Risk Based Authentication Market Report
Published Date: 31 January 2026 | Report Code: risk-based-authentication
Risk Based Authentication Market Size, Share, Industry Trends and Forecast to 2033
This report provides an in-depth analysis of the Risk Based Authentication market from 2023 to 2033, covering market size, trends, technological advancements, and regional insights. It aims to equip stakeholders with valuable insights to navigate the evolving landscape of digital security.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
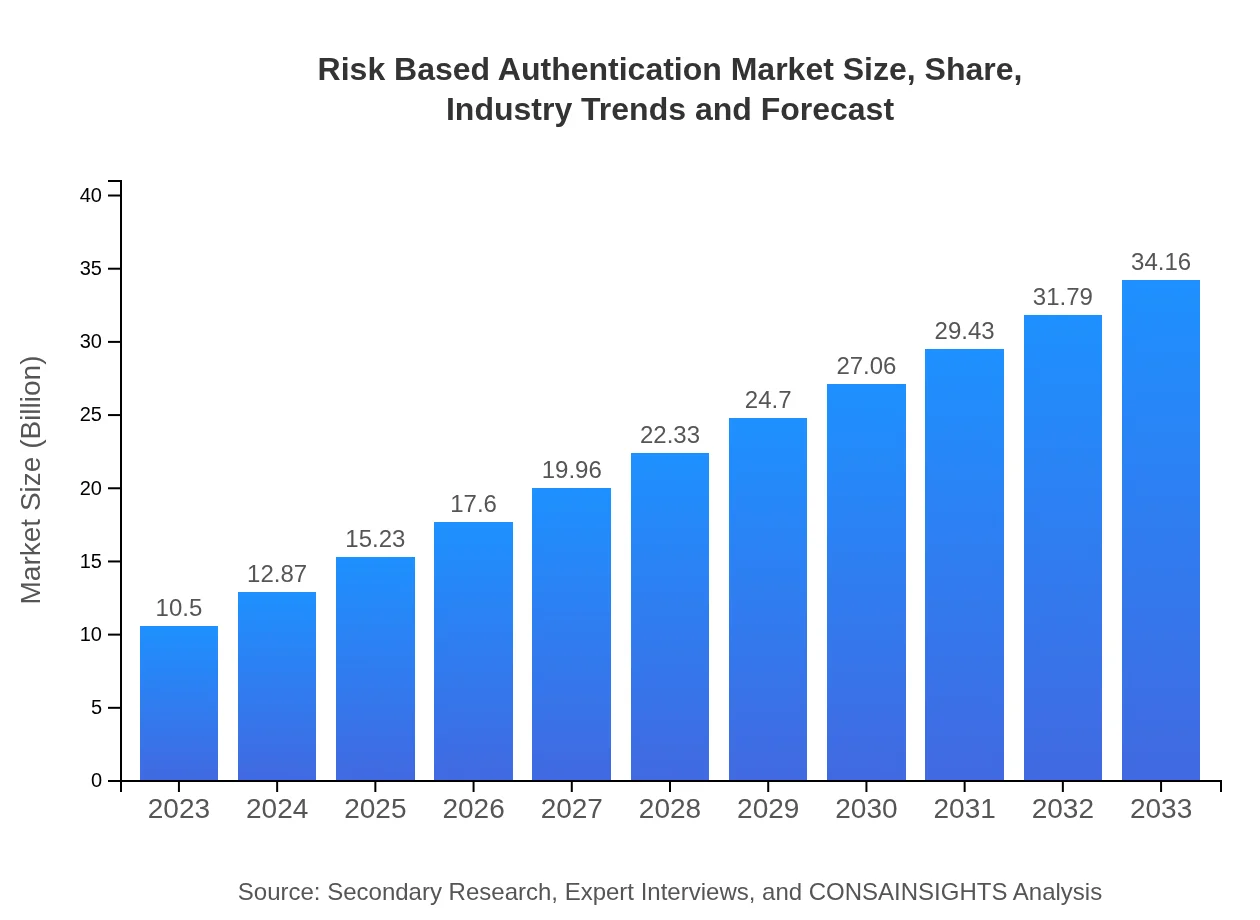
| 2023 Market Size | $10.50 Billion |
| CAGR (2023-2033) | 12% |
| 2033 Market Size | $34.16 Billion |
| Top Companies | IBM Corporation, RSA Security LLC, Auth0 (Okta, Inc.), Duo Security (Cisco) |
| Last Modified Date | 31 January 2026 |
Risk Based Authentication Market Overview
Customize Risk Based Authentication Market Report market research report
- ✔ Get in-depth analysis of Risk Based Authentication market size, growth, and forecasts.
