Privileged Identity Management Market Report
Published Date: 31 January 2026 | Report Code: privileged-identity-management
Privileged Identity Management Market Size, Share, Industry Trends and Forecast to 2033
This report provides an in-depth analysis of the Privileged Identity Management market, covering various segments and regional insights from 2023 to 2033, including market size, trends, forecasts, and key players.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
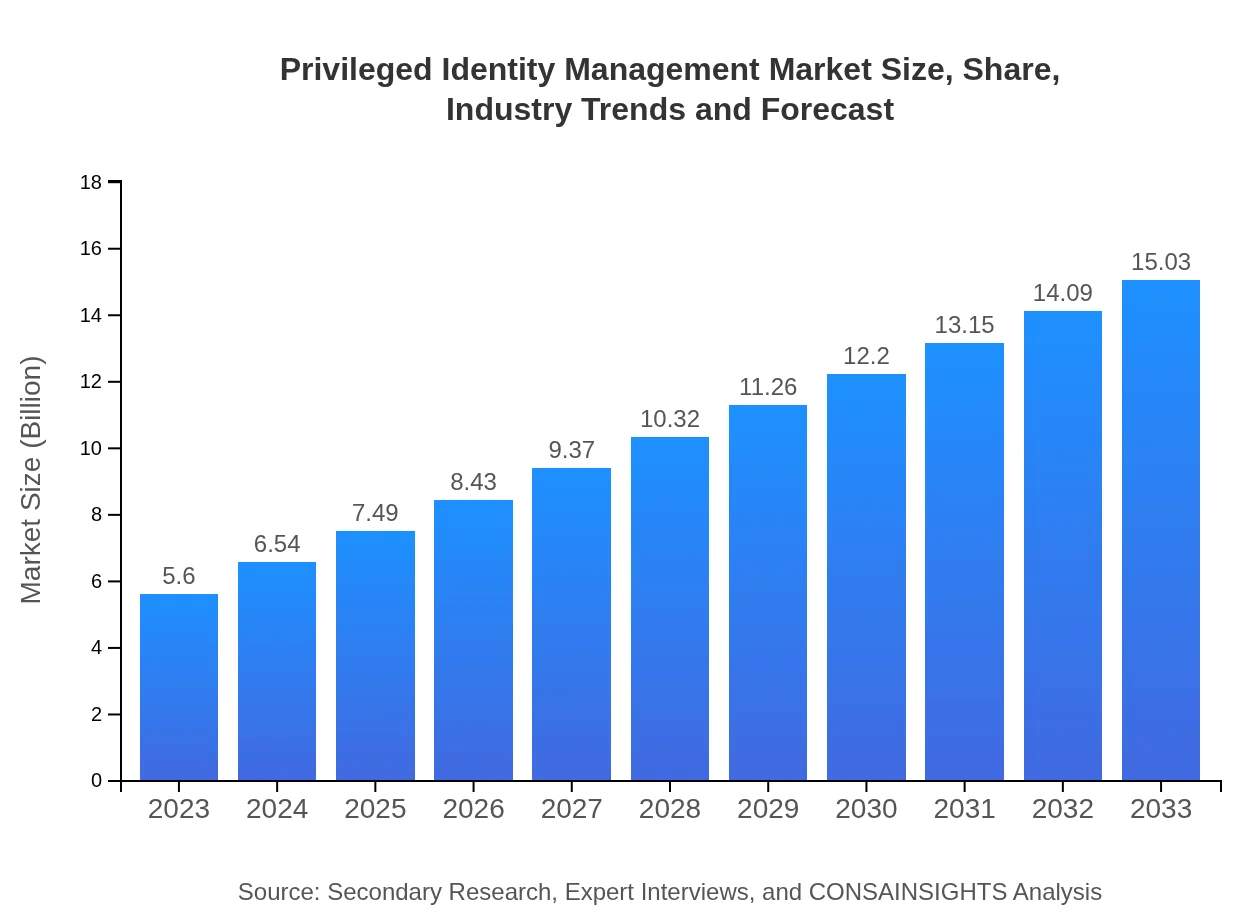
| 2023 Market Size | $5.60 Billion |
| CAGR (2023-2033) | 10% |
| 2033 Market Size | $15.03 Billion |
| Top Companies | CyberArk Software, SailPoint Technologies |
| Last Modified Date | 31 January 2026 |
Privileged Identity Management Market Overview
Customize Privileged Identity Management Market Report market research report
- ✔ Get in-depth analysis of Privileged Identity Management market size, growth, and forecasts.
