Security And Vulnerability Management Market Report
Published Date: 31 January 2026 | Report Code: security-and-vulnerability-management
Security And Vulnerability Management Market Size, Share, Industry Trends and Forecast to 2033
This report provides an in-depth analysis of the Security and Vulnerability Management market, covering market trends, sizes, and growth forecasts from 2023 to 2033. It offers insights into regional performances and detailed evaluations of various segments within the industry.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
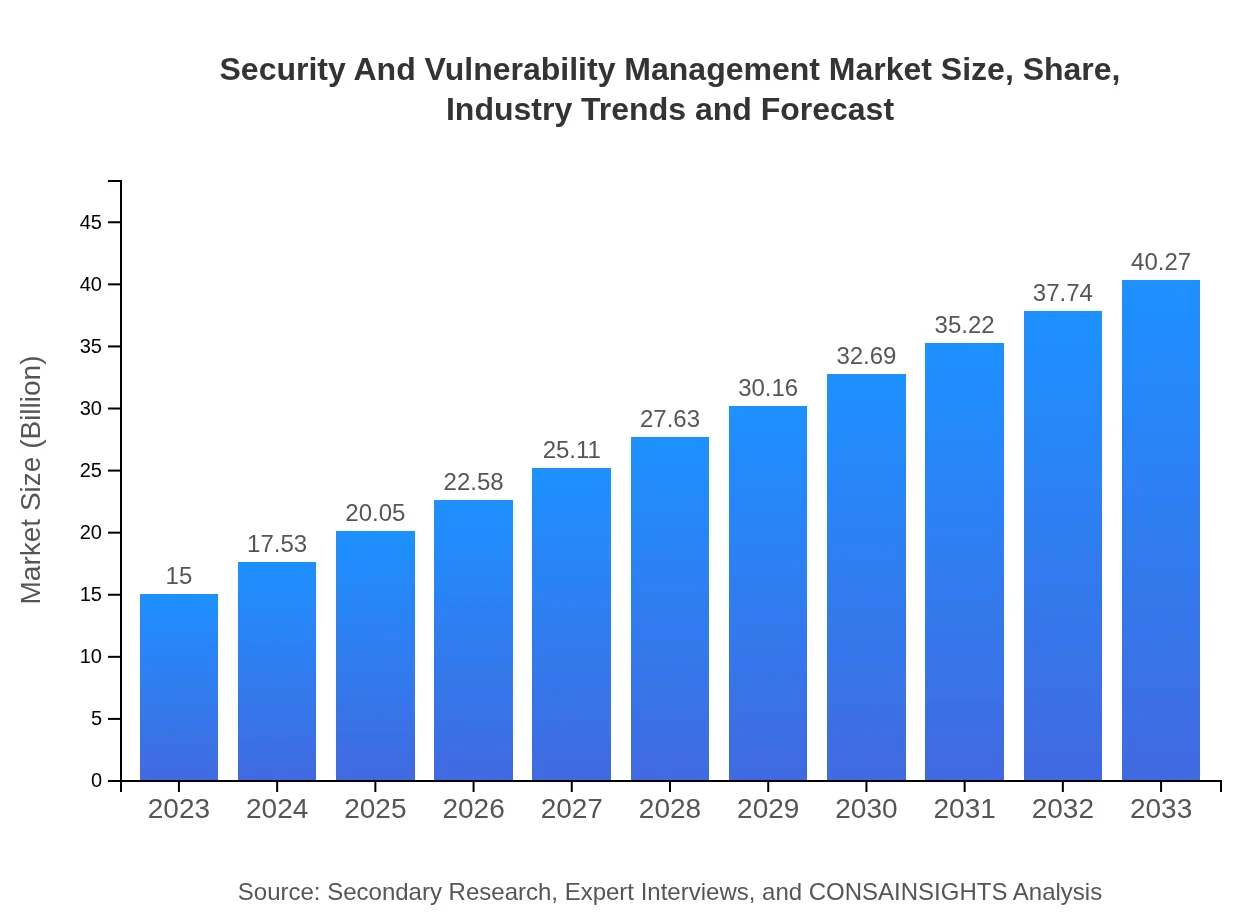
| 2023 Market Size | $15.00 Billion |
| CAGR (2023-2033) | 10% |
| 2033 Market Size | $40.27 Billion |
| Top Companies | Palo Alto Networks, McAfee, Symantec, Fortinet, Trend Micro |
| Last Modified Date | 31 January 2026 |
Security And Vulnerability Management Market Overview
Customize Security And Vulnerability Management Market Report market research report
- ✔ Get in-depth analysis of Security And Vulnerability Management market size, growth, and forecasts.