- ✔ Understand Risk Based Authentication's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Risk Based Authentication
What is the Market Size & CAGR of Risk Based Authentication market in 2023?
Risk Based Authentication Industry Analysis
Risk Based Authentication Market Segmentation and Scope
Tell us your focus area and get a customized research report.
Risk Based Authentication Market Analysis Report by Region
Europe Risk Based Authentication Market Report:
Europe's RBA market is anticipated to grow from USD 2.65 billion in 2023 to USD 8.62 billion by 2033. The region is witnessing increased adoption of RBA technology to address GDPR compliance and protect user data, resulting in heightened investment in advanced authentication methods.Asia Pacific Risk Based Authentication Market Report:
In the Asia Pacific region, the RBA market is projected to grow from USD 2.01 billion in 2023 to USD 6.54 billion by 2033, reflecting substantial investment in cybersecurity by governments and large enterprises. Rapid digital transformation in countries like India and China, coupled with an increase in mobile banking activities, drives demand for advanced authentication solutions.North America Risk Based Authentication Market Report:
In North America, the market is forecast to expand from USD 3.84 billion in 2023 to USD 12.50 billion by 2033. With stringent regulatory frameworks and high rates of identity fraud, businesses are increasingly relying on RBA solutions to enhance security and compliance, driving substantial market growth.South America Risk Based Authentication Market Report:
The South American RBA market is expected to rise from USD 0.77 billion in 2023 to USD 2.51 billion by 2033. Enhanced digital banking solutions and a growing need for secure e-commerce platforms push firms to adopt RBA strategies to mitigate risks associated with rising cyber threats.Middle East & Africa Risk Based Authentication Market Report:
The Middle East and Africa RBA market is expected to grow from USD 1.23 billion in 2023 to USD 3.99 billion by 2033. Factors such as increasing cyber threats and the region's push for digitization and modernization in several sectors are contributing to this growth.Tell us your focus area and get a customized research report.
Risk Based Authentication Market Analysis By Authentication Method
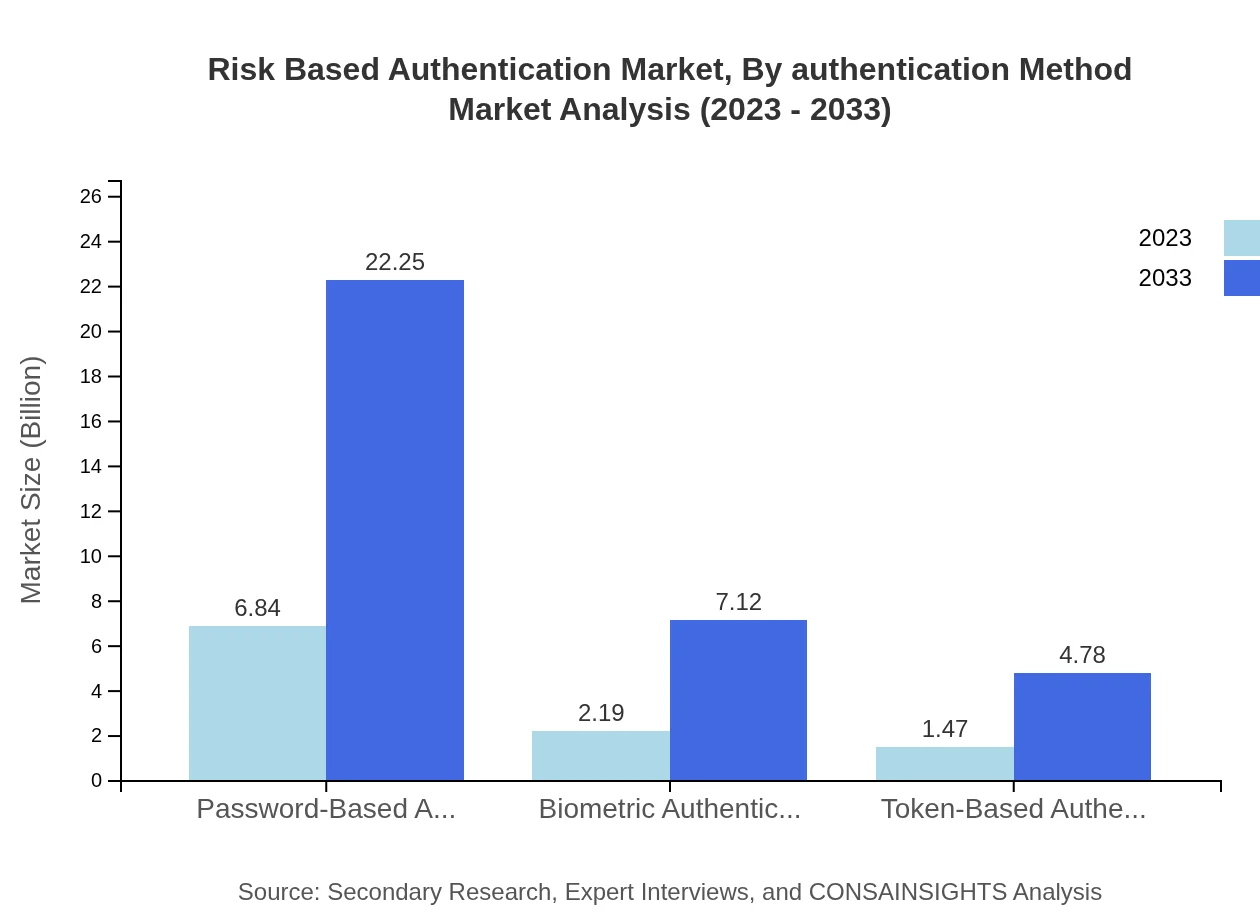
The Risk-Based Authentication Market is primarily driven by various authentication methods, with the market size for password-based authentication at USD 6.84 billion in 2023 and expected to reach USD 22.25 billion by 2033, representing a dominant share of 65.15%. Other methods include biometric authentication, projected to grow from USD 2.19 billion (20.85% share) to USD 7.12 billion, and token-based authentication, expected to grow from USD 1.47 billion to USD 4.78 billion.
Risk Based Authentication Market Analysis By Industry
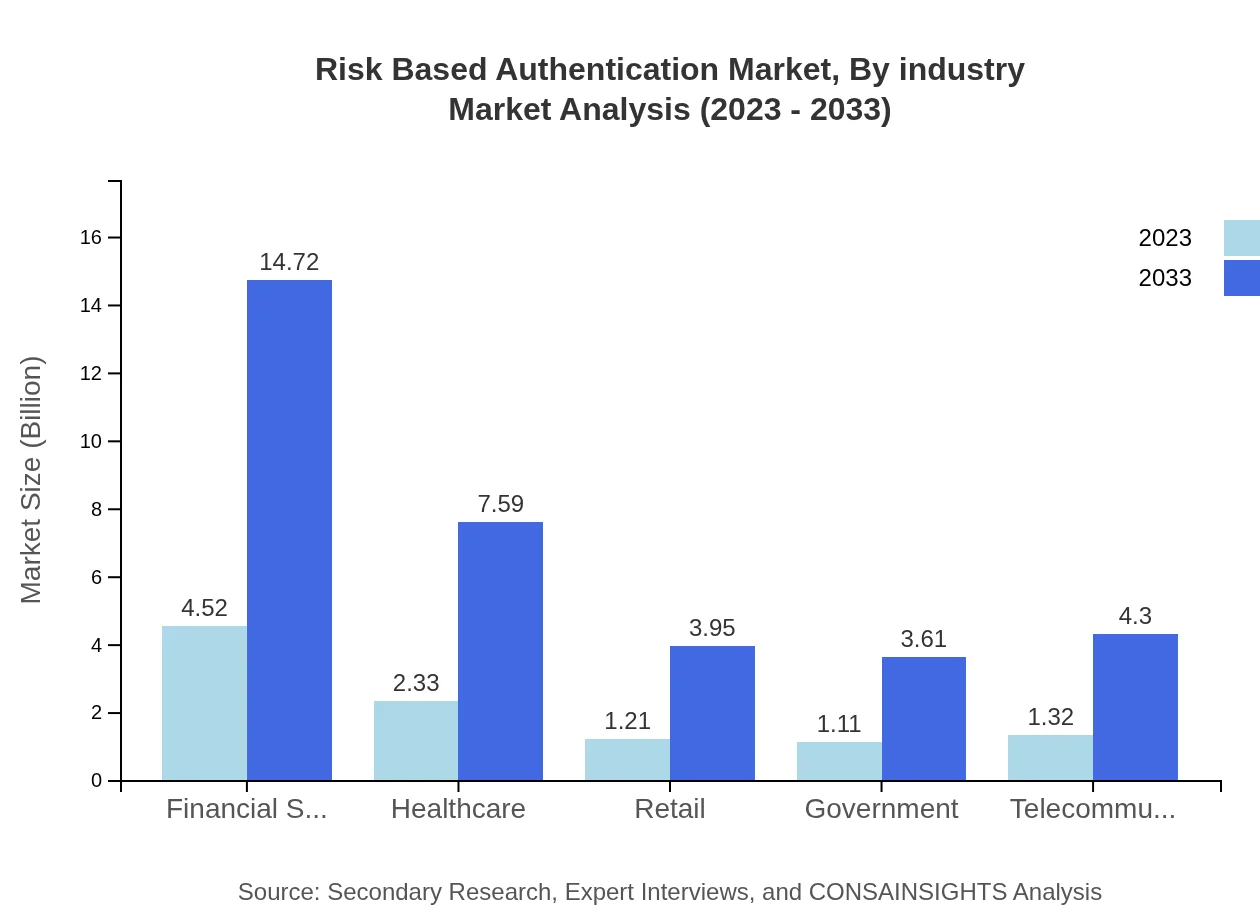
