Unified Threat Management Market Report
Published Date: 31 January 2026 | Report Code: unified-threat-management
Unified Threat Management Market Size, Share, Industry Trends and Forecast to 2033
This report provides an extensive analysis of the Unified Threat Management market, including growth forecasts from 2023 to 2033. Insights include market size, industry trends, regional analysis, and profiles of leading companies in the sector.
| Metric | Value |
|---|---|
| Study Period | 2023 - 2033 |
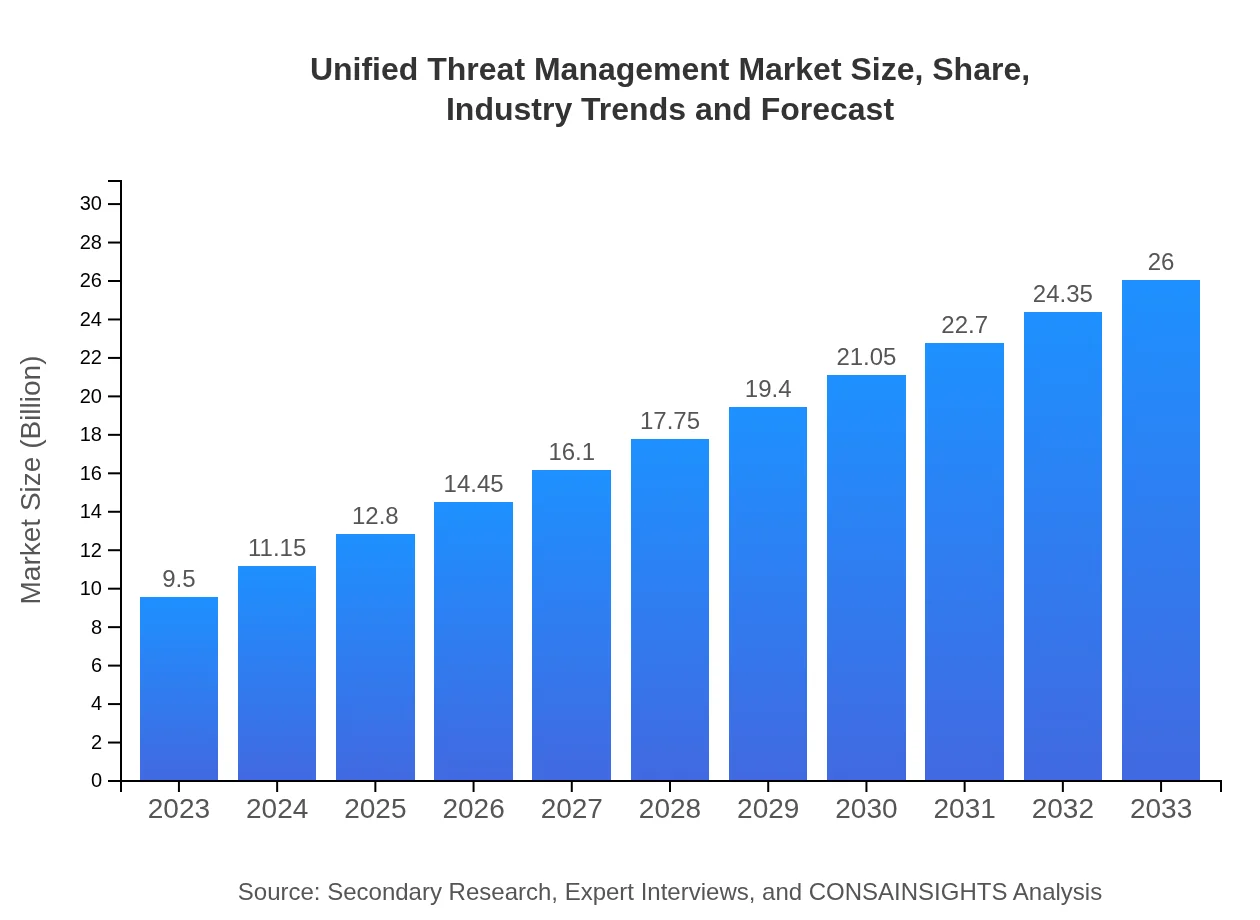
| 2023 Market Size | $9.50 Billion |
| CAGR (2023-2033) | 10.2% |
| 2033 Market Size | $26.00 Billion |
| Top Companies | Cisco Systems, Inc., Fortinet, Inc., Palo Alto Networks, Inc., Check Point Software Technologies, Sophos Ltd. |
| Last Modified Date | 31 January 2026 |
Unified Threat Management Market Overview
Customize Unified Threat Management Market Report market research report
- ✔ Get in-depth analysis of Unified Threat Management market size, growth, and forecasts.
- ✔ Understand Unified Threat Management's regional dynamics and industry-specific trends.
- ✔ Identify potential applications, end-user demand, and growth segments in Unified Threat Management
What is the Market Size & CAGR of Unified Threat Management market in 2023?
Unified Threat Management Industry Analysis
Unified Threat Management Market Segmentation and Scope
Tell us your focus area and get a customized research report.
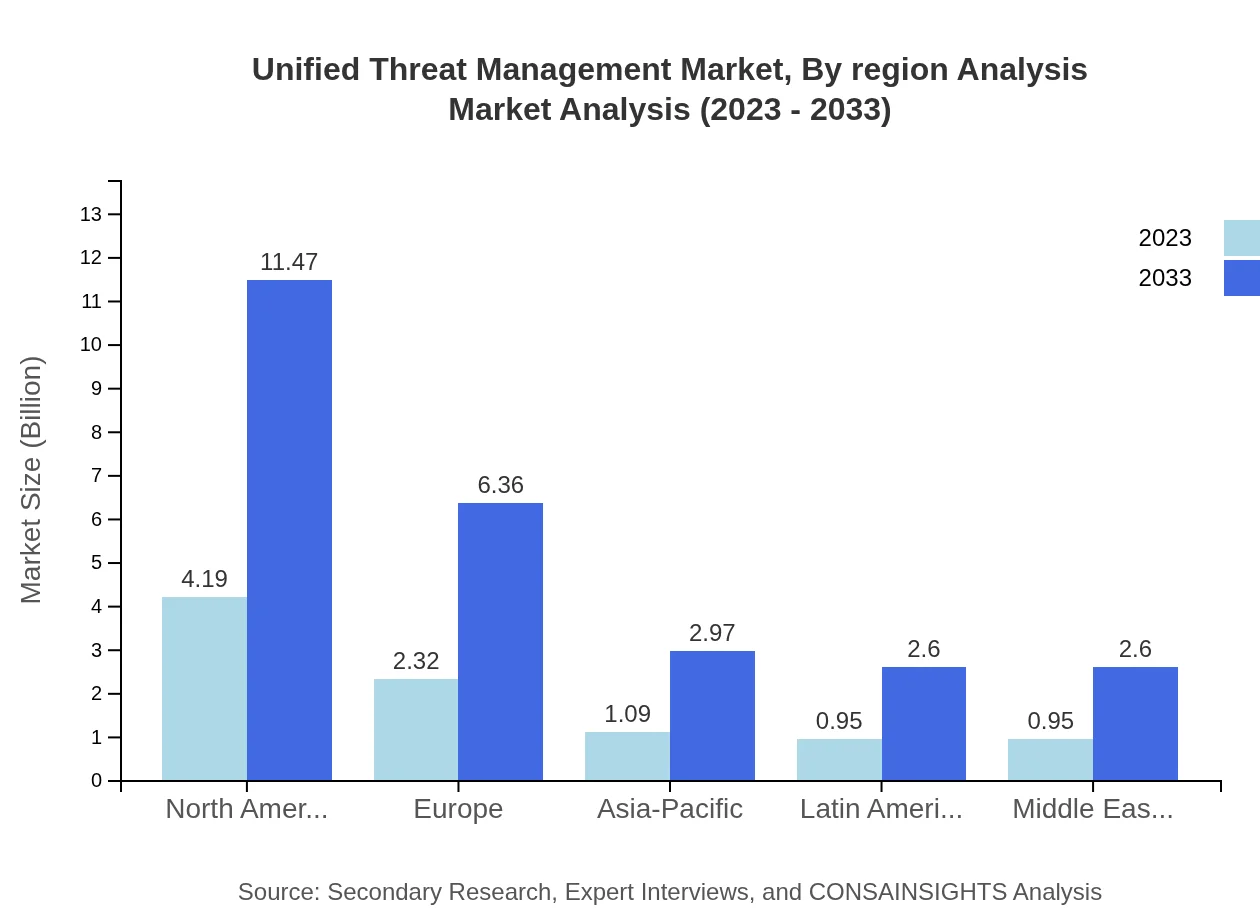
Unified Threat Management Market Analysis Report by Region
Europe Unified Threat Management Market Report:
In Europe, the UTM market is forecasted to grow from USD 2.89 billion in 2023 to USD 7.92 billion by 2033. The demand for unified security solutions is significantly driven by the increasing regulatory pressures, particularly the GDPR. Countries like Germany, France, and the UK are investing in UTM technologies to enhance their cybersecurity frameworks.Asia Pacific Unified Threat Management Market Report:
The Asia Pacific region is experiencing rapid growth in the Unified Threat Management market, with its size expected to increase from USD 1.59 billion in 2023 to USD 4.36 billion by 2033. The rise in cyber threats combined with increasing digital transformation initiatives across various sectors contributes to this growth. Countries like China, India, and Japan are at the forefront of adopting UTM solutions, reflecting the region's expanding security requirements.North America Unified Threat Management Market Report:
North America dominates the Unified Threat Management market, with a market size anticipated to grow from USD 3.67 billion in 2023 to USD 10.05 billion by 2033. This region is characterized by a high adoption rate of UTM solutions driven by a well-established IT infrastructure and strict compliance regulations. The USA is the largest market, where both large enterprises and SMEs prioritize cybersecurity in their operations.South America Unified Threat Management Market Report:
In South America, the UTM market is projected to grow from USD 0.87 billion in 2023 to USD 2.37 billion by 2033. Factors driving this growth include an increasing number of cyber threats and a rising adoption of advanced security technologies, particularly among small and medium enterprises. Brazil and Argentina are leading investors in cybersecurity solutions, contributing to regional market growth.Middle East & Africa Unified Threat Management Market Report:
The Middle East and Africa region is expected to expand from USD 0.48 billion in 2023 to USD 1.30 billion by 2033. This growth is supported by rising cyber threats and an increasing emphasis on digital transformation by businesses. Governments are also undertaking initiatives to bolster national cybersecurity, impacting market dynamics positively.Tell us your focus area and get a customized research report.
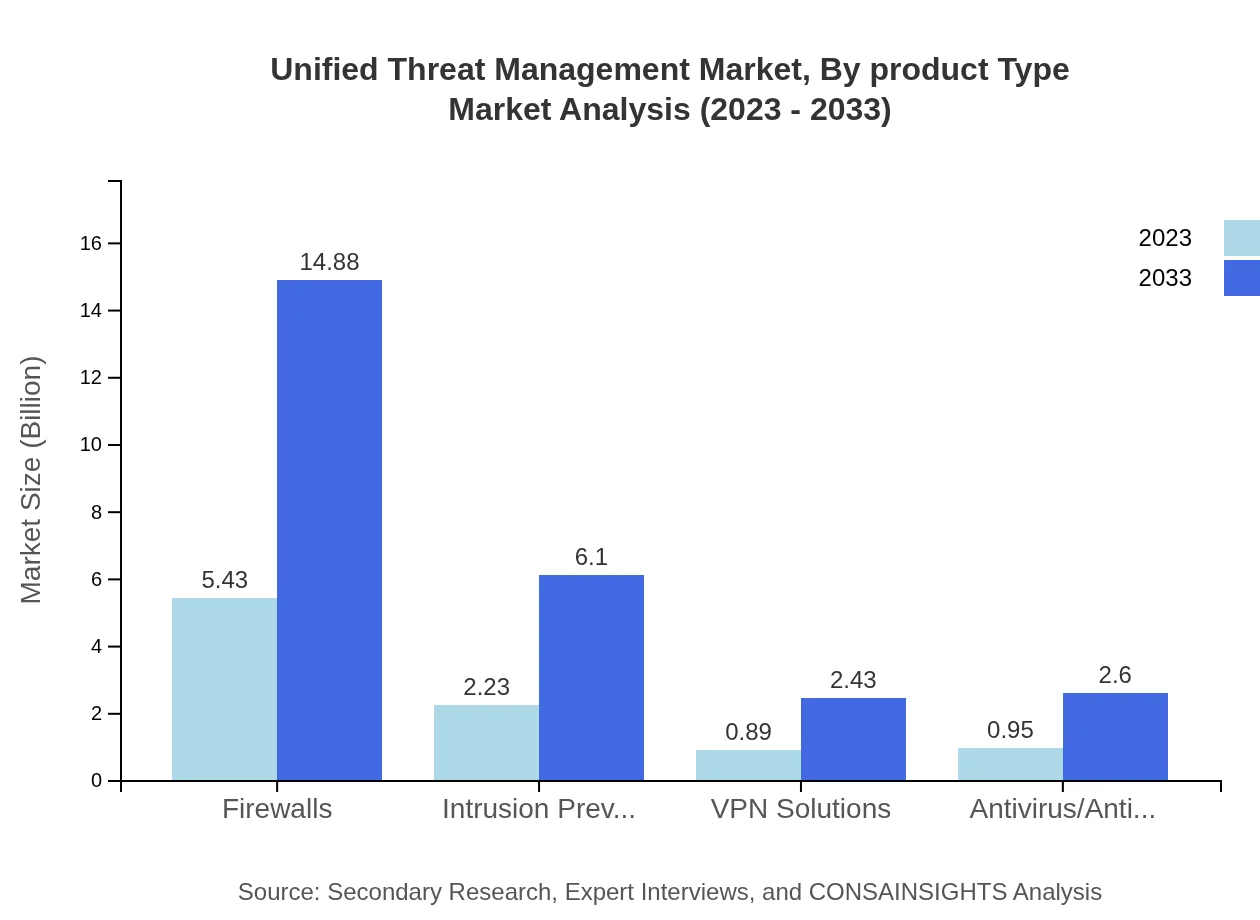
Unified Threat Management Market Analysis By Product Type
In 2023, the firewalls segment is projected to dominate the UTM market with a size of USD 5.43 billion, expected to grow to USD 14.88 billion by 2033, holding a share of 57.21%. Other significant segments include intrusion prevention systems and antivirus/antimalware solutions, which are anticipated to grow substantially as organizations seek comprehensive protection.
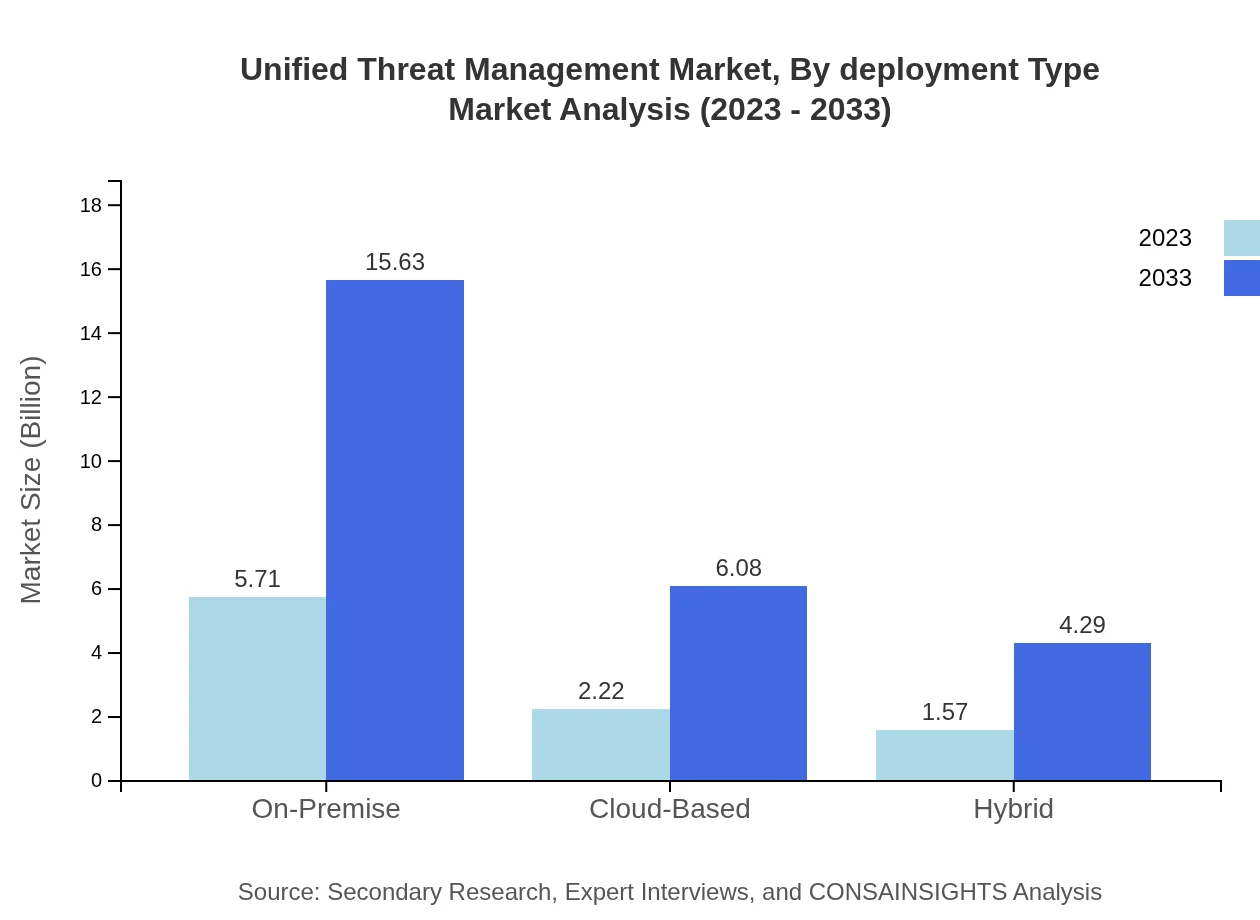
Unified Threat Management Market Analysis By Deployment Type
The on-premise deployment type leads the UTM market with an estimated size of USD 5.71 billion in 2023, growing to USD 15.63 billion by 2033, while comprising a market share of 60.11%. Cloud-based solutions are also gaining traction, indicating a shift towards flexibility and scalability in security management.
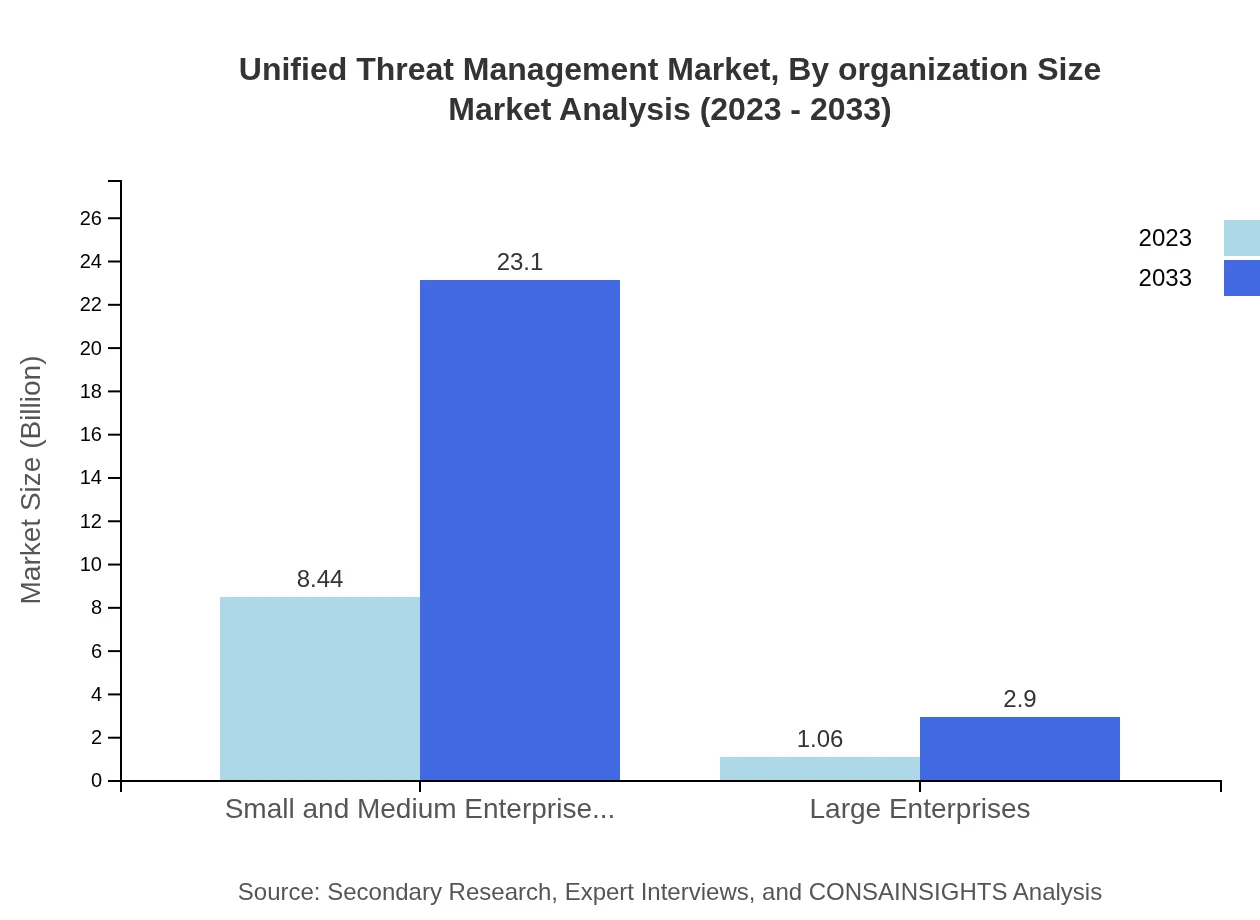
Unified Threat Management Market Analysis By Organization Size
SMEs are expected to lead the UTM market segment with a size of USD 8.44 billion in 2023, projected to reach USD 23.10 billion by 2033, representing an impressive share of 88.83%. This reflects the rising awareness among smaller firms regarding the necessity of integrated security solutions, particularly amid increasing cyber threats.
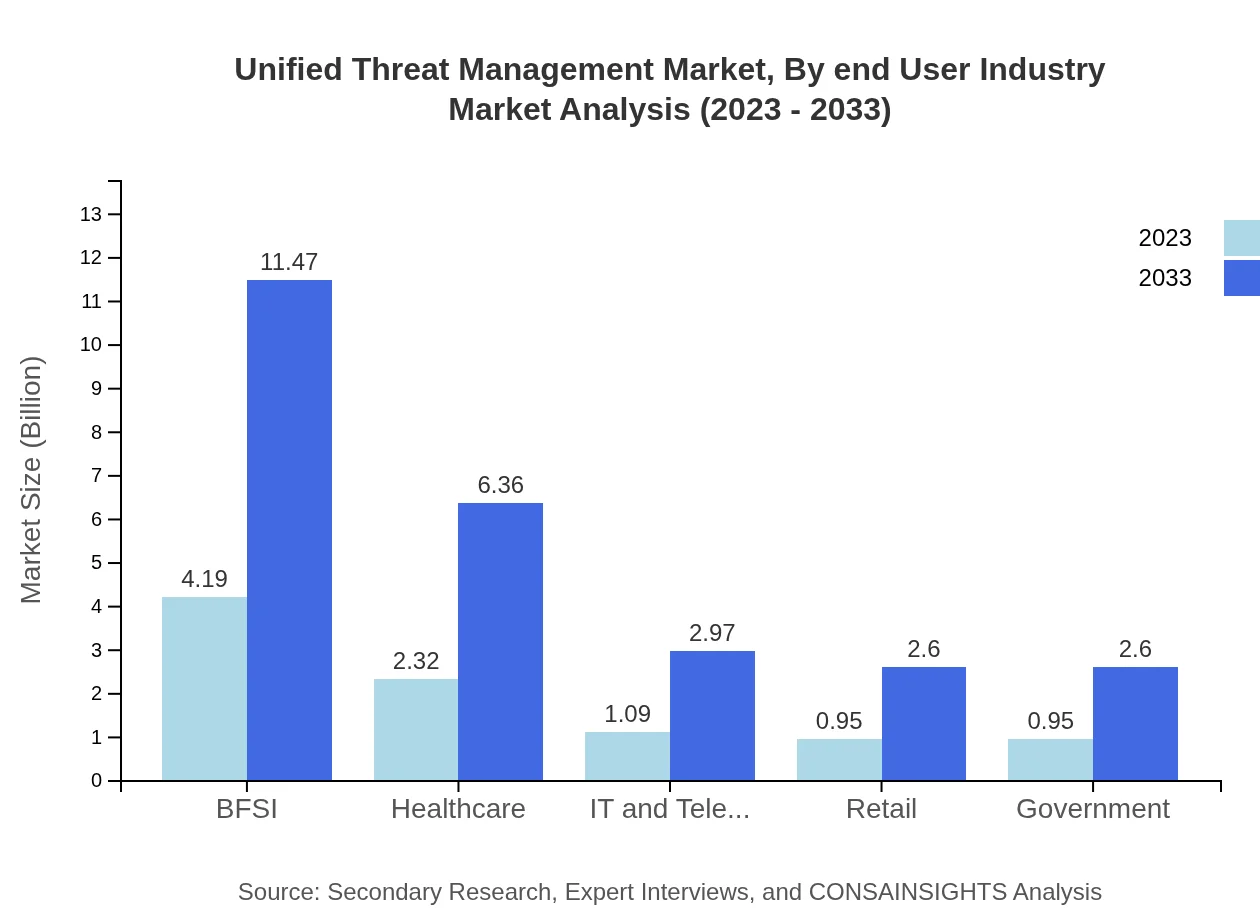
Unified Threat Management Market Analysis By End User Industry
The BFSI sector holds a significant portion of the UTM market, with an estimated size of USD 4.19 billion in 2023, anticipated to grow to USD 11.47 billion by 2033. The urgency for compliance and security against data breaches drives demand across this industry, alongside other key sectors including healthcare and IT and Telecom.
Unified Threat Management Market Analysis By Region Analysis
Regional analysis reveals North America as the leading market segment, significantly driven by advanced infrastructure and stringent regulations, followed closely by Europe. Emerging markets in Asia Pacific are rapidly adopting UTM solutions, while South America and Africa are beginning to recognize the importance of comprehensive cybersecurity measures to combat increasing cyber threats.
Unified Threat Management Market Trends and Future Forecast
Tell us your focus area and get a customized research report.
Global Market Leaders and Top Companies in Unified Threat Management Industry
Cisco Systems, Inc.:
Cisco is a leader in networking and security technology, providing a comprehensive UTM solution that integrates multiple security functions to protect networks from sophisticated threats.Fortinet, Inc.:
Fortinet specializes in high-performance network security appliances and unified threat management systems, focusing on providing advanced protection against evolving cyber threats.Palo Alto Networks, Inc.:
Palo Alto Networks is known for its innovative cybersecurity solutions, offering integrated UTM products that deliver robust security and visibility across enterprise networks.Check Point Software Technologies:
Check Point provides comprehensive cybersecurity software and hardware solutions, known for its integrated UTM capabilities that streamline security management.Sophos Ltd.:
Sophos focuses on next-generation UTM solutions combining multiple security technologies, aimed at simplifying and enhancing protection for businesses of all sizes.We're grateful to work with incredible clients.









FAQs
What is the market size of Unified Threat Management?
The Unified Threat Management market is valued at approximately $9.5 billion in 2023 and is expected to grow at a CAGR of 10.2%, reaching around $26.14 billion by 2033.
What are the key market players or companies in this Unified Threat Management industry?
Major players in the Unified Threat Management market include Cyberoam, Fortinet, Sophos, WatchGuard, and Barracuda Networks, which dominate the landscape through innovative solutions and strategic partnerships.
What are the primary factors driving the growth in the Unified Threat Management industry?
Growth drivers include increasing cyber threats, rising adoption of cloud-based solutions, regulatory compliance needs, and the need for integrated security solutions.
Which region is the fastest Growing in the Unified Threat Management?
North America is the fastest-growing region, expected to expand from $3.67 billion in 2023 to $10.05 billion by 2033, followed closely by Europe and Asia-Pacific.
Does ConsaInsights provide customized market report data for the Unified Threat Management industry?
Yes, ConsaInsights offers customized market reports tailored to client needs, enabling insights into specific segments, regions, and trends in the Unified Threat Management market.
What deliverables can I expect from this Unified Threat Management market research project?
Expect comprehensive market analysis, including market size, growth trends, competitive landscape, regional insights, segmentation data, and future forecasts.
What are the market trends of Unified Threat Management?
Current trends include the shift towards cloud-based solutions, increasing use of AI for threat detection, and the rising importance of mobile security solutions.