- ✔ Understand Privileged Identity Management's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Privileged Identity Management
What is the Market Size & CAGR of Privileged Identity Management market in 2033?
Privileged Identity Management Industry Analysis
Privileged Identity Management Market Segmentation and Scope
Tell us your focus area and get a customized research report.
Privileged Identity Management Market Analysis Report by Region
Europe Privileged Identity Management Market Report:
Europe's market is projected to grow from USD 1.69 billion in 2023 to USD 4.55 billion in 2033. This region benefits from stringent data protection rules like GDPR, pushing organizations to invest heavily in PIM solutions.Asia Pacific Privileged Identity Management Market Report:
The Asia Pacific region is projected to witness substantial growth from USD 1.21 billion in 2023 to USD 3.24 billion in 2033. This increase is fueled by rapid digital transformation and rising cyber threats, prompting organizations to deploy robust PIM strategies.North America Privileged Identity Management Market Report:
In North America, the PIM market is expected to grow from USD 1.81 billion in 2023 to USD 4.85 billion in 2033. The prevalence of advanced threats and strict regulatory requirements make this region a key player in PIM implementation.South America Privileged Identity Management Market Report:
The South American market, though smaller, is estimated to grow from USD 0.24 billion in 2023 to USD 0.65 billion in 2033. The increasing focus on security regulations in countries like Brazil is driving the adoption of PIM solutions.Middle East & Africa Privileged Identity Management Market Report:
The Middle East and Africa are anticipated to grow from USD 0.65 billion in 2023 to USD 1.74 billion in 2033, driven by the increasing adoption of digital technologies across sectors.Tell us your focus area and get a customized research report.
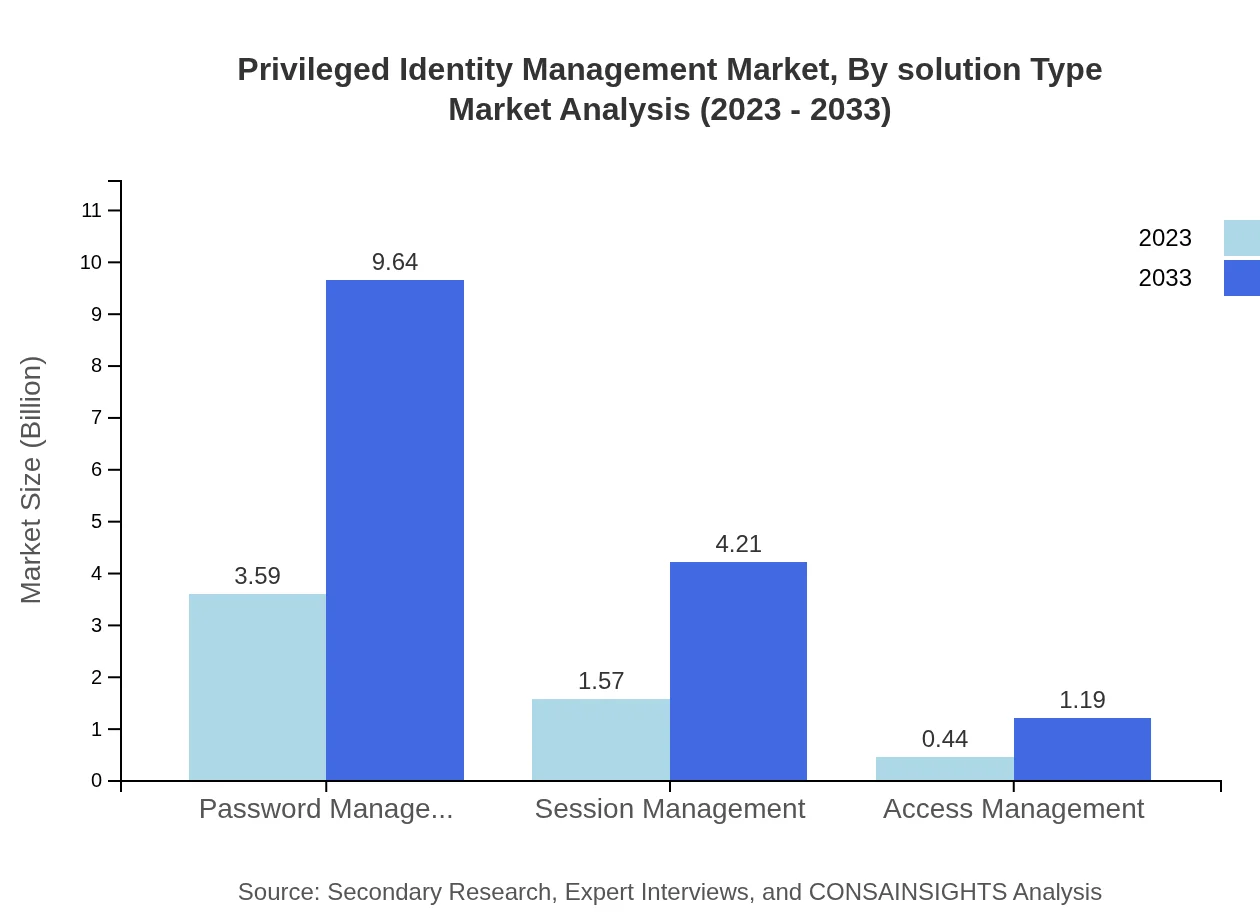
Privileged Identity Management Market Analysis By Solution Type
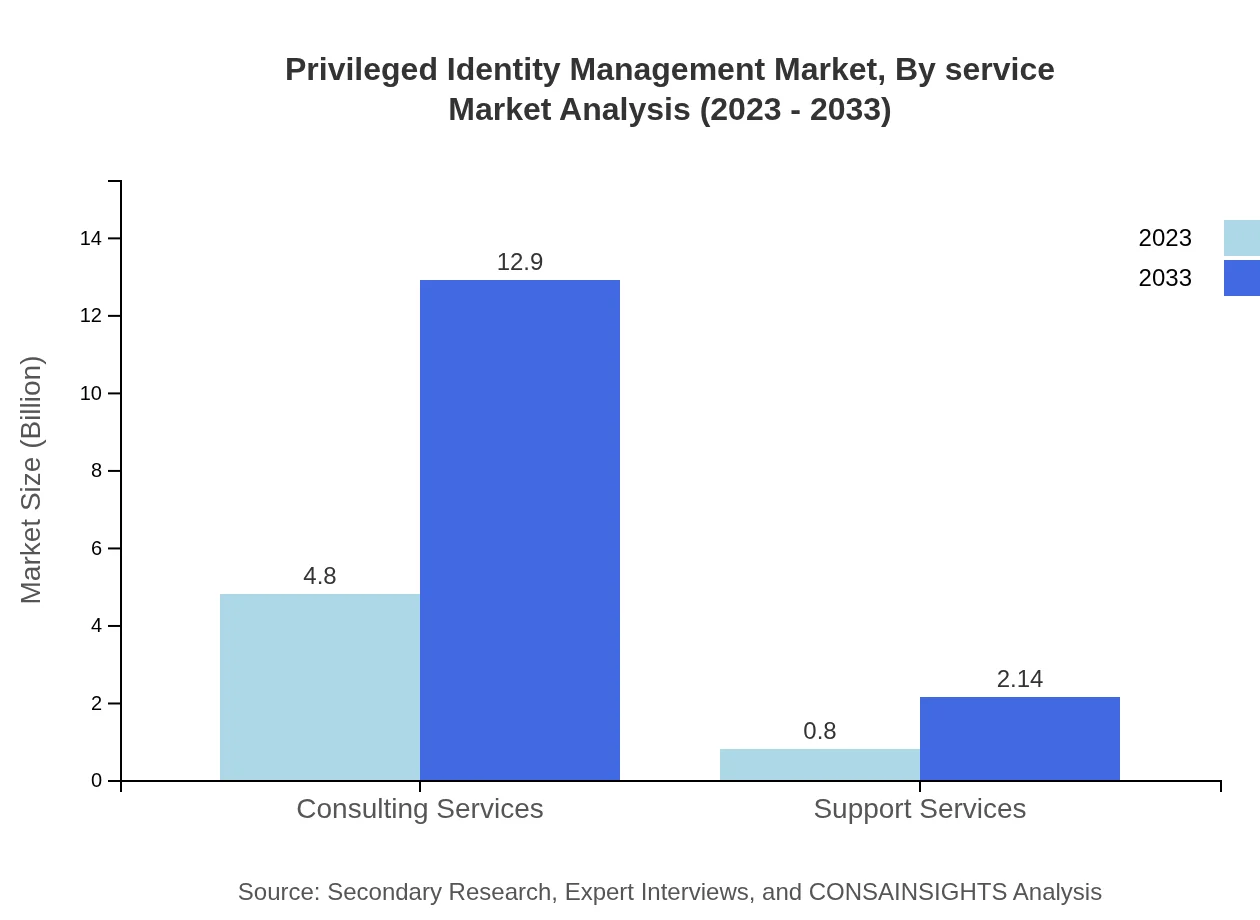
The solution type segment reflects a significant allocation of resources, with consulting services leading the market. In 2023, consulting is valued at USD 4.80 billion and is expected to rise to USD 12.90 billion by 2033. Support services follow closely behind, with an increase from USD 0.80 billion in 2023 