Industries utilizing RBA solutions show varied market sizes, with financial services dominating the segment at USD 4.52 billion in 2023, projected to grow to USD 14.72 billion, holding a share of 43.08%. Healthcare is also significant, anticipated to grow from USD 2.33 billion to USD 7.59 billion (22.21% share). Other industries like retail, government, and telecommunications are expanding their RBA investments to secure sensitive data.
Risk Based Authentication Market Analysis By Deployment Model
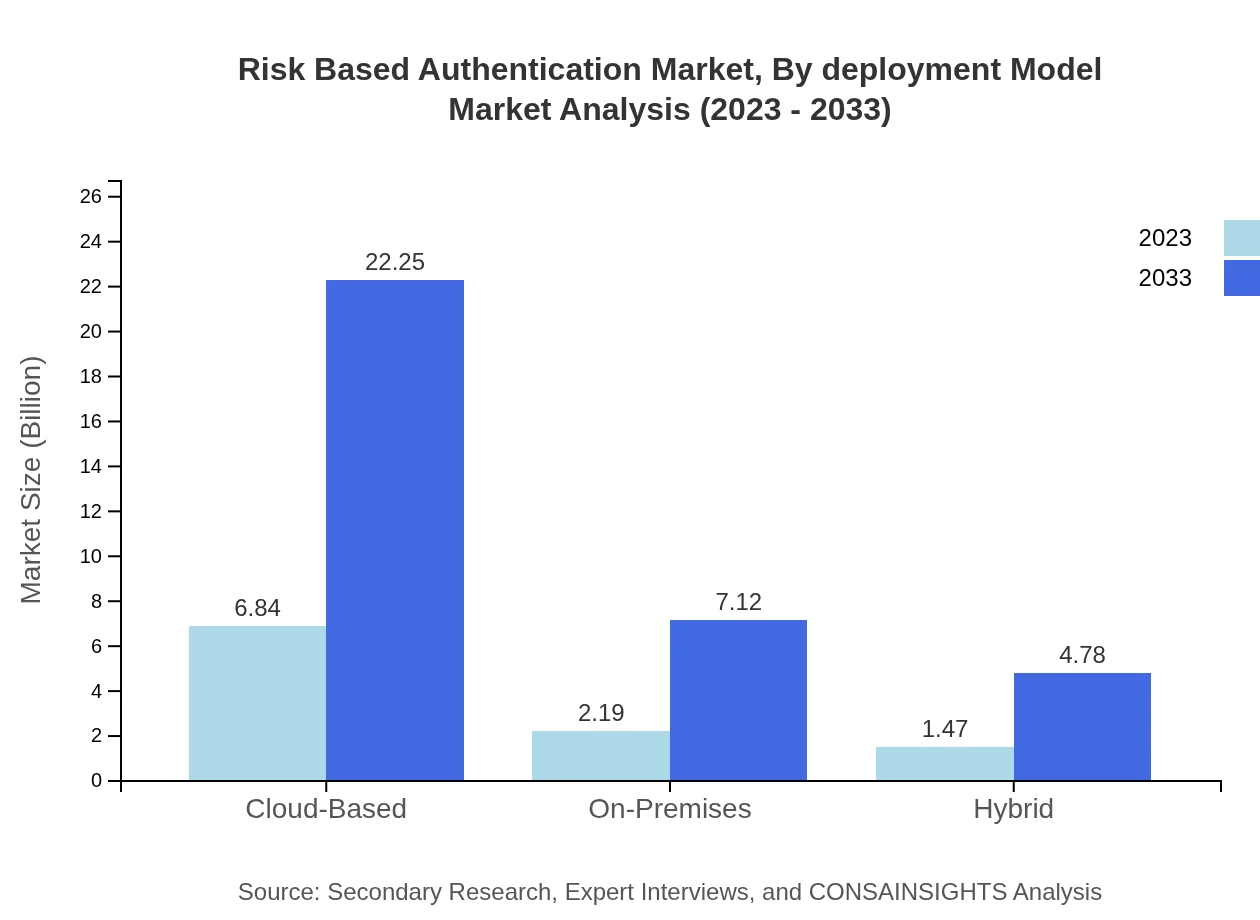
The cloud-based deployment model is expected to witness substantial growth from USD 6.84 billion in 2023 to USD 22.25 billion by 2033, maintaining a 65.15% market share. On-premises models are predicted to grow from USD 2.19 billion to USD 7.12 billion (20.85% share), while hybrid models will move from USD 1.47 billion to USD 4.78 billion, reflecting organizational preference for flexibility in deployment.
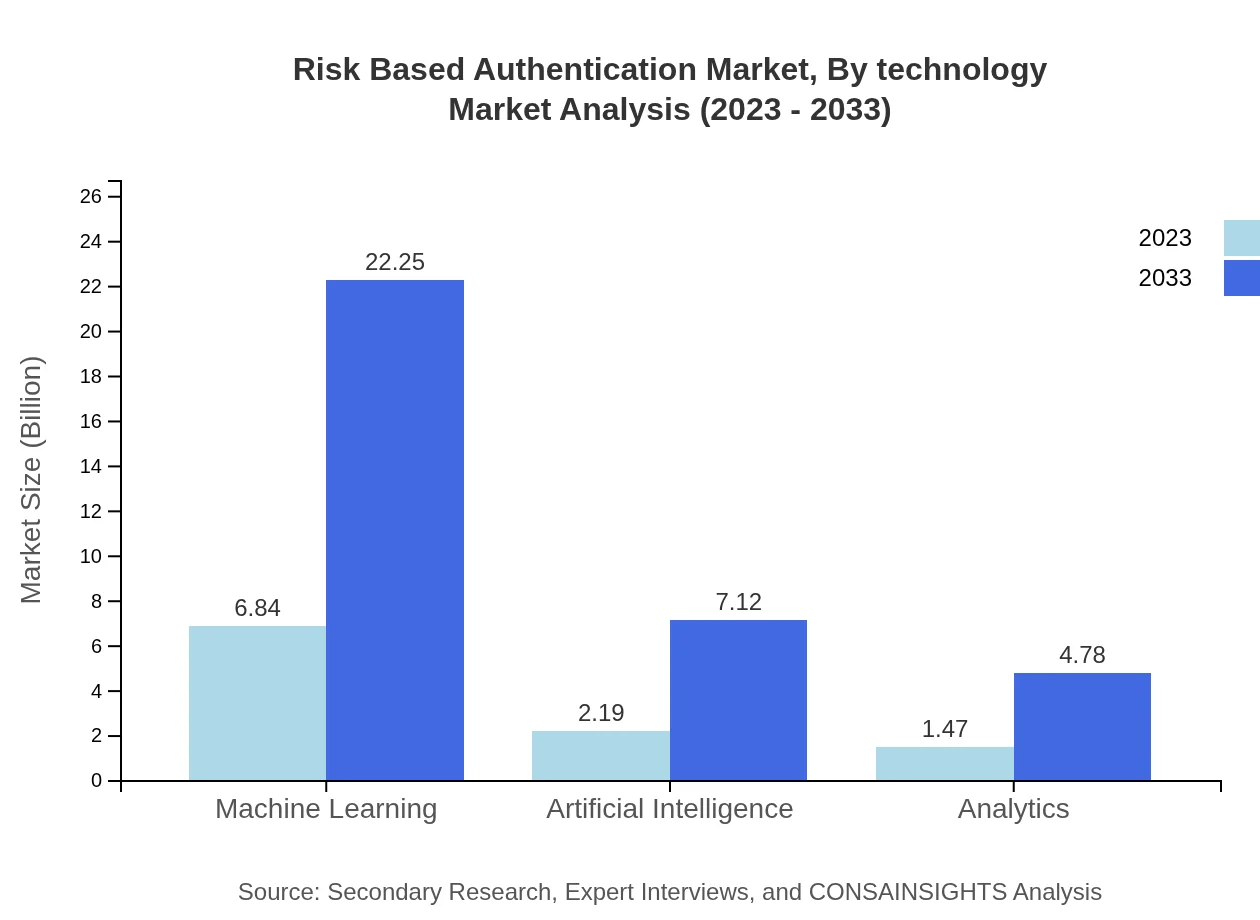
Risk Based Authentication Market Analysis By Technology
Technological advancements are reshaping the RBA market, with machine learning leading innovation at a size of USD 6.84 billion in 2023, expected to reach USD 22.25 billion (65.15% share). AI-driven authentication follows closely, projected to grow from USD 2.19 billion to USD 7.12 billion (20.85% share), contributing to enhanced user behavior analysis and risk assessment.
Risk Based Authentication Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Risk Based Authentication Industry
