Security Policy Management Market Report
Published Date: 31 January 2026 | Report Code: security-policy-management
Security Policy Management Market Size, Share, Industry Trends and Forecast to 2033
This report offers a comprehensive analysis of the Security Policy Management market from 2023 to 2033, detailing insights into market size, growth trends, key industry players, regional performance, and future forecasts.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
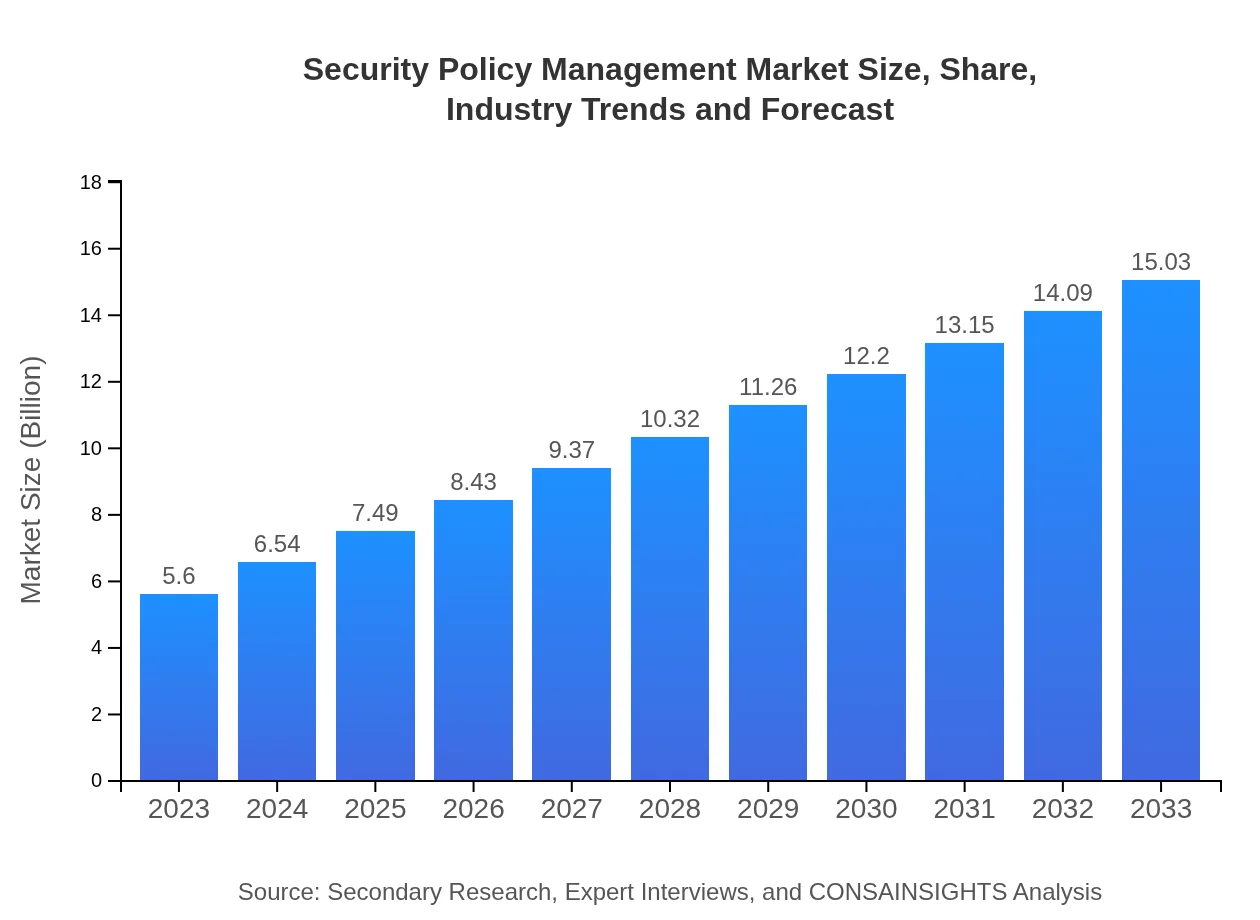
| 2023 Market Size | $5.60 Billion |
| CAGR (2023-2033) | 10% |
| 2033 Market Size | $15.03 Billion |
| Top Companies | Symantec Corporation, IBM Security, McAfee LLC, Cisco Systems, Inc., Check Point Software Technologies |
| Last Modified Date | 31 January 2026 |
Security Policy Management Market Overview
Customize Security Policy Management Market Report market research report
- ✔ Get in-depth analysis of Security Policy Management market size, growth, and forecasts.