- ✔ Understand Security And Vulnerability Management's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Security And Vulnerability Management
What is the Market Size & CAGR of Security And Vulnerability Management Market in 2023?
Security And Vulnerability Management Industry Analysis
Security And Vulnerability Management Market Segmentation and Scope
Tell us your focus area and get a customized research report.
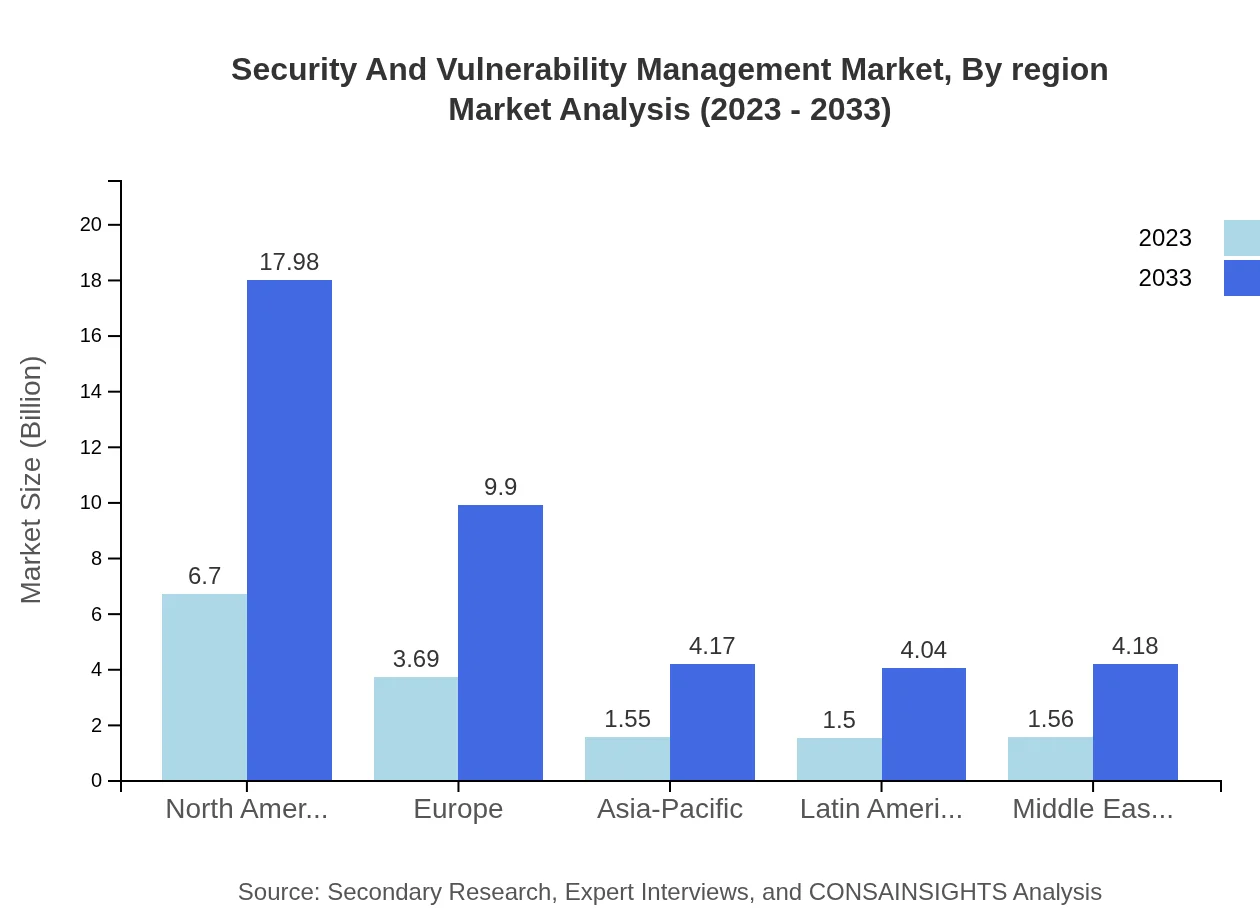
Security And Vulnerability Management Market Analysis Report by Region
Europe Security And Vulnerability Management Market Report:
The European market is set to increase from $5.05 billion in 2023 to $13.57 billion by 2033. The General Data Protection Regulation (GDPR) and other compliance frameworks will drive demand for robust security management solutions across various sectors, including finance and healthcare.Asia Pacific Security And Vulnerability Management Market Report:
In Asia Pacific, the Security and Vulnerability Management market is expected to grow from $2.72 billion in 2023 to $7.30 billion by 2033. With increasing investments in digital transformation and a rising number of cyber threats, countries in this region, especially China and India, are ramping up their security measures, contributing to this growth shift.North America Security And Vulnerability Management Market Report:
