Network Forensics Market Report
Published Date: 31 January 2026 | Report Code: network-forensics
Network Forensics Market Size, Share, Industry Trends and Forecast to 2033
This report provides an in-depth analysis of the Network Forensics market, emphasizing growth trends, regional insights, and technological advancements from 2023 to 2033. It offers forecasts, industry analysis, segmentation, and profiles of leading market players.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
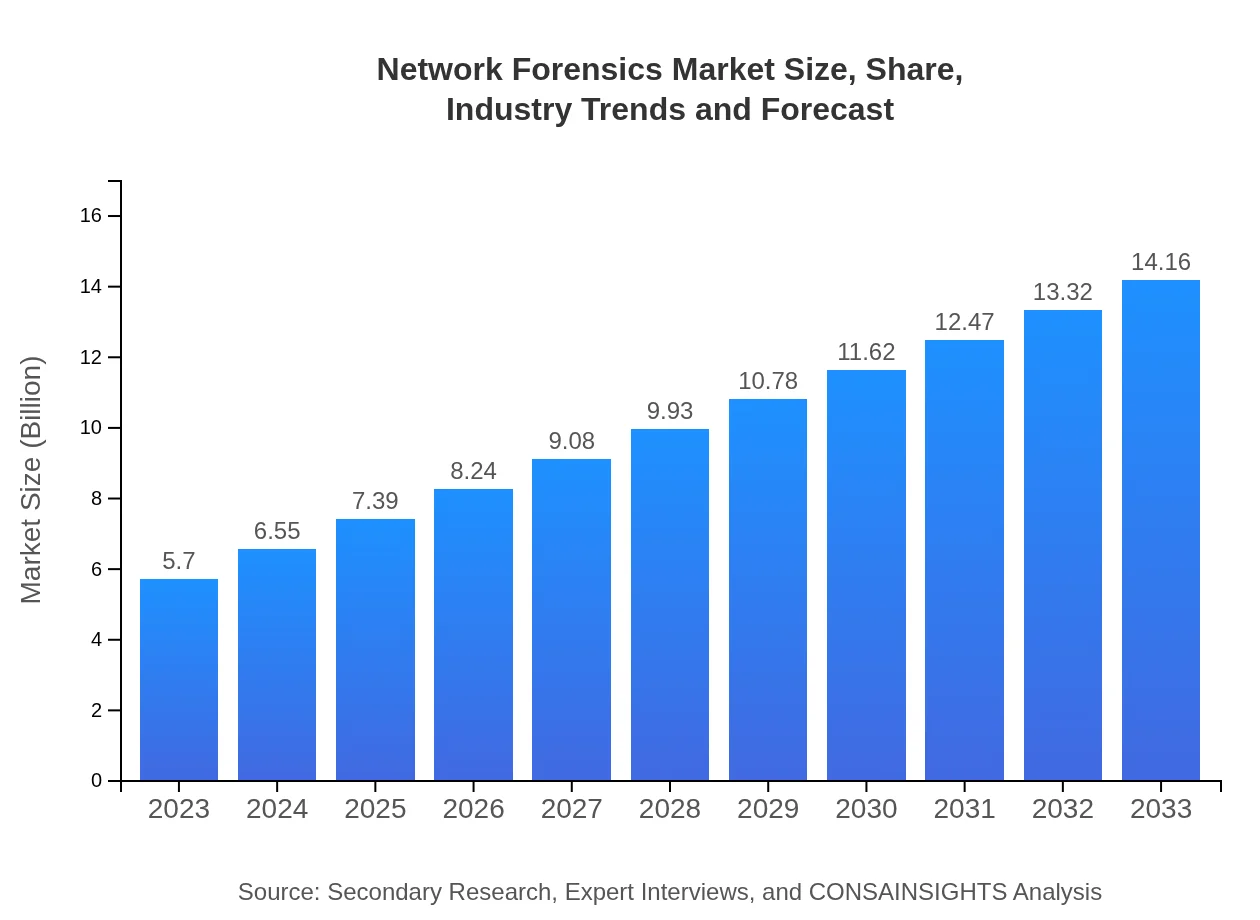
| 2023 Market Size | $5.70 Billion |
| CAGR (2023-2033) | 9.2% |
| 2033 Market Size | $14.16 Billion |
| Top Companies | Cisco Systems, IBM Security, Fortinet, NetWitness, RSA Security |
| Last Modified Date | 31 January 2026 |
Network Forensics Market Overview
Customize Network Forensics Market Report market research report
- ✔ Get in-depth analysis of Network Forensics market size, growth, and forecasts.