to USD 2.14 billion in 2033. Password management and session management are critical areas, projected to grow consistently due to their importance in user authentication processes.
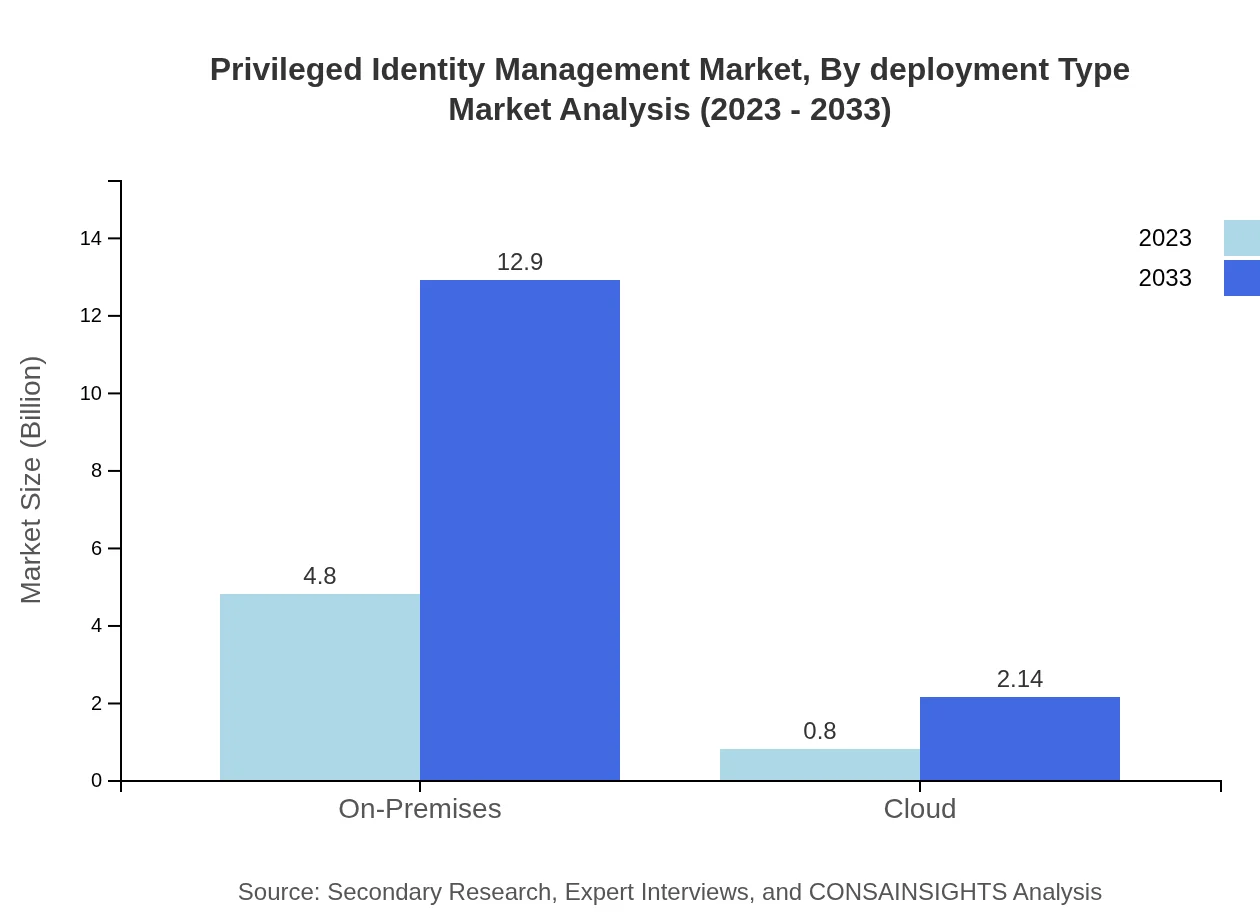
Privileged Identity Management Market Analysis By Deployment Type
The deployment segment is dominated by on-premises solutions, which are projected to grow significantly from USD 4.80 billion in 2023 to USD 12.90 billion in 2033, constituting 85.79% of the market share. Conversely, cloud solutions are gaining traction, expected to rise from USD 0.80 billion to USD 2.14 billion, reflecting a growing trend toward flexible and scalable security operations.
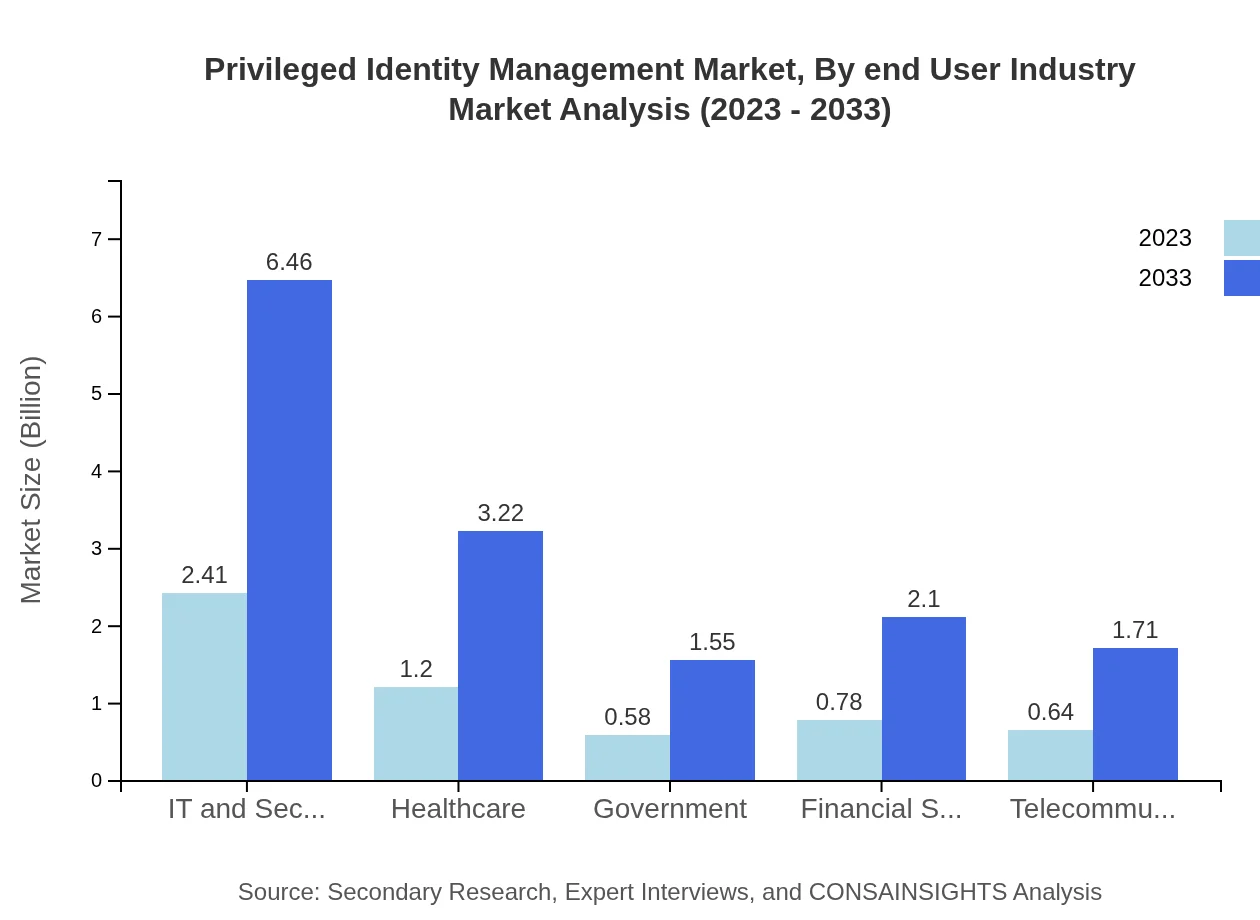
Privileged Identity Management Market Analysis By End User Industry
Key industries investing in PIM solutions include IT and security, which represent 42.97% of the market. The healthcare sector, with anticipated growth from USD 1.20 billion to USD 3.22 billion, also emphasizes securing sensitive patient data while complying with strict regulations. Government and financial services are other key sectors driving market growth.
Privileged Identity Management Market Analysis By Service