North America remains the largest market, projected to expand from $5.42 billion in 2023 to $14.54 billion by 2033. The presence of major technology companies and a strong regulatory environment encourages high levels of spending on security solutions, especially in the United States, where organizations face sophisticated cyber threats.South America Security And Vulnerability Management Market Report:
The South American market will grow from $1.32 billion in 2023 to $3.56 billion by 2033. Economic development and the increasing awareness of cybersecurity threats among businesses are driving security investments, especially in Brazil and Argentina, where digital infrastructure is rapidly evolving.Middle East & Africa Security And Vulnerability Management Market Report:
The Middle East and Africa market is expected to rise from $0.49 billion in 2023 to $1.31 billion by 2033. As organizations in these regions increasingly prioritize cybersecurity due to recent high-profile breaches, investment in vulnerability management solutions is expected to surge.Tell us your focus area and get a customized research report.
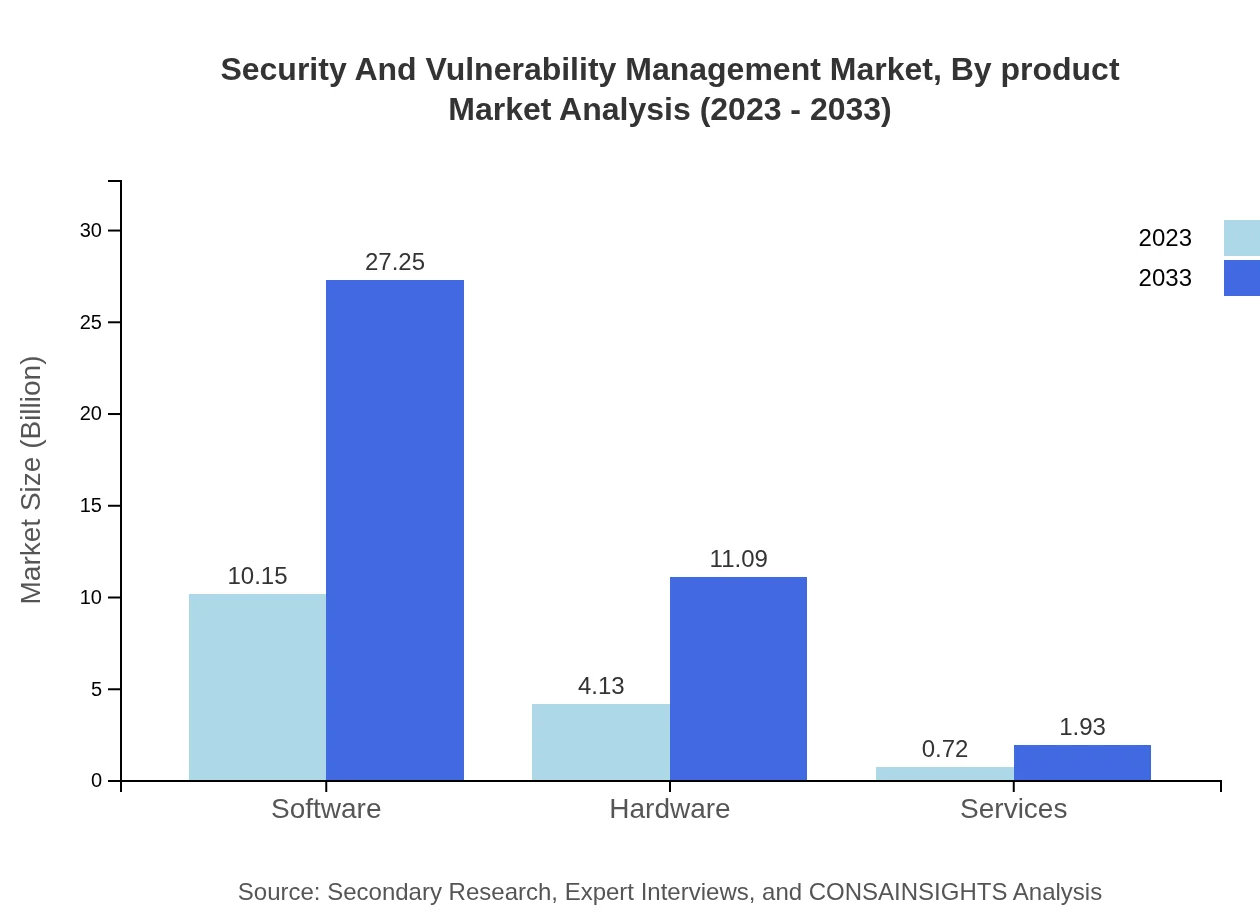
Security And Vulnerability Management Market Analysis By Product