- ✔ Understand Security Policy Management's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Security Policy Management
What is the Market Size & CAGR of Security Policy Management market in 2023?
Security Policy Management Industry Analysis
Security Policy Management Market Segmentation and Scope
Tell us your focus area and get a customized research report.
Security Policy Management Market Analysis Report by Region
Europe Security Policy Management Market Report:
The European market is projected to expand from $1.95 billion in 2023 to $5.24 billion by 2033, driven by regulations such as GDPR that enforce strict compliance requirements on organizations. The ongoing development of policies to protect consumer data further propels market growth.Asia Pacific Security Policy Management Market Report:
In the Asia Pacific region, the Security Policy Management market is expected to grow from $0.87 billion in 2023 to $2.35 billion by 2033, exhibiting a robust CAGR of around 10.36%. Factors contributing to this growth include rising cybersecurity awareness, increased cloud adoption, and government initiatives aimed at enhancing national security measures.North America Security Policy Management Market Report:
North America holds a significant share of the Security Policy Management market, projected to grow from $1.94 billion in 2023 to $5.22 billion by 2033. Key factors include stringent regulatory mandates, high adoption rates of advanced technology solutions, and a mature cybersecurity landscape urging organizations to enhance their security frameworks.South America Security Policy Management Market Report:
The South American Security Policy Management market will see an increase from $0.42 billion in 2023 to $1.12 billion in 2033. This growth is driven by the progression of digital transformation initiatives and enhanced focus on data protection regulations, which necessitate comprehensive security strategies among local enterprises.Middle East & Africa Security Policy Management Market Report:
In the Middle East and Africa, market growth is expected to move from $0.41 billion in 2023 to $1.11 billion by 2033, as governments invest in cybersecurity initiatives to combat rising cyber threats. This region's focus on improving IT infrastructures also facilitates market expansion.Tell us your focus area and get a customized research report.
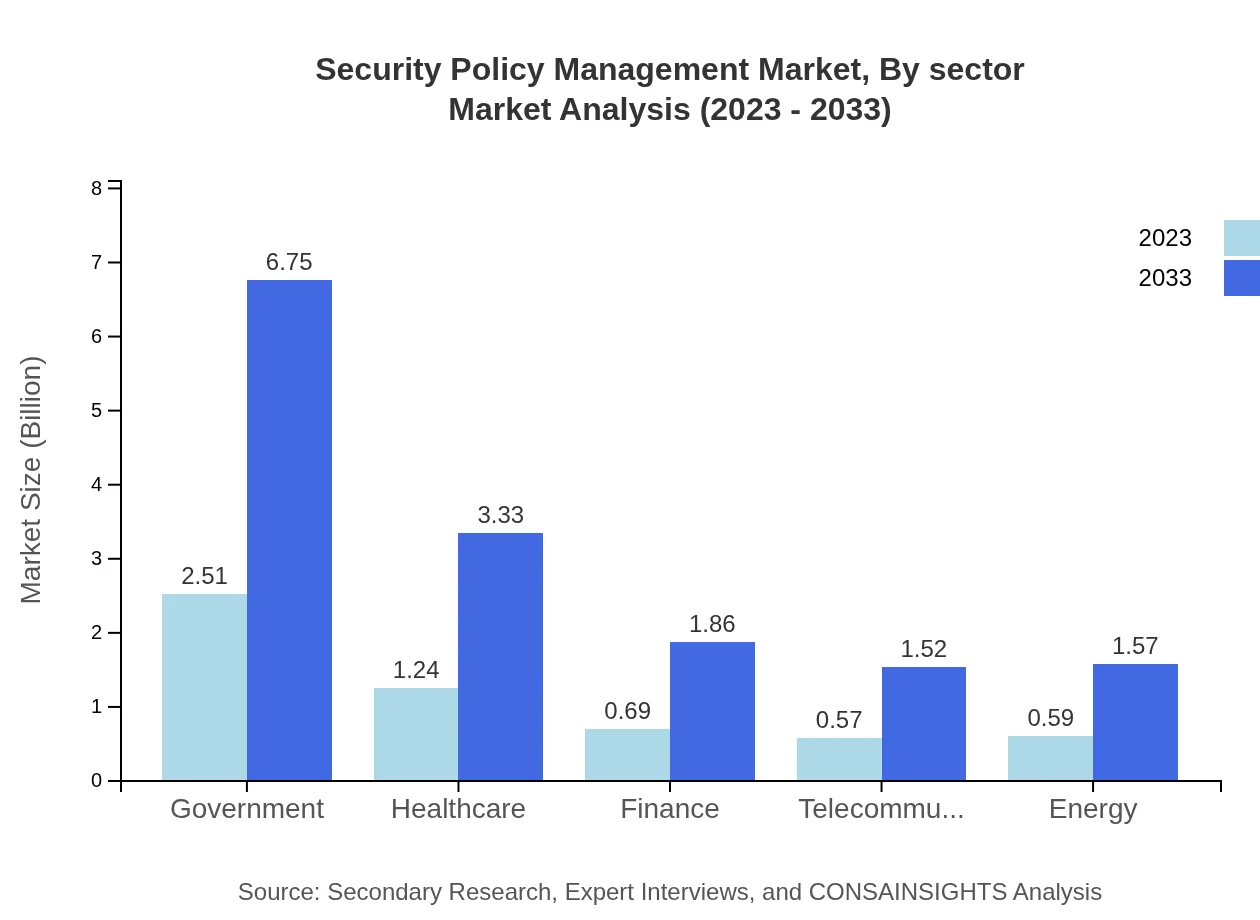
Security Policy Management Market Analysis By Sector
The government sector remains the largest segment, projected to grow from $2.51 billion in 2023 to $6.75 billion by 2033, maintaining a considerable market share of 44.89%. The healthcare sector follows, expected to rise from $1.24 billion to $3.33 