Security Assessment Market Report
Published Date: 31 January 2026 | Report Code: security-assessment
Security Assessment Market Size, Share, Industry Trends and Forecast to 2033
This report analyzes the Security Assessment market, providing insights on market size, industry trends, and forecasts from 2023 to 2033. It details segmentation by product, application, and regions, presenting key player analyses and future trends.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
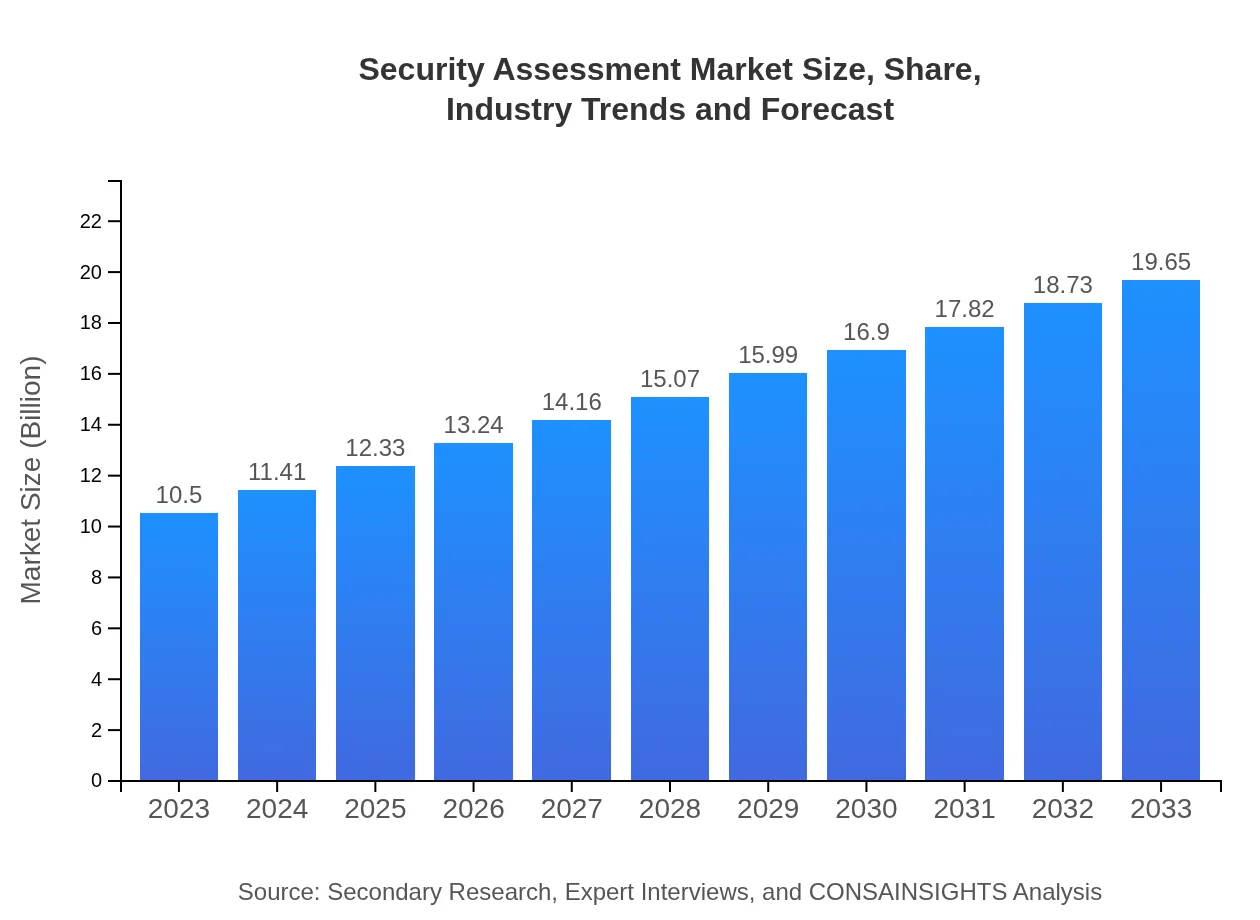
| 2023 Market Size | $10.50 Billion |
| CAGR (2023-2033) | 6.3% |
| 2033 Market Size | $19.65 Billion |
| Top Companies | IBM Security, Qualys, McAfee, Palo Alto Networks, CrowdStrike |
| Last Modified Date | 31 January 2026 |
Security Assessment Market Overview
Customize Security Assessment Market Report market research report
- ✔ Get in-depth analysis of Security Assessment market size, growth, and forecasts.