IBM Corporation:
IBM offers an extensive suite of security solutions, including advanced RBA technology that integrates AI and machine learning for real-time threat detection.RSA Security LLC:
RSA provides industry-leading RBA solutions that prioritize user experience while providing fraud detection and risk management capabilities.Auth0 (Okta, Inc.):
Auth0 delivers a flexible, scalable RBA platform that protects applications through multi-factor authentication and adaptive security measures.Duo Security (Cisco):
Duo Security offers cloud-based RBA solutions focusing on zero-trust security principles to secure users and devices within organizations.We're grateful to work with incredible clients.









FAQs
What is the market size of risk Based Authentication?
The global Risk-Based Authentication market is estimated to reach approximately $10.5 billion by 2033, growing at a CAGR of 12% from 2023. This significant growth reflects increasing demand for security solutions in various sectors.
What are the key market players or companies in this risk Based Authentication industry?
Key players in the Risk-Based Authentication market include leading technology companies specializing in cybersecurity solutions, including IBM, RSA Security, Okta, and Microsoft, among others, which are constantly innovating to enhance security solutions.
What are the primary factors driving the growth in the risk Based Authentication industry?
The growth in the risk-based authentication industry is driven by rising cyber threats, increasing digital transactions, the growing adoption of cloud-based solutions, and regulatory compliance requirements to safeguard sensitive data.
Which region is the fastest Growing in the risk Based Authentication?
North America is the fastest-growing region in the risk-based authentication market, projected to expand from $3.84 billion in 2023 to $12.50 billion by 2033, due to heightened cybersecurity concerns and advanced technology adoption.
Does ConsaInsights provide customized market report data for the risk Based Authentication industry?
Yes, ConsaInsights offers tailored market report data for the risk-based authentication industry, enabling organizations to acquire insights specific to their needs and make informed strategic decisions based on detailed market analysis.
What deliverables can I expect from this risk Based Authentication market research project?
Deliverables from the risk-based authentication market research project include comprehensive market analysis reports, competitive landscape assessments, segment-wise evaluations, and regional insights, all aimed at supporting strategic planning and decision-making.
What are the market trends of risk Based Authentication?
Current market trends in risk-based authentication include integration of AI and machine learning for enhanced security, increased investment in biometric authentication methods, and a shift towards cloud-based solutions to optimize access management.