- ✔ Understand Network Forensics's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Network Forensics
What is the Market Size & CAGR of Network Forensics market in 2023 and 2033?
Network Forensics Industry Analysis
Network Forensics Market Segmentation and Scope
Tell us your focus area and get a customized research report.
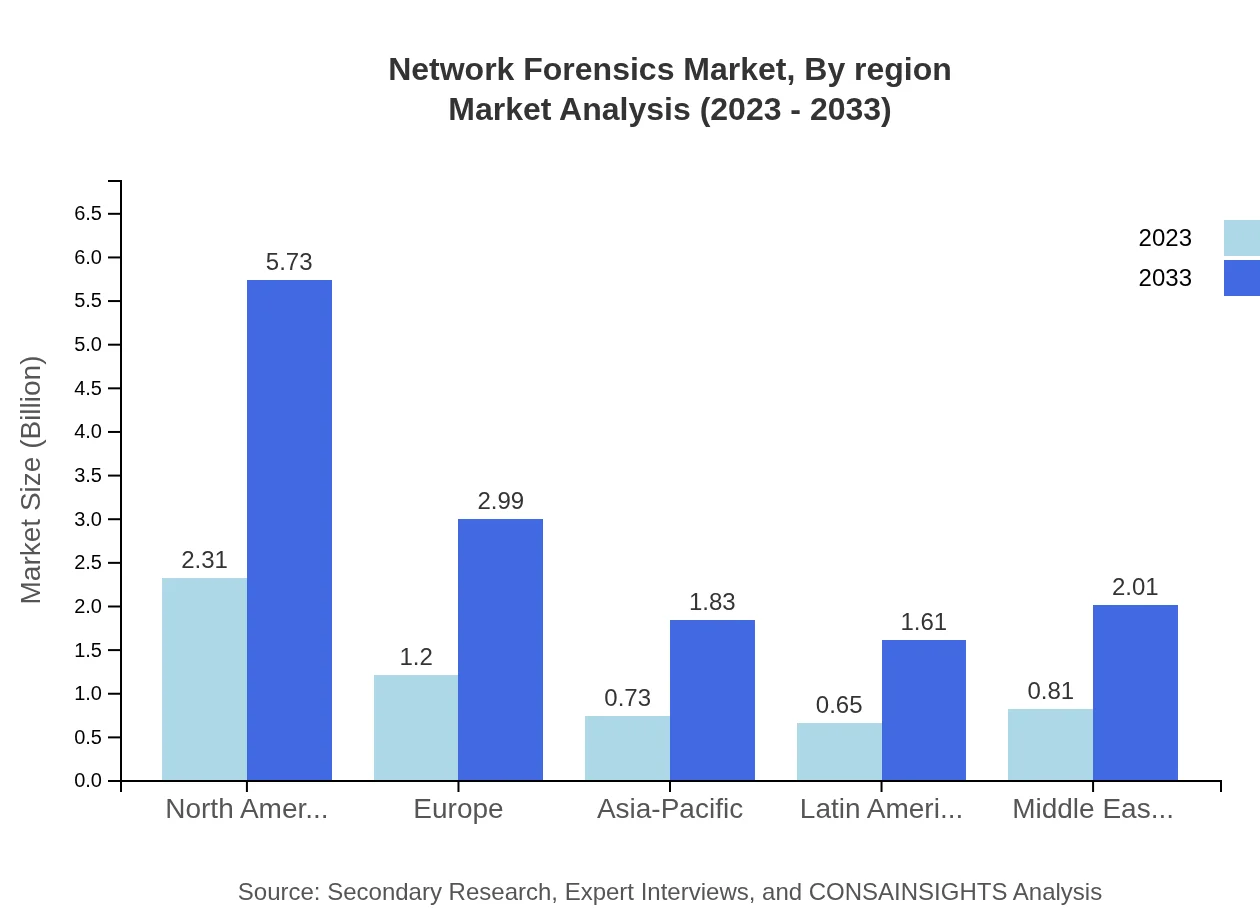
Network Forensics Market Analysis Report by Region
Europe Network Forensics Market Report:
In Europe, the Network Forensics market is projected to grow from $1.58 billion in 2023 to $3.94 billion by 2033. The growth stems from stringent data protection laws such as GDPR, driving businesses to invest heavily in network forensic solutions to comply with regulations and mitigate risks associated with cybersecurity threats.Asia Pacific Network Forensics Market Report:
The Asia Pacific region is anticipated to witness significant growth in the Network Forensics market, with revenues projected to increase from $1.09 billion in 2023 to $2.71 billion by 2033. This growth is driven by increasing internet penetration, rising cybersecurity incidences, and extensive investments in IT infrastructure across countries like India, China, and Japan. The growing adoption of advanced threat detection technologies further contributes to market expansion in this region.North America Network Forensics Market Report:
North America is currently the largest market for Network Forensics, with an expected market size of $2.16 billion in 2023 growing to approximately $5.36 billion by 2033. The region’s leading position is attributed to high cybersecurity investments, strict compliance regulations, and a well-established IT infrastructure. The growing necessity for protecting sensitive data amidst increasing cyber threats significantly boosts market growth in North America.South America Network Forensics Market Report:
In South America, the market for Network Forensics is poised to grow from $0.54 billion in 2023 to $1.35 billion by 2033. Factors influencing this growth include a rising awareness of cybersecurity threats among businesses and government initiatives to encourage digital transformation, thereby boosting demand for network security solutions and forensic applications.Middle East & Africa Network Forensics Market Report:
In the Middle East and Africa, the Network Forensics market is expected to see growth from $0.32 billion in 2023 to $0.80 billion by 2033. The region is gradually adopting advanced security solutions, driven by increasing internet connectivity, mobile penetration, and cyber threat awareness. Investments in infrastructure and a growing focus on digital security will propel the market further.Tell us your focus area and get a customized research report.
Network Forensics Market Analysis By Solution Type
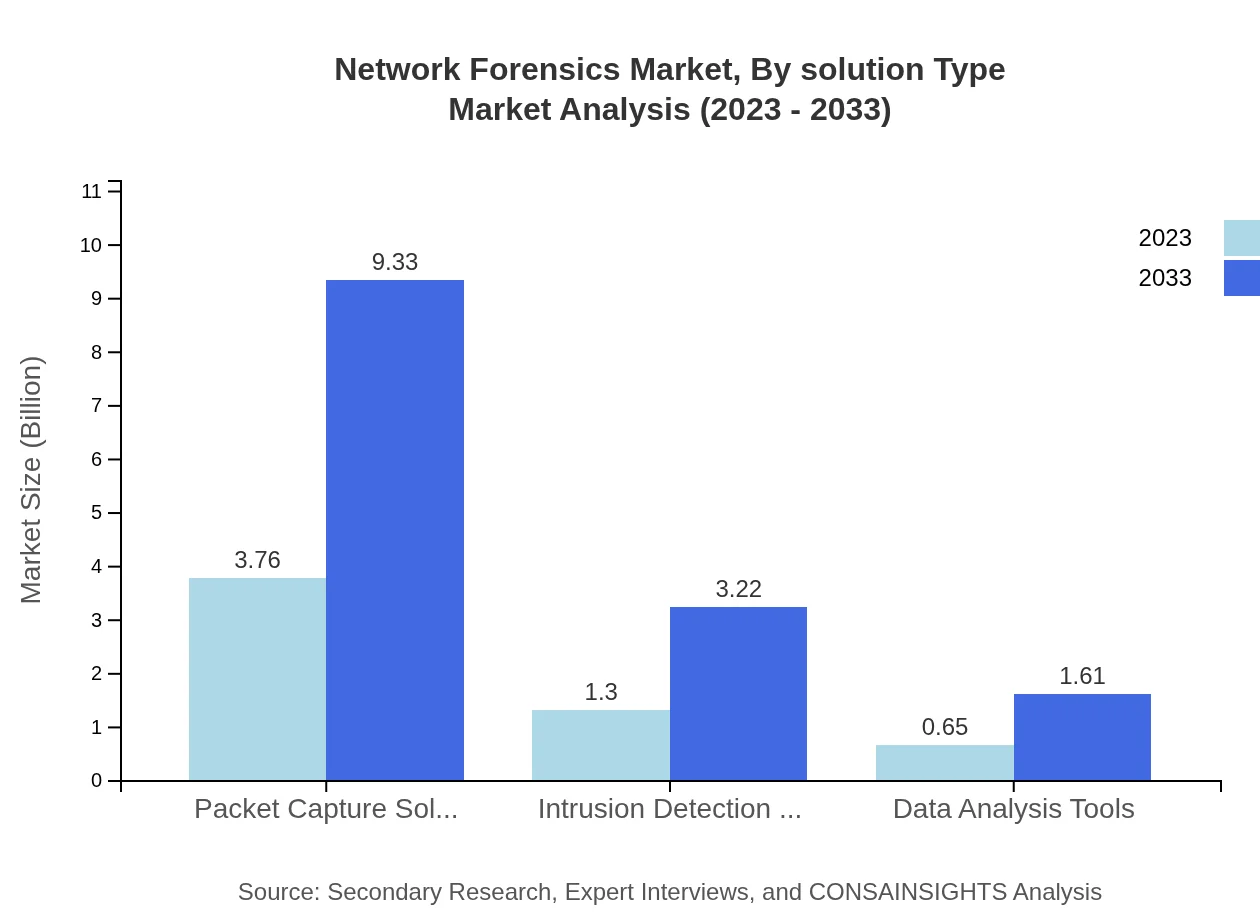
