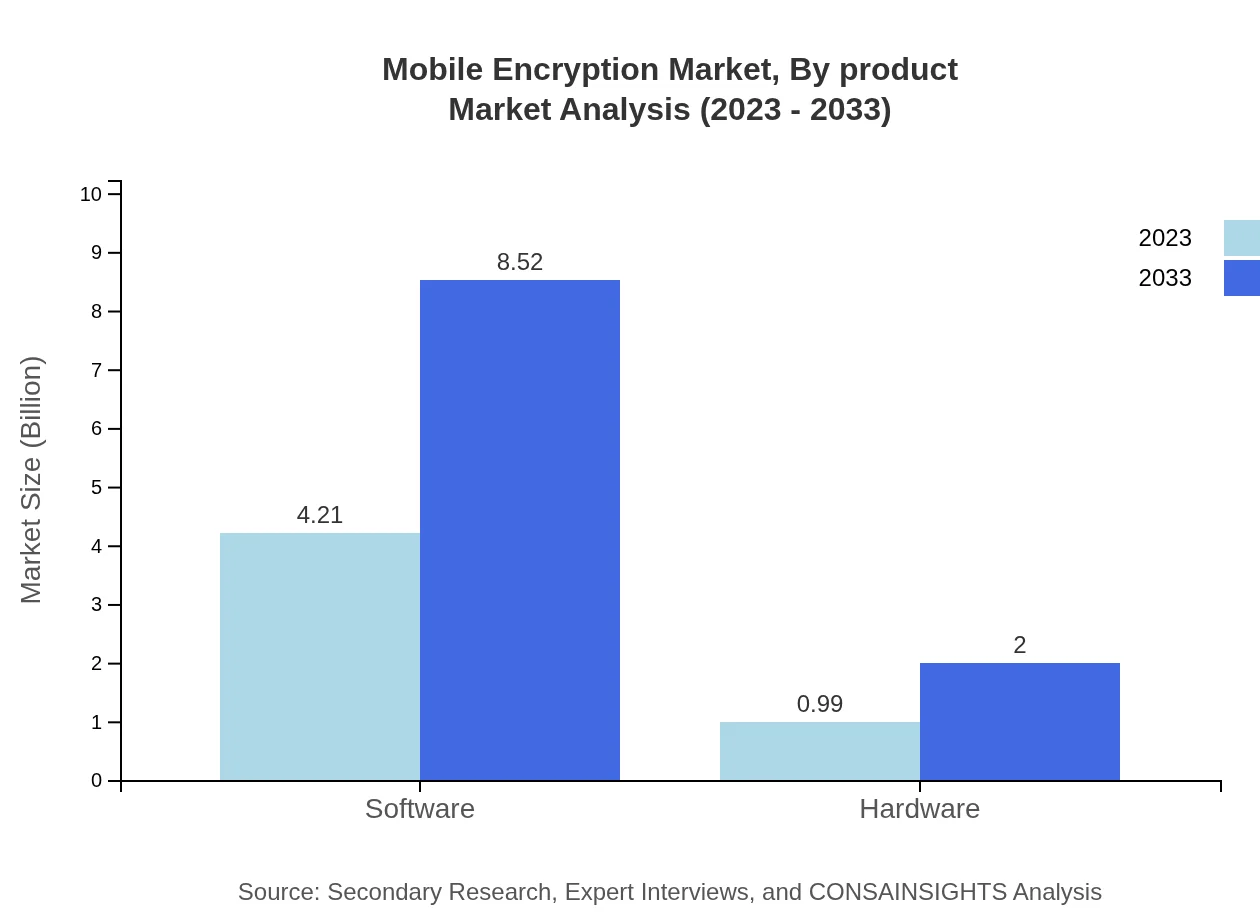
Mobile Encryption Market Analysis By Product
The Mobile Encryption market can be divided into software and hardware categories. As of 2023, the software segment dominates the market size at $4.21 billion, expected to reach $8.52 billion by 2033. This growth is driven by the rising demand for sophisticated security solutions on mobile devices. The hardware segment, albeit smaller at $0.99 billion in 2023, is also set to grow to $2.00 billion by 2033, propelled by an increased focus on end-to-end security solutions.
