Security Orchestration Market Report
Published Date: 31 January 2026 | Report Code: security-orchestration
Security Orchestration Market Size, Share, Industry Trends and Forecast to 2033
This report provides an in-depth analysis of the Security Orchestration market, covering market size, industry trends, segmentation, and regional insights from 2023 to 2033. It aims to equip stakeholders with valuable strategic insights and forecasts to make informed decisions in this dynamic landscape.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
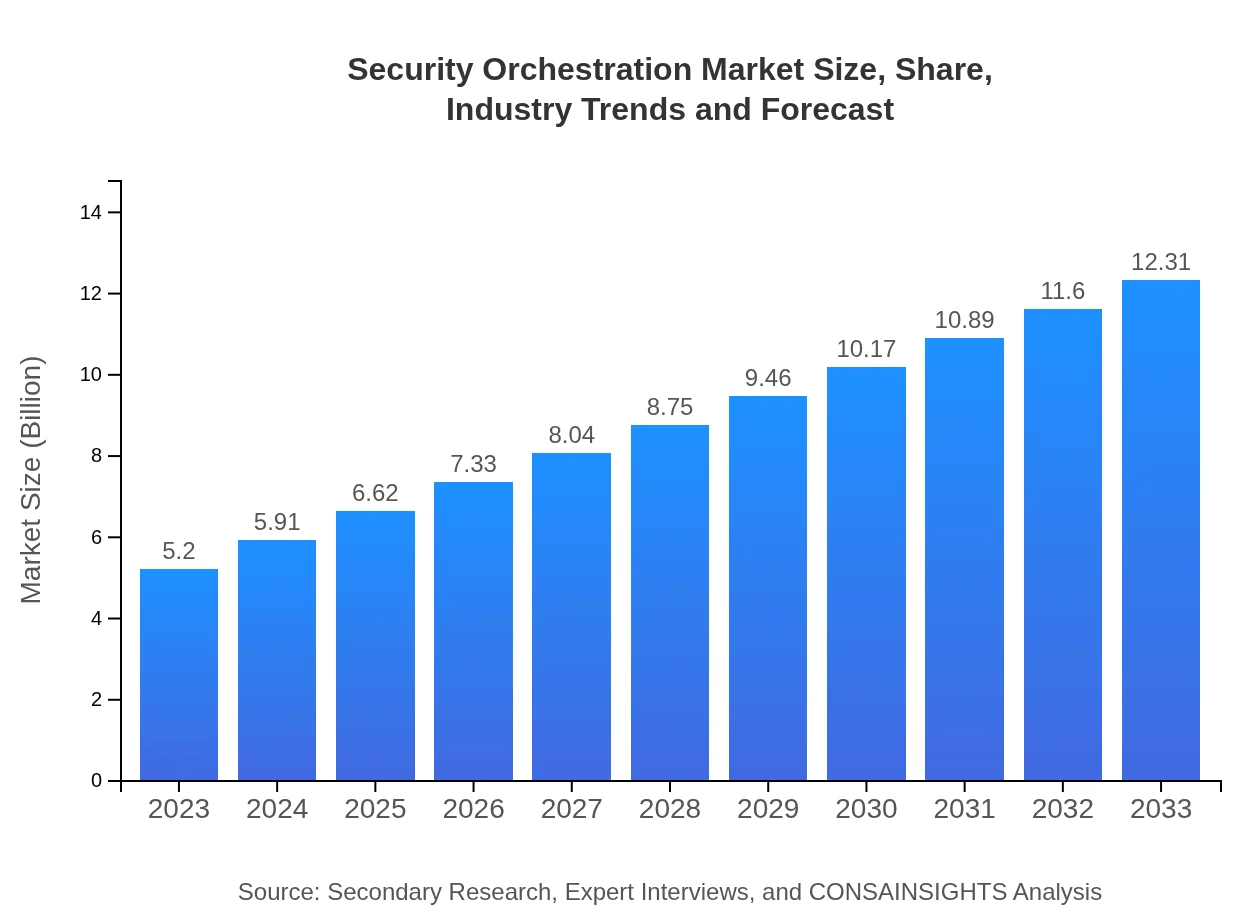
| 2023 Market Size | $5.20 Billion |
| CAGR (2023-2033) | 8.7% |
| 2033 Market Size | $12.31 Billion |
| Top Companies | IBM Security, Splunk Inc., Palo Alto Networks, CybSafe, ServiceNow |
| Last Modified Date | 31 January 2026 |
Security Orchestration Market Overview
Customize Security Orchestration Market Report market research report
- ✔ Get in-depth analysis of Security Orchestration market size, growth, and forecasts.