The Network Forensics market is segmented by solution type into packet capture solutions, intrusion detection systems (IDS), data analysis tools, and others. Packet capture solutions hold a significant market share of 65.91% in 2023, with expectations to maintain a dominant position. Intrusion detection systems, accounting for 22.75% of the market, provide critical insights into network security breaches. Data analysis tools, comprising 11.34% of the market, enhance the effectiveness of investigations and incident response.
Network Forensics Market Analysis By Deployment
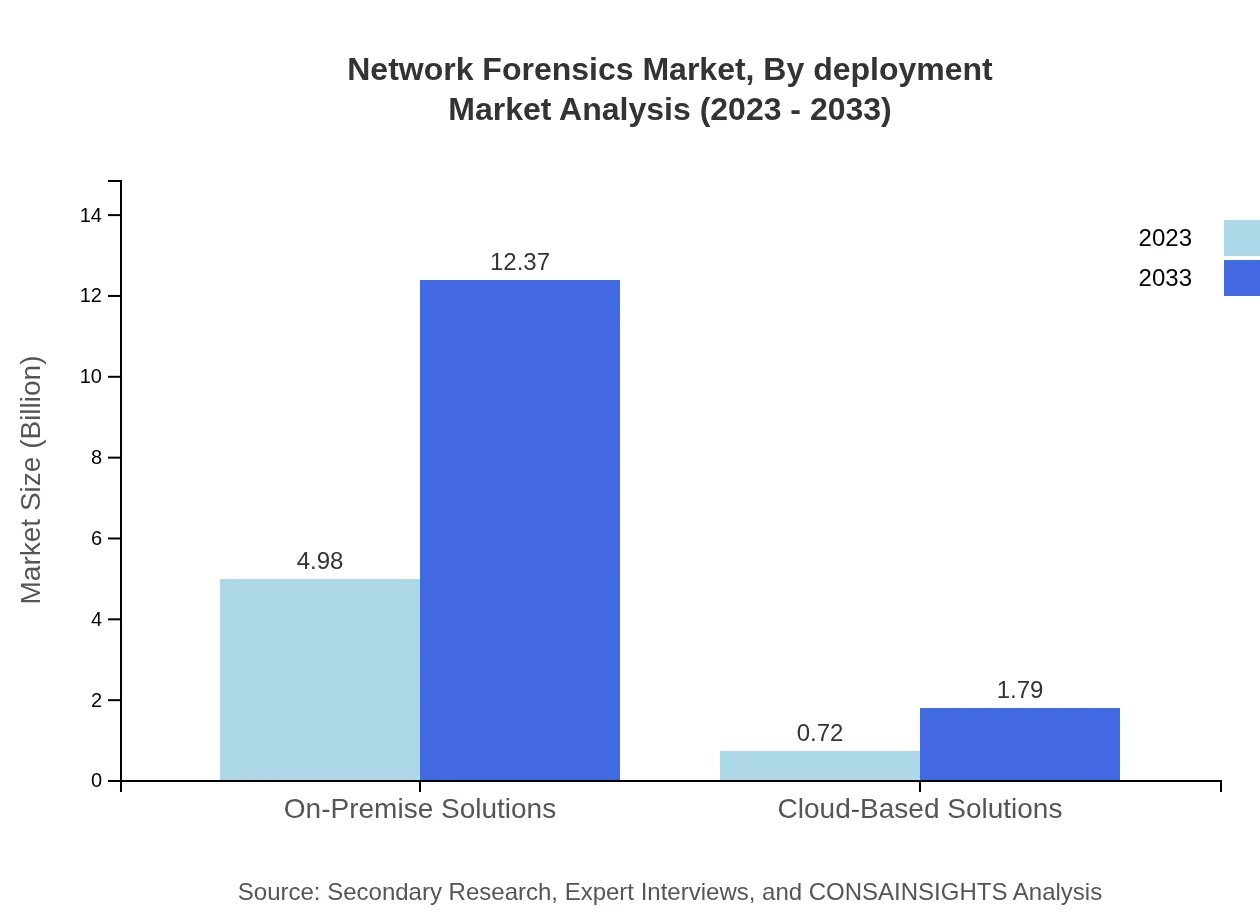
The deployment of Network Forensics solutions is categorized into on-premise and cloud-based options. On-premise solutions account for 87.33% of the market share as enterprises prefer this model for greater control over their data. However, the adoption of cloud-based solutions, representing 12.67% share, is rising as organizations lean towards flexible and scalable options suitable for remote work environments.
Network Forensics Market Analysis By End User
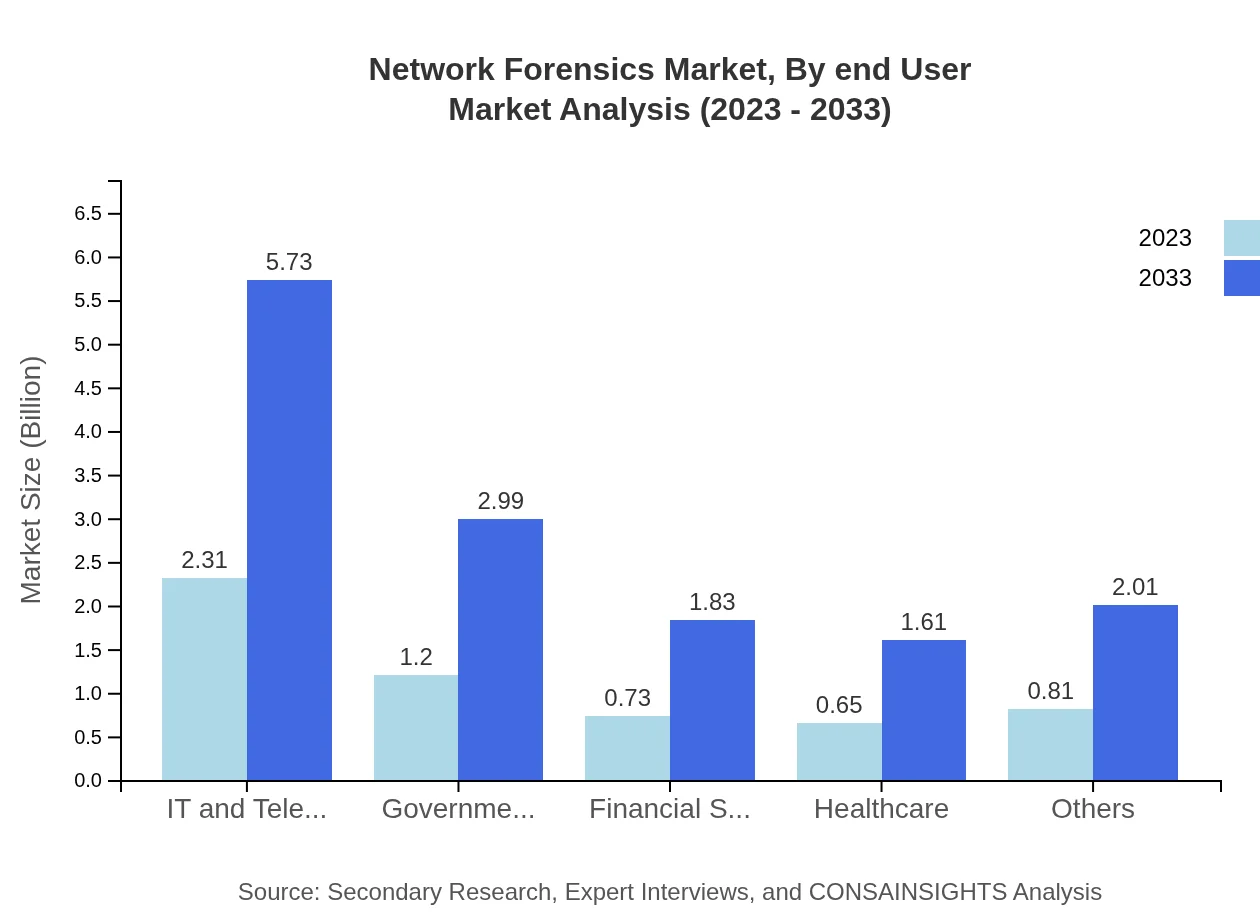
End-user segmentation includes IT and Telecom, government agencies, financial services, healthcare, and others. IT and Telecom dominate the market with a 40.45% share in 2023. Government agencies account for 21.09%, reflecting their critical need for cybersecurity measures. The financial sector (12.89%) and healthcare (11.40%) sectors also show significant demand for effective network forensics due to the sensitivity of their data.