Service offerings play a crucial role in the PIM landscape, highlighted by consulting and support services, which together contribute a significant portion of the market. Consulting services are projected to dominate with nearly 85.79% market share, while support services are essential for maintaining effective PIM frameworks across organizations.
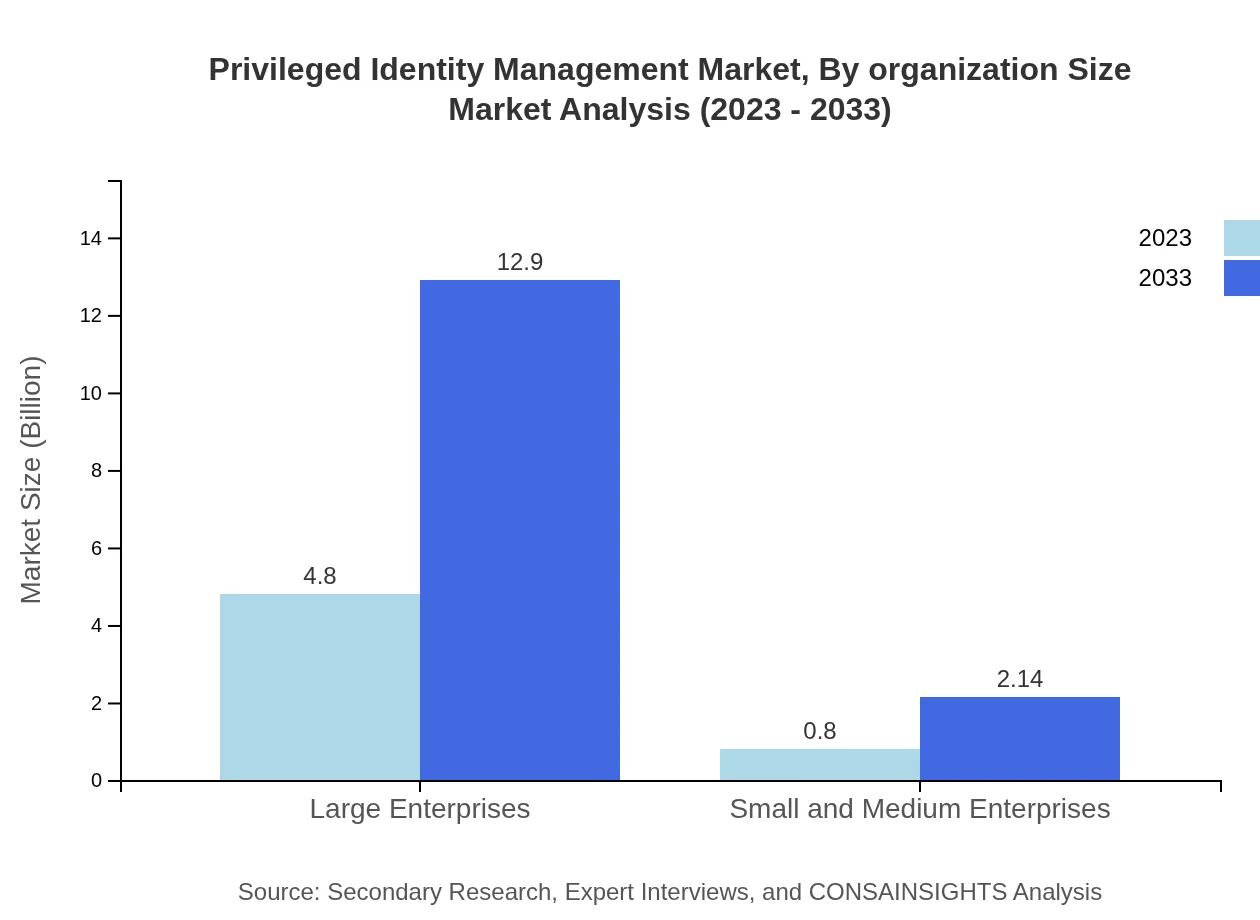
Privileged Identity Management Market Analysis By Organization Size
Large enterprises are the primary consumers of PIM solutions, accounting for an impressive 85.79% share of the market. Smaller organizations, while less dominant in market share, are increasingly adopting PIM measures as security awareness heightens, with a projected growth from USD 0.80 billion to USD 2.14 billion by 2033.
Privileged Identity Management Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Privileged Identity Management Industry
CyberArk Software:
CyberArk provides comprehensive identity security solutions focused on mitigating risks associated with privileged account access, including innovative password management and session monitoring technologies.SailPoint Technologies:
SailPoint specializes in identity governance and administration, offering advanced technologies for managing user identities and access rights efficiently across various applications.We're grateful to work with incredible clients.









FAQs
What is the market size of privileged Identity Management?
The privileged identity management market is currently valued at approximately $5.6 billion, with a projected CAGR of 10% through 2033. This growth invites extensive investment and innovation in securing privileged accounts and access.
What are the key market players or companies in this privileged Identity Management industry?
Key players in the privileged identity management sector include established firms known for their security solutions. Market leaders continuously expand their offerings to enhance security postures across various industries.
What are the primary factors driving the growth in the privileged Identity Management industry?
Growth in the privileged identity management industry is propelled by increasing cyber threats, regulatory compliance requirements, and the adoption of cloud services, compelling organizations to secure privileged access effectively.
Which region is the fastest Growing in the privileged Identity Management?
The fastest-growing region for privileged identity management from 2023 to 2033 is Europe, projected to grow from approximately $1.69 billion to $4.55 billion, driven by stringent security regulations and growth in digital transformation.
Does ConsaInsights provide customized market report data for the privileged Identity Management industry?
Yes, ConsaInsights offers tailored market report data for the privileged identity management industry, ensuring that clients receive valuable insights tailored to their specific needs and objectives.
What deliverables can I expect from this privileged Identity Management market research project?
Expect comprehensive deliverables, including market size reports, trend analyses, competitor insights, regional breakdowns, and strategic recommendations to aid in informed decision-making within the privileged identity management space.
What are the market trends of privileged Identity Management?
Current market trends indicate a significant shift towards multifactor authentication and AI-driven security solutions, with increasing investments in consulting and support services to enhance identity protection mechanisms.