The Security and Vulnerability Management market can be divided into three main product categories. Software holds the most substantial share at 67.66%, driven by advanced analytics and automation capabilities. Hardware solutions account for 27.54%, providing essential infrastructure for implementing security measures. Services, making up 4.80%, are increasingly important as businesses seek specialized expertise in threat management.
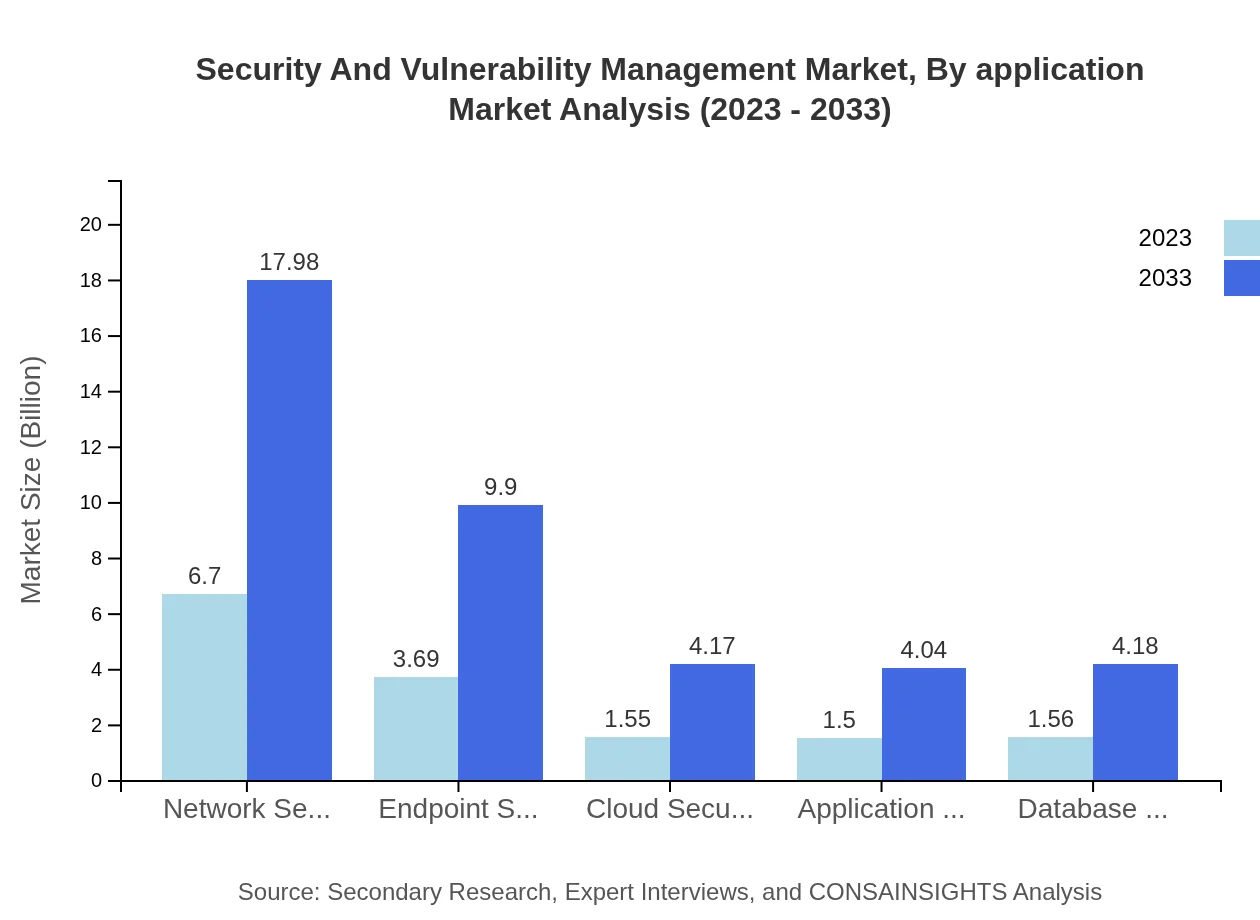
Security And Vulnerability Management Market Analysis By Application
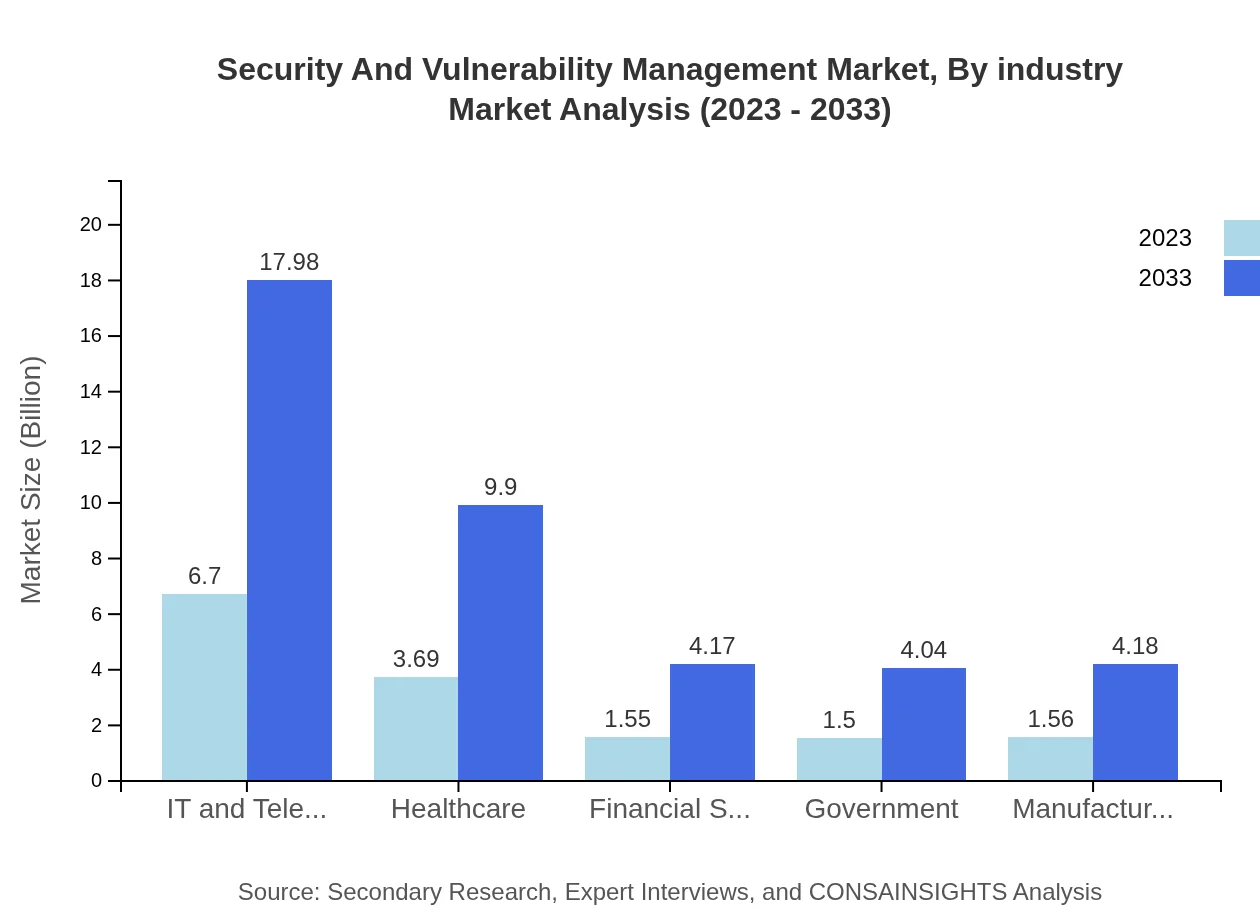
Key application sectors within the Security and Vulnerability Management market include IT and telecommunications (44.65% market share), healthcare (24.58%), financial services (10.35%), government (10.03%), and manufacturing (10.39%). Each sector increasingly relies on security management systems to protect sensitive information and ensure compliance.
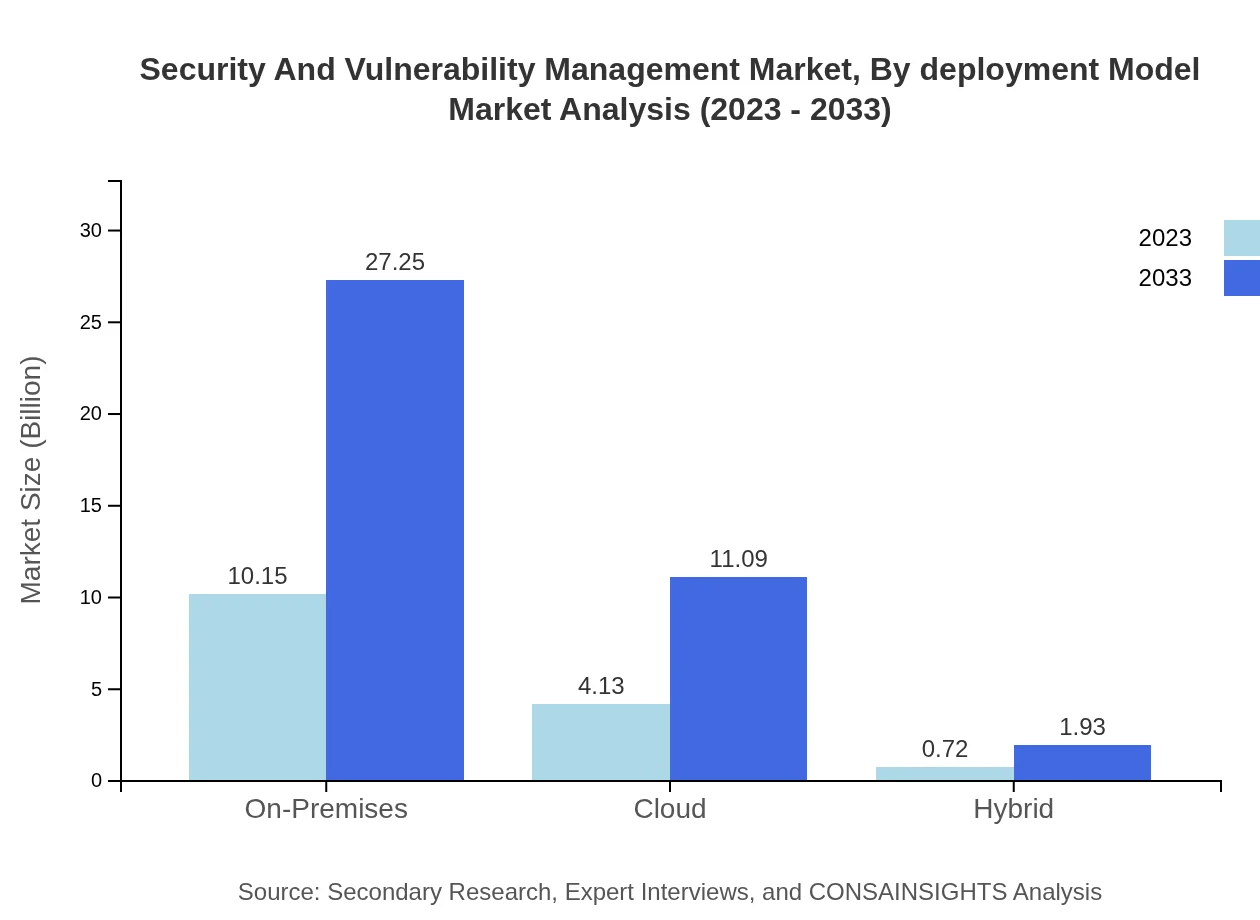
Security And Vulnerability Management Market Analysis By Deployment Model
Deployment models in the market include on-premises (67.66%), cloud (27.54%), and hybrid (4.80%). On-premises solutions remain popular for sensitive environments, while cloud deployments are gaining traction due to their flexibility and scalability, particularly among SMEs.
