Out Of Band Authentication Market Report
Published Date: 31 January 2026 | Report Code: out-of-band-authentication
Out Of Band Authentication Market Size, Share, Industry Trends and Forecast to 2033
This report provides comprehensive insights into the Out Of Band Authentication market, including its current state, future trends, and growth forecasts from 2023 to 2033. It covers market analysis by region, segmentation, industry dynamics, and profiles of leading players.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
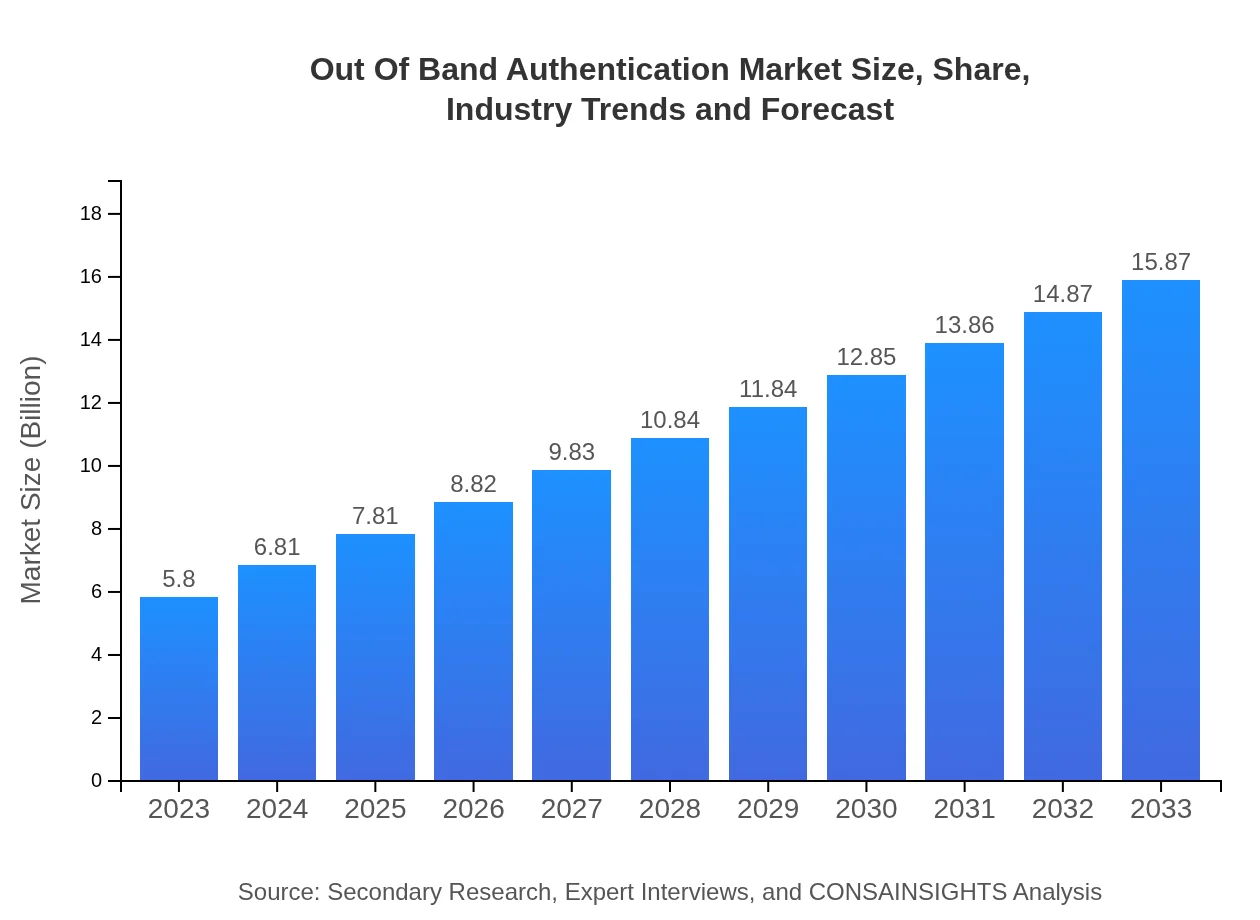
| 2023 Market Size | $5.80 Billion |
| CAGR (2023-2033) | 10.2% |
| 2033 Market Size | $15.87 Billion |
| Top Companies | Duo Security, Okta, Authy, Gemalto |
| Last Modified Date | 31 January 2026 |
Out Of Band Authentication Market Overview
Customize Out Of Band Authentication Market Report market research report
- ✔ Get in-depth analysis of Out Of Band Authentication market size, growth, and forecasts.