billion, representing 22.12% of the market share. The finance sector also shows significant potential, with growth projections from $0.69 billion to $1.86 billion, while telecommunications, energy, and compliance regulations like GDPR will continuously impact the market landscape.
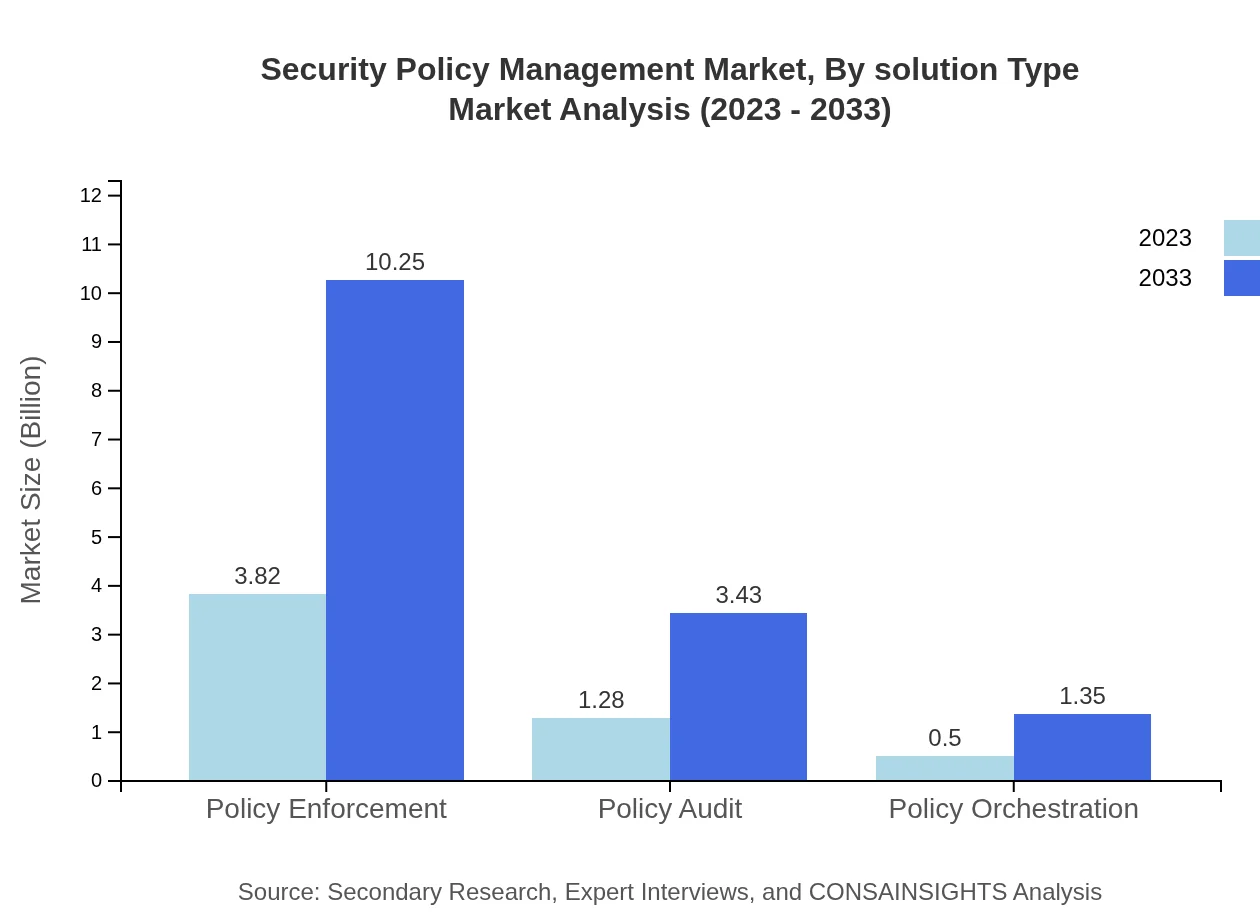
Security Policy Management Market Analysis By Solution Type
Solutions involving policy enforcement are projected to grow significantly, from $3.82 billion in 2023 to $10.25 billion by 2033. Policy auditing and orchestration make up crucial aspects of compliance strategy, with expected market shares of 22.8% and 9.01%, respectively. These solutions ensure that organizations manage their security policies across dynamic environments, thus fostering adaptive compliance mechanisms.
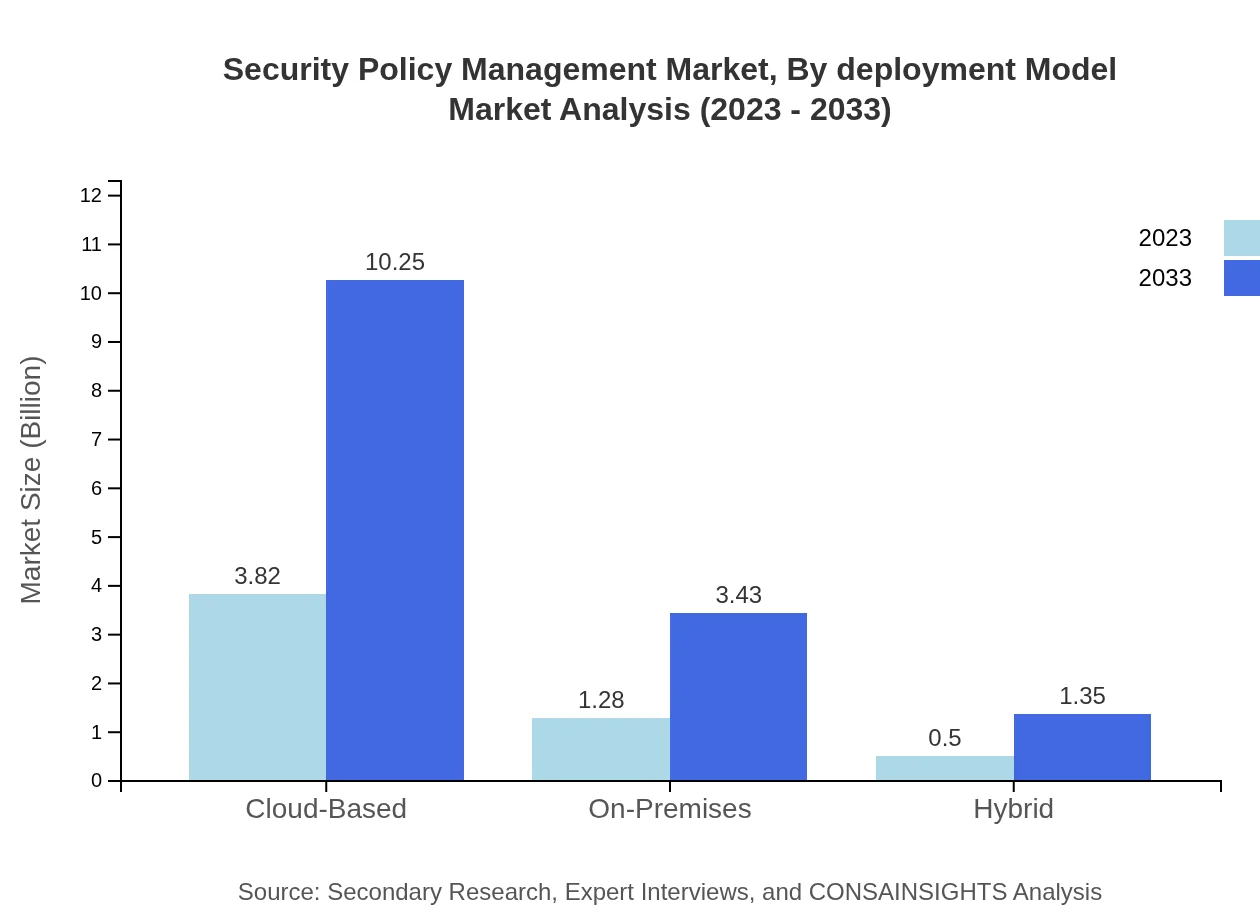
Security Policy Management Market Analysis By Deployment Model
The cloud-based deployment model is dominant, forecasted to expand from $3.82 billion in 2023 to $10.25 billion by 2033. On-premises and hybrid solutions also see growth but at a slower rate, reflecting the industry's shift towards cloud computing and the necessity for scalable security infrastructure responsive to evolving threats.
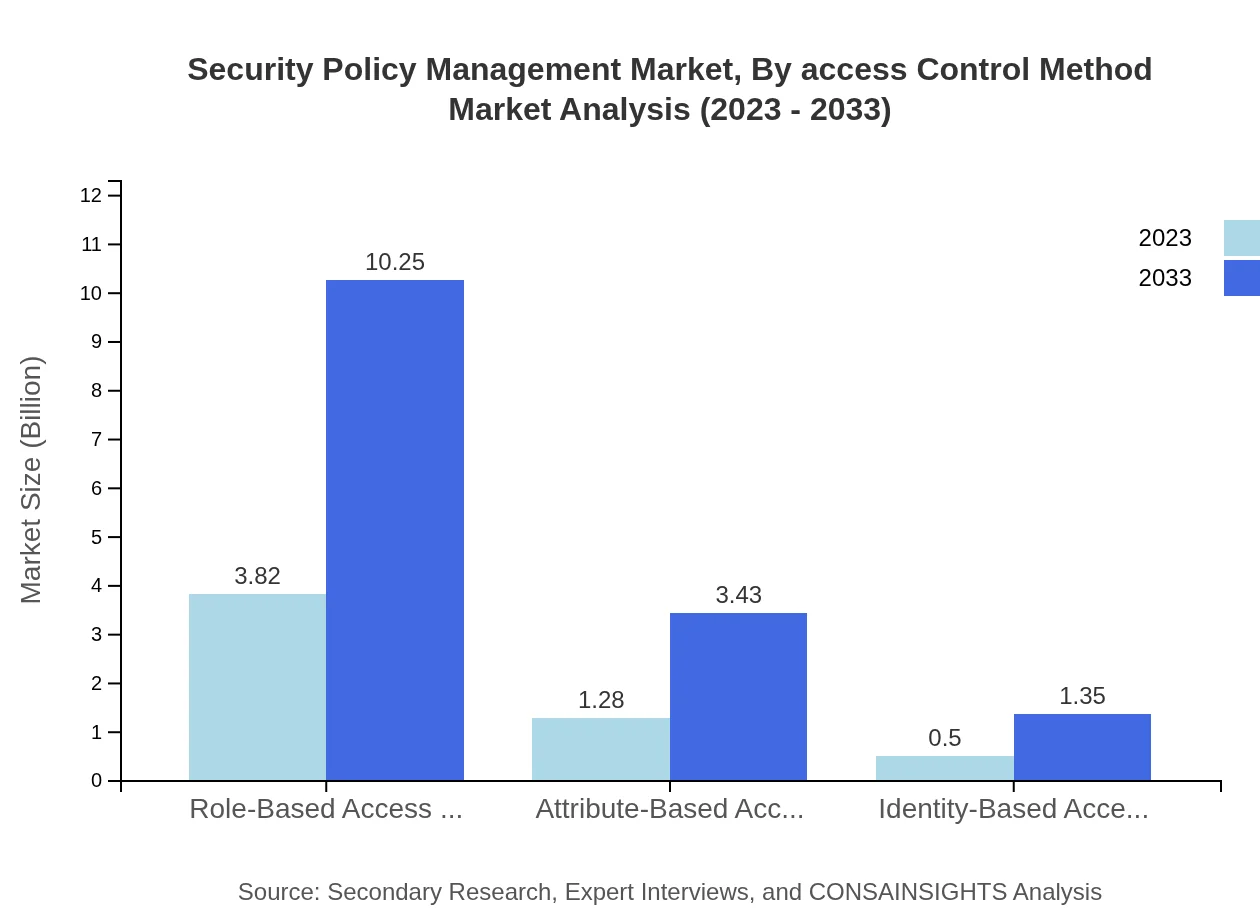
Security Policy Management Market Analysis By Access Control Method