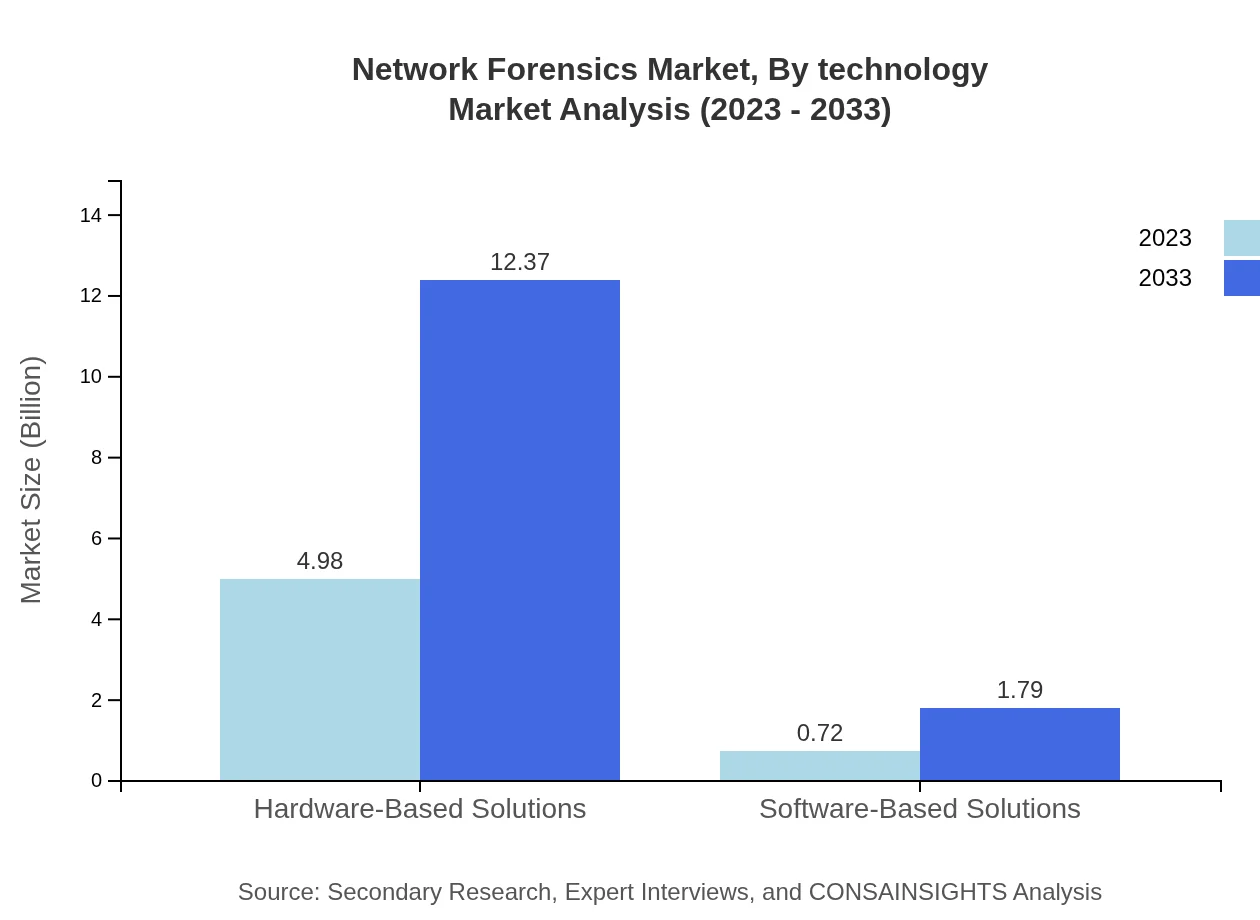
Network Forensics Market Analysis By Technology
Technological trends in the Network Forensics market focus on advancements such as machine learning and artificial intelligence for improved threat detection and analysis. The integration of AI-powered analytics and automated incident response are crucial for enhancing forensic investigations. The trend towards utilizing big data approaches is also emerging, aiming to manage and analyze extensive network traffic effectively.
Network Forensics Market Analysis By Region
Geographically, the North American region leads the Network Forensics market, reflecting a 40.45% share. Following closely are Europe (21.09%) and the Asia Pacific region (12.89%). Other regions, including Latin America and the Middle East and Africa, hold 11.4% and 14.17% respectively, indicating diverse growth opportunities as organizations worldwide recognize the importance of implementing robust network forensic solutions.
Network Forensics Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Network Forensics Industry
Cisco Systems:
Cisco is a leading player in the network security space, providing advanced network forensics tools that help organizations analyze traffic, detect anomalies, and respond to threats effectively.IBM Security:
IBM offers a comprehensive range of security solutions, including network forensics products that leverage AI and automation to streamline the threat detection and response processes.Fortinet:
Fortinet is renowned for its innovative security solutions, focusing on network forensics as essential in their strategy for combating cyber threats across enterprises.NetWitness:
NetWitness specializes in network forensics and monitoring solutions, providing organizations with real-time threat detection capabilities and deep insights into network behavior.RSA Security:
RSA Security's solutions are pivotal in enhancing network forensics capabilities through advanced analytics and incident response tools aimed at identifying and mitigating threats swiftly.We're grateful to work with incredible clients.









FAQs
What is the market size of Network Forensics?
The global market size for network forensics is projected to reach $5.7 billion by 2033, growing at a CAGR of 9.2%. This growth reflects increasing concerns over network security and the complexity of cybersecurity threats.
What are the key market players or companies in the Network Forensics industry?
Key players in the network forensics market include Cisco, IBM, and Palo Alto Networks. These companies are renowned for their innovative solutions and contribute significantly to market expansion through advanced technologies and strategic partnerships.
What are the primary factors driving the growth in the Network Forensics industry?
Major factors driving growth in the network forensics industry include rising cyber threats, regulatory mandates for security compliance, and the increasing adoption of advanced security solutions. The growing complexity of IT infrastructure necessitates enhanced forensic capabilities.
Which region is the fastest Growing in the Network Forensics?
The fastest-growing region in the network forensics market is North America, projected to increase from $2.16 billion in 2023 to $5.36 billion by 2033. Europe also shows significant growth, expanding from $1.58 billion to $3.94 billion in the same period.
Does ConsaInsights provide customized market report data for the Network Forensics industry?
Yes, ConsaInsights offers customized market report data tailored to specific needs in the network forensics industry. These reports can be adjusted to focus on particular regions, companies, or market segments to provide applicable insights.
What deliverables can I expect from this Network Forensics market research project?
From the network forensics market research project, you can expect detailed reports including market size and share analysis, growth projections, and competitive landscape reviews. Custom insights based on segments and regional performance will also be provided.
What are the market trends of Network Forensics?
Market trends in network forensics include the shift towards cloud-based solutions and increased incorporation of AI and machine learning. There’s a significant rise in packet capture systems, reflecting the need for robust data retention and analysis capabilities.