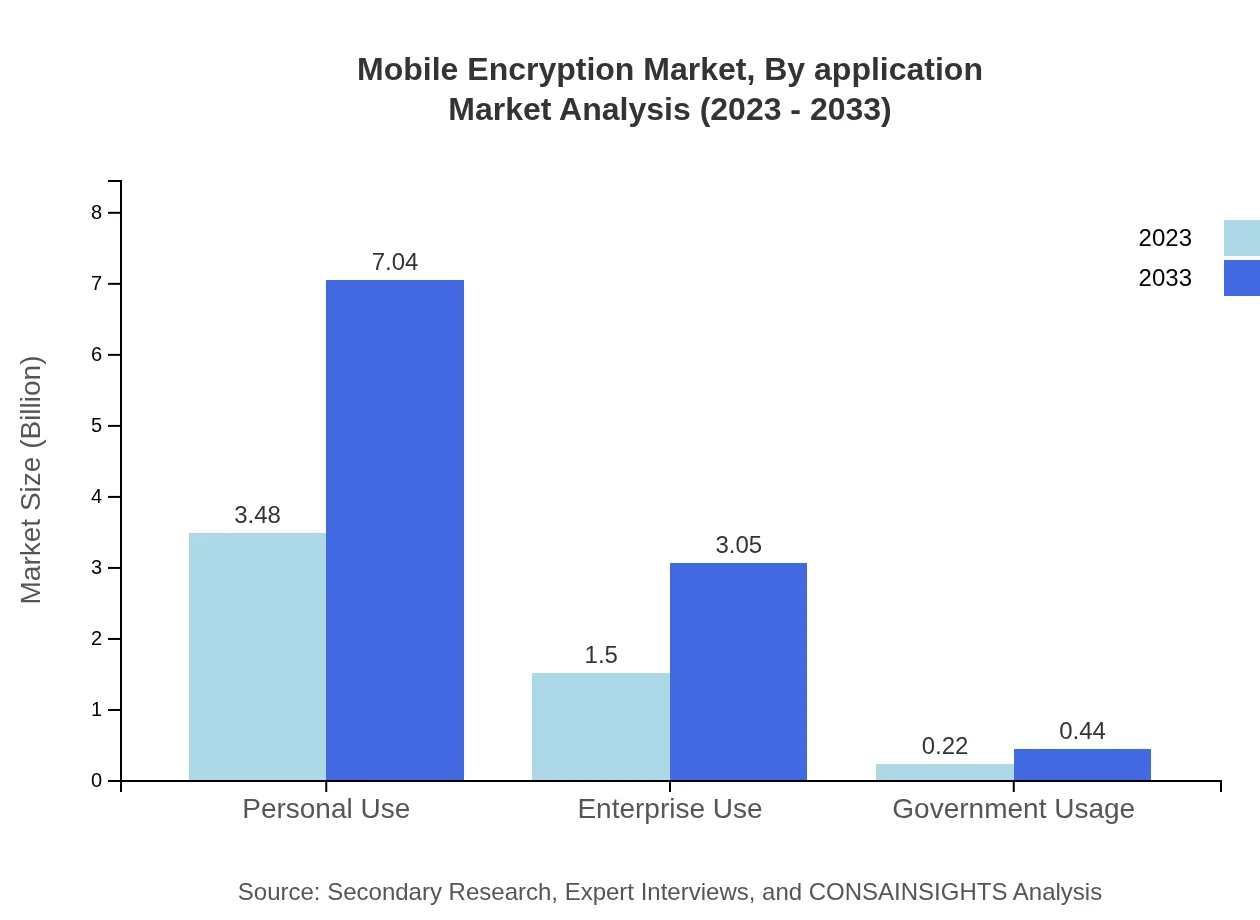
Mobile Encryption Market Analysis By Application
The segmentation by application includes personal use, enterprise use, and government usage. Personal use holds a significant market share of 66.91% in 2023, generating approximately $3.48 billion and projected to reach $7.04 billion by 2033. Enterprise use, while smaller, represents a growing segment with a market size of $1.50 billion in 2023 and $3.05 billion by 2033, reflecting increasing corporate focus on data protection.