- ✔ Understand Security Assessment's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Security Assessment
What is the Market Size & CAGR of Security Assessment market in 2023?
Security Assessment Industry Analysis
Security Assessment Market Segmentation and Scope
Tell us your focus area and get a customized research report.
Security Assessment Market Analysis Report by Region
Europe Security Assessment Market Report:
The European market is anticipated to rise from $3.19 billion in 2023 to $5.96 billion by 2033. The European Union's stringent data protection regulations, such as GDPR, have compelled organizations to adopt more comprehensive security assessment measures, driving market growth.Asia Pacific Security Assessment Market Report:
The Asia Pacific region's security assessment market is projected to grow from $1.81 billion in 2023 to $3.39 billion in 2033. This growth is driven by increased digitalization, adoption of cloud-based services, and stringent regulations. Countries like China and India are leading in market expansion due to rapid urbanization and technological advancements.North America Security Assessment Market Report:
North America is expected to see robust growth, with the market expanding from $4.04 billion in 2023 to $7.55 billion by 2033. This can be attributed to the high presence of major security assessment vendors, increased investments in cybersecurity solutions, and a culture of proactive security management among organizations.South America Security Assessment Market Report:
In South America, the market is forecasted to move from $0.42 billion in 2023 to $0.78 billion by 2033. The region is gradually recognizing the importance of cybersecurity, with governments and businesses placing more focus on enhancing their security posture against evolving threats.Middle East & Africa Security Assessment Market Report:
The Middle East and Africa market is estimated to grow from $1.05 billion in 2023 to $1.96 billion by 2033. Accelerated by digital transformation initiatives, countries in this region are increasingly investing in cybersecurity to protect against threats and achieve compliance with international standards.Tell us your focus area and get a customized research report.
Security Assessment Market Analysis By Product
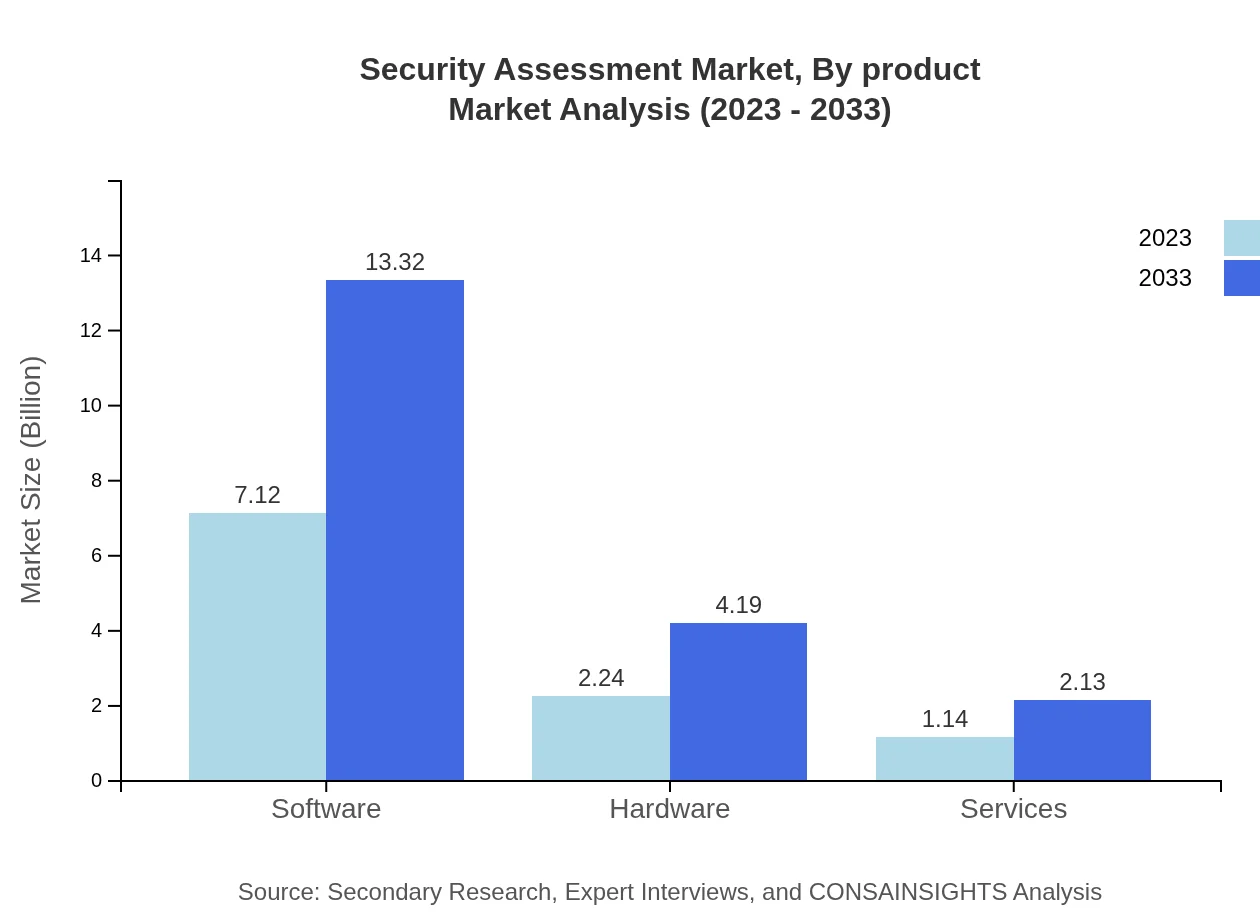
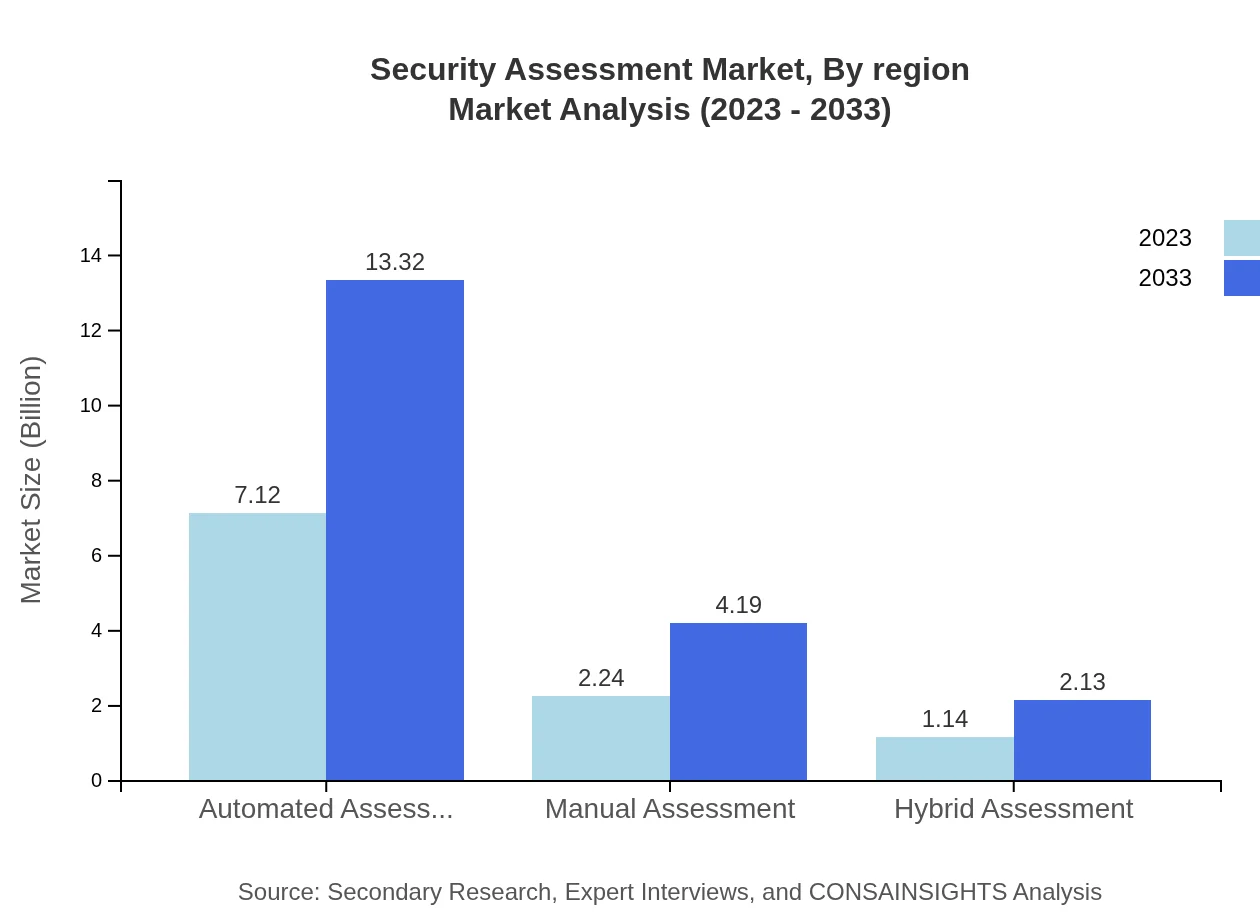
In the security assessment market, different product types such as software and hardware play pivotal roles. As of 2023, the software segment, which emphasizes automated assessments, is valued at $7.12 billion, and is expected to reach $13.32 billion by 2033. Hardware solutions, focusing on network security devices, are growing steadily from $2.24 billion in 2023 to $4.19 billion by 2033.