- ✔ Understand Out Of Band Authentication's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Out Of Band Authentication
What is the Market Size & CAGR of Out Of Band Authentication market in 2033?
Out Of Band Authentication Industry Analysis
Out Of Band Authentication Market Segmentation and Scope
Tell us your focus area and get a customized research report.
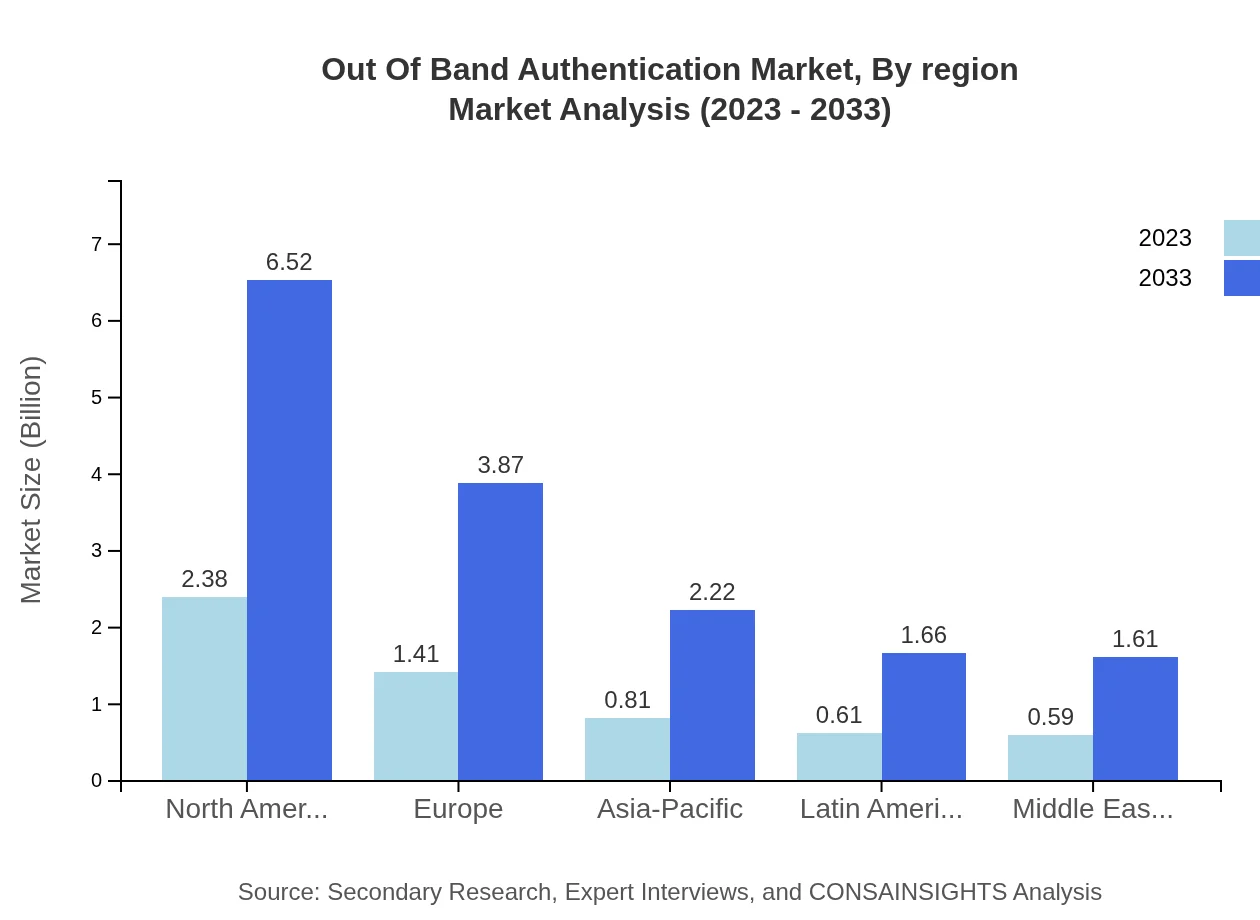
Out Of Band Authentication Market Analysis Report by Region
Europe Out Of Band Authentication Market Report:
The European market is projected to increase from 1.87 billion USD in 2023 to 5.13 billion USD by 2033. The growth is supported by the digitization of services across various sectors and heightened regulations such as GDPR, fostering a greater need for secure authentication methods.Asia Pacific Out Of Band Authentication Market Report:
The Asia Pacific region is expected to witness considerable growth, with market size projected to increase from 1.10 billion USD in 2023 to 3.01 billion USD by 2033. The surge is driven by a rising number of internet users and the proliferation of mobile devices, increasing the demand for secure authentication methods.North America Out Of Band Authentication Market Report:
Northern America leads the market with a size of 1.97 billion USD in 2023, anticipated to grow to 5.41 billion USD by 2033, driven by strong investments in cybersecurity and compliance with stringent data security regulations.South America Out Of Band Authentication Market Report:
In South America, the Out Of Band Authentication market is set to grow from 0.35 billion USD in 2023, reaching approximately 0.96 billion USD by 2033. The growth is fueled by heightened cybersecurity awareness and a gradual digital transformation in financial services.Middle East & Africa Out Of Band Authentication Market Report:
In the Middle East and Africa, the market is expected to grow from 0.51 billion USD in 2023 to 1.38 billion USD by 2033. This growth is attributed to increasing digital transactions and the rising need for compliance with cyber security frameworks.Tell us your focus area and get a customized research report.
Out Of Band Authentication Market Analysis By Authentication Method
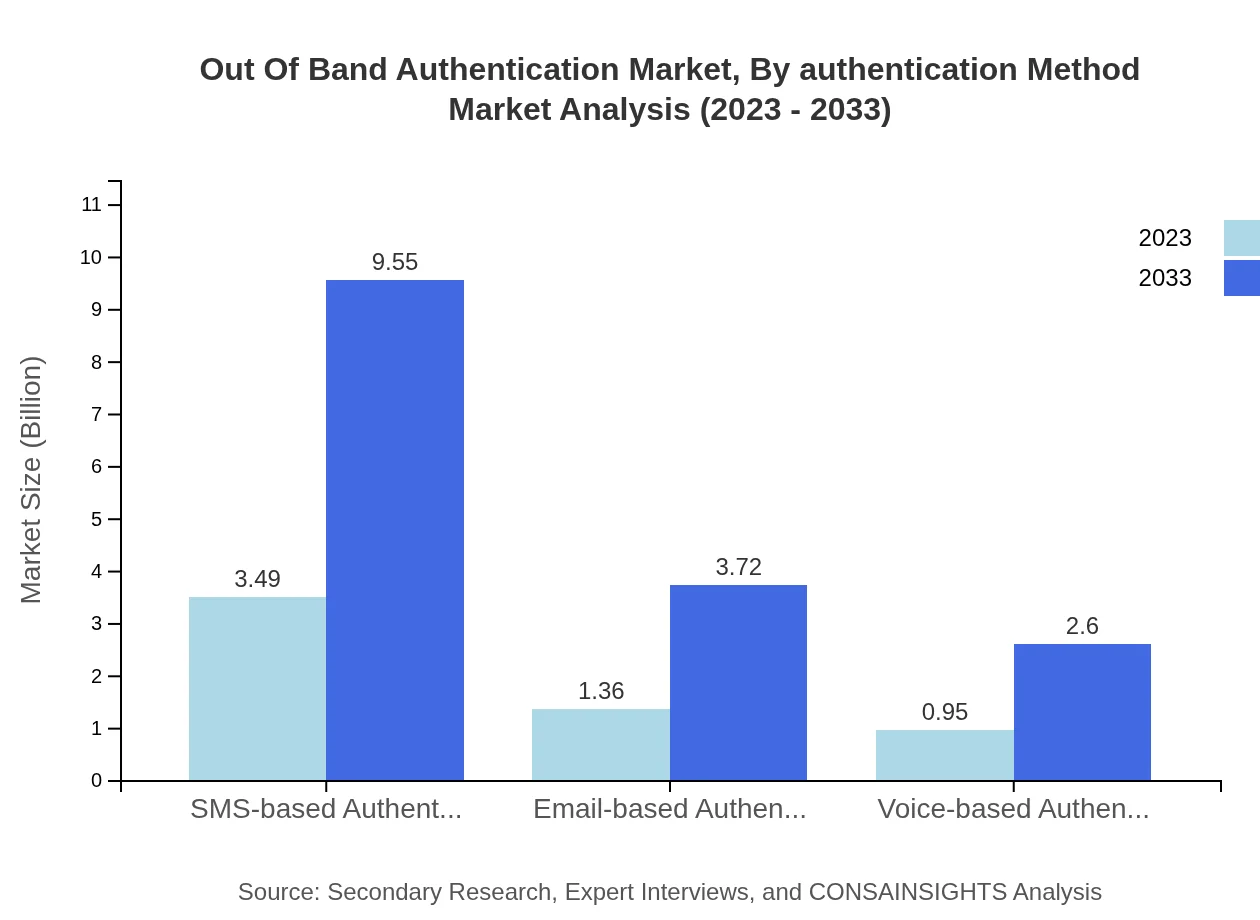
The Out-of-Band Authentication market segmented by authentication method shows varying performances across technologies. OTP technology currently leads with a market size of 2.96 billion USD in 2023 and is expected to reach 8.11 billion USD by 2033, holding a 51.09% market share. SMS-based authentication follows with 3.49 billion USD growing to 9.55 billion USD, while push notifications hold a significant 24.21% market share.
Out Of Band Authentication Market Analysis By End User
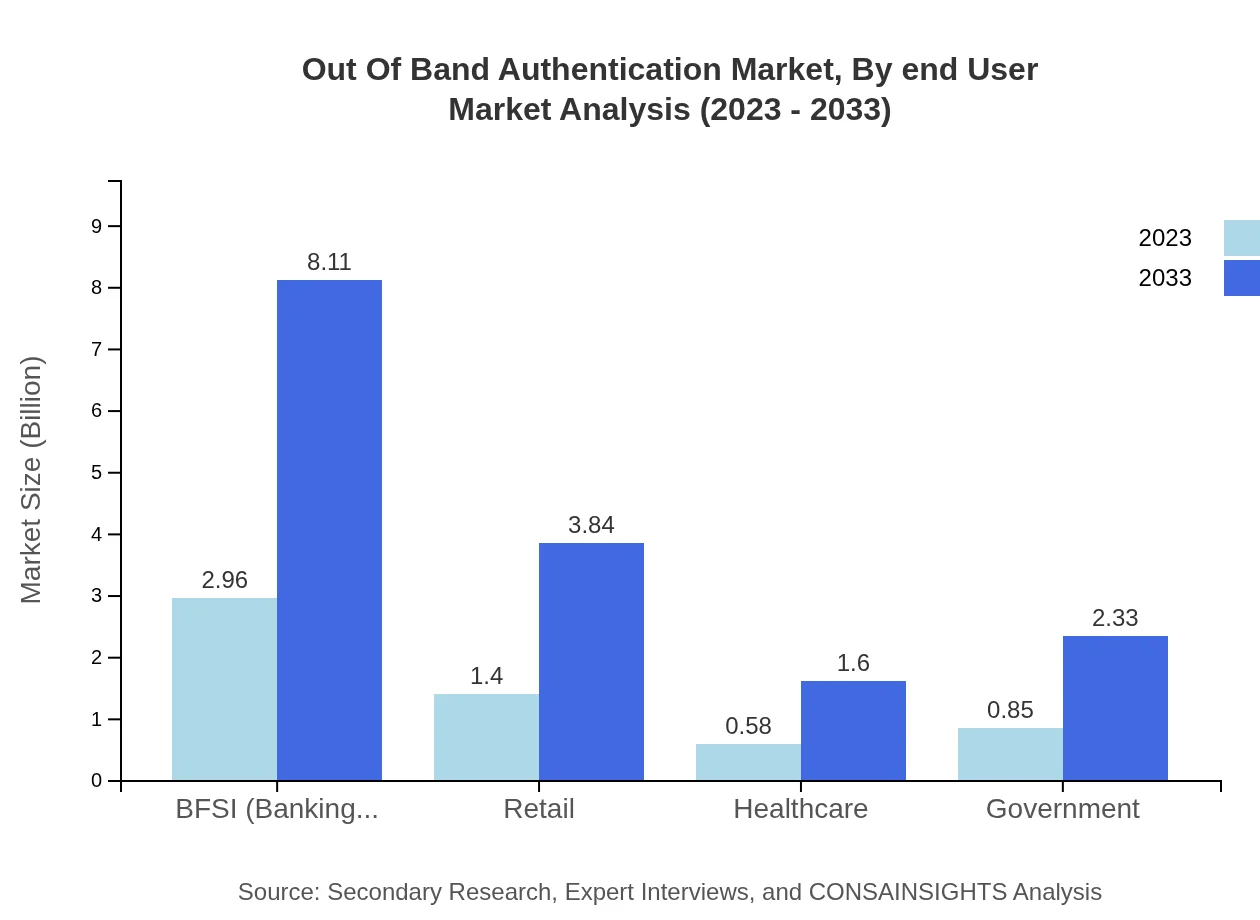