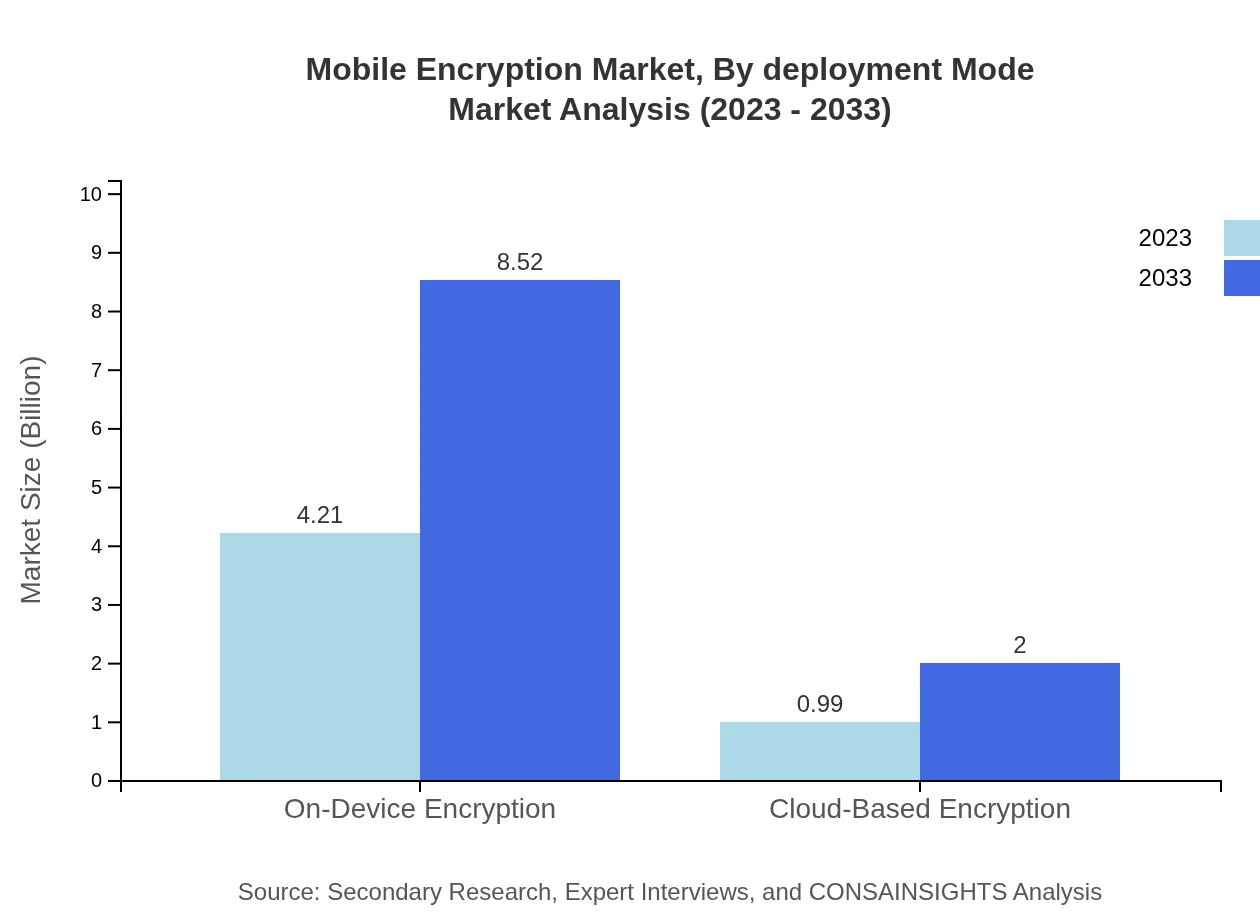
Mobile Encryption Market Analysis By Deployment Mode
In terms of deployment modes, on-device encryption continues to lead, accounting for $4.21 billion in 2023 and expected to reach $8.52 billion by 2033. Cloud-based encryption holds a smaller share at $0.99 billion but is projected to grow rapidly to $2.00 billion, driven by the growing popularity of cloud services and remote work trends.
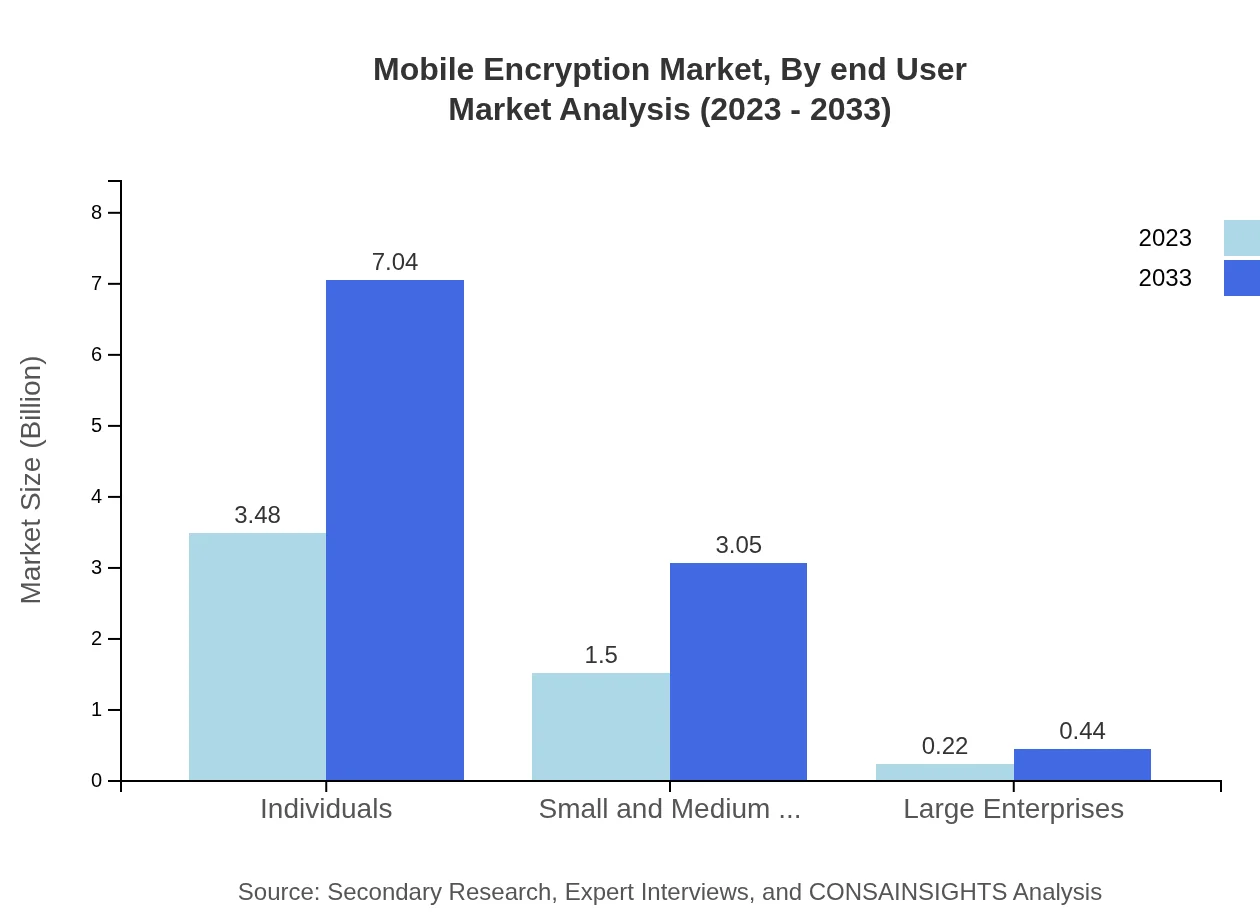
Mobile Encryption Market Analysis By End User
The mobile encryption market serves various end-users, including individuals, small and medium enterprises (SMEs), and large enterprises. Individual users are the largest segment at $3.48 billion in 2023 and are expected to grow to $7.04 billion by 2033. SMEs and large enterprises follow, with $1.50 billion and $0.22 billion in 2023 respectively, expected to grow to $3.05 billion and $0.44 billion by 2033.
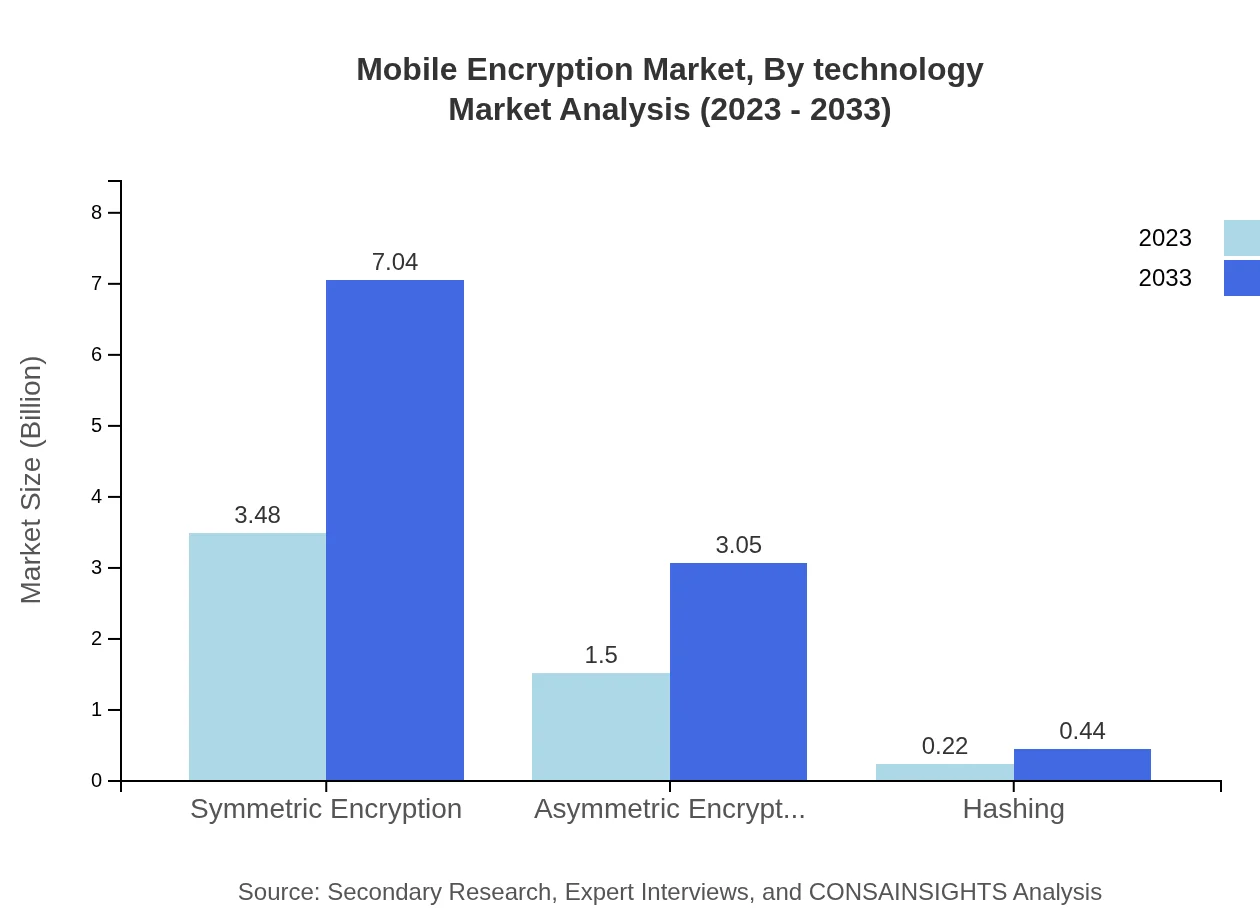
Mobile Encryption Market Analysis By Technology
The market can also be segmented by technology, including symmetric encryption, asymmetric encryption, and hashing. Symmetric encryption maintains a leading share of 66.91%, generating $3.48 billion in 2023 and projected to reach $7.04 billion in 2033. Asymmetric encryption and hashing contribute smaller but growing shares, with their respective forecasts indicating growth from $1.50 billion to $3.05 billion and from $0.22 billion to $0.44 billion in the same period.