- ✔ Understand Security Orchestration's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Security Orchestration
What is the Market Size & CAGR of the Security Orchestration market in 2023?
Security Orchestration Industry Analysis
Security Orchestration Market Segmentation and Scope
Tell us your focus area and get a customized research report.
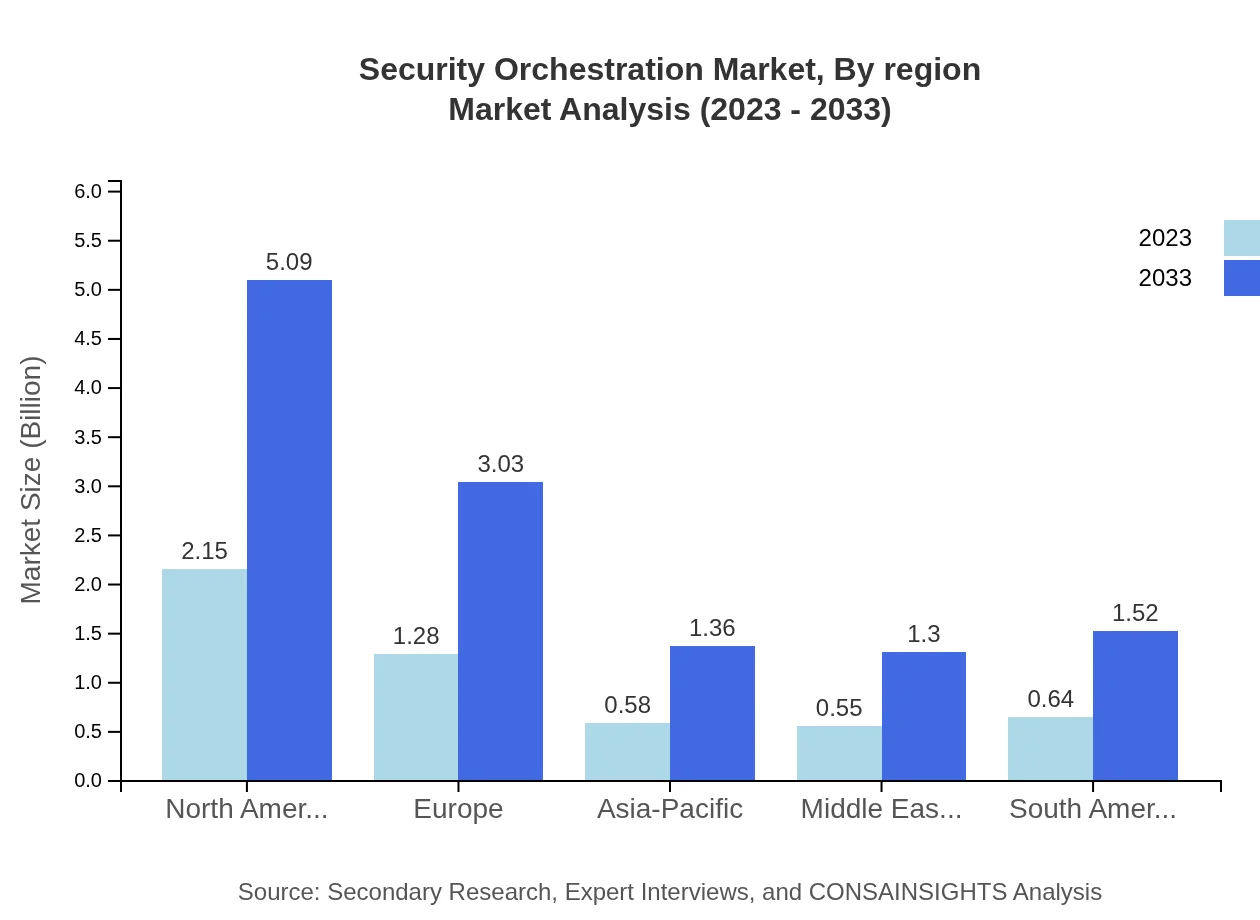
Security Orchestration Market Analysis Report by Region
Europe Security Orchestration Market Report:
In Europe, the market will see a rise from $1.58 billion in 2023 to $3.74 billion by 2033. The introduction of regulations such as GDPR and the need for compliance are key factors propelling the adoption of security orchestration tools across various industries.Asia Pacific Security Orchestration Market Report:
The Asia Pacific region is expected to record substantial growth in the Security Orchestration market, increasing from $0.99 billion in 2023 to $2.35 billion by 2033. This growth is driven by escalating cybersecurity incidents and increasing investments in digital security measures across nations like India and China, where enterprises are rapidly digitizing their operations.North America Security Orchestration Market Report:
North America remains the largest market for Security Orchestration, projected to grow from $1.81 billion in 2023 to $4.28 billion by 2033. The presence of major technology vendors, heightened awareness of cyber threats, and stringent regulatory requirements drive the demand for advanced security solutions in the region.South America Security Orchestration Market Report:
In South America, the market is anticipated to grow from $0.26 billion in 2023 to $0.61 billion by 2033. The adoption of security orchestration is gaining traction due to the growing awareness of cybersecurity threats among organizations, particularly in Brazil and Argentina, leading to increased budgets for security technologies.Middle East & Africa Security Orchestration Market Report:
The Middle East and Africa region is forecasted to grow from $0.56 billion in 2023 to $1.33 billion by 2033. Rising investments in cybersecurity infrastructure and a proactive approach to threat management are anticipated to significantly bolster the Security Orchestration market in this region.Tell us your focus area and get a customized research report.
Security Orchestration Market Analysis By Product
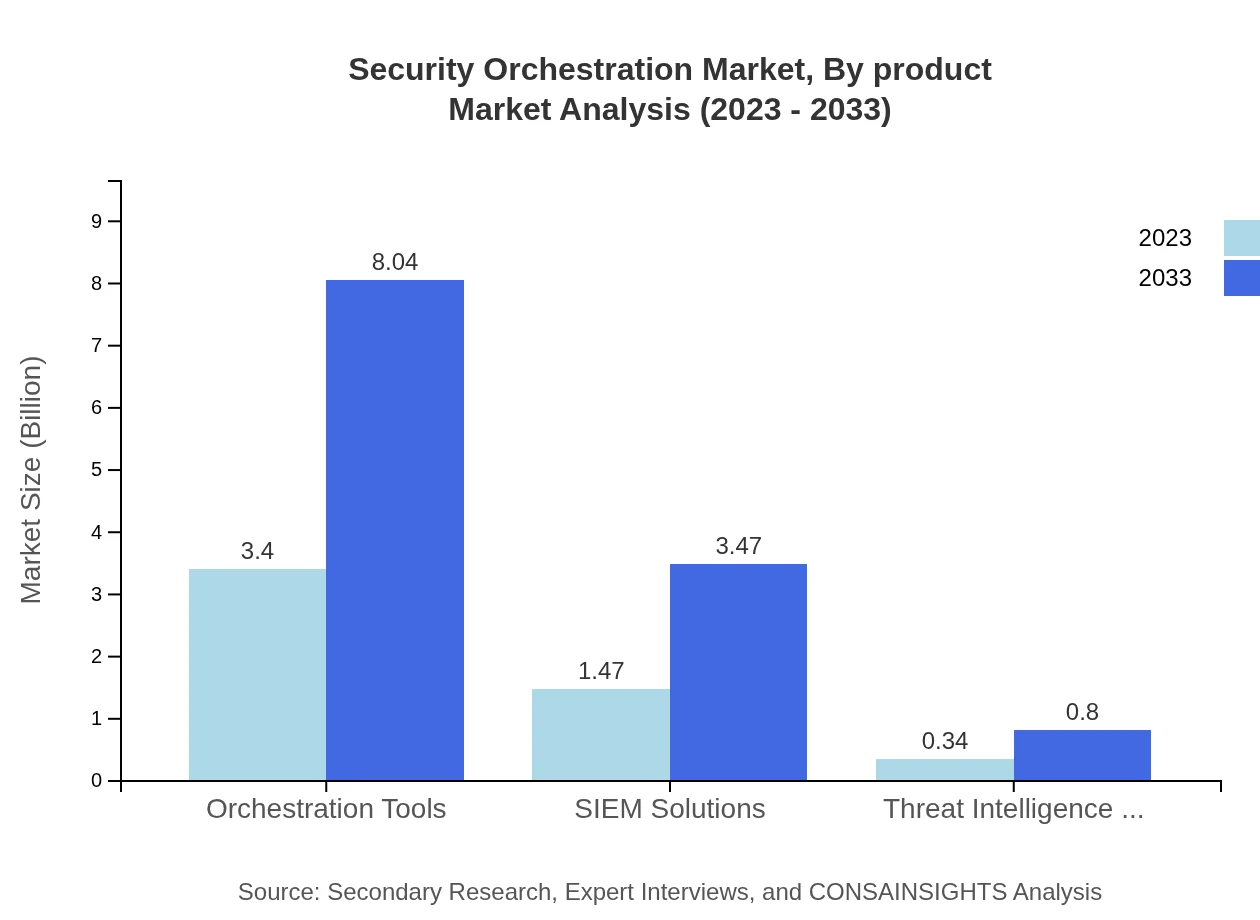