Security Assessment Market Analysis By Application
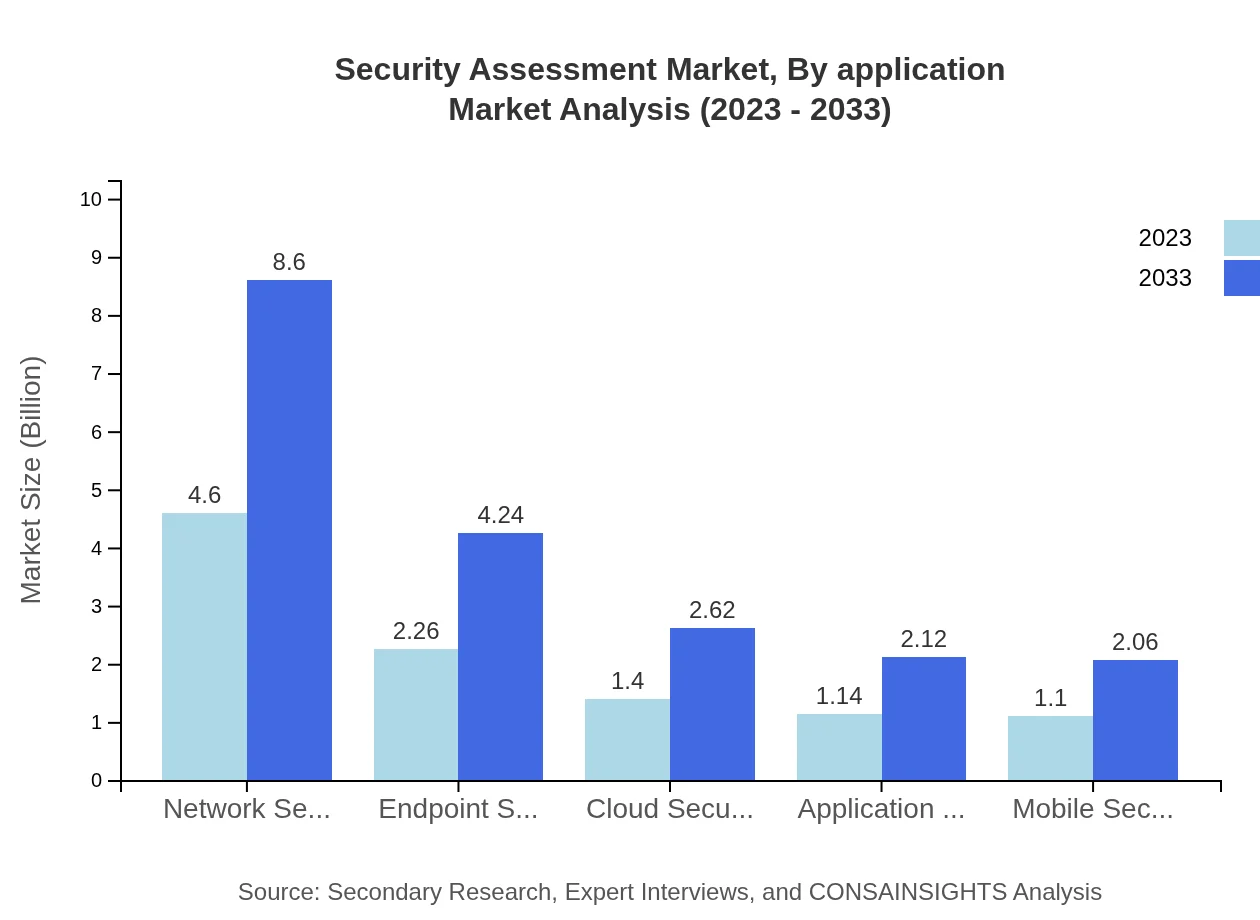
Key applications of security assessments include IT and telecom, banking, financial services and insurance (BFSI), government, healthcare, and retail. The IT and telecom sector, for instance, holds a market size of $4.60 billion in 2023, projected to expand to $8.60 billion by 2033, as the sector increasingly relies on robust security frameworks.
Security Assessment Market Analysis By End User
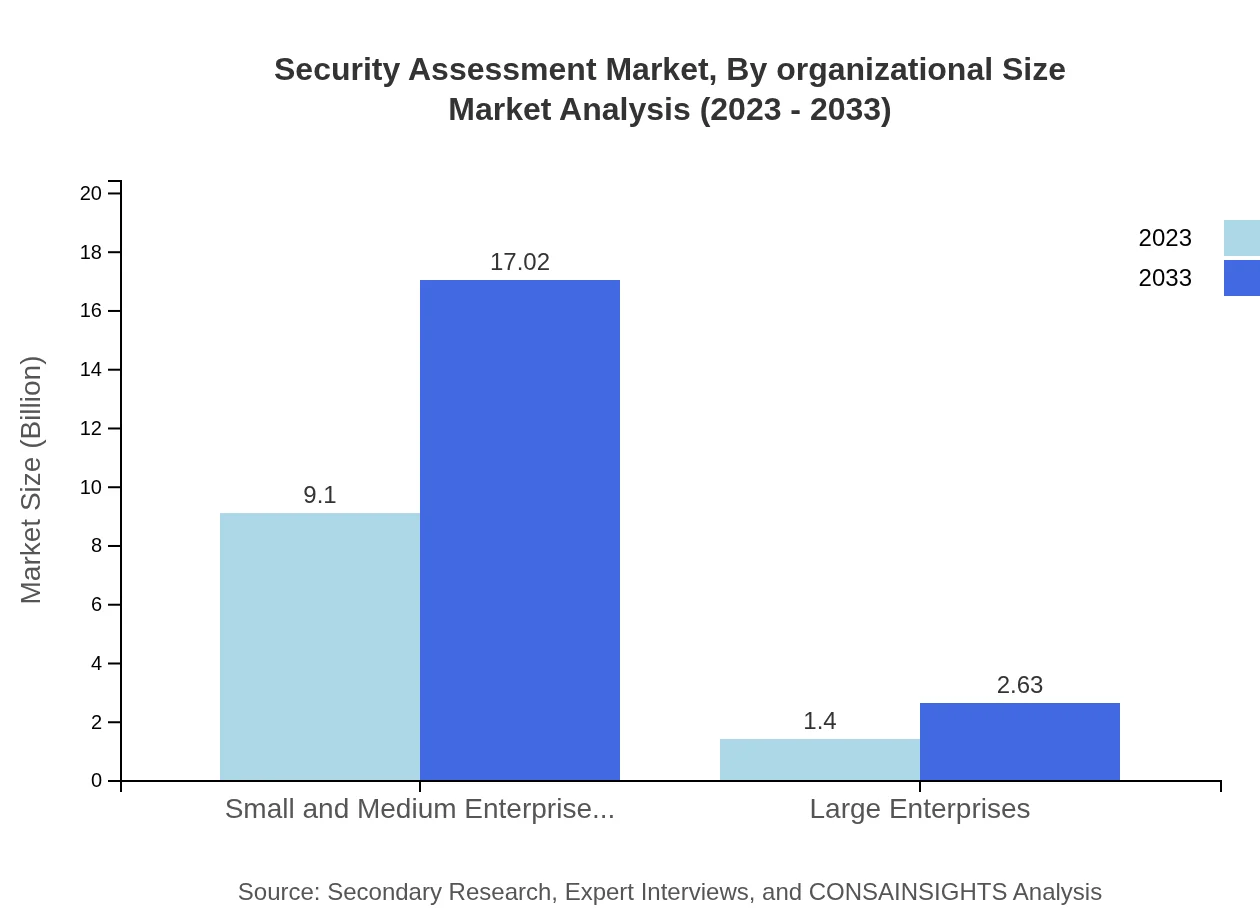
End-users of security assessment solutions range from small and medium enterprises (SMEs) to large enterprises. SMEs dominate the market with a share of 86.62% in 2023, reflecting their increasing acknowledgment of security's importance. The market size for SMEs is expected to grow from $9.10 billion in 2023 to $17.02 billion in 2033.