Security And Vulnerability Management Market Analysis By Industry
The industry analysis reveals notable interest from sectors like IT and Telecommunications, driving innovations in network security; healthcare, requiring compliance-driven solutions; and government, focusing on data protection against external threats.
Security And Vulnerability Management Market Analysis By Region
Regional performance varies significantly, with North America leading the market. The emphasis on advanced security technologies in Europe and Asia-Pacific shows promising growth potential, while South America and the Middle East/ Africa are emerging markets with increasing investment in security solutions.
Security And Vulnerability Management Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Security And Vulnerability Management Industry
Palo Alto Networks:
A leading provider of cybersecurity solutions, Palo Alto Networks offers advanced threat intelligence and security automation tools tailored for enterprise environments.McAfee:
McAfee is a veteran in the cybersecurity sector, recognized for its comprehensive software and services aimed at protecting digital environments from threats.Symantec:
Renowned for its expertise in endpoint security, Symantec delivers integrated solutions to defend systems against malware and cyber breaches.Fortinet:
Fortinet specializes in high-performance cybersecurity solutions, providing next-gen firewalls and comprehensive security management systems.Trend Micro:
With a global presence, Trend Micro offers multiple layers of security solutions designed to protect against various threats across networks and endpoints.We're grateful to work with incredible clients.









FAQs
What is the market size of Security and Vulnerability Management?
The global Security and Vulnerability Management market is valued at approximately $15 billion in 2023, with an expected compound annual growth rate (CAGR) of 10%, projecting significant growth by 2033.
What are the key market players or companies in this Security and Vulnerability Management industry?
Key players in the Security and Vulnerability Management industry include major companies such as IBM, Tenable, Rapid7, and Qualys, who are instrumental in shaping market dynamics with innovative security solutions.
What are the primary factors driving the growth in the Security and Vulnerability Management industry?
Growth in the Security and Vulnerability Management industry is driven by increasing cybersecurity threats, the need for compliance with regulatory standards, and the growing adoption of digital technologies across multiple sectors.
Which region is the fastest Growing in the Security and Vulnerability Management?
North America is the fastest-growing region, with a market size projected to rise from $5.42 billion in 2023 to $14.54 billion by 2033, driven by robust investments in cybersecurity solutions.
Does ConsaInsights provide customized market report data for the Security and Vulnerability Management industry?
Yes, ConsaInsights offers customized market reports for the Security and Vulnerability Management industry, tailoring data and insights to meet specific client needs for strategic decision-making.
What deliverables can I expect from this Security and Vulnerability Management market research project?
Deliverables from the market research project typically include detailed reports, regional analysis, segment-wise market data, growth projections, and competitive landscape insights.
What are the market trends of Security and Vulnerability Management?
Current market trends include increased investment in automation and AI for cybersecurity, a shift towards cloud-based solutions, and a heightened focus on regulatory compliance and risk management.