The primary product segments in the Security Orchestration market include Orchestration Tools, SIEM Solutions, and Threat Intelligence Solutions. Orchestration tools dominate the market, commanding a $3.40 billion share in 2023, expected to increase to $8.04 billion by 2033, accounting for 65.29% of the market by product. SIEM solutions hold a significant portion, with expected revenue growth from $1.47 billion in 2023 to $3.47 billion by 2033, representing a 28.19% market share.
Security Orchestration Market Analysis By Application
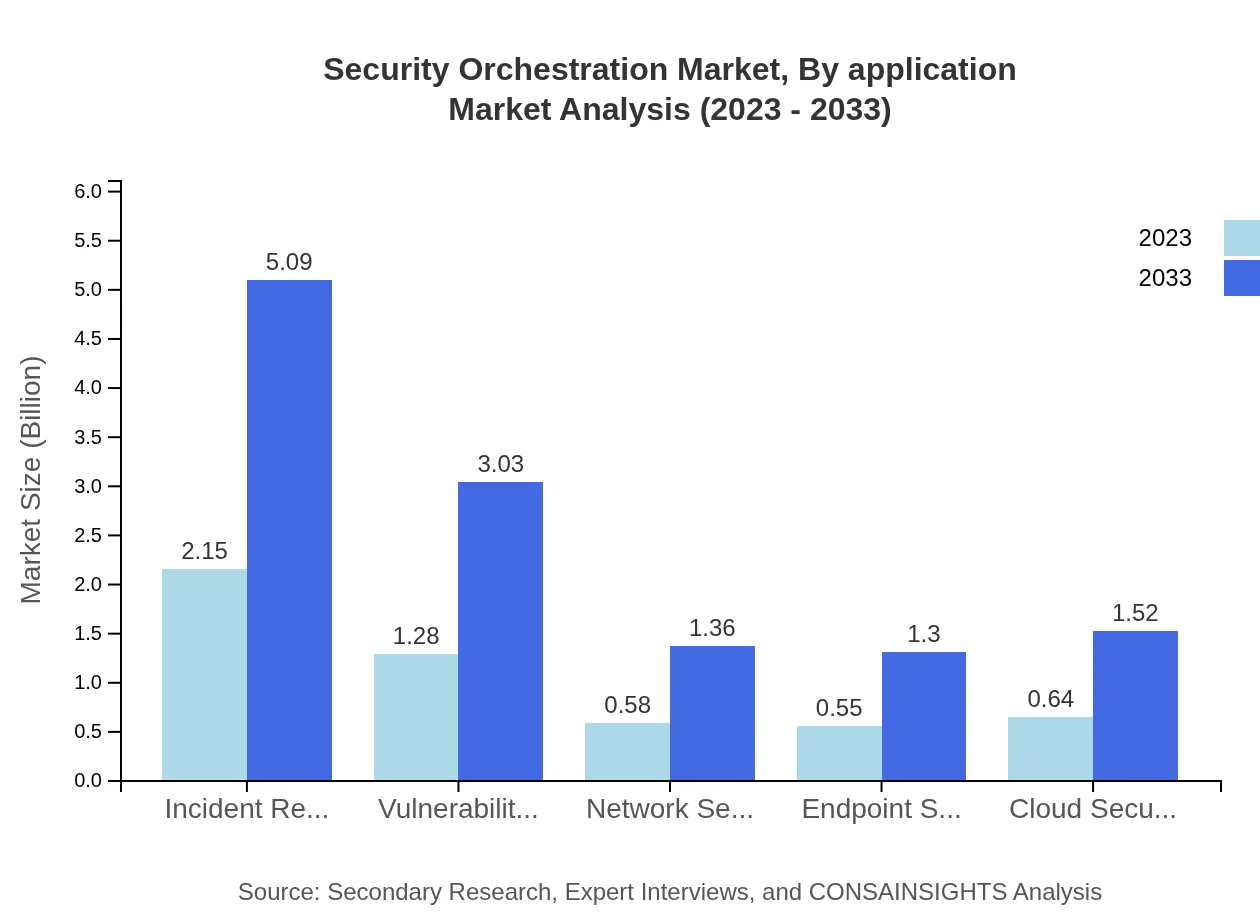
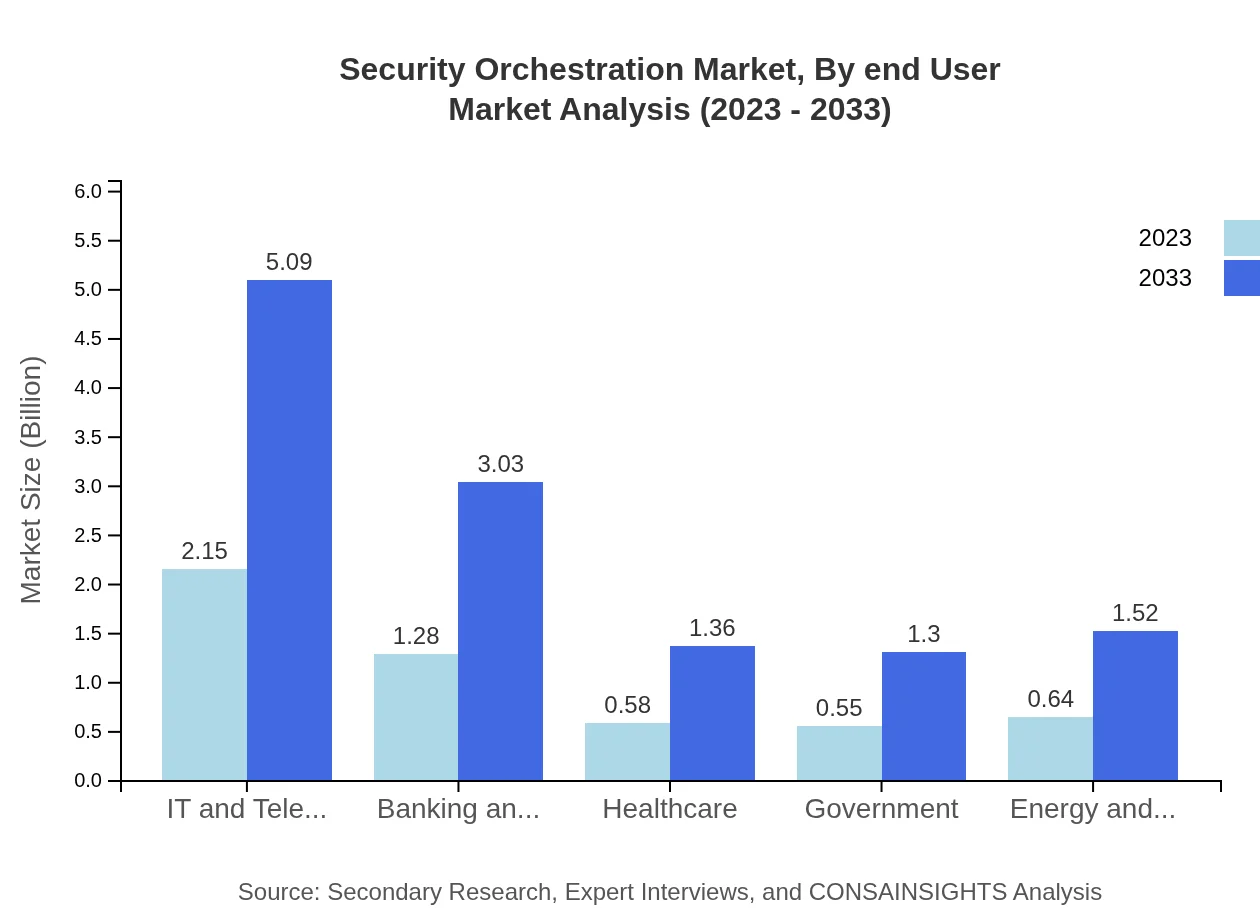
The key application segments include IT and Telecom, Banking and Financial Services, Government, and Healthcare. IT and Telecom alone capture a substantial market share, increasing from $2.15 billion in 2023 to $5.09 billion by 2033, while Banking and Financial Services are expected to rise from $1.28 billion to $3.03 billion.
Security Orchestration Market Analysis By Deployment Type
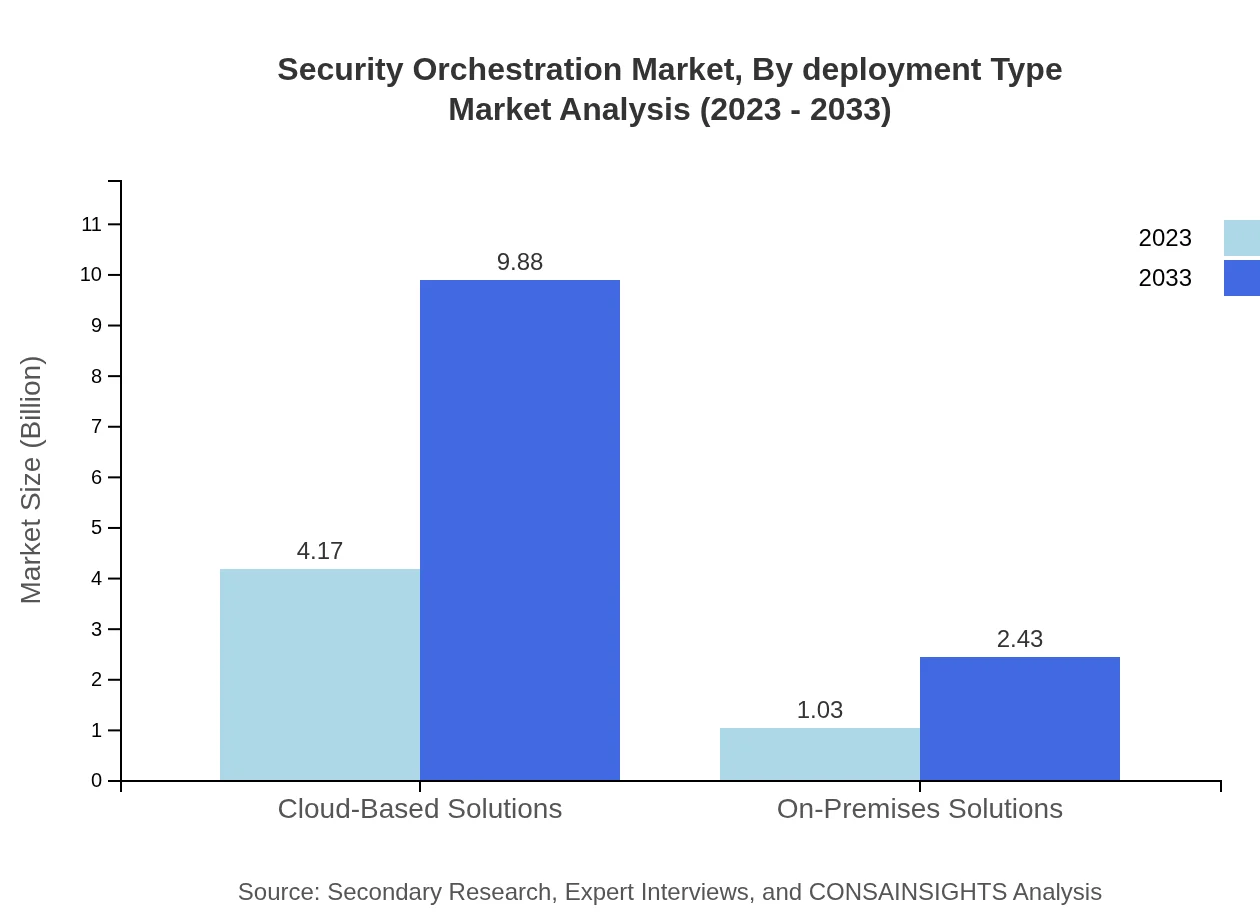
The Security Orchestration market is divided between Cloud-based and On-Premises Solutions. Cloud-based solutions are projected to feature prominently, scaling from $4.17 billion in 2023 to $9.88 billion by 2033, capturing 80.24% of the deployment type market. On-Premises Solutions are anticipated to grow from $1.03 billion to $2.43 billion over the same period.
Security Orchestration Market Analysis By End User
The market showcases diversified end-user segments, with notable contributions from sectors such as Healthcare, Government, and Energy and Utilities. As organizations face an increasing number of cyber threats, the market for these sectors is expected to augment substantially.
Security Orchestration Market Analysis By Region
Regional analysis indicates North America will continue to dominate the market, closely followed by Europe and the Asia-Pacific. Each region exhibits unique characteristics that reflect their economic and regulatory landscapes, shaping their demand for security solutions.
Security Orchestration Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Security Orchestration Industry
IBM Security:
IBM Security provides integrated security solutions designed to help organizations manage and respond to complex security environments efficiently.Splunk Inc.:
Splunk Inc. is known for its SIEM solutions and robust security orchestration capabilities that enhance visibility and create automated workflows.Palo Alto Networks:
A leader in cybersecurity, Palo Alto Networks offers innovative security orchestration platforms that empower users to respond to threats swiftly.CybSafe:
CybSafe specializes in behavioral security and automation, delivering orchestration tools that enhance cyber resilience.ServiceNow:
ServiceNow integrates security orchestration into its broader IT service management platform to improve incident response and resolution times.We're grateful to work with incredible clients.









FAQs
What is the market size of security Orchestration?
The global security orchestration market is valued at approximately $5.2 billion in 2023, with a projected CAGR of 8.7% leading to substantial growth by 2033.
What are the key market players or companies in this security Orchestration industry?
Key players in the security orchestration market include major firms like Splunk, IBM, Cisco, and Palo Alto Networks, which lead in innovation and market share, ensuring competitive dynamics in this evolving industry.
What are the primary factors driving the growth in the security Orchestration industry?
The growth of the security orchestration industry is driven by increasing cyber threats, demand for automated security processes, and the integration of AI technologies, enhancing operational efficiency and incident response capabilities across sectors.
Which region is the fastest Growing in the security Orchestration market?
The Asia-Pacific region is the fastest-growing area in the security orchestration market, expected to grow from a market size of $0.99 billion in 2023 to $2.35 billion by 2033, indicating substantial opportunity for expansion.
Does ConsaInsights provide customized market report data for the security Orchestration industry?
Yes, ConsaInsights offers customized market report data tailored to specific needs within the security orchestration industry, enabling clients to gain insights relevant to their unique market strategies and operational goals.
What deliverables can I expect from this security Orchestration market research project?
Deliverables from the security orchestration market research project include comprehensive reports on market trends, player analyses, segment insights, and forecast data, ensuring a thorough understanding of the industry's landscape.
What are the market trends of security Orchestration?
Current market trends in security orchestration include heightened demand for automation, advancements in cloud-based security solutions, and an evolving focus on integrating threat intelligence, ensuring organizations can quickly adapt to emerging cyber threats.