Security Assessment Market Analysis By Organizational Size
The market exhibits distinct trends across various organizational sizes. Large enterprises account for approximately 13.38% of the share in 2023 and are projected to see growth from $1.40 billion to $2.63 billion by 2033, as they endeavor to maintain compliance and safeguard sensitive information.
Security Assessment Market Analysis By Region
The evaluation methods in the security assessment market include automated and manual assessments. Automated assessments, with a size of $7.12 billion in 2023 and $13.32 billion by 2033, hold a substantial share due to their efficiency and effectiveness. In contrast, manual assessments also maintain relevance, valued at $2.24 billion in 2023, with projections to reach $4.19 billion by 2033.
Security Assessment Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Security Assessment Industry
IBM Security:
IBM Security provides a comprehensive suite of security assessment solutions designed to help organizations identify and remediate vulnerabilities. Their expertise in automated security assessments bolsters their position as market leaders.Qualys:
Qualys offers cloud-based security assessment solutions that provide continuous visibility and compliance. Their innovative platform assists businesses in automating their security practices while maintaining a strong security posture.McAfee:
McAfee specializes in cybersecurity software and hardware solutions, focusing on comprehensive threat intelligence and automated security assessments to safeguard businesses against cyber threats.Palo Alto Networks:
Palo Alto Networks is well-known for its next-generation security solutions, providing proactive security assessment and vulnerability management to protect against sophisticated cyber threats.CrowdStrike:
CrowdStrike utilizes cutting-edge cloud technology to deliver security assessments, leveraging AI for real-time threat detection and response, making them a key player in the industry.We're grateful to work with incredible clients.









FAQs
What is the market size of security assessment?
The market size of the security assessment industry is estimated at $10.5 billion in 2023, with a projected compound annual growth rate (CAGR) of 6.3% through 2033.
What are the key market players or companies in this security assessment industry?
Key players in the security assessment market include major IT and cybersecurity firms such as IBM, McAfee, Rapid7, and Qualys, which provide comprehensive security solutions to organizations globally.
What are the primary factors driving the growth in the security assessment industry?
Growth in the security assessment industry is driven by increasing cyber threats, the rising need for regulatory compliance, and the demand for advanced security solutions, particularly as businesses move towards more complex IT infrastructures.
Which region is the fastest Growing in the security assessment?
The fastest-growing region in the security assessment market is Europe, with a market size projected to increase from $3.19 billion in 2023 to $5.96 billion by 2033, indicating strong growth potential.
Does ConsaInsights provide customized market report data for the security assessment industry?
Yes, ConsaInsights offers customized market reports tailored to specific needs within the security assessment industry, helping organizations gain insights that are relevant to their unique market conditions.
What deliverables can I expect from this security assessment market research project?
Deliverables from the security assessment market research project typically include detailed market analysis, segment insights, competitor analysis, and forecasts, all tailored to inform strategic decision-making.
What are the market trends of security assessment?
Market trends in security assessment include increased adoption of automated assessments, rising importance of cloud security, and a shifting focus towards IT security solutions, emphasizing proactive strategies for threat management.