The BFSI sector dominates the Out-of-Band Authentication market, with a size of 2.96 billion USD in 2023, expected to grow to 8.11 billion USD by 2033 (51.09% share). Retail and healthcare follow, holding 24.21% and 10.05% shares, respectively, as these sectors increasingly recognize the importance of secure transactions.
Out Of Band Authentication Market Analysis By Technology
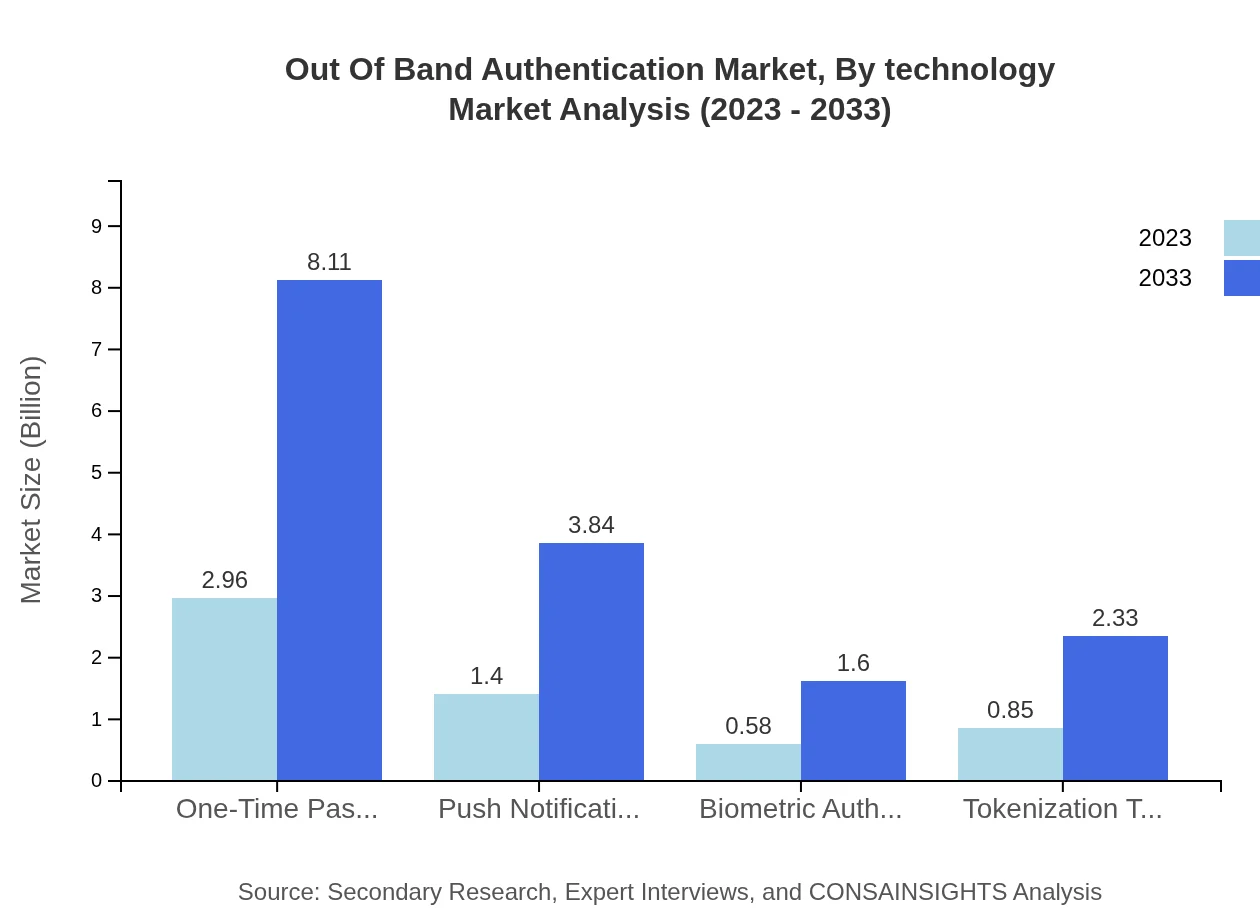
The primary technologies utilized in Out-of-Band Authentication include OTP, SMS-based solutions, push notifications, and biometric techniques. SMS-based authentication is the largest segment, growing from 3.49 billion USD in 2023 to 9.55 billion USD by 2033, capturing 60.18% of the market share. Each technology offers different advantages in securing transactions and safeguarding user identities.
Out Of Band Authentication Market Analysis By Region
Market analysis by region shows North America leading with a 41.09% share in 2023, projected to maintain this position by 2033. Europe and Asia-Pacific follow, holding 24.35% and 13.97% shares, respectively. Emerging markets in Latin America and the Middle East & Africa demonstrate rapid growth due to increasing digital reliance.
Out Of Band Authentication Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Out Of Band Authentication Industry
Duo Security:
A subsidiary of Cisco, Duo Security provides a comprehensive cloud-based platform that improves security with multi-factor authentication solutions.Okta:
Specializing in identity management, Okta offers a secure platform for companies to implement multifaceted authentication processes tailored to their specific needs.Authy:
Authy is notable for its ease of integration and is widely used for two-factor authentication services across various applications and platforms.Gemalto:
Now part of Thales, Gemalto provides a range of digital security services, including advanced authentication solutions that cater to sectors such as finance and telecommunications.We're grateful to work with incredible clients.









FAQs
What is the market size of Out-Of-Band Authentication?
The Out-Of-Band Authentication market is expected to grow from $5.8 billion in 2023 to an estimated size by 2033. It is projected to experience a Compound Annual Growth Rate (CAGR) of 10.2% during the forecast period.
What are the key market players or companies in this Out-Of-Band Authentication industry?
Key players in the Out-Of-Band Authentication industry include technology leaders and cybersecurity firms specializing in authentication solutions. These companies are actively enhancing their offerings to tackle evolving security challenges and meet diverse market needs.
What are the primary factors driving the growth in the Out-Of-Band Authentication industry?
The growth in the Out-Of-Band Authentication industry is driven by increasing cybersecurity threats, growing adoption of mobile and cloud computing, and a rising demand for secure transaction methods. Regulatory compliance mandates also significantly influence market expansion.
Which region is the fastest Growing in the Out-Of-Band Authentication?
The fastest-growing region for Out-Of-Band Authentication is North America, where the market is projected to increase from $1.97 billion in 2023 to $5.41 billion in 2033. Europe and the Asia Pacific also display significant growth potential.
Does ConsaInsights provide customized market report data for the Out-Of-Band Authentication industry?
Yes, ConsaInsights offers tailored market report data for the Out-Of-Band Authentication industry. Clients can request specific insights, data segments, and trend analyses to align with their strategic objectives and business models.
What deliverables can I expect from this Out-Of-Band Authentication market research project?
From the Out-Of-Band Authentication market research project, expect comprehensive reports detailing market size, growth forecasts, competitive analysis, and regional assessments, along with strategic recommendations and segmentation insights.
What are the market trends of Out-Of-Band Authentication?
Current market trends in Out-Of-Band Authentication include a focus on multi-factor authentication solutions, growing integration with advanced biometrics, and increased reliance on mobile authentication technologies as businesses seek enhanced security measures.