Role-based access control (RBAC) is the leading access control method, expected to grow from $3.82 billion to $10.25 billion, making up 68.19% of the market. Attribute-based access control and identity-based access control, though smaller segments, are gaining traction due to their flexibility in managing access rights tailored to organizational needs.
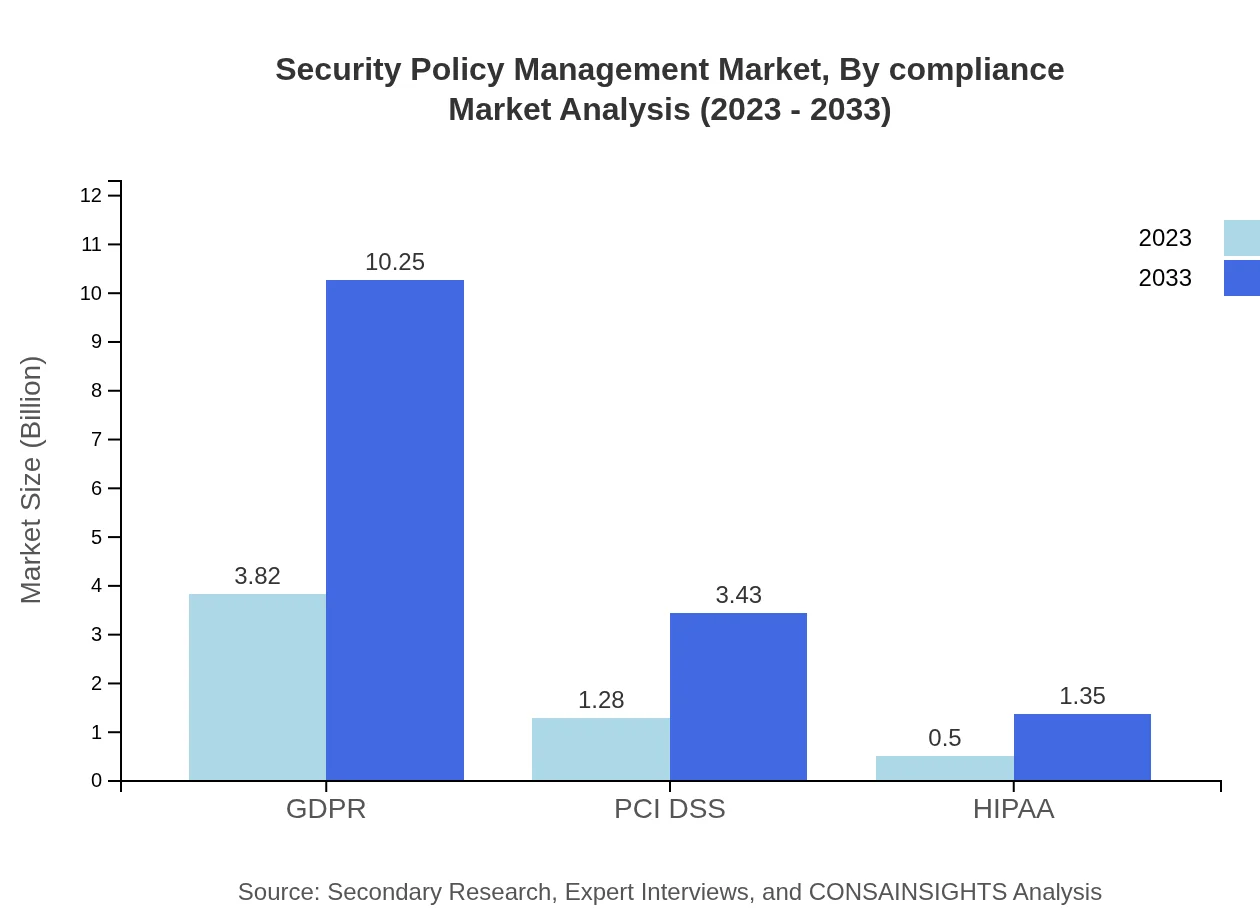
Security Policy Management Market Analysis By Compliance
Compliance requirements like GDPR and PCI DSS play an essential role in shaping the security policy management landscape. The market share for GDPR-related solutions is expected to dominate with 68.19%, reflecting the urgency for organizations to comply with data protection regulations. Additionally, HIPAA will maintain a small share as healthcare compliance grows more complex.
Security Policy Management Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Security Policy Management Industry
Symantec Corporation:
A leader in cybersecurity with extensive offerings in security policy management solutions that integrate advanced threat protection, compliance management, and analytics.IBM Security:
IBM provides a comprehensive set of security solutions including identity and access management, regulatory compliance frameworks, and policy enforcement automation tools.McAfee LLC:
McAfee offers robust security policy management solutions focusing on data loss prevention, identity protection, and adaptive security responses.Cisco Systems, Inc.:
Cisco provides integrated security solutions, including policy management to safeguard networks from emerging cyber threats through continuous monitoring and compliance enforcement.Check Point Software Technologies:
Check Point specializes in providing unified security policy management tools that facilitate efficient policy configuration and enforcement across varied environments.We're grateful to work with incredible clients.









FAQs
What is the market size of security Policy Management?
The global Security Policy Management market is valued at approximately $5.6 billion in 2023. It is projected to experience a robust CAGR of 10% throughout the next decade, highlighting significant growth and investment opportunities.
What are the key market players or companies in this security Policy Management industry?
Key players in the Security Policy Management industry include major companies such as IBM, Cisco, Check Point Software Technologies, and McAfee. These firms lead through innovation and a commitment to cybersecurity solutions, fostering competitive dynamics.
What are the primary factors driving the growth in the security Policy Management industry?
Growth in the Security Policy Management sector is driven by increasing cyber threats, regulatory compliance requirements, and the need for improved IT security frameworks. Moreover, advancements in technology add efficiency to security policy enforcement.
Which region is the fastest Growing in the security Policy Management?
The fastest-growing region for Security Policy Management is North America, projected to expand from $1.94 billion in 2023 to $5.22 billion in 2033. Growth is supported by high demand for cybersecurity solutions.
Does ConsaInsights provide customized market report data for the security Policy Management industry?
Yes, ConsaInsights offers customized market report data tailored to the specific needs of clients in the Security Policy Management industry. This enables businesses to strategize effectively.
What deliverables can I expect from this security Policy Management market research project?
In a Security Policy Management market research project, you can expect comprehensive reports, market forecasts, regional analysis, segmentation breakdowns, and actionable insights to enhance decision-making.
What are the market trends of security Policy Management?
Current trends in the Security Policy Management sector include a shift towards cloud-based solutions, increasing integration of AI for policy management, and rising importance of compliance frameworks in policy creation.