Mobile Encryption Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Mobile Encryption Industry
Symantec Corporation:
A leading cybersecurity company offering a range of encryption solutions integrating endpoint protection with advanced threat intelligence.McAfee LLC:
Known for providing comprehensive security solutions, McAfee focuses on advanced mobile encryption products designed for both consumers and enterprises.IBM Corporation:
IBM offers a suite of encryption technologies that empower organizations to secure sensitive data across devices, emphasizing scalability and compliance.Qualys, Inc.:
Qualys provides cloud-based solutions for regulatory compliance, monitoring, and encryption to protect sensitive information effectively.Microsoft Corporation:
In addition to numerous software products, Microsoft offers strong encryption capabilities integrated into its software and cloud services, catering to a wide user base.We're grateful to work with incredible clients.









FAQs
What is the market size of mobile Encryption?
The mobile encryption market is valued at $5.2 billion in 2023 and is expected to grow at a CAGR of 7.1% over the next decade, projecting substantial growth as data security becomes increasingly critical.
What are the key market players or companies in this mobile Encryption industry?
Key players in the mobile encryption market include industry leaders focused on delivering robust encryption solutions, enhancing data privacy and security for consumers and enterprises alike.
What are the primary factors driving the growth in the mobile Encryption industry?
The demand for data protection amid rising cyber threats, increasing regulations for data security, and the proliferation of mobile devices are significant factors propelling the mobile encryption industry's growth.
Which region is the fastest Growing in the mobile Encryption market?
The Asia Pacific region is forecasted to be the fastest-growing market, with values rising from $1.08 billion in 2023 to $2.18 billion by 2033, driven by technological advancements and rising security concerns.
Does ConsaInsights provide customized market report data for the mobile Encryption industry?
Yes, ConsaInsights offers customized market reports tailored to specific client needs in the mobile encryption sector, providing insights into market size, trends, and competitive analysis.
What deliverables can I expect from this mobile Encryption market research project?
Deliverables from the mobile encryption market research include comprehensive reports on market size, segmentation analysis, growth forecasts, and trends that inform strategic decision-making.
What are the market trends of mobile Encryption?
Current trends include a shift towards multi-layered security solutions, the rise of cloud-based encryption, and increasing end-user awareness, all contributing to the evolution of